Create and manage sensitivity labels
Sensitivity labels from the Microsoft Purview Information Protection let you classify and protect your organization's data, while making sure that user productivity and their ability to collaborate isn't hindered. Sensitivity labels allow Teams admins to protect and regulate access to sensitive organizational content created during collaboration within teams.
Organizations can use sensitivity labels to:
Provide protection settings that include encryption and content markings.
Protect content in Office apps across different platforms and devices.
Protect content in third-party apps and services by using Microsoft Defender for Cloud Apps.
Protect containers that include Teams, Microsoft 365 Groups, and SharePoint sites.
Extend sensitivity labels to Power BI.
Extend sensitivity labels to assets in Microsoft Purview Data Map.
Extend sensitivity labels to third-party apps and services.
Classify content without using any protection settings.
Label scopes
When you create a sensitivity label, you're asked to configure the label's scope, which determines two things:
Which label settings you can configure for that label
Where the label will be visible to users
You can apply the sensitivity labels to the following scopes:
Files & emails: email and Office files
Groups & sites: Microsoft Teams sites, Microsoft 365 groups, and SharePoint sites
Schematized data assets
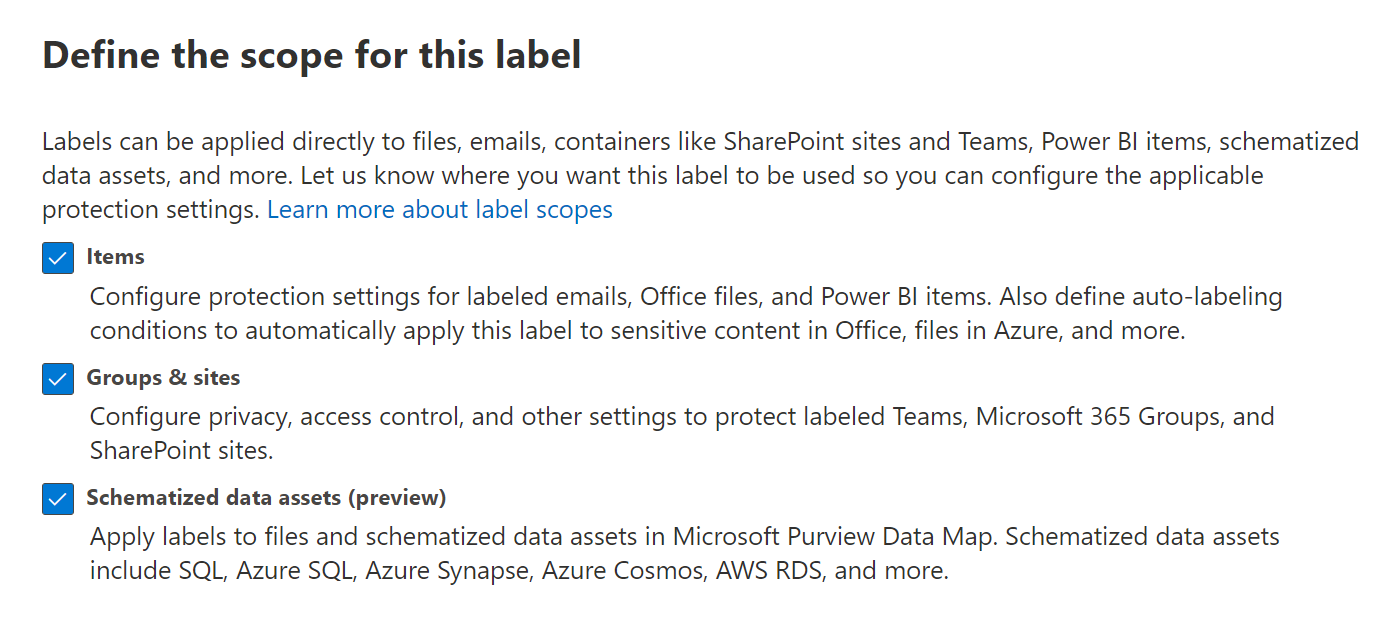
Sensitivity label settings for groups & sites (containers)
In addition to using sensitivity labels to protect documents and emails, you can also use sensitivity labels to protect content in the following containers: Microsoft Teams sites, Microsoft 365 groups (formerly Office 365 groups), and SharePoint sites. For this container-level protection, use the following label settings:
- Privacy (public or private) of teams sites and Microsoft 365 groups
- External user access
- External sharing from SharePoint sites
- Access from unmanaged devices
- Authentication contexts
- Prevent discovery of private teams for users who have this capability (preview)
- Shared channels control for team invitations (preview)
- Default sharing link for a SharePoint site (PowerShell-only configuration)
- Site sharing settings (PowerShell-only configuration)
- Default label for channel meetings
Privacy and external user access settings
Configure the Privacy and External users access settings.
Privacy: Keep the default of Public if you want anyone in your organization to access the team site or group where this label is applied.
Select Private if you want access to be restricted to only approved members in your organization.
Select None when you want to protect content in the container by using the sensitivity label, but still let users configure the privacy setting themselves.
The settings of Public or Private set and lock the privacy setting when you apply this label to the container. Your chosen setting replaces any previous privacy setting that might be configured for the team or group, and locks the privacy value so it can be changed only by first removing the sensitivity label from the container. After you remove the sensitivity label, the privacy setting from the label remains and users can now change it again.
External user access: Control whether the group owner can add guests to the group.
Device external sharing and device access settings
To configure the Control external sharing from labeled SharePoint sites and Use Azure AD Conditional Access to protect labeled SharePoint sites setting.
Control external sharing from labeled SharePoint sites: Select this option to then select either external sharing for anyone, new and existing guests, existing guests, or only people in your organization.
Use Azure AD Conditional Access to protect labeled SharePoint sites: Select this option only if your organization has configured and is using Azure Active Directory Conditional Access. Then, select one of the following settings:
Determine whether users can access SharePoint sites from unmanaged devices: This option uses the SharePoint feature that uses Azure AD Conditional Access to block or limit access to SharePoint and OneDrive content from unmanaged devices.
Choose an existing authentication context: This option lets you enforce more stringent access conditions when users access SharePoint sites that have this label applied. These conditions are enforced when you select an existing authentication context that has been created and published for your organization's Conditional Access deployment. If users don't meet the configured conditions or if they use apps that don't support authentication contexts, they are denied access.
When you apply this sensitivity label to a supported container, the label automatically applies the classification and protection settings to the connected site or group. Content in these containers however, do not inherit the labels for the classification and settings such as visual markings, or encryption.
Make sure you've enabled sensitivity labels for Office files in SharePoint and OneDrive, so that users can label their documents in SharePoint sites or team sites.
You can automatically assign that label to files and emails when it matches conditions that you specify. For more information, see Apply a sensitivity label to content automatically.
Enable sensitivity labels for groups & sites
Configuration options for Site and group settings don't display until you enable this capability.
Note
Azure AD and MSOnline PowerShell modules are planned for deprecation and moved to Microsoft Graph PowerShell. The commands below have been updated to reflect the commands for Microsoft Graph PowerShell.
Open a Windows PowerShell window on your computer.
Connect to Microsoft Graph.
Connect-MgGraphFetch the current group settings for the organization.
$Setting = Get-MgDirectorySetting -Id (Get-MgDirectorySetting | where -Property DisplayName -Value "Group.Unified" -EQ).idNote
If no group settings have been created for this Azure AD organization, you must first create the settings. Follow the steps in Azure Active Directory cmdlets for configuring group settings to create group settings for this Azure AD organization.
Enable the feature:
$Setting["EnableMIPLabels"] = "True"Then save the changes and apply the settings:
Set-MgDirectorySetting -Id $Setting.Id -DirectorySetting $SettingNote
If you were using sensitivity labels before September 2019, you will also need to synchronize your sensitivity labels to Azure AD.
For more information and instructions, see How to enable sensitivity labels for containers and synchronize labels.
Create and publish sensitivity labels
The global admin can create and manage sensitivity labels from the Microsoft Purview compliance portal.
For additional guidance and instructions, see Create and publish sensitivity labels.
Go to the Microsoft Purview compliance portal > Information protection.
Select Labels tab and select + Create a label to start the New sensitivity label wizard.
On the Name and create a tooltip for your label page, provide information.
On the Define the scope for this label page, select Groups & sites or other scopes.
The options selected determine the label's scope for the settings that you can configure and where they'll be visible when they're published
Follow the prompts in the wizard for the label settings to complete the creation.
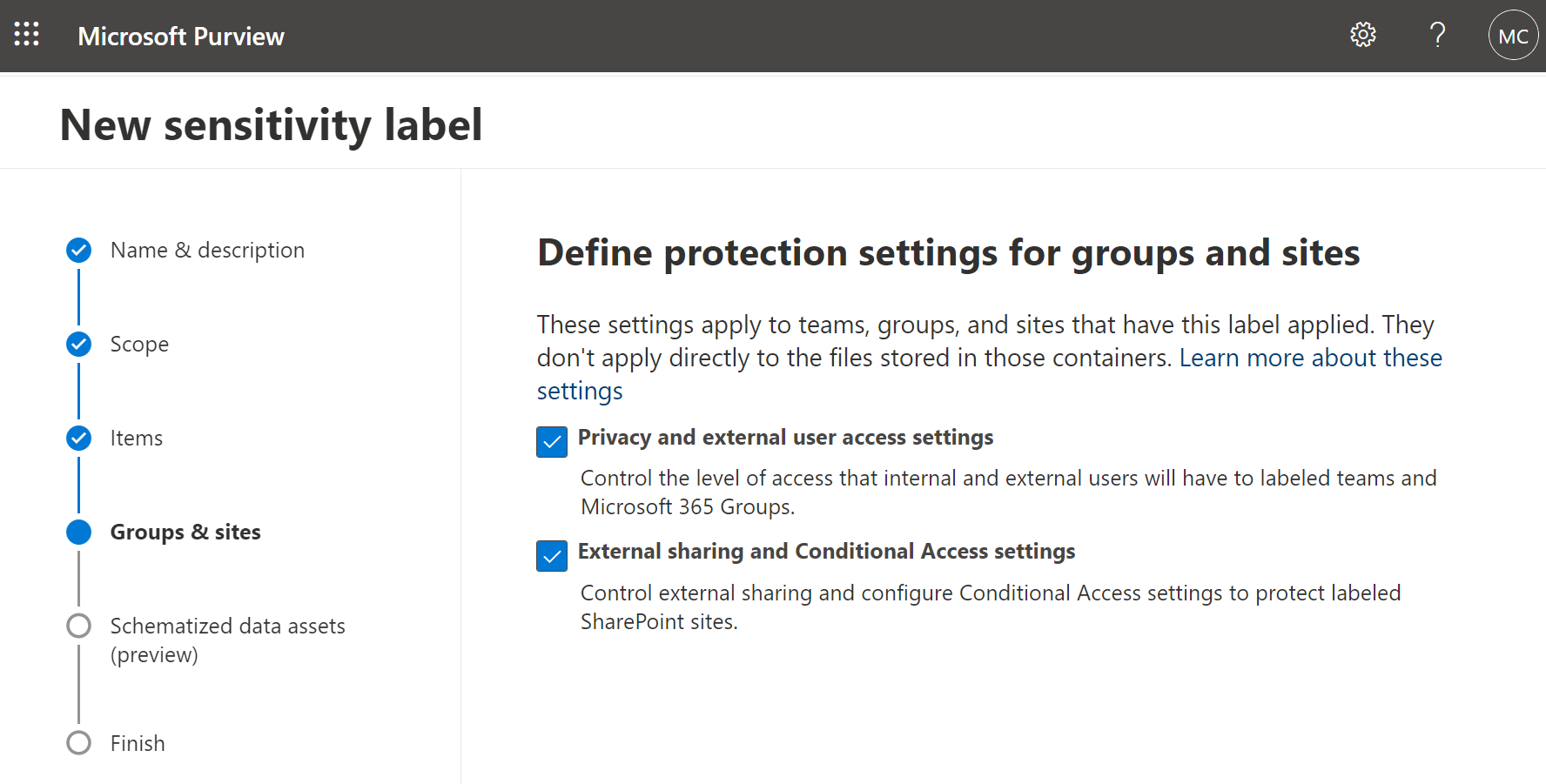
Once you created a sensitivity label, you need to publish the sensitivity label by creating a label policy. The users who are assigned a sensitivity label policy that includes this label will be able to select it for sites and groups.
Only these site and group settings take effect when you apply the label to a team, group, or site. Other label settings, such as encryption and content marking, aren't applied to the content within the team, group, or site.
Use sensitivity labels with Teams
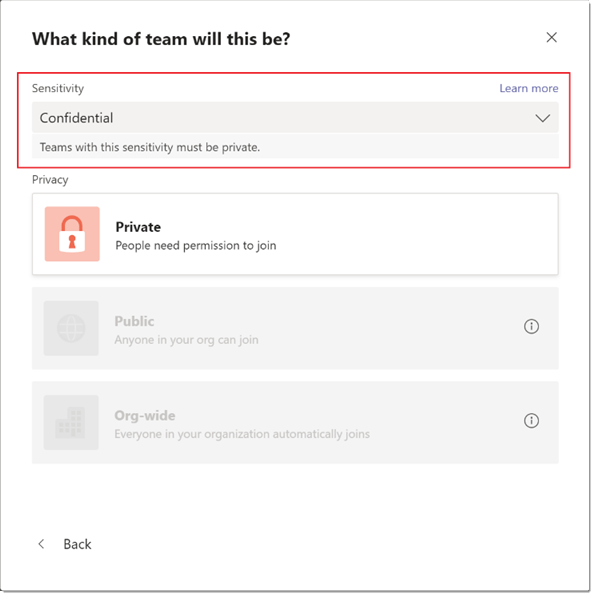
Admins can create a sensitivity label that, when applied during team creation, allows users to create teams with a specific privacy (public or private) setting.
For example, the admin creates a sensitivity label named "Confidential" with the policy that any team that's created with this label must be a private team. When a user creates a new team and selects the Confidential label, the only privacy option that's available to the user is Private. Other privacy options such as Public and Org-wide are disabled for the user.
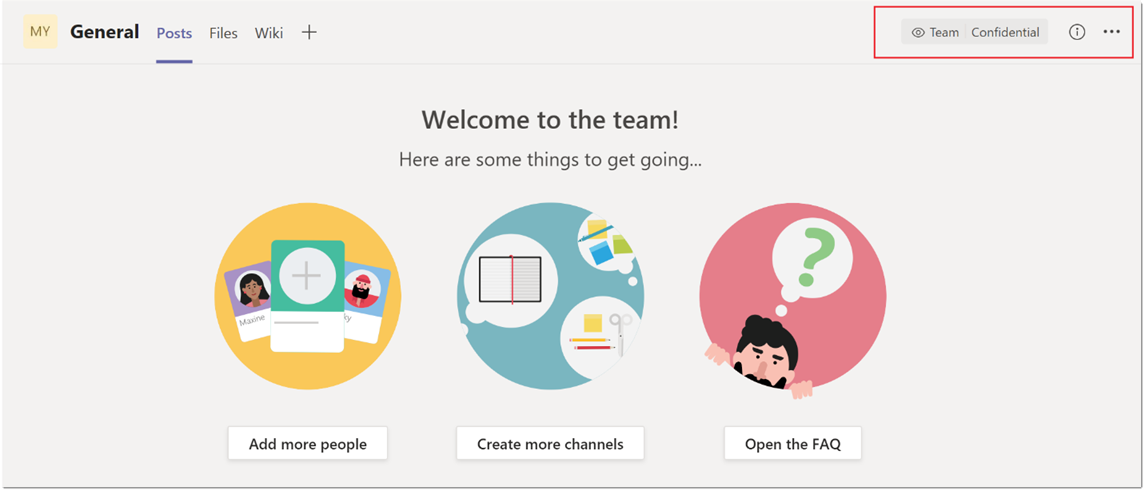
When the team is created, the sensitivity label is visible in the upper-right corner of channels in the team.
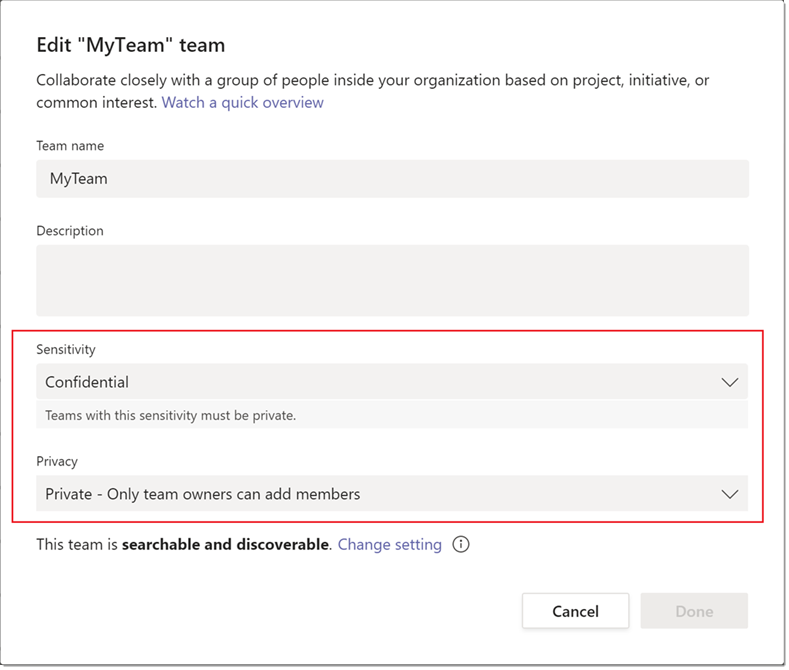
A team owner can change the sensitivity label and the privacy setting of the team at any time by going to the team, and then clicking Edit team.
Note
Microsoft 365 no longer supports the old classifications for new Microsoft 365 groups and SharePoint sites after you enable sensitivity labels for containers. However, existing groups and sites that support sensitivity labels still display the old classification values until you convert them to use sensitivity labels. For more information, see Azure Active Directory classification and sensitivity labels for Microsoft 365 groups.
For more information, see:
Example scenarios for sensitivity labels
Example scenarios for how you can use sensitivity labels with Teams in your organization include:
- Set the privacy level (public or private) for teams
- Control guest access to teams
Control guest access to teams
You can use sensitivity labels to control guest access to your teams. Teams created with a label that doesn't allow guest access are only available to users in your organization. People outside your organization can't be added to the team.
Microsoft Teams admin center
You can apply sensitivity labels when you create or edit a team in the Microsoft Teams admin center. Sensitivity labels are also visible in team properties and in the Classification column on the Manage teams page of the Microsoft Teams admin center.
Limitations
Before you use sensitivity labels for Teams, be aware of the following limitations:
Sensitivity labels aren't supported by Teams Graph APIs and PowerShell cmdlets
Users won't be able to specify sensitivity labels while creating teams directly through Teams Graph APIs or Teams PowerShell cmdlets. However Modern Groups Graph APIs and PowerShell cmdlets do allow the creation of groups with sensitivity labels. This means that you can create groups with sensitivity labels by using these methods, and then convert these groups into teams.
Support for private channels
Private channels that are created in a team inherit the sensitivity label that was applied on a team. The same label is automatically applied on the SharePoint site collection for the private channel.
However, if a user directly changes the sensitivity label on a SharePoint site for a private channel, that label change isn't reflected in the Teams client. In this scenario, users continue to see the original sensitivity label applied on the team in the private channel header.
How to create and configure sensitivity labels for Teams
Use the instructions from the Microsoft Purview documentation to create and configure sensitivity labels for Teams:
Admin policies' effect on sensitivity labels and meeting templates
While some admin policies—such as lobby settings and who can present—specify defaults that the meeting organizer can change, most admin policies determine if a given feature is available to users at all.
Sensitivity labels can enforce end-to-end encryption, watermarks, and automatic recording even if the related admin policy is turned off for the meeting organizer. Templates can't do this, however. Admin policies take precedence over template settings.
For example, if you create a highly sensitive label and configure it to enforce watermarking and end-to-end encryption, that enforcement will take place even if watermarking and end-to-end encryptions are disabled for the meeting organizer in the admin policy. However, if you use a template to turn on watermarking and end-to-end encryption for that same meeting organizer, those features won't be available in the meeting because the admin policy takes precedence over them.
As you plan for your meeting templates and sensitivity labels, ensure that the settings that you want to control with them are enabled in admin policies where required.
Sensitivity labels and templates together
Some settings are only available in sensitivity labels and some are only available in templates. The following are available in both:
- Chat
- End-to-end encryption
- Lobby settings
- Meeting recording
- Watermarking
Whenever a sensitivity label is used, the settings configured in the label take precedence over any template or meeting organizer settings.
The settings in a sensitivity label can be left uncontrolled when the label is created, allowing a template or the meeting organizer to control these settings.
Sensitivity labels are often used for multiple purposes—labeling documents, sites, and emails, as well as meetings. You can avoid creating additional labels that are just for meetings by using templates along with the labels to account for variations within a particular type of meeting.
For example your marketing department might have different requirements than the research department for sensitive meetings. You can configure the settings that are common to both in a sensitivity label and then make separate templates available to the two groups, which further refine the meeting settings for that group. Both templates could use the same label.
User-based policies and meeting-based policies
Teams policies—including meeting policies—apply at the user or group level. Sensitivity label and template settings apply at the individual meeting level where those labels and templates are used. Consider where it makes sense to configure settings in Teams admin policies versus sensitivity labels or templates.
Here are a few examples:
If you want different default lobby settings for the research department and the marketing department, you can configure these defaults using admin policies and further modify them with labels or templates.
If you want watermarks available only for governance officials, you can enable them only for those people using an admin policy. You can then have templates that enforce watermarking, but the watermarking will only be used in meetings organized by governance officials.
Different meeting types with the same sensitivity
Using templates and labels together can be useful if you have different types of meetings that have the same sensitivity. For example, if some of your sensitive meetings are interactive and some are presentations where there's minimal interaction from attendees, you can create two templates:
- One to use for presentations that turn off attendee video and audio.
- One to use for interactive meetings that leave video and audio at the discretion of the meeting organizer.
Both templates could use the Sensitive label, which would control additional settings such as who can bypass the lobby and who can present.
Specify default values that meeting organizers can change
While labels generally enforce a particular setting, templates can either enforce a setting or allow the meeting organizer to change it. This allows you to implement default settings that meet your compliance needs while giving meeting organizers the option to override the setting if appropriate.
For example, for a baseline level of protection, you might want to use a sensitivity label to turn off watermarking. At the same time, you can use a template to set the default for who can bypass the lobby, but allow the meeting organizer to change the setting if they need to.
You can assign your baseline protection label to the template so that both are used when a meeting organizer chooses that template.
Some admin policies can also be used to set a default value that can be changed by a meeting organizer. These include lobby controls and who can present.
For more information, see Use Teams meeting templates, sensitivity labels, and admin policies together for sensitive meetings
Sensitivity labels for Microsoft Teams Premium
Microsoft Teams Premium brings sensitivity labels and policies together with configurable meeting features. Depending on how an organization configures its labels, Teams Premium applies a templatized set of designated meeting options designed to enhance security and compliance.
Those options include:
- Who needs to wait in the meeting lobby
- Who needs to ask to join the meeting
- Calendar labels, for example, “Don't forward”
- Enforcing automatic recording
- Restricted copying and pasting from the meeting chat
- Advanced encryption control for audio-video streams
- Watermarking on live content and video
For more information, see Use sensitivity labels to protect calendar items, Teams meetings and chat.

