Don't forget to secure your hardware
In our modern world, the operating system alone can no longer protect devices from the wide range of attacks and techniques that cybercriminals use. These include physical, firmware, kernel attacks, and speculative execution techniques. The device’s hardware itself must now be secure down to its very core, including the chips and processors that store and handle sensitive information. A Zero Trust response will treat hardware components as untrustworthy. If any hardware component is compromised, the whole device, anything that runs on it, or connects to it, is consequently at risk. Let’s look at a set of hardware security features that help you advance your organization’s security posture.
Fortunately, updating and servicing your environment with security capabilities at the hardware level can help eliminate entire classes of vulnerabilities and threats for the device population and your organization more globally. Additionally, this can also mean considerable performance improvements as opposed to when the same security capabilities are implemented only in software. That improves productivity as a result.
The hardware-based security capabilities are meant to optimize your security posture improvement journey and will help you plan for and consistently increase your Microsoft Secure Score and your Zero Trust maturity level month to month (see the unit about continually improving your security posture). While most of these features are built in and automatically enabled in the latest Windows devices, some are configurable with Microsoft Intune. Let’s take a look.
Microsoft Pluton processor and TPM
Windows uses Trusted Platform Module (TPM) technology to provide hardware-based security-related functions, such as access control and authentication, including Windows Hello for Business and BitLocker. The industry standard today is the TPM 2.0 version, which has been a Windows policy requirement for new devices since 2016. Review the many security-related Windows features that require TPM and compare its current version with the previous version in TPM recommendations (Windows).
A TPM is a secure crypto-processor that performs cryptographic, key management, and system integrity measurement functionality in hardware that is isolated from other OS and application code running on the CPU. The isolation ensures that encryption keys and other sensitive information can’t be extracted even if the attacker has somehow found a way to install malware or has taken physical possession of the PC. The newest CPU-embedded Microsoft Pluton security processor supports the TPM standard and can be used as the TPM 2.0 for the PC. Regardless of whether Pluton is used as the TPM for a system, it can separately provide hardware protection for Windows scenarios that have requirements beyond what TPM 2.0 is capable of today. Additionally, Pluton is integrated with the Windows Update service, which means it’s automatically kept up to date with security updates directly from Microsoft. This is one example of how servicing and security are connected at the chip level. If these are important to you, then ask your original equipment manufacturer (OEM) about Pluton support on their devices. If you're using a device built for Windows 11 specifically, then you'll automatically benefit from having a built-in TPM 2.0, providing a great starting point with Zero Trust security posture. Otherwise, consider upgrading to a TPM 2.0-enabled device with your OEM or enabling TPM 2.0, if it's present but not enabled in your device's BIOS settings.
Dynamic Root of Trust for Measurement (DRTM)
In older versions of Windows, attackers would sometimes use what is referred to as a boot kit or rootkit to carry out malware attacks on firmware and evade detection. This is malicious software that would run before Windows starts, or during the boot process itself, ensuring that the malicious code has the highest level of privilege on the device.
Dynamic Root of Trust for Measurement (DRTM) is a technology that protects the bootup of your devices allowing the system to freely follow the normal UEFI Secure Boot process. However, before launching, the system enters a hardware controlled trusted state that forces the CPU(s) down a hardware-secured code path. If a malware rootkit/bootkit has bypassed UEFI Secure Boot and resides in memory, DRTM will prevent it from accessing secrets and critical code protected by the virtualization-based security environment. On the servicing end, the simplicity of the underlying measurements allows future updates to be deployed more widely and quickly to all of your devices using DRTM.
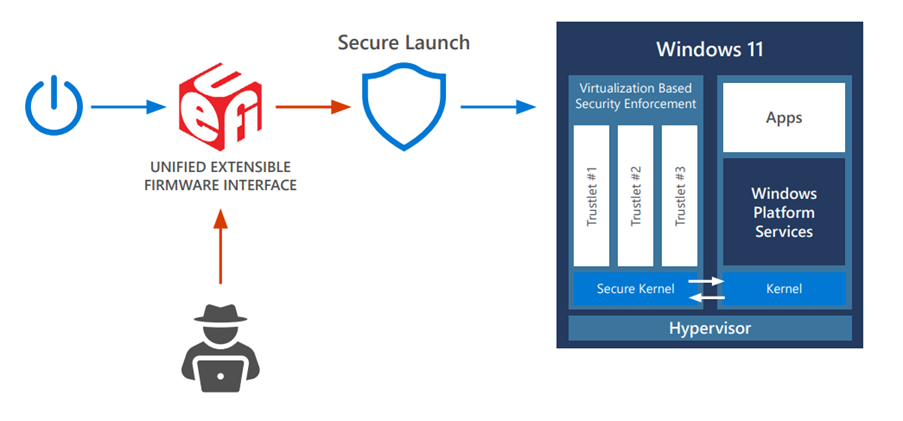
The device is turned on, allowed to go into the normal boot process. It’s then put through the secured code path through Secure Launch. This then ensures that critical code and information has been kept separate using VBS."
To use DRTM, check system requirements, configure, and run Windows Defender System Guard Secure Launch. Use Intune’s security baselines to Launch system guard, as captured below:
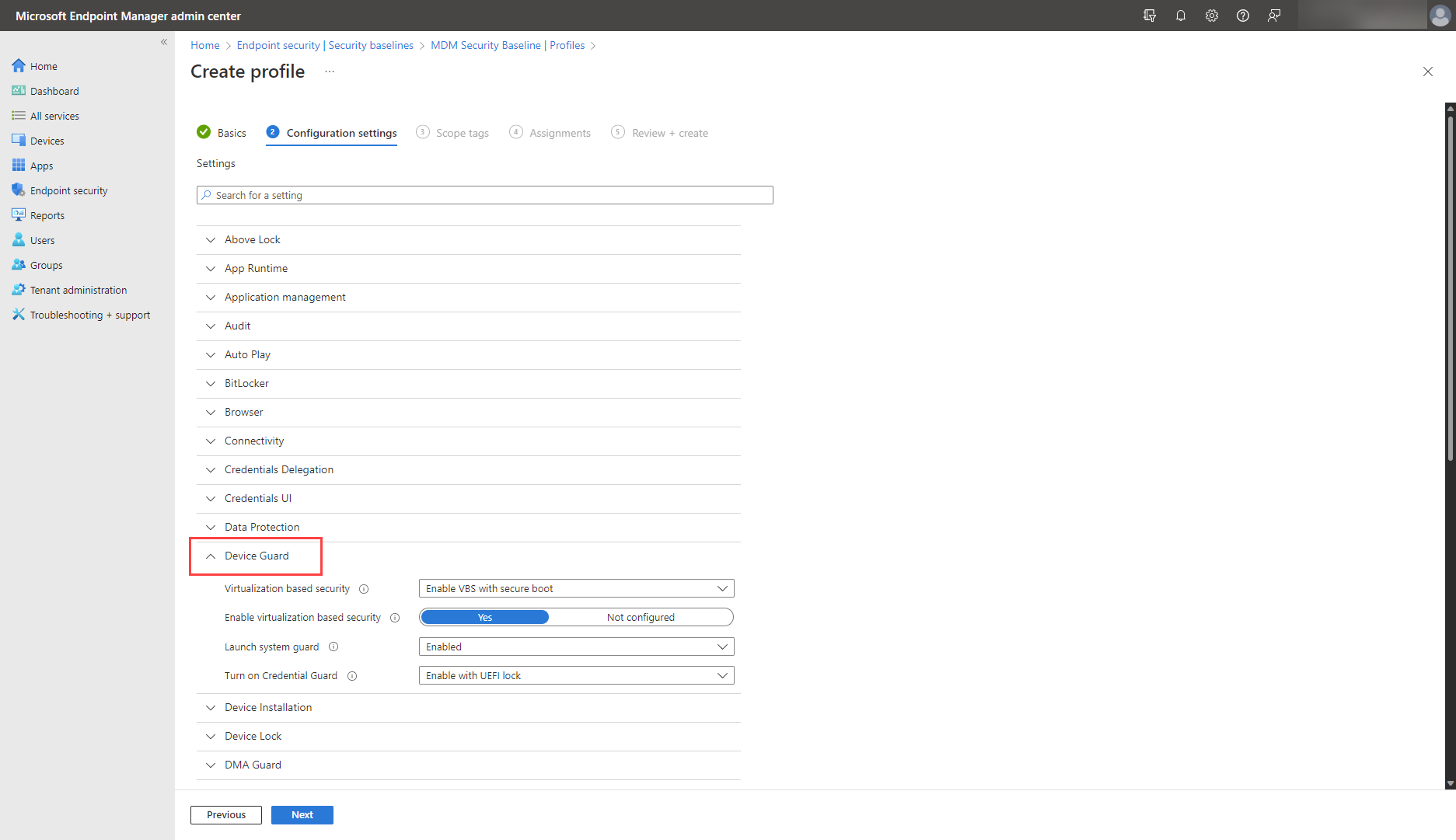
Alternatively, use Intune’s settings catalog to Configure System Guard Launch, as shown:
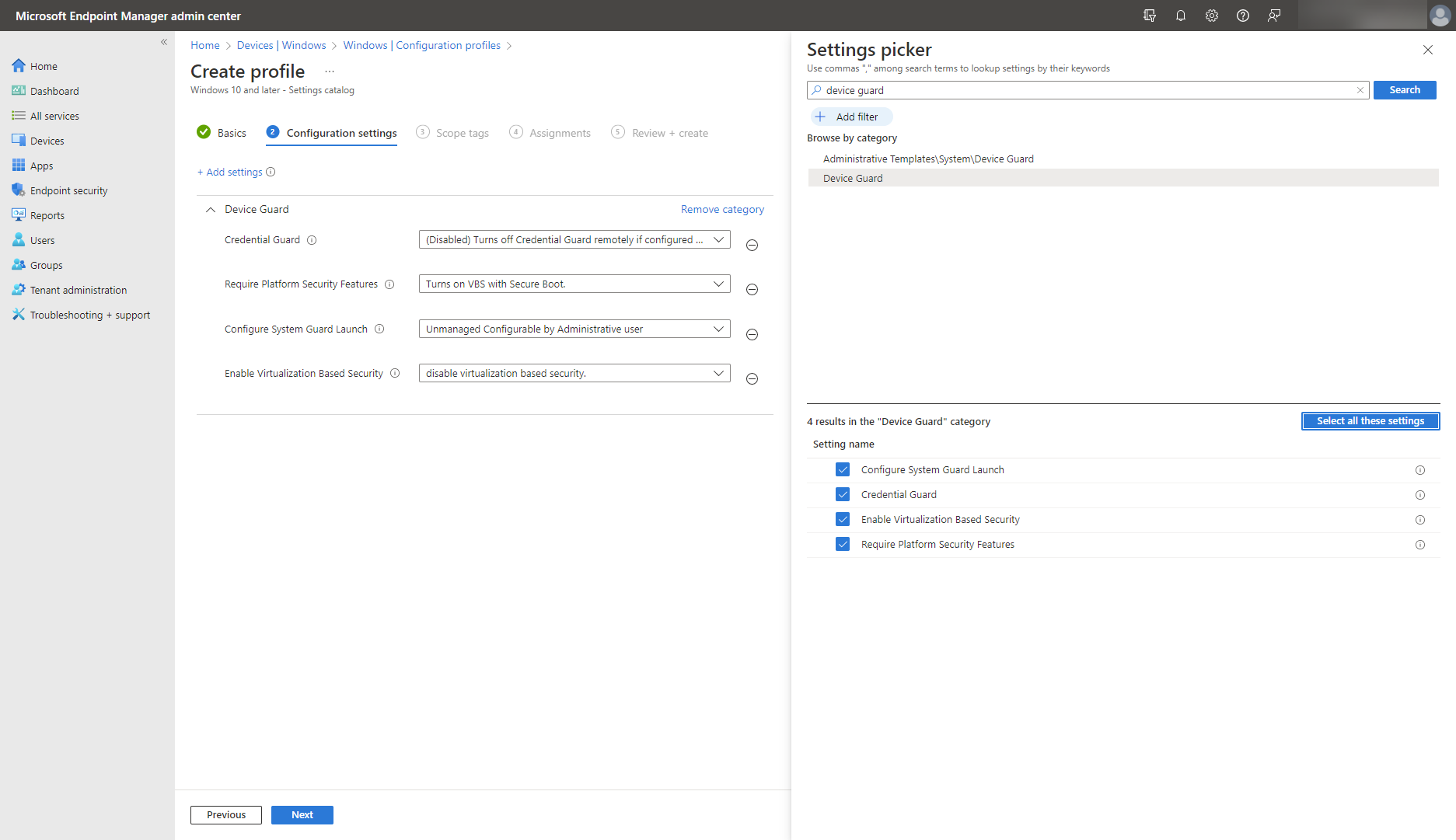
To verify that Secure Launch is running, use System Information (MSInfo32):
- Select Start.
- Search for System Information.
- Look for Secure Launch under Virtualization-based Security Services Running and Virtualization-based Security Services Configured.
Memory integrity
Memory integrity, also known as hypervisor-protected code integrity (HVCI), uses virtualization-based security (VBS) to run Kernel Mode Code Integrity (KMCI) inside the secure VBS environment instead of the main Windows kernel. The CPU’s hardware virtualization instructions are used to create a secure memory region that is separate and isolated from the normal operating system on your devices. This isolated memory region is enabled together with Secure Boot and allows you to check the integrity of all kernel code before it's allowed to run. As a result, you can prevent malicious code injection, even if drivers and other kernel-mode software have bugs or experience admin-level attacks like WannaCry, and ultimately protect sensitive operating system functions.
Prepare for the best performance of memory integrity, ensuring your devices have:
- Hypervisor support
- A minimum of 4 GB RAM (8 GB strongly recommended)
- UEFI Secure Boot
- TPM 2.0 strongly recommended
- Preferably, systems with CPUs that support Mode Based Execution Control
- Ideally, a Windows Defender Application Control (WDAC) policy deployed at the same time, covered in the unit on application security.
Configure memory integrity for strong runtime protection of the Windows kernel even against admin-level attacks.
Enable virtualization-based protection of code integrity on compatible devices in Intune, using the Code Integrity node in the AppLocker CSP or using custom OMA-URI with the Policy CSP - VirtualizationBasedTechnology. Settings catalog and security baselines can be initially configured in the Device Guard category in Intune, together with the System Guard Launch.
While most new Windows devices will come with HVCI switched on by default, servicing makes it possible for you to turn it on for your devices in various ways, including through Windows Security app, an MDM provider, Group Policy, or registry configuration.
Secured-core PCs
A considerable majority of enterprises report that they've experienced at least one firmware attack in the last two years. It can be difficult for organizations to keep up and fully carry out what needs to be done to prevent and respond to such attacks as they continue to arise. Secured-core PCs help achieve optimal hardware security. They're especially recommended for those in organizations in sensitive industries like healthcare or finance.
Produced in collaboration between Microsoft and chip manufacturers, Secured-core PCs come already preconfigured with the most advanced security measures that protect Windows 11 devices at the core. For example, Secured-cored PCs will have Windows Defender System Guard Secure Launch configured and automatically enabled to ensure DRTM is running when the device is started (see the DRTM section). They also have built-in hypervisor-protected code integrity (HVCI) enabled to ensure that all operating system code is trustworthy, and all executable code is signed by known and approved authorities only.
Use the Secured-core PC assessment guide for detailed guidance on how these features are configured and enabled for Secured-core PCs.
This selection of features shows that security at the chip level is serviced in ways that are largely invisible and, therefore, often forgotten: in device manufacturing, out-of-the-box preconfiguration, or automatic updates that you can trust.
With these improvements, your organization is advancing its Zero Trust maturity level at the hardware level.
