Ask Learn
PreviewPlease sign in to use this experience.
Sign inThis browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Microsoft 365 enables people from outside the Microsoft 365 organization to collaborate with users within the organization. It does so through B2B collaboration, which is a feature within Microsoft Entra External ID. With B2B collaboration, you can securely share your company's applications and services with external users, while maintaining control over your own corporate data. With B2B collaboration, you can work safely and securely with external partners, large or small, even if they don't have Microsoft Entra ID or an IT department.
With B2B collaboration, an external user is invited to sign in to your Microsoft Entra organization using their own credentials. This B2B collaboration user can then access the apps and resources you want to share with them. A user object is created for the B2B collaboration user in the same directory as your employees. B2B collaboration user objects have limited privileges in your directory by default, and they can be managed like employees, added to groups, and so on.
A simple invitation and redemption process lets partners use their own credentials to access your company's resources. You can also enable self-service sign-up user flows to let external users sign up for apps or resources themselves. Once the external user redeems their invitation or completes sign-up, they're represented in your directory as a user object. The user type for these B2B collaboration users is typically set to "guest" and their user principal name contains the #EXT# identifier.
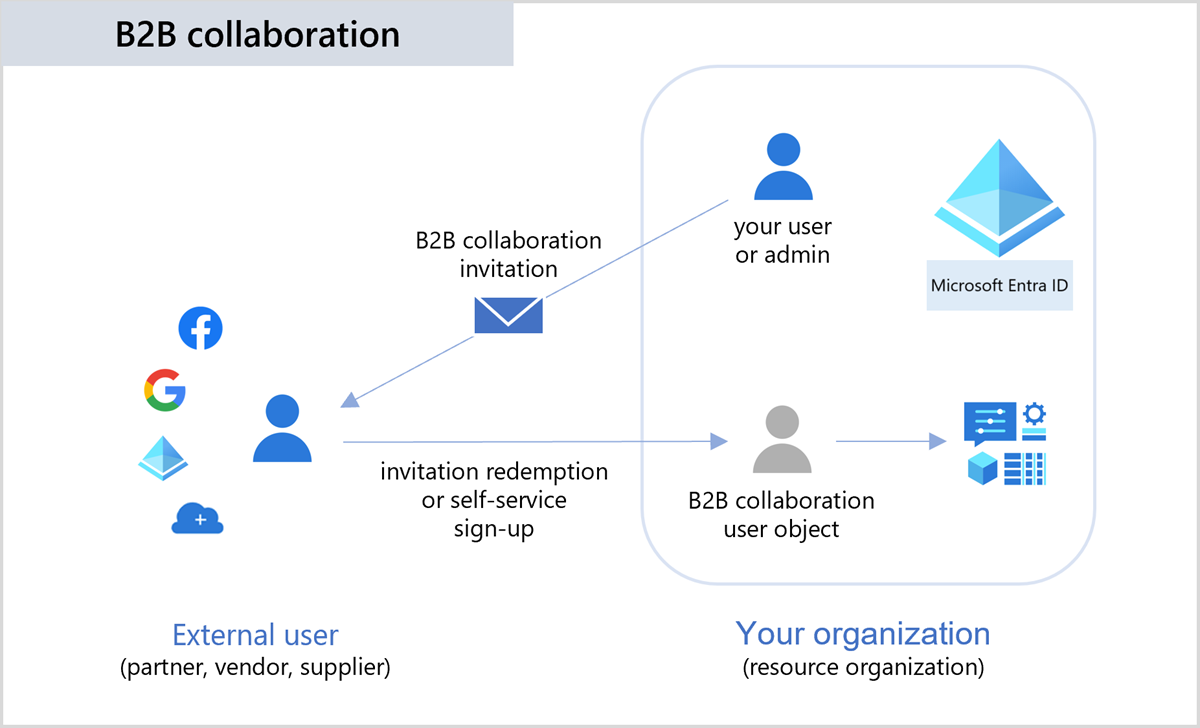
The following list describes B2B collaboration users based on how they authenticate (internally or externally) and their relationship to your organization (guest or member):
Being able to easily share files and documents with the right people while preventing oversharing requires planning. The following resources provide more background to help you create a secure guest sharing environment in Microsoft 365.
In addition to Microsoft Teams and SharePoint, Microsoft 365 also supports guest access in other applications. The following Microsoft 365 products support guest access.
Microsoft Office applications like Microsoft Word and Excel control guest access by the location of the output file, such as Microsoft SharePoint, Teams, or OneDrive.
As a Microsoft 365 administrator, you must ensure the configuration of your organization's external collaboration settings enable guest user access. If you want to add a guest user, an administrator must first assign you a role that allows you to create users in your tenant directory. Examples of such roles include a Global Administrator role or a limited administrator directory role, such as a Guest Inviter or User Administrator.
Note
Organizations can configure their external collaboration policies to prevent certain types of users or administrators from inviting guests. To find out how to view and set these policies, see Enable B2B external collaboration and manage who can invite guests.
Administrators can invite guest users to their organization's Microsoft Entra ID, to a group, or to an application. After they invite a person through any of these methods, the system adds the invited user's account to the organization's Microsoft Entra ID with a user type of Guest*.* The guest user must then redeem their invitation before they can begin collaborating with organizational users.
After an administrator adds a guest user to the organization's Microsoft Entra ID, the guest user can select either:
When an organization adds a guest user to its Microsoft Teams, SharePoint, or Microsoft Entra ID, the system automatically adds the user to the Guest users list in the Microsoft 365 admin center. Once a user shows up in the Guest users list, you can remove their access there as well. After you add a guest user in Microsoft Entra ID, you can assign them to a group, or give them access to an app in your organization.
By default, Microsoft 365 turns on guest access for an organization's Microsoft 365 groups. The Microsoft 365 Administrator controls whether to allow guest access to groups for the whole organization or for individual groups.
To view guest users in the Microsoft 365 admin center, expand Users in the left-hand navigation pane and then select Guest users.
The user profile for a Microsoft Entra B2B collaboration user includes the following key properties:
User Principal Name (UPN). The UPN for a B2B collaboration user object contains a #EXT# identifier.
User type. The UserType property indicates the relationship of the user to the host tenancy. This property can have two values:
Note
The UserType property has no relation to how the user signs in, the directory role of the user, and so on. This property simply indicates the user's relationship with the host organization and allows the organization to enforce policies that depend on this property.
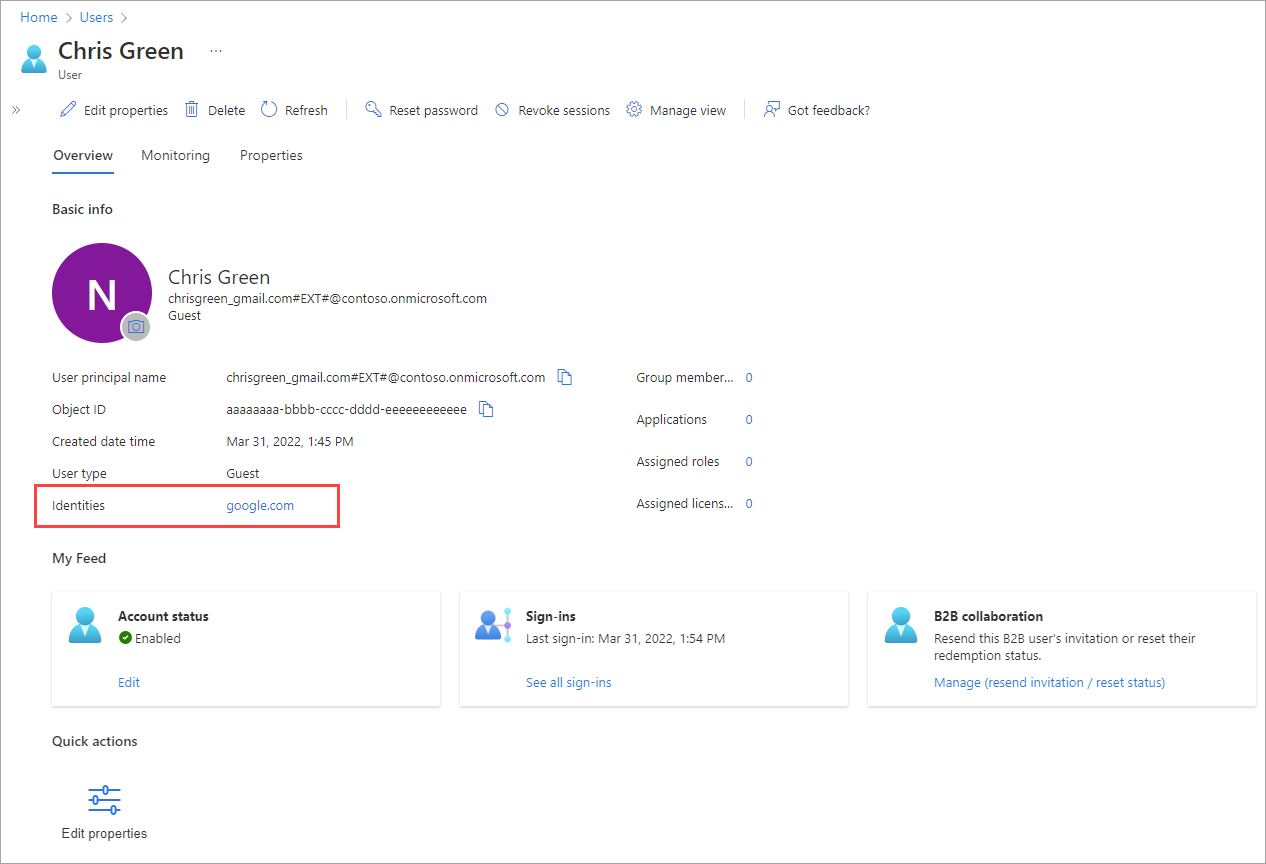
Identities. This property indicates the user's primary identity provider. A user can have several identity providers, which can be viewed by selecting the link next to Identities in the user's profile or by querying the Identities property through the Microsoft Graph API. Identities and UserType are independent properties.
| Identities property value | Sign-in state |
|---|---|
| ExternalAzureAD | This user is homed in an external organization and authenticates by using a Microsoft Entra account that belongs to the other organization. |
| Microsoft account | This user is homed in a Microsoft account and authenticates by using a Microsoft account. |
| {host's domain} | This user authenticates by using a Microsoft Entra account that belongs to this organization. |
| google.com | This user has a Gmail account and signed up by using self-service to the other organization. |
| facebook.com | This user has a Facebook account and signed up by using self-service to the other organization. |
| This user signed up by using Microsoft Entra External ID email one-time passcode (OTP). | |
| {issuer URI} | This user is homed in an external organization that doesn't use Microsoft Entra ID as their identity provider, but instead uses a Security Assertion Markup Language (SAML)/WS-Fed-based identity provider. The issuer URI is shown when the Identities field is clicked. |
Note
A value in Identities doesn't imply a particular value for UserType.
Microsoft Entra ID enables organizations to restrict what data guest users can see. Microsoft Entra ID sets guest users to a limited permission level by default, while the default for member users is the full set of user permissions. There's another guest user permission level in your organization's Microsoft Entra external collaboration settings for even more restricted access. The guest access levels include:
| Permission level | Access level |
|---|---|
| Same as member users | Guests have the same access to Microsoft Entra resources as member users. |
| Limited access (default) | Guests can see membership of all nonhidden groups. |
| Restricted access | Guests can't see membership of any group. |
When a guest user's permission level is set to Restricted access, they can view only their own user profile. They don't have permission to view other users, even if the guest searches by User Principal Name or objectId. Restricted access also restricts guest users from seeing the membership of groups they're in.
Note
There are no licensing requirements to restrict guest access.
External collaboration settings let an organization specify what roles it can invite guest users for B2B collaboration. These settings also include options for allowing or blocking specific domains, and options for restricting what guest users can see in your Microsoft Entra admin center. The following options are available:
For B2B collaboration with other Microsoft Entra organizations, you should also review your cross-tenant access settings. Doing so ensures your inbound and outbound B2B collaboration. It also scopes access to specific users, groups, and applications.
To update guest access permissions in Microsoft Entra ID, perform the following steps:
B2B collaboration user accounts are the result of inviting guest users to collaborate by using the guest users' own credentials. When the invitation is initially sent to the guest user, an account is created in your tenant. This account doesn't have any credentials associated with it because authentication is performed by the guest user's identity provider. The Identities property for the guest user account in your directory is set to the host's organization domain until the guest redeems their invitation. The user sending the invitation is added as a default value for the Sponsor (preview) attribute on the guest user account. In the admin center, the invited user's profile shows an External user state of PendingAcceptance.
Note
Guest user invitations don't expire. For more information about the redemption process, see B2B collaboration invitation redemption.
After the B2B collaboration user accepts the invitation, the Identities property in the user's profile is updated based on the user's identity provider.
Note
The directory sync information is also available through the onPremisesSyncEnabled property in Microsoft Graph.
To add guest users to your organization's Microsoft Entra ID, perform the following steps:
Sign into Microsoft 365 as a Global Administrator or a user with a limited administrator directory role or the Guest Inviter role.
On the Microsoft 365 admin center, select Show All in the navigation pane.
Under the Admin centers group in the navigation pane, select Identity.
In the Microsoft Entra admin center, in the left-hand navigation pane, select Users, and then select All users.
On the Users window, select +New user on the menu bar. In the drop-down menu that appears, select Invite external user.
On the Invite external user page, under the Basics tab, enter the guest user's Email address and Display name. You can optionally send an invitation message, which you can also enter here, along with the email address of a recipient you wish to CC.
You can optionally select the Properties tab to enter the external user's full name and job information.
You can also select the Assignments tab to assign the external user to existing groups, or to add security roles to the user account.
Note
The system doesn't support Group email addresses. Instead, enter the email address for an individual. Also, some email providers allow users to add a plus symbol (+) and other text to their email addresses to help with things like inbox filtering. However, Microsoft Entra ID doesn’t currently support plus symbols in email addresses. To avoid delivery issues, omit the plus symbol and any characters following it up to the @ symbol.
When you're ready to send the invitation, select the Review + Invite button. Doing so displays the Review + invite tab, which shows you whether any required information is missing. When everything looks OK, select Invite to automatically send the invitation to the guest user.
After you send the invitation, the system automatically adds the user account to the directory as a guest. It adds the guest user account with a user principal name (UPN) in the format emailaddress#EXT#@domain. For example, john_contoso.com#EXT#@fabrikam.onmicrosoft.com, where fabrikam.onmicrosoft.com is the organization from which you sent the invitation.
To manually add a guest user to a group, perform the following steps:
You can also use dynamic groups with Microsoft Entra B2B collaboration. For more information, see Dynamic groups and Microsoft Entra B2B collaboration.
To add guest users to an application, perform the following steps:
Having an issue? We can help!
Please sign in to use this experience.
Sign in