Cyber Expert
The Cyber Expert collection is intended for learners ranging from grades 9-12 / Upper Secondary / Ages 14-18. This collection of cybersecurity maps is intended to help educators deepen students’ knowledge of cybersecurity concepts.
Cryptic Ciphers
Players arrive in a Cyber Kingdom and meet an unusual companion—a talking owl! The owl has arrived from another kingdom that has been destroyed. The kingdom has been overrun by monsters in the Nether Empire and they’re going to invade this kingdom too!

In this Minecraft map, players work through three different lessons: Encryption & Decryption, Integrity, and Social Engineering.
By the end of the unit, students will be able to:
- Define important academic words related to cybersecurity concepts
- Differentiate between encryption and decryption
- Encrypt and decrypt messages using Caesar Ciphers and Vigenère Ciphers
- Explain the concept of message integrity
- Describe the concept of social engineering
- Explain how individuals can avoid falling victim to social engineering
The full lesson plan and educational materials for Cyber Expert: Cryptic Ciphers are found on the Minecraft Education website.
Encryption & Decryption

Players report to the Secret Messages Office. In this space, messages arrive from across the kingdom. Each of the messages is encrypted so rival kingdom spies can’t read the messages if they’re intercepted. Players need to decrypt the messages to read them and then encrypt the messages to send them.
Integrity
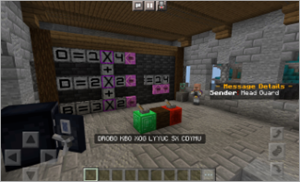
To ensure messages haven’t been tampered with, players need to check the integrity of the message. To check the integrity of the message, players learn and apply a check sum method.
Social Engineering
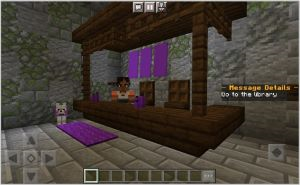
In this lesson, players better understand the concept of social engineering and the importance of keeping certain information confidential.
Daring Defense
Now that the portal has been opened, the players must help defend the castle! These monsters will overrun the castle – and the kingdom could be destroyed!

In this Minecraft map, players work through three different lessons: Firewalls, DoS/DDoS Attacks, and Access Controls.
By the end of the unit, students will be able to:
- Define important academic words related to cybersecurity concepts
- Differentiate between DoS and DDoS attacks
- Create a firewall using allow and deny rules
- Prevent unauthorized users on the network by implementing an access control system
The full lesson plan and educational materials for Cyber Expert: Daring Defense are found on the Minecraft Education website.
Firewalls

A firewall involves creating a series of rules to block or allow different traffic. Players need to create a firewall containing rules. This task uses villagers and malware as an analogy for the ports and IP addressing rules within a firewall. Players report to the Guard, who stands by the gate. They need to create code to decide (based on the wave) who is allowed to enter the castle and who should be denied.
DoS/DDoS Attacks
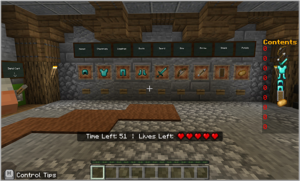
In this lesson, players process requests via minecarts for resources and equipment for the soldiers. However, watch out for bad or fake requests—it could cause a denial of service (DoS) attack. Or even worse—a DDoS (Distributed Denial of Service) attack that will overwhelm us completely!
Access Controls

In this lesson, players grant access to individuals who should have certain access to specific rooms in the castle.
Malware Mayhem
When players spawn into the world, they find themselves in the dungeon. The kingdom is being overrun with species of malware. Players need to help the Scholar collect specimens of the malware so they can figure out how to defeat them!

In this Minecraft map, players work through three different lessons: Malware, Ransomware, and Back-Up Data.
By the end of the unit, students will be able to:
- Differentiate between the different types of malware
- Articulate how malware attacks
- Protect ourselves from cyberattacks
- Define the concept of ransomware
- Describe the importance of backup software
The full lesson plan and educational materials for Cyber Expert: Malware Mayhem are found on the Minecraft Education website.
Malware
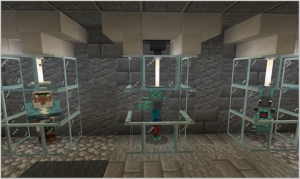
In this task, players travel to the forest to capture a virus, trojan, and a worm using jam, honey, and chocolate. The jam, honey, and chocolate spread are used as analogies for a honey pot (a virtual trap to lure attackers). Honeypots are used as early warning systems for new malware or cyberattacks. They’re set up to look like vulnerable computers or systems. The different treats used represents different vulnerabilities to attract different attacks. Once the new malware or cyberattack falls for the trap, cybersecurity experts who develop new defensive mechanism can analyze the attacks to counter them.
Ransomware
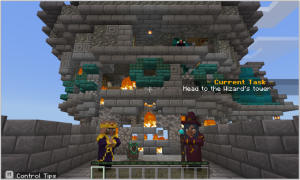
Oh no! The malware has taken over the Wizard’s tower! They’re demanding ransom and the King refused to pay. Well, that might have been a costly mistake! The malware has used TNT on the Wizard’s Tower and it’s destroyed.
Back-Up Data
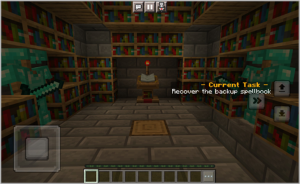
The Wizard informs the player that there’s off-site backup of all the important books in the secret library. To open the vault where the books are kept in, the player must locate three different keys hidden around the kingdom. They need to look for three people hidden in plain sight around the kingdom. Once they're found, they react to the codeword—ENIGMA. Players must answer their questions to receive the key for the secret library.