Elevate privileges using Microsoft Entra Privileged Identity Management
Microsoft Entra Privileged Identity Management (PIM) enables organizations to manage, control, and monitor user access. PIM provides access to resources in Microsoft Entra ID, Azure resources, and other Microsoft online services like Microsoft 365 and Microsoft Intune.
Microsoft Entra Privileged Identity Management provides organizations with the following benefits:
- It identifies the users assigned privileged roles to manage Azure resources.
- It identifies the users assigned administrative roles to manage Azure resources.
- It enables on-demand "Just in time" administrative access to:
- Microsoft online services like Microsoft 365 and Intune
- Azure resources
- Resource groups
- Individual resources such as virtual machines
- The organization can see a history of administrator activation, including changes administrators made to Azure resources.
- Organizations receive alerts about changes in administrator assignments.
- Users require approval to activate Microsoft Entra privileged admin roles.
- Organizations can review membership of administrative roles and require users to provide a justification for continued membership.
Note
You examine Privileged Identity Management in greater detail in the Learning Path titled Explore security metrics in Microsoft 365 Defender.
Just in time administrator access
Historically, an administrator assigns users to admin roles through the Microsoft Entra admin center, other Microsoft online services portals, or the Microsoft Entra cmdlets in Windows PowerShell. As a result, that user becomes a permanent admin, always active in the assigned role.
Besides these traditional Microsoft 365 administrator roles, the Microsoft Entra PIM service introduces the concept of an eligible administrator. Eligible admins are users that need privileged access periodically, but not all-day, every day. The role is inactive until the user needs access. At that point, the user must complete an activation process to become an active admin for a predetermined amount of time. Using this approach is becoming more common for organizations to reduce or eliminate “standing admin access” to privileged roles.
The following diagram shows how a regular user can use PIM to elevate privileges to selected administrative roles.
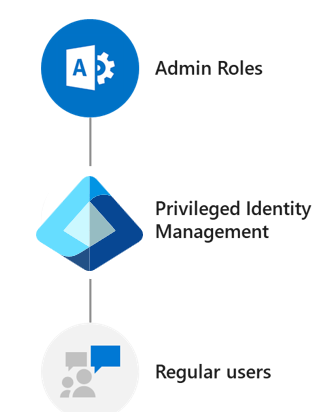
The Privileged Role Administrator
The Privileged Role Administrator (PRA) manages Microsoft Entra PIM and updates role assignments for other users. This role is critical role in maintaining effective privileged access management and ensuring the security and integrity of sensitive resources and data within an organization. The responsibilities and capabilities associated with the PRA role include:
- Managing Privileged Roles
- The PRA is responsible for defining and managing privileged roles within the organization.
- They identify the roles that require elevated privileges and determine the appropriate individuals or groups who should hold these roles.
- The PRA can assign, modify, and remove privileged roles based on business requirements and the principle of least privilege.
- Granting Just-in-Time (JIT) Access
- JIT access is a feature in PIM that allows temporary elevation of privileges to perform specific tasks for a limited time.
- The PRA configures JIT policies to define the tasks that require elevated access and the conditions for granting access.
- They review and approve or reject access requests from users who need temporary privileged access.
- Monitoring and Auditing Privileged Access
- The PRA is responsible for monitoring and auditing privileged access within the organization.
- They review access logs and reports to ensure compliance and identify any unauthorized or suspicious activities related to privileged accounts.
- The PRA takes necessary actions, such as revoking access or conducting further investigations, if the organization detects any anomalies or security incidents.
- Security and Compliance
- The PRA aligns privileged access with security and compliance policies.
- They collaborate with security teams to establish and enforce access controls, policies, and procedures related to privileged accounts.
- The PRA works to minimize security risks associated with privileged access and maintains a secure and compliant environment.
- Training and Documentation
- The PRA can also create documentation, guidelines, and training materials related to privileged access management.
- They educate other administrators and users about best practices, security measures, and proper usage of privileged accounts and roles.
The Privileged Role Administrator, as the designated administrator within PIM, has the authority to assign specific administrator roles to users within the organization. The PRA manages and controls privileged access by defining and assigning roles through PIM. They determine which users require elevated privileges for specific administrative tasks and assign them the appropriate roles.
PIM offers a range of built-in roles for common administrative tasks, such as Global Administrator, Exchange Administrator, SharePoint Administrator, and more. The PRA can assign these predefined roles to users or create custom roles tailored to the organization's specific needs.
Through the PIM interface, the PRA can:
- Review access requests from users.
- Approve or reject access requests based on established policies.
- Set the duration for which a user has elevated privileges.
The PRA ensures that organizations follow the principle of least privilege, granting elevated access only when necessary and for a limited time. The next unit examines the principle of least privilege.
In summary, the Privileged Role Administrator within PIM is responsible for:
- Assigning administrator roles to users.
- Managing user access requests.
- Ensuring the secure and controlled delegation of privileged access in Microsoft 365.
Additional reading. For more information, see Assign directory roles to users using Microsoft Entra PIM.
Request role activation
If you're eligible for an administrative role, then you must activate the role assignment when you need to perform privileged actions. For example, if you occasionally manage Microsoft 365 features, your organization's privileged role administrators might not make you a permanent Global Administrator, since that role also impacts other services. Instead, they would make you eligible for Microsoft Entra roles such as Exchange Online Administrator. You can request to activate that role when you need its privileges so that you have administrator control for a predetermined time period.
Important
When the PRA activates a role, Microsoft Entra PIM temporarily adds active assignment for the role. PIM creates active assignment (assigns user to a role) within seconds. When deactivation (manual or through activation time expiration) happens, PIM removes the active assignment within seconds as well. Application may provide access based on the role the user has. In some situations, application access may not immediately reflect the fact that user got role assigned or removed. If an application previously cached the fact the user doesn't have a role, the user may not receive access when they try to access the application again. Similarly, if an application previously cached the fact the user has a role, the user may still receive access if the role gets deactivated. Each specific situation depends on the application’s architecture. For some applications, signing out and signing back in may help get access added or removed.
When you need to assume a Microsoft Entra role, you can request activation by completing the following steps:
- Sign in to the Microsoft Entra admin center as at least a Privileged Role Administrator.
- In the Microsoft Entra admin center, under the Identity governance group in the navigation pane, select Privileged Identity Management.
- On the Privileged Identity Management | Quick start page, in the middle navigation pane under the Tasks group, select My roles.
- On the My roles page, the Eligible assignments tab is displayed by default. This tab displays the list of your eligible roles.
- Find the role you want to activate. Under the Action column for that role, select Activate.
- In the Activate pane that appears, select Additional verification required and follow the instructions to provide security verification. You must only authenticate once per session.
- After multifactor authentication, select Activate before proceeding.
- If you want to specify a reduced scope, select Scope to open the filter pane. On the filter pane, you can specify the Microsoft Entra resources that you need access to. It's a best practice to request access to the fewest resources that you need.
- If necessary, specify a custom activation start time. When you specify a start time, the system activates the role after the selected time.
- In the Reason box, enter the reason for the activation request.
- Select Activate.
- If the role requires approval to activate, a notification appears in the upper right corner of your browser informing you the request is pending approval.
Additional reading. For more information, see How to activate or deactivate roles in Privileged Identity Management.
Knowledge check
Choose the best response for the following question. Then select “Check your answers.”