Describe different ransomware entry points
The high-reward, low-risk nature of ransomware has seen an escalation in the number of cybercriminals looking to get rich quickly by seeking out and exploiting your security vulnerabilities, increasing the volume of attacks.
Every attack has a point of entry. The entry point for any cyberattack is where it breaches your security defenses. Until then, the cybercriminal is just probing your security, looking for a weakness.
By strengthening and bolstering the most common entry points, you can plug the holes to improve your overall security position and prevent attacks. The diagram below shows some of the more common entry points a cybercriminal may look to attack.
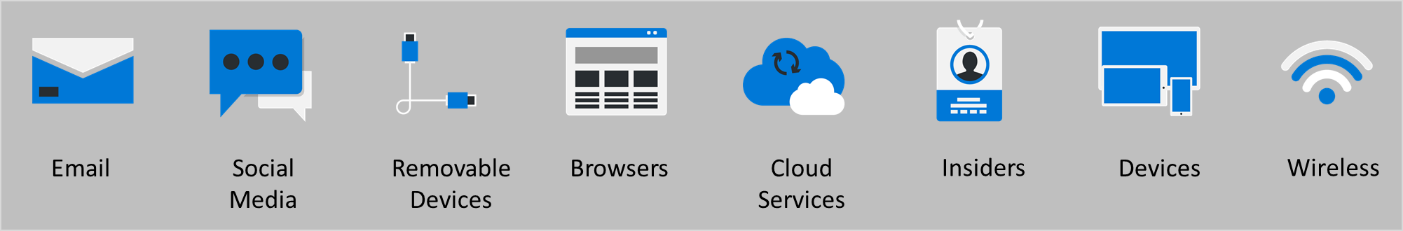
The most common attack vector is email. A cybercriminal sends a seemingly legitimate email resulting in the recipient taking action. This action might include selecting a link that allows the device to be compromised, or unwittingly downloading ransomware.
Wireless networks
Another attack vector used by cybercriminals is wireless networks. A cybercriminal will find an unsecured wireless network, for example, at an airport or conference, and use it to exploit vulnerabilities in any devices that access it.
Remote access services
With an increase in the number of people working from home, cybercriminals have been targeting services that allow remote access to secure networks. For example, by using remote desktop protocol (RDP) software to access another computer or virtual private network (VPN) to provide a secure connection to your work servers.
Insiders
Even with the best technological security systems, it can be argued that people represent the most easily exploitable link in your defenses. For example, an individual might accidentally leave their laptop or smart device on the train, or it might get stolen. In both cases, any data on the device and the device itself can allow a cybercriminal to gain access to your systems. Another factor to consider is the disgruntled employee, who willingly infects your devices before leaving. However, it's more often the case that simple human error provides the means for a cyberattack to take place.
Social engineering
Social engineering uses deception to manipulate users into revealing private and personal information. For example, many popular heist movies have a point where they need to fool a security guard into giving up something like a security card, or their personal information, without realizing they've done it. Cybercriminals use these social engineering techniques to befriend people to get what they want. Another typical social engineering attack happens when the cybercriminal aims to gain the trust of an authorized user by posing as a person of authority. For example, a cybercriminal pretends to be a support engineer who tricks the user into revealing their credentials.
There are dozens of different types of social engineering attacks, and the outcome is always the same. To elicit or obtain information that allows the cybercriminal to continue their attack.
Case study – a private hospital
The following outlines the attack:
- The target was a private acute care hospital in the United States.
- The attackers were never identified, and no one claimed responsibility.
- The cybercriminals used a phishing attack as an entry point to gain credentials to the hospital systems, allowing the ransomware to be installed.
- The impact of the attack stopped the day-to-day running of the hospital because all patient data and critical administrative systems were unavailable to doctors and nurses.
- To resolve the situation, the hospital paid a Bitcoin ransom of $3.4 million. This was the most efficient way to restore their administrative systems and the regular functioning of the hospital and the patients in its care.
The response:
- The hospital reported the incident to the Federal Bureau of Investigation (FBI) and the local state police department, who began an investigation into the attack. At the time, the FBI recommended that the hospital shouldn't pay the ransom.