Prepare for directory synchronization
Today, businesses are often becoming a mixture of on-premises and cloud applications. Users require access to applications both on-premises and in the cloud. This design requires the need to have a single identity across these various on-premises and cloud applications.
Provisioning is the process of:
- Creating an object based on certain conditions.
- Keeping the object up to date.
- Deleting the object when conditions are no longer met.
For example, when a new user joins an organization, the company enters the user into its Human Resources (HR) system. At that point, provisioning can create a corresponding user account in the cloud (Microsoft Entra ID), in on-premises Active Directory, and different applications the user needs access to. Identity provisioning enables the user to start work and have access to the applications and systems they need on day one.
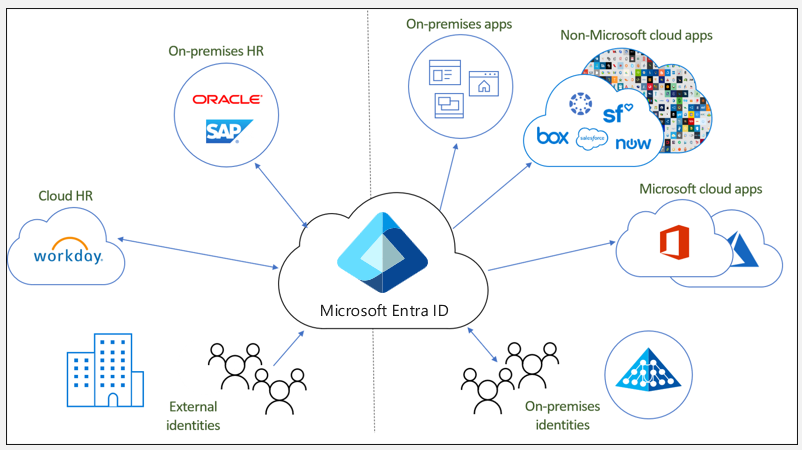
On-premises identity provisioning involves provisioning from on-premises sources (like Active Directory) to Microsoft Entra ID. The most common scenario occurs when a user in on-premises Active Directory is provisioned into Microsoft Entra ID. The system accomplishes identity provisioning through directory synchronization using either Microsoft Entra Connect Sync or Microsoft Entra Cloud Sync.
Before an organization deploys directory synchronization to synchronize its on-premises Active Directory objects to Microsoft Entra ID, it must prepare its environment by analyzing the following features:
- On-premises Active Directory preparation
- UPN suffixes
- Microsoft 365 IdFix tool
Consider activating directory synchronization as a long-term commitment. After an organization activates directory synchronization, it can only edit synchronized objects using on-premises Active Directory management tools.
On-premises Active Directory preparation
When an organization prepares to deploy directory synchronization, it must first prepare its on-premises Active Directory. To prepare Active Directory for directory synchronization with Microsoft Entra ID, an organization must:
- Identify the source of authority
- Clean-up Active Directory
- Set up auditing
Source of authority
For directory synchronization, source of authority refers to the location where Active Directory service objects, such as users and groups, are mastered in a cross-premises deployment. Where an object is mastered refers to the original source that defines copies of an object. Organizations can change the source of authority for an object by using one of these scenarios:
- Activate
- Deactivate
- Reactivate directory synchronization from within Microsoft 365 or with Windows PowerShell
Note
Once the system synchronizes an object, its source of authority transfers from Microsoft 365 to the organization's on-premises directory service.
Active Directory cleanup
To help ensure a smooth transition to Microsoft 365 by using directory synchronization, an organization should prepare its Active Directory forest before it begins its Microsoft 365 directory synchronization deployment.
An organization's directory remediation efforts should focus on the following tasks:
- Remove duplicate proxyAddresses and userPrincipalName
- Update blank and invalid userPrincipalName attributes with valid userPrincipalName
- Remove invalid and questionable characters in the following attributes:
- givenName
- surname (sn)
- sAMAccountName
- displayName
- proxyAddresses
- mailNickname
- userPrincipalName
UPN suffixes
Before an organization deploys directory synchronization, it should verify that:
- Its on-premises user objects in Active Directory have a UPN suffix configured. The UPN suffix is the part of a UPN to the right of the @ character; for example, @adatum.com and @contoso.com.
- The UPN suffix value is correct for both the Active Directory domain and Microsoft 365.
When an Internet routable domain is used as the UPN, then this domain should be the UPN suffix. In doing so, the users' principal names should be in the form user@domain. If the on-premises UPN suffix doesn't contain an Internet routable DNS domain (such as adatum.local), the default routing domain (for example, adatum.onmicrosoft.com) is used for the UPN suffix in Microsoft 365.
Tip
As a best practice, Microsoft recommends using the primary SMTP email address of each user as their UPN. The reason for this recommendation is that several applications, such as Skype for Business, ask for the email address in their sign-in window. Since they technically require the UPN sign-in name, using the primary SMTP email as their UPN address can reduce confusion.
If you must change the UPN suffix in the on-premises Active Directory, it's important to check for any applications that are dependent on a specific UPN.
If directory synchronization is deployed, the user’s UPN for Microsoft 365 might not match the user’s on-premises UPN defined in Active Directory. This mismatch can occur if an administrator assigned the user a Microsoft 365 subscription license before the domain was verified. To resolve this issue, the administrator can use Windows PowerShell to update users’ UPNs in Microsoft 365. This resolution ensures each user's Microsoft 365 UPN matches their corporate user name and domain in the on-premises Active Directory.
Microsoft 365 IdFix tool
The IdFix DirSync Error Remediation tool identifies and fixes most of the object synchronization errors in Active Directory forests. Organizations should run this tool in preparation for identity synchronization to Microsoft 365. This remediation enables an organization to successfully synchronize users, contacts, and groups from its on-premises Active Directory into Microsoft 365.
The IdFix tool queries all the Active Directory domains in the currently authenticated forest. It then displays object attribute values the directory synchronization tool would report as errors. The IdFix tool displays these object attribute values in a data grid. This design supports the ability to scroll, sort, and edit the objects.
Depending on the method of use, the Microsoft 365 IdFix tool provides:
- Confirmation that each change is enforced. IdFix displays a list of objects that have potential errors. An admin should review the list and select the objects they want the IdFix tool to fix. IdFix only changes the selected objects.
- Transaction rollback. IdFix can undo confirmed updates to object attributes applied to the forest.
- Well-known exclusions. Organizations might not want all Active Directory objects available for editing. The reason for identifying these exclusions is that edits to some objects could harm the source environment, such as critical system objects. IdFix excludes these objects from its data grid.
- Save to File. IdFix exports data into CSV or LDF format for offline editing or investigation.
- Import of CSV. IdFix imports data from a CSV file. Because this function relies upon the distinguishedName attribute to determine the value to update, the recommended method to use this feature is to export from a query, such as the Save to File. Keep the other columns as they were and don't introduce escape characters into the values.
- Verbose logging. Because the Microsoft 365 IdFix tool makes changes in an organization's environment, the system enables verbose logging by default.
- Support for multi-tenant and dedicated Microsoft 365 tenants. Depending on an organization's environment, the Microsoft 365 IdFix tool supports validation of multiple or dedicated Microsoft 365 tenants.
Warning
Organizations should use the IdFix tool with caution because it enables changes to bulk-update objects.
Knowledge check
Choose the best response for the following question. Then select “Check your answers.”