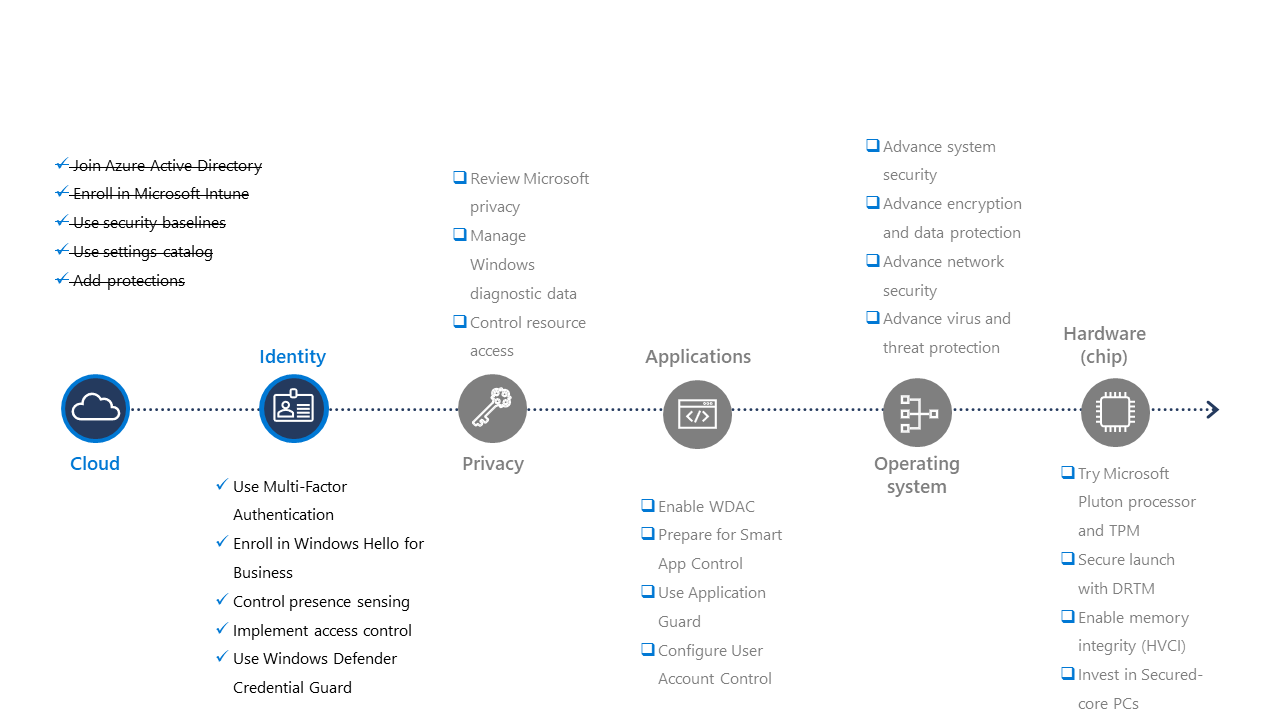
Advance your identity security
Our work and personal lives increasingly depend on the security of our credentials. This means that credential breaches can have serious consequences for your organization and your users. Identity can represent people, devices, and even services. To protect your users and organization as a whole, your best option is a Zero Trust approach. It helps you to ensure that identities across your organization remain strong, flexible, and empower you to control access at a granular level. The modern device management tools we’ve just covered will help advance your organization’s security posture based on this feature selection. Manage and secure identities for employees, partners, and customers anywhere with Microsoft Intune and Microsoft Entra ID to complement your monthly servicing updates.
Go passwordless with multi-factor authentication
Passwords can be hard to remember, and they're frequent targets for cybercriminals. More often than we’d like to admit, users reuse the same password across accounts. To tackle this issue, use Windows Hello for Business as the premier built-in passwordless solution and/or multi-factor authentication (MFA) with Microsoft Entra ID.
Windows takes a Zero Trust approach to passwords through several FIDO-certified methods, enabling the use of FIDO2 security keys for shared devices. Fast Identity Online (FIDO) is an open authentication standard that is designed to prevent users from reusing the same passwords across accounts. If one account is compromised, all accounts using that same password are also at risk. We’ll cover passwordless and multi-factor authentication, which can be used together for maximum protection.
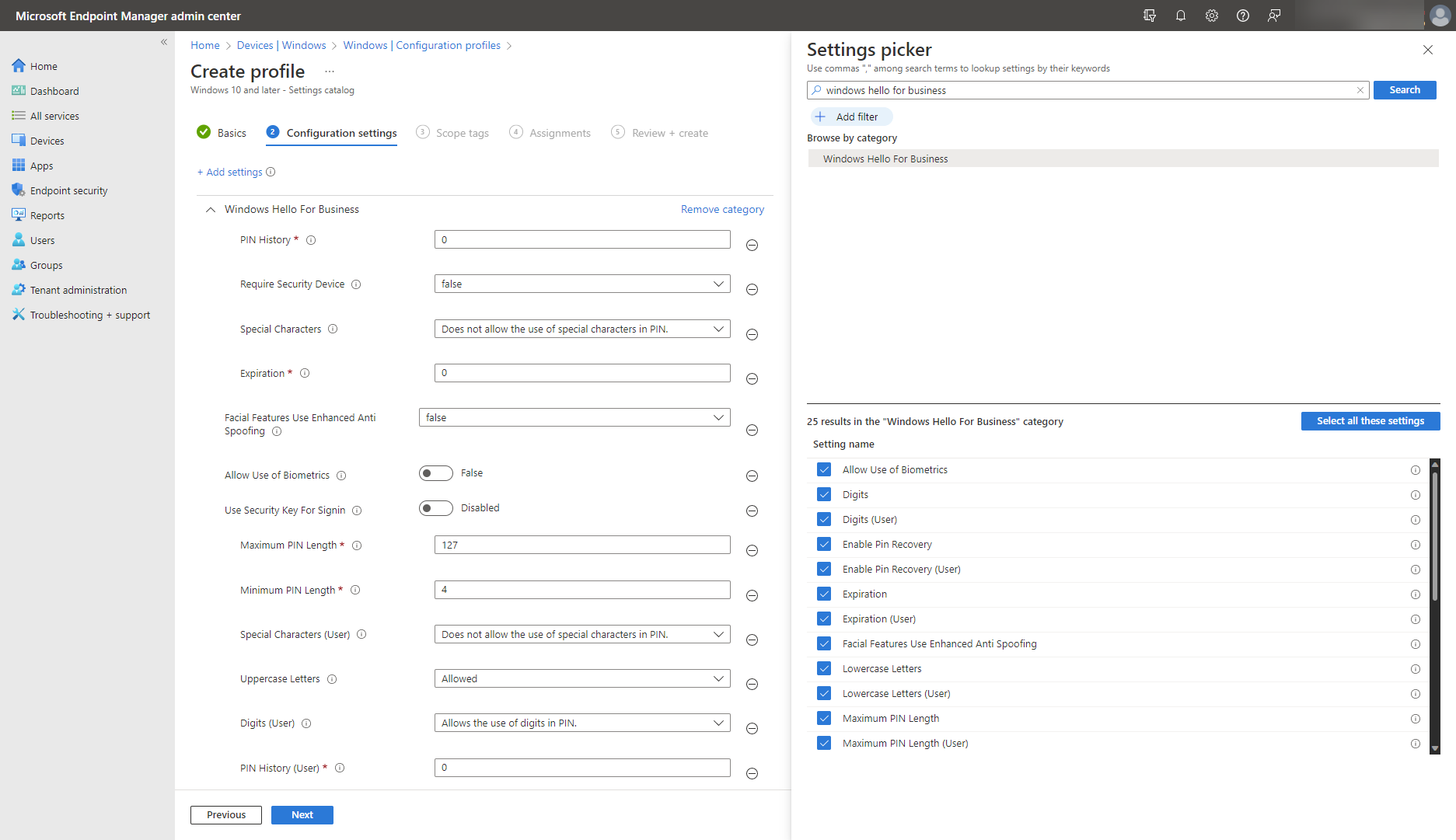
Windows Hello for Business can protect user identities by removing the need to use passwords from day one. It relies on facial recognition, a fingerprint, or a PIN to verify user identity. It binds the user’s credentials to their device, can only be used on the registered device, and will not work on any other device. This setup, integrated with Microsoft Entra ID in enterprise, multiple device scenarios protects against password stealing and phishing attacks. Improve your security posture with the following stages:
Get started: Enroll your devices in Windows Hello for Business based on your organization’s environment, including on-premises, cloud, or hybrid. Configure a tenant-wide Windows Hello for Business policy with Microsoft Intune or manually:
- Set Windows Hello for Business to Enable.
- Configure PIN requirements: length, letter case, special characters, expiration, history, and recovery options.
- Enable additional protections, such as a Trusted Platform Module (TPM) chip, biometric authentication, anti-spoofing, certificate for on-premises resources, and security keys for sign-in.
Advance further: For increased protection, create conditional access, for example, to only allow users to gain access to resources if they’re on devices that are managed and up to date based on organization’s security policies. This way, you can help protect your organization from the remote credential stealing and phishing attacks. Always require users to physically act to gain access and reduce the number of passwords needed.
Optimize: For even stronger security, configure Windows Hello for Business to combine passwordless protection with multi-factor authentication (MFA) provided by the identity provider such as Microsoft Entra ID.
Alternatively, use the settings catalog to configure Windows Hello for Business, illustrated below.
With multi-factor authentication (MFA), you can combine multiple authentication requirements before access is granted to an account. For example, you can require that users also approve any request using their Microsoft Authenticator app or provide a verification code sent to their phone or email in addition to their biometric information in order to gain access.
If the device is registered within the Microsoft Entra tenant and associated to an individual user, you can set up passwordless authentication that requires the user’s biometrics or a PIN to access that device. Use the Microsoft Authenticator app to set it up. Microsoft Authenticator can also be used to bootstrap Windows Hello for Business.yFinally, you can enable users to use a single physical security key as alternative passwordless authentication to access resources and platforms.
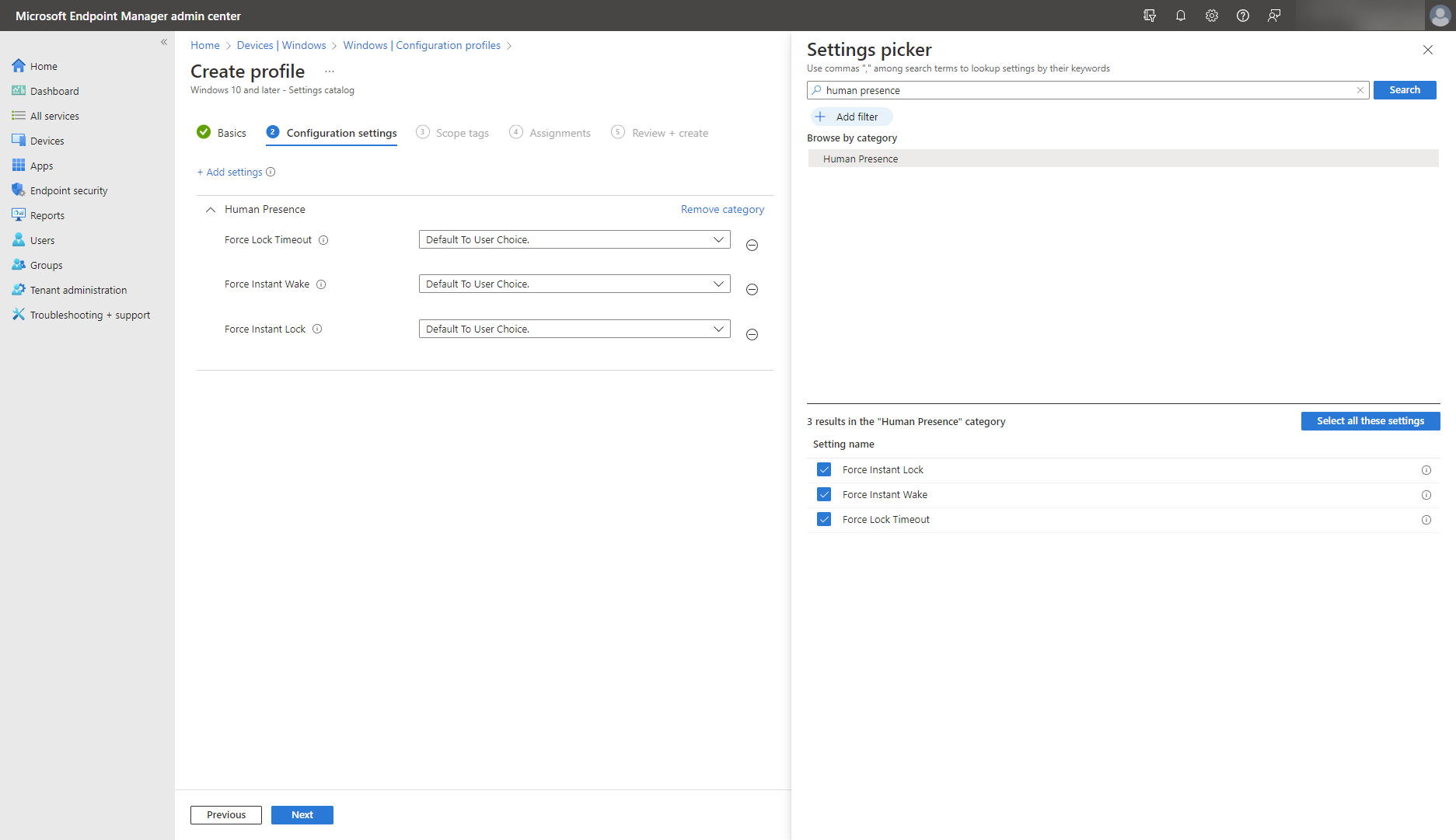
Presence sensing: Wake on approach and lock on leave
Windows presence sensing provides another layer of data security and privacy protection for hybrid workers. The latest Windows devices can intelligently adapt to your presence to help you stay secure and productive, whether you’re working at home, the office, or a public environment. Windows presence sensing uses Windows Hello facial recognition with presence detection sensors to sign you in hands-free, and automatically lock your device when you leave. The capability to wake your PC upon approach is configurable on Windows 11 devices, while the lock on leave feature is also available on Windows 10. Check if your device has a presence sensor built in to wake up and pair it up with Bluetooth to lock it.
Control presence sensing using the settings catalog:
Implement access control
Access Control enables you to control objects and audit system events, such as if a user tries to access certain file system objects. This way, you can control and track activities on sensitive objects.
Configure access control for your Windows devices to control the authorization of users, groups, and computers to objects and resources across your organization’s devices and network. With access control you can:
- Enable users to access resources in a manner that is consistent with organizational policies and what they need for their daily work.
- Update users’ ability to access resources regularly as an organization’s policies change or as users’ jobs change.
- Identify and fix access issues when legitimate users are unable to access resources that they need to perform their jobs.
Use Access Control Lists to configure the permissions available for specific objects. Use System Access Control Lists for permissions to system resources.
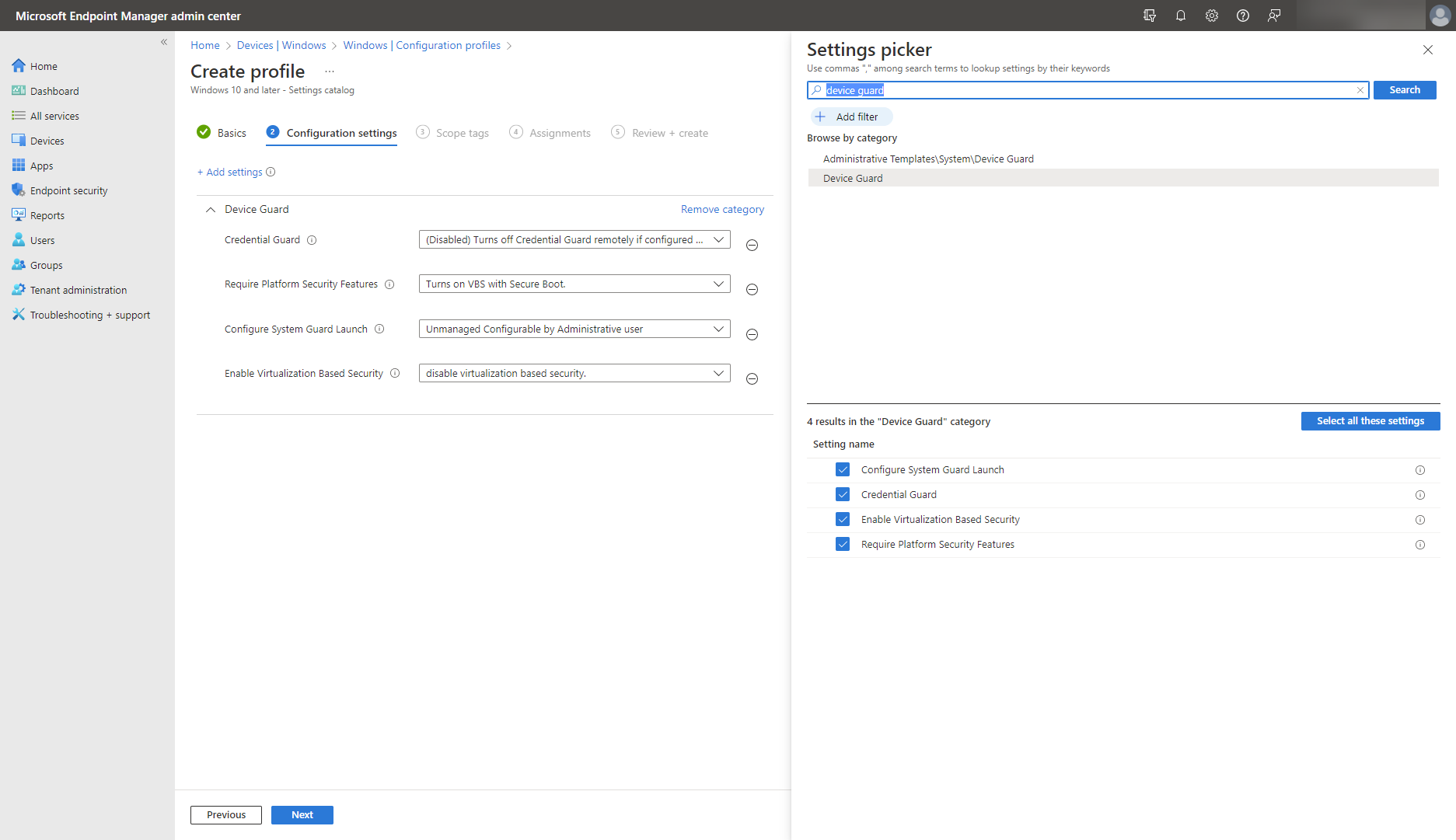
Use Windows Defender Credential Guard
Beginning with Windows 11, version 22H2 update, the Windows Defender Credential Guard is enabled by default on enterprise edition. If not, enable Windows Defender Credential Guard to protect your system using a combination of hardware and virtualization-based security. Use it to protect against advanced persistent threats, including credential theft attacks like pass-the-hash, where a cybercriminal uses a hash of a password in order to move laterally across the environment. It can also prevent malware, which might have somehow gained administrative privileges, from extracting secrets.
Enable Windows Defender Credential Guard using the settings catalog or a security baseline, as illustrated below.
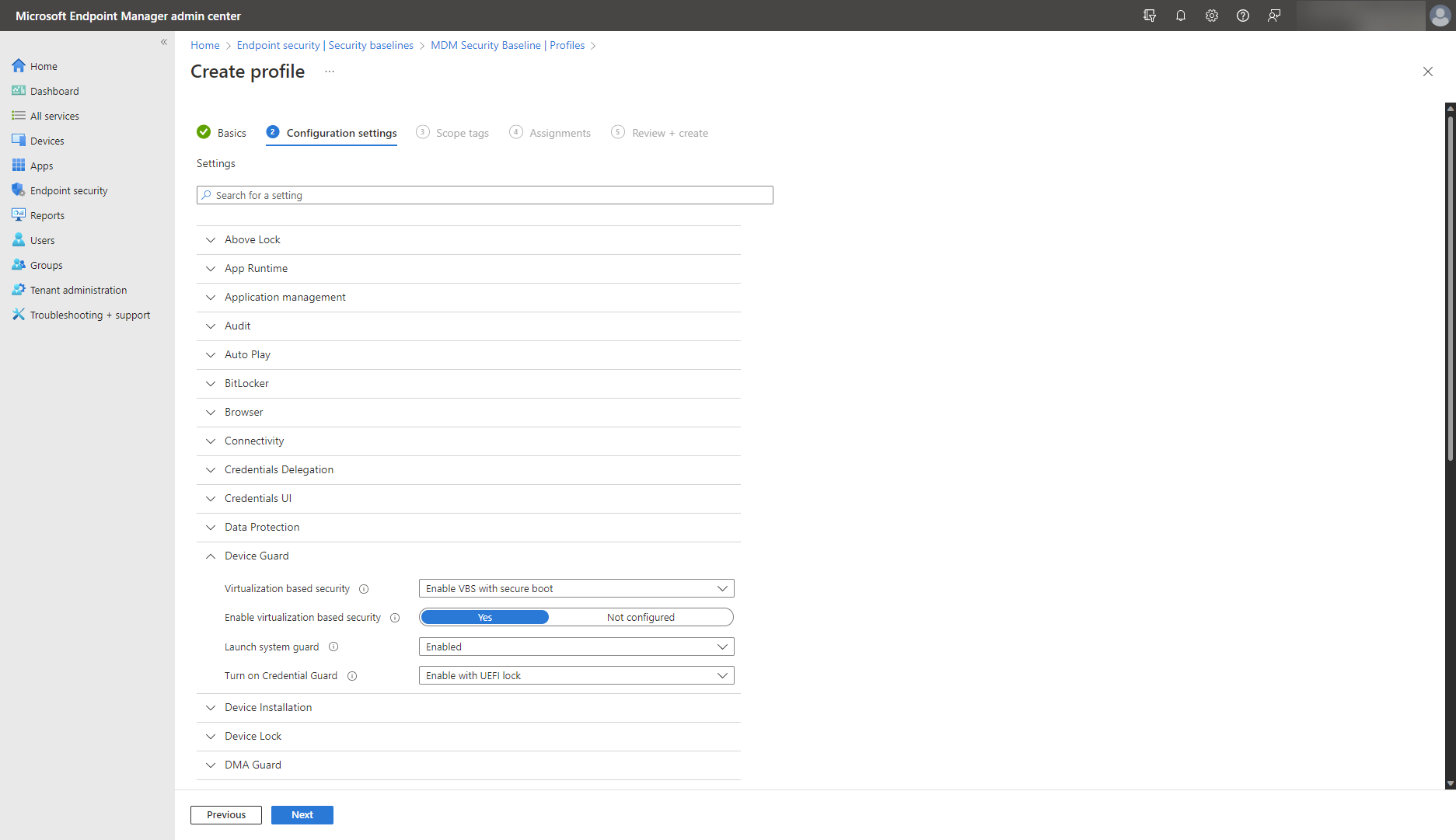
Users in your organization might need to connect to remote devices over a remote desktop connection. If so, enable Windows Defender Remote Credential Guard to ensure that credentials are never passed over the network, and instead only stay on your devices. Additionally, it will also allow you to provide single sign-on experiences for all remote desktop sessions, for seamless and protected sign-ins.