Secure your applications layer
Zero Trust mandates securing all applications: applications that are centrally managed or controlled, and reputable and trusted applications managed by your users. This is because if any application has its security misconfigured, even for a short while, it can create opportunities for hackers to exploit its vulnerabilities. Any improperly secured application can enable cybercriminals to gain access to important data on devices and the wider networks to which they’re connected. Downloading regular updates from your app vendors is the first step to ensure that your applications are protected. Additionally, keeping your Windows OS updated with monthly quality and feature updates provided by our servicing mechanisms contributes to increased application security and improved tools. Let’s look at some of the configurable application security features and Intune tools that you can further use to implement protection for applications on all of your organization’s devices.
Windows Defender Application Control (WDAC)
Ensure that you’re only allowing appropriate applications on your devices as the first proactive step to your application security strategy. While memory integrity hardens your operating system against kernel memory threats, you can combine it with Windows Defender Application Control (WDAC) for enhanced protections with an appropriate enterprise license. Do so by controlling which applications are allowed to be installed and run on your devices.
To begin, configure and enable WDAC by doing the following:
- Define the desired circle-of-trust for your WDAC policies. By circle-of-trust, we mean a description of the business intent of the policy expressed in natural language. This definition will guide you as you create the actual policy rules for your policy XML.
- Use Windows Defender Application Control wizard to create your initial policy. Learn more about using Intune’s built-in policies and designing and creating your own policy rules and file rules, which are undergoing constant improvements.
- Deploy the policy in audit mode on a small set of devices.
- Use the Windows Defender Application Control wizard to create rules from event logs for any files blocked on the small set of devices that you want to allow.
- Repeat the above steps as many times as necessary.
- Deploy the policy in audit mode on more devices.
- Continue to monitor events (for example, with advanced hunting).
- Once ready, convert the policy to enforcement mode and repeat the staged deployment.
- To get even more secure, use signed policies to protect Windows Defender Application Control against tampering.
Secondly, deploy your WDAC policies in Intune with custom OMA-URI functionality, which will be improving in the upcoming months:
- Know a generated policy’s GUID, which can be found in the policy xml as <PolicyID
- Convert the policy XML to binary format using the ConvertFrom-CIPolicy cmdlet in order to be deployed. The binary policy may be signed or unsigned.
- Open the Microsoft Intune portal and create a profile with custom settings.
- Specify a Name and Description, and use the following values for the remaining custom OMA-URI settings:
- OMA-URI: ./Vendor/MSFT/ApplicationControl/Policies/Policy GUID/Policy
- Data type: Base64
- Certificate file: upload your binary format policy file. You don't need to upload a Base64 file, as Intune will convert the uploaded .bin file to Base64 on your behalf.
Smart App Control
With Smart App Control, some small businesses can give employees flexibility to choose their own applications, while maintaining tight security. Smart App Control prevents users from running malicious applications on Windows devices by blocking untrusted or unsigned software. This way, Smart App Control goes beyond previous built-in browser protections. Using AI, the feature only allows running apps that are predicted to be safe, based on existing and new intelligence processed daily.
Smart App Control is available on new devices shipped with Windows 11, version 22H2. Devices with previous versions of Windows 11 can take advantage of this feature with a reset and clean installation of Windows 11, version 22H2. Learn more on how to adapt this feature to your particular environment.
Application isolation and containers
Sometimes, cybercriminals might try to use social engineering tactics to trick users into facilitating their application attacks, such as getting users to open malicious links in emails or visit a malicious site. Browsers and applications’ scanning and filtering capabilities might not be enough to stop these types of attacks, so we offer a few servicing tools to help.
You’re taking a Zero Trust stance against any application and browser session when treating it as untrustworthy by default. Isolate applications through Microsoft Defender Application Guard and run websites opened in Microsoft Edge browser, Word files, Excel files, and others inside a container that is separate from the rest of the system. This means that any malicious code and activity is contained inside the container and away from the desktop system. To implement application isolation, configure it using Microsoft Defender Application Guard for Office or for Edge browser. In Intune, locate Microsoft Defender Application Guard settings in the settings catalog, under Microsoft Edge category:
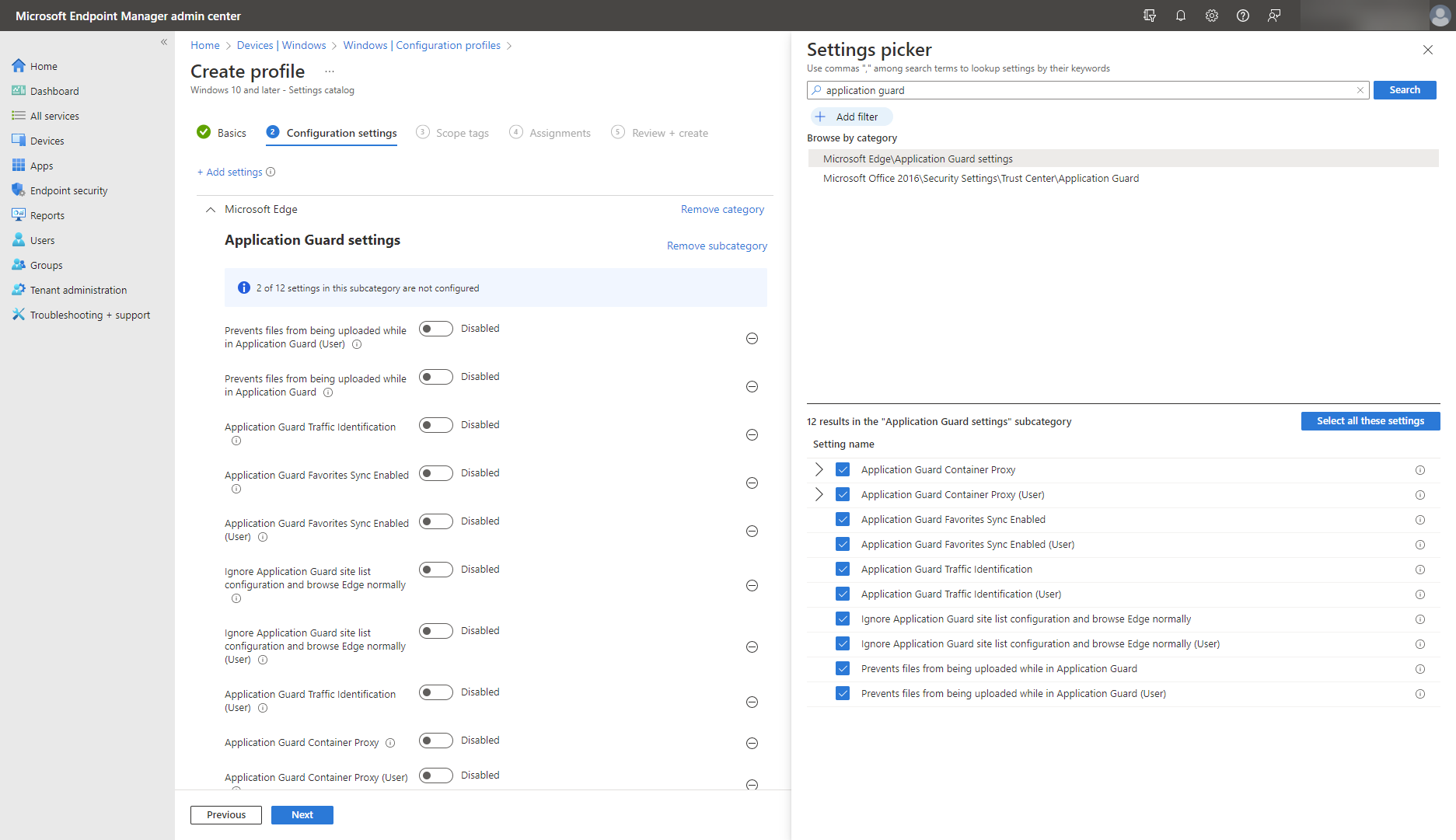
Similarly, locate Microsoft Office category in settings catalog to configure Security Settings > Trust Center > Application Guard, as shown below.
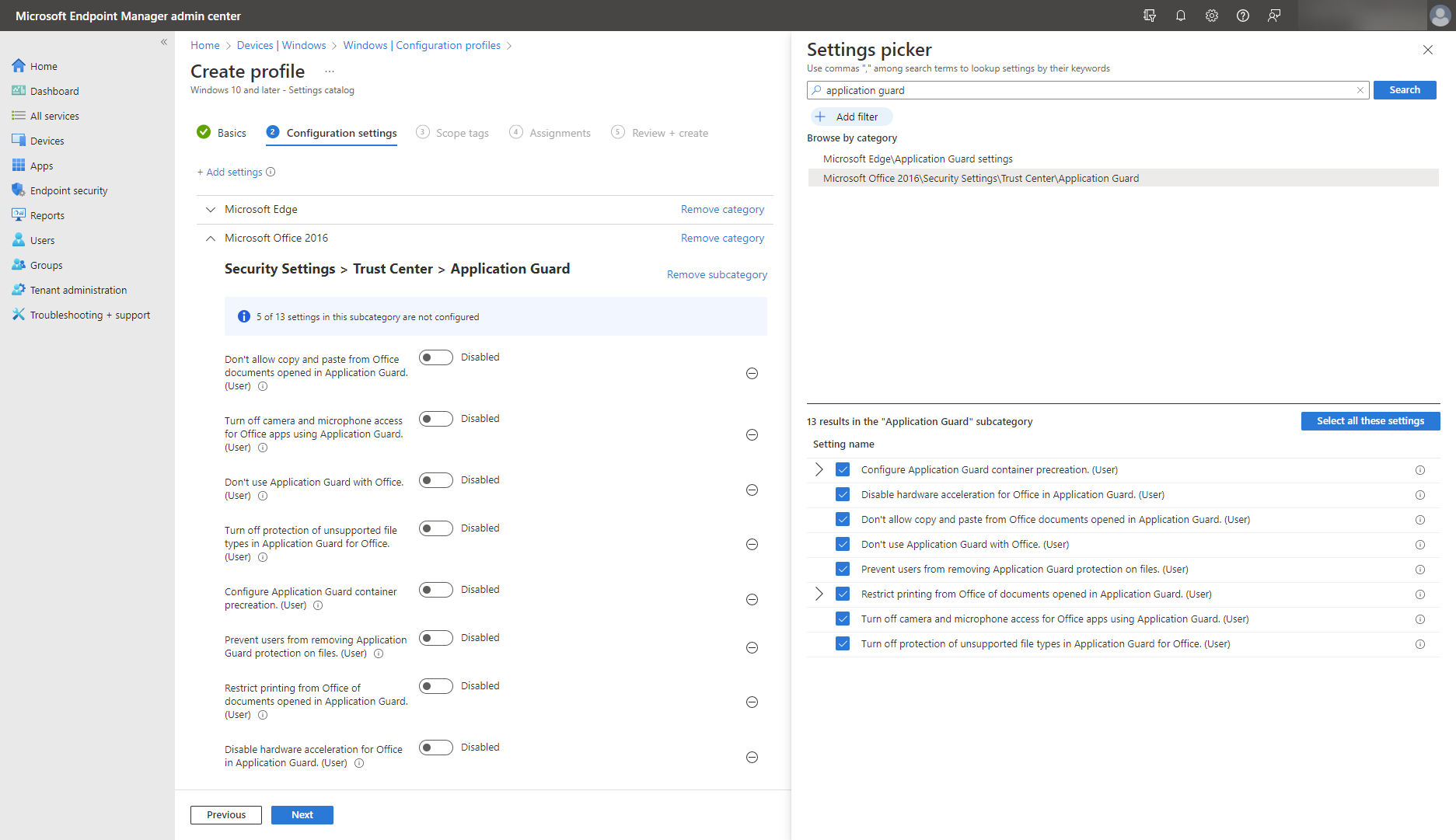
For Universal Windows Platform (UWP) applications, set up and configure Windows containers designed for Windows applications. This way, you enforce restrictions on network connectivity and make sure that applications have only limited access to the file system and registry. As a consequence, malicious code or infected apps will have fewer avenues for escape. Consider this additional level of security on your journey to advance your security posture.
User Account Control
Make sure that all your devices are configured for least privilege access, so that users don’t use admin accounts for everyday usage. Admin privileges should be protected. If they're compromised, malware would have more control over the device and potentially even gain control over other devices, platforms, and systems.
Implement User Account Control to ensure that your users stay productive, using the least privilege access needed to get their work done, and only when they need it. This way, apps always run in the security context of a non-administrator account, unless an admin explicitly authorizes admin-level access for the app. Users will be notified that an app needs admin permission to run, and the request to run has to manually be approved by an admin user.
You use UAC specific security policies to configure how User Account Control works in your organization. You can configure them in different ways, including security baselines and settings catalog in Intune, under the Local Policies Security Options.
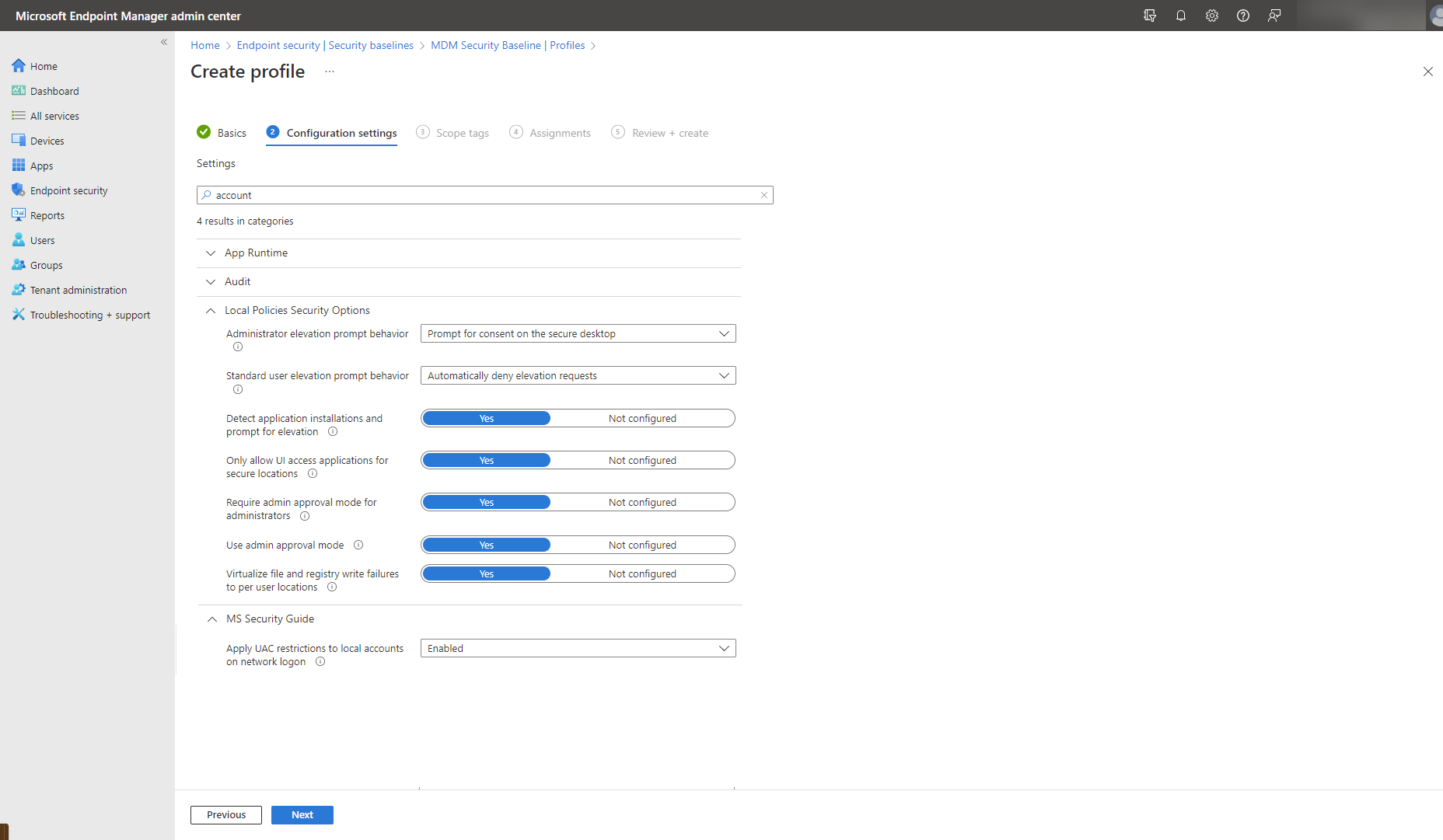
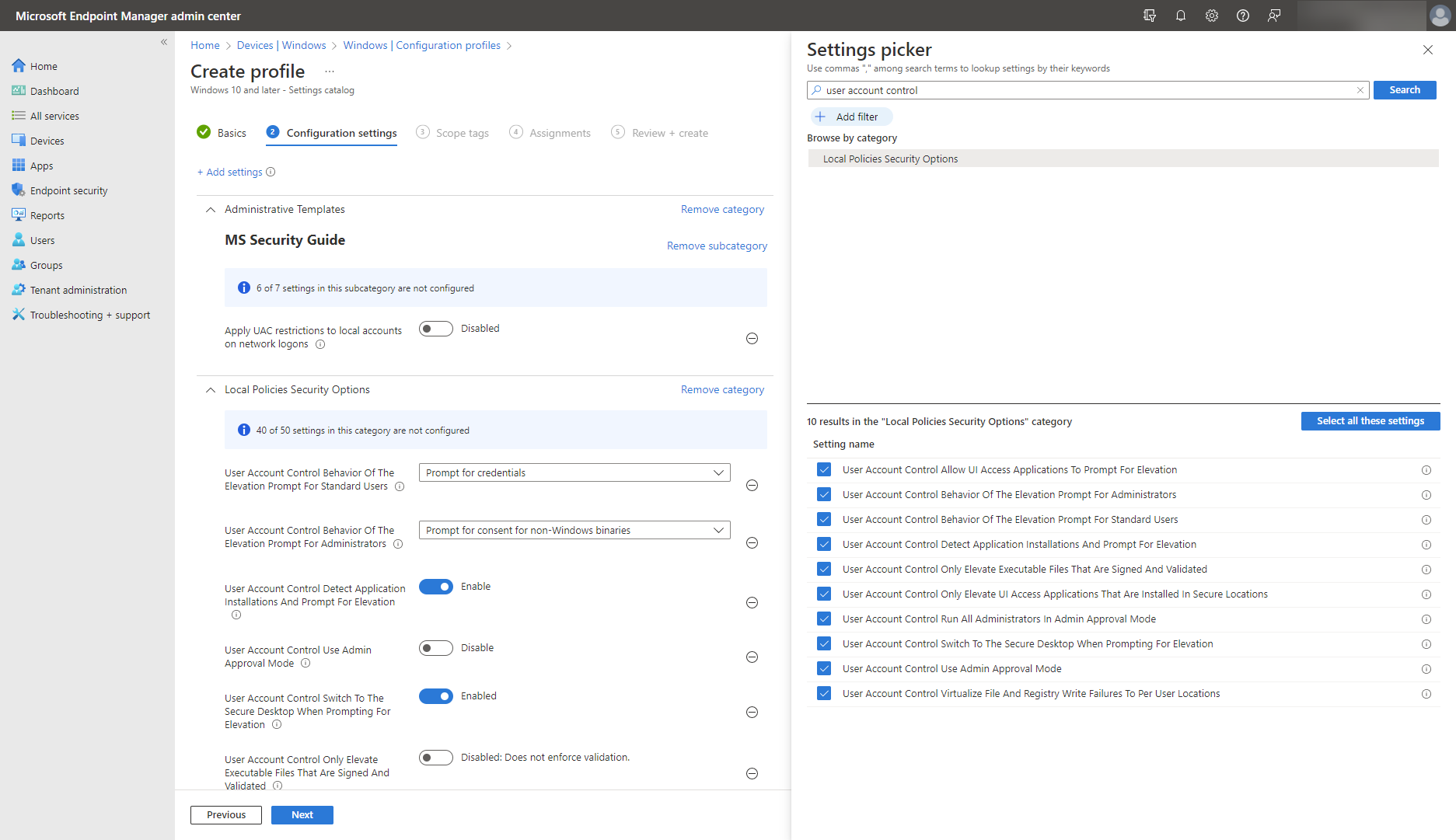
As an alternative to User Account Control, Windows Autopilot offers a new approach with a collection of technologies used to set up and pre-configure new devices, getting them ready for productive use and ensuring they're delivered locked down and compliant with corporate security policies. Learn more about Autopilot Device deployment for hybrid work.
