Protect users from malicious URLs by using Safe Links
Safe Links is a feature in Microsoft Defender for Office 365 that provides:
- URL scanning and rewriting of inbound email messages in mail flow.
- Time-of-click verification of URLs and links in email messages and other locations.
Safe Links scanning occurs in addition to the regular anti-spam and anti-malware protection in inbound email messages in Exchange Online Protection (EOP). Safe Links scanning can help protect your organization from malicious links that attackers use in phishing attacks and other forms of attacks.
When an organization's mail system delivers to a recipient an email with an embedded URL, the web page or attachment on the other side of the link might be safe to view at the time of delivery. However, it might not be safe when the user opens the email and selects the link. Safe Links protects the user by rewriting the link in the message body. By doing so, Safe Links checks the link when the user selects it, rather than when the mail system received and delivered the message.
When a user selects a link in a message or document, Safe Links checks to see if the link is malicious. It does so by redirecting the URL to a secure server in the Microsoft 365 environment that checks the URL against a blocklist of known malicious web sites.
- If the site is safe, Safe Links redirects the browser to the original destination web site.
- If the site is on the blocklist, Safe Links blocks the user from continuing to the site. The browser then displays a warning page similar to the following image.
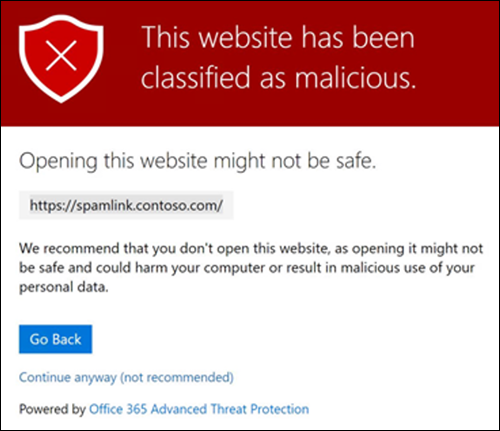
Safe Links is selective enough to remove only malicious links. Even within a single email, it only removes the malicious links. If there are other links that are safe, the user can select them and navigate to the target websites without interference.
Like Safe Attachments, Safe Links protects your organization according to policies your security administrators create. You can create and configure policies and apply them to specific people, groups, or domains.
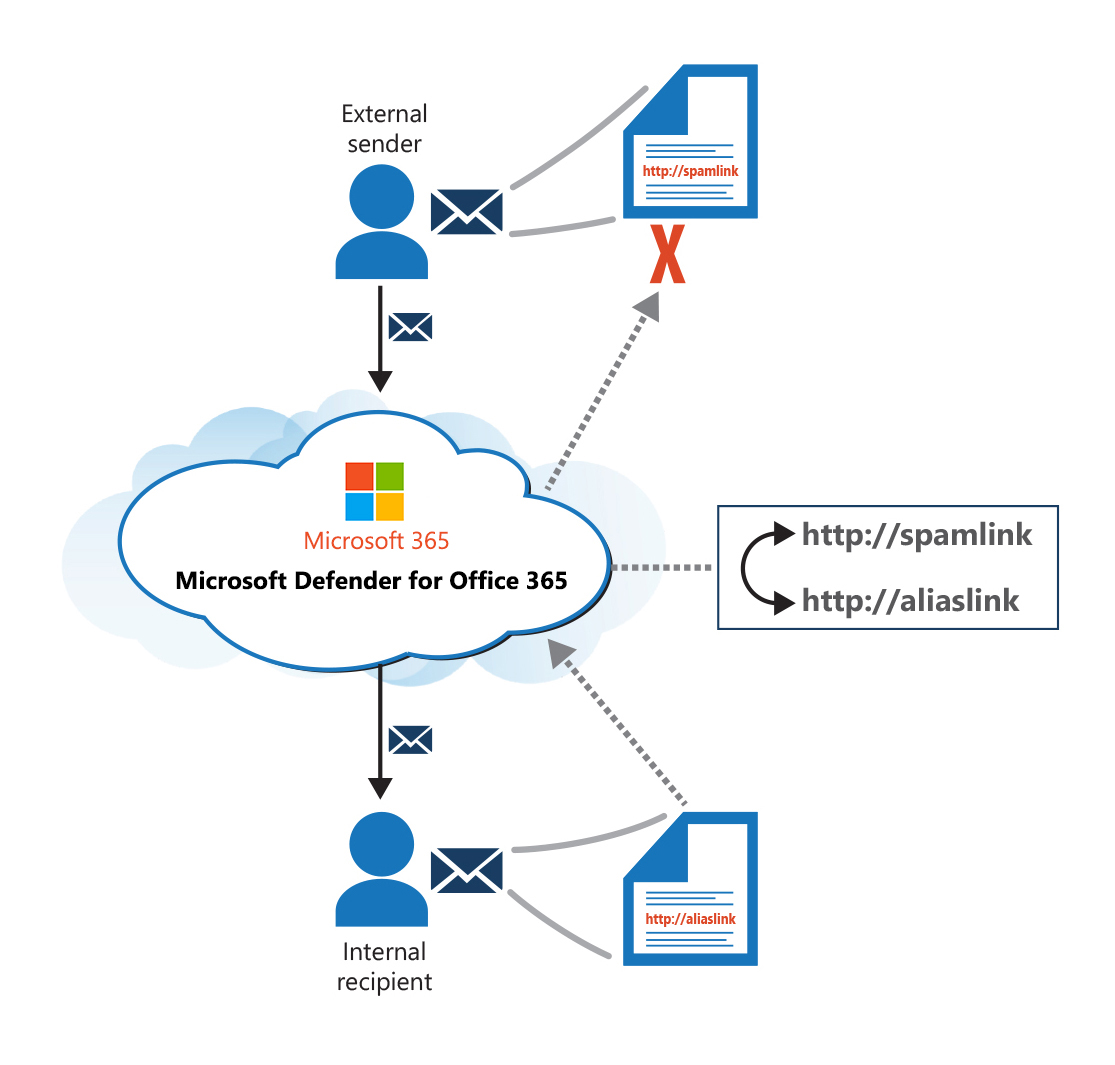
The following graphic shows how Microsoft Defender for Office 365 rewrites malicious links while in transport. If a recipient opens a dangerous link, the system doesn't redirect them to the original target. Rather, they connect to Microsoft Defender XDR.
Note
Microsoft Defender XDR is now Microsoft Defender XDR (Extended Detection and Response).
Safe Links protection is available in the following locations:
- Email messages. Similar to Safe Attachments, there's no default Safe Links policy. However, the Built-in protection preset security policy provides Safe Links protection to all recipients (users not specified in custom Safe Links policies). Organizations can also create Safe Links policies that apply to specific users, group, or domains.
- Microsoft Teams. Safe Links protection for links in Teams conversations, group chats, or from channels also controlled by Safe Links policies.
- Office 365 apps. Safe Links protection for Office 365 apps is available in supported desktop, mobile, and web apps. You configure Safe Links protection for Office 365 apps in the global setting that are outside of Safe Links policies. The Safe Links service applies protection for Office 365 apps to all organizational users licensed for Microsoft Defender for Office 365. This protection applies even for users not included in active Safe Links policies.
URL detonation
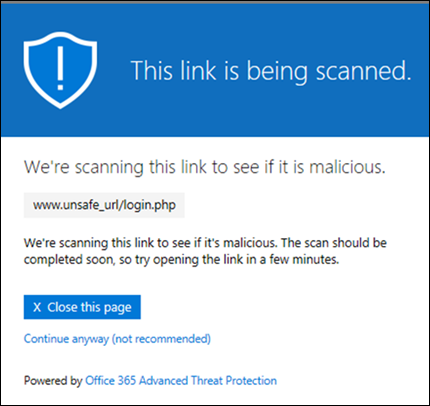
URL detonation is a capability that combines elements of Safe Links and Safe Attachments into a single feature. This feature protects users in the event a link points to a malicious file on a web server. When a user selects a link to a file on a web server, the system downloads the file into the Safe Attachments sandbox environment. The Safe Attachments then run service, or "detonates" the file so that it can analyze the content.
While Safe Attachments analyzes the content of the file, the system presents a web page to the user explaining that a scan is in process. If Safe Attachments ultimately determines the file to be malicious, Safe Links redirects the user to a warning page advising the user the site is malicious.
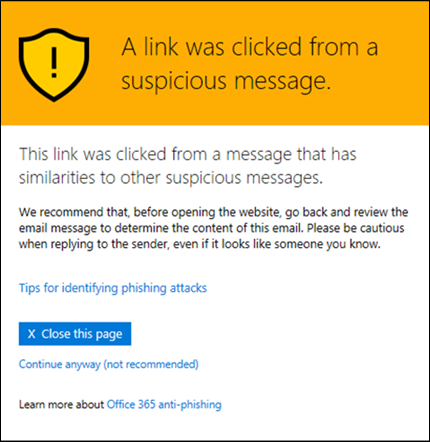
Suspicious message warning
When a user selects a URL in an email message that's similar to other suspicious messages, Safe Links displays the following warning message. You should instruct your users to double-check the email message before proceeding to the site.
Safe Links scenarios
The following table describes common scenarios for Safe Links in Microsoft 365 and Office 365 organizations that include Microsoft Defender for Office 365.
| Scenario | Result |
|---|---|
| Jean is a member of the Marketing department. The organization turned on Safe Links protection for Office 365 apps. A Safe Links policy that applies to members of the Marketing department also exists. Jean opens a PowerPoint presentation in an email message, and then selects a URL in the presentation. | An organization must create at least one Safe Links policy for any of its users to get Safe Links protection in inbound email messages. Safe Links protects Jean because the organization created a Safe Links policy for the Marketing department, of which Jean is a member. The organization also turned on Safe Links protection for Office 365 apps. For more information about the requirements for Safe Links protection in Office 365 apps, see Safe Links settings for Office 365 apps. |
| Manu's' Microsoft 365 E5 organization has no Safe Links policies configured. Manu receives an email from an external sender that contains a URL to a malicious website that Manu ultimately selects. | Safe Links doesn't protect any users in Manu's organization. An organization must create at least one Safe Links policy for any of its users to get Safe Links protection in inbound email messages. The organization must include Manu in the conditions of a policy for Manu to get Safe Links protection. |
| In Pat's organization, administrators didn't create Safe Links policies. However, the organization did turn on Safe Links protection for Office 365 apps. Pat opens a Word document and selects a URL in the file. | Safe Links doesn't protect any users in Pat's organization, even though the organization turned on Safe Links protection for Office 365 apps. Even with Safe Links protection for Office 365 apps turned On, the organization must still create at least one Safe Links policy for anyone to get Safe Links protection. Since no Safe Links policies exist, Pat isn't eligible for Safe Links protection. |
| Lee's organization added https://tailspintoys.com in the Block the following URLs list in the global settings for Safe Links. A Safe Links policy that includes Lee already exists. Lee receives an email message that contains the URL https://tailspintoys.com/aboutus/trythispage. Lee selects the URL. | Safe Links might automatically block the URL for Lee. it all depends on the URL entry in the list and the email client Lee used. For more information, see "Block the following URLs" list for Safe Links. |
| Jamie and Julia both work for contoso.com. A long time ago, admins configured Safe Links policies that apply to both Jamie and Julia. Jamie sends an email to Julia, not knowing the email contains a malicious URL. | Safe Links protects Julia if the Safe Links policy that applies to her also applies to messages between internal recipients. For more information, see Safe Links settings for email messages. |
Knowledge check
Choose the best response for the following question. Then select “Check your answers.”