Create security and compliance alerts for Microsoft Teams
You can use the alert policy to monitor users' activities. Alerts are generated when users perform activities that match the conditions of an alert policy. For example, malware attacks, phishing campaigns, and unusual levels of file deletions and external sharing. You can create and review the alert dashboard from the Microsoft Purview compliance portal.
Alert policies let you categorize the alerts that are triggered by a policy, apply the policy to all users in your organization, set a threshold level for when an alert is triggered, and decide whether to receive email notifications when alerts are triggered.
How alert policies work
The following diagram shows the basic workflow of how alert policies work:
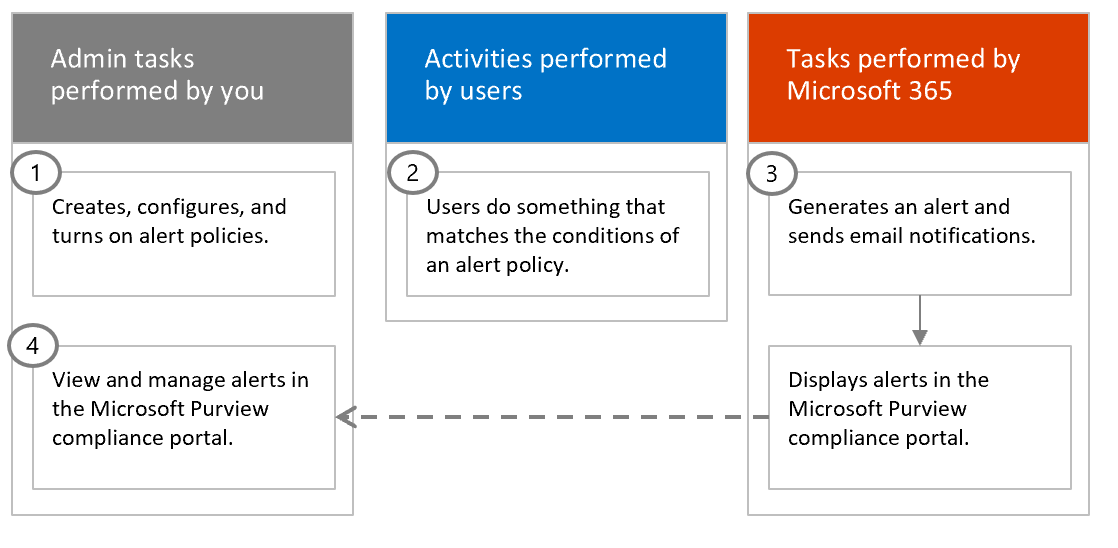
Administrators create new or modify existing policies in the Microsoft Purview compliance portal that monitor unusual user or admin activity.
A user or administrator performs actions, which match the conditions and triggers an alert policy, such as creating an eDiscovery case or possibly adding full access permissions to a mailbox.
An alert is generated, and the according alert action is triggered, such as sending an email to all global administrators. Additionally, an alert entry is created in the alert dashboard in the Microsoft Purview compliance portal.
Administrators review alerts in the alerts dashboard and decide to acknowledge or dismiss the alert.
Alert policy settings
An alert policy consists of a set of rules and conditions that define the user or admin activity that generates an alert, a list of users who trigger the alert if they perform the activity, and a threshold that defines how many times the activity has to occur before an alert is triggered. You also categorize the policy and assign it a severity level.
An alert policy consists of the following settings and conditions:
Activity the alert is tracking: You create a policy to track an activity or in some cases a few related activities, such a sharing a file with a guest by sharing it, assign access permissions, or create an anonymous link. When a user performs the activity defined by the policy, an alert is triggered based on the alert threshold settings.
Activity conditions: For most activities, you can define other conditions that must be met to trigger an alert.
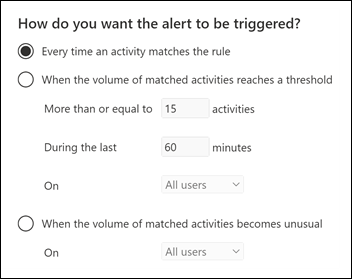
When the alert is triggered: You can configure a setting that defines how often an activity can occur before an alert is triggered.
Alert category: To help with tracking and managing the alerts generated by a policy, you can assign one of the following categories to a policy:
Data loss prevention
Data lifecycle management
Mail flow
Permissions
Threat management
Others
When an activity occurs that matches the conditions of the alert policy, the alert that's generated is tagged with the category defined in the setting. The tagging allows you to track and manage alerts that have the same category setting on the Alerts page in the compliance portal because you can sort and filter alerts based on category.
Alert severity: Similar to the alert category, you assign a severity attribute (Low, Medium, High, or Informational) to alert policies. Like the alert category, when an activity occurs that matches the conditions of the alert policy, the alert that's generated is tagged with the same severity level that's set for the alert policy.
Email notifications: You can set up the policy so that email notifications are sent (or not sent) to a list of users when an alert is triggered.
Create new alerts
To create a new alert policy in the Microsoft Purview compliance portal and to check if audit logging is turned on, follow these steps:
Sign into the Microsoft Purview compliance portal and select Policies > Alert policies.
Select + New alert policy from the top pane to create a new alert policy.
On the Name your alert, categorize it, and choose a severity. page, enter the following:
Name for identifying the use of this alert policy.
Description for other administrators to understand the purpose of this alert policy.
Severity for a level of importance for events of these alerts.
Category to configure access for different roles in your organization.
Select Next.
On the Choose an activity, conditions and when to trigger the alert page, select a desired activity and condition for the alert, then select Next.
On the Decide if you want to notify people when this alert is triggered page, you can specify the recipients of the notification and frequency of daily notification limit. Select Next.
On the Review your settings page, you can review the alert settings and decide to turn on the policy right away or later. Select Finish when everything is configured as desired.
View alerts
The Role Based Access Control (RBAC) permissions assigned to users in your organization determine which alerts a user can see on the Alerts page. Here are some examples:
Members of the Microsoft Purview Records Management role group can view only the alerts that are generated by alert policies that are assigned the Information governance category.
Members of the Compliance Administrator role group can't view alerts that are generated by alert policies that are assigned the Threat management category.
Members of the eDiscovery Manager role group can't view any alerts because none of the assigned roles provide permission to view alerts from any alert category.
For more information, see Alert policies in Microsoft 365.

