Introduction to Zero Trust
A Zero Trust approach to security is required to be effective at keeping up with threats, changes to cloud platforms, and changes in business models responding to a rapidly evolving world. You can find best practices for adopting a Zero Trust approach to security throughout the Microsoft Cybersecurity Reference Architecture (MCRA) and Microsoft cloud security benchmark (MCSB).
Microsoft Zero Trust approach to security is based on three principles: assume breach, verify explicitly, and least privilege.
Guiding principles of Zero Trust
Verify explicitly - Always authenticate and authorize based on all available data points.
Use least privilege access - Limit user access with Just-In-Time and Just-Enough-Access (JIT/JEA), risk-based adaptive policies, and data protection.
Assume breach - Minimize blast radius and segment access. Verify end-to-end encryption and use analytics to get visibility, drive threat detection, and improve defenses.
This is the core of Zero Trust. Instead of believing everything behind the corporate firewall is safe, the Zero Trust model assumes breach and verifies each request as though it originated from an uncontrolled network. Regardless of where the request originates or what resource it accesses, the Zero Trust model teaches us to "never trust, always verify."
It is designed to adapt to the complexities of the modern environment that embraces the mobile workforce, protects people, devices, applications, and data wherever they are located.
A Zero Trust approach should extend throughout the entire digital estate and serve as an integrated security philosophy and end-to-end strategy. This is done by implementing Zero Trust controls and technologies across six foundational elements. Each of these is a source of signal, a control plane for enforcement, and a critical resource to be defended.
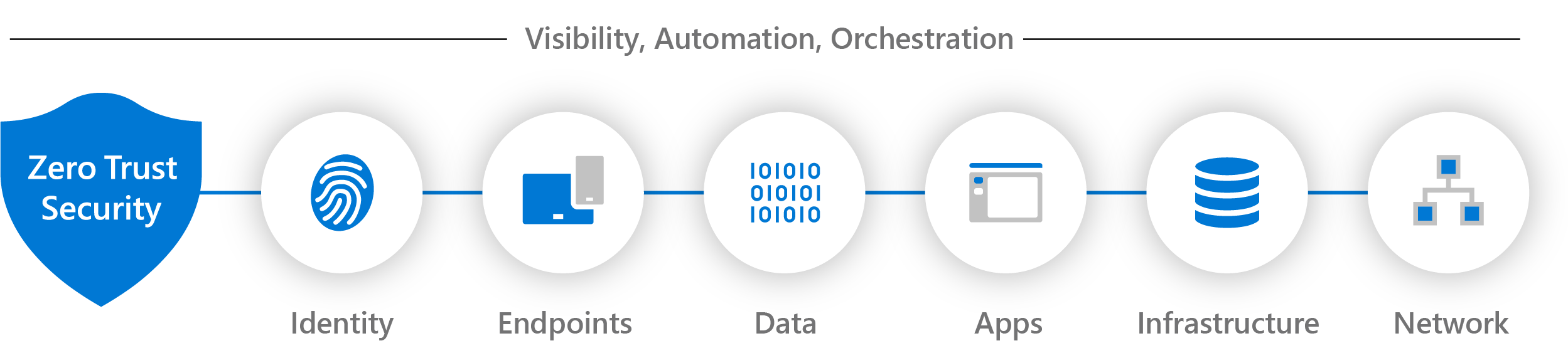
Different organizational requirements, existing technology implementations, and security stages all affect how a Zero Trust security model implementation is planned. Using our experience in helping customers to secure their organizations, as well as in implementing our own Zero Trust model, we've developed the following guidance to assess your readiness and to help you build a plan to get to Zero Trust.
These principles apply across the technical estate and are usually applied to a Zero Trust transformation through a series of either modernization initiatives (RaMP) or technology pillars (with deployment guidance for each pillar).