Protect cloud applications using Zero Trust
To safely benefit from cloud applications, organizations need to achieve a good balance that enables access to apps, while also ensuring and maintaining enough control to protect themselves and their users from risks. A Zero Trust framework empowers your organization to do this. With Zero Trust, you can:
- Apply technologies to control and discover shadow IT.
- Ensure appropriate permissions for app use.
- Limit access based on insights from real-time analytics.
- Monitor abnormal behavior in apps.
- Control user actions.
- Validate secure configuration options.
To achieve these goals, organizations can use a continuous protection process. A Zero Trust approach encourages the implementation of a robust and continuous protection process.
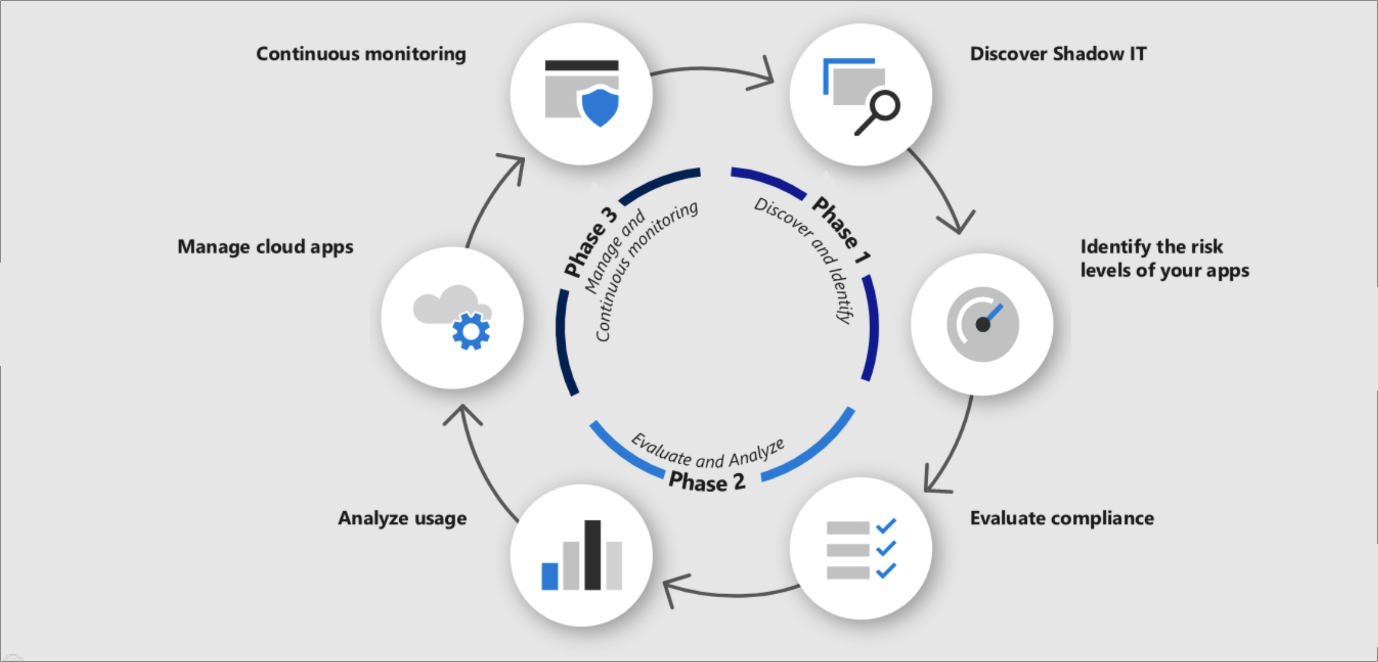
The process consists of three broad phases:
- Discover and identify: Discover shadow IT and identify risk levels.
- Evaluate and analyze: Evaluate compliance of apps and analyze usage patterns.
- Manage and continuously monitor: Manage cloud apps based on your discovery, evaluation, and analyses, and continue to monitor apps.
To achieve this, your organization can use cloud app discovery tools designed to help you to implement the process. These tools will automatically find cloud apps used across the organization, and enable you to:
- Assess app risk levels: For example, through a calculated score from 1 to 10, to represent an app's risk.
- Evaluate app compliance: Checking whether discovered apps meet compliance requirements for your organization.
- Analyze usage patterns: Understand how individuals use apps and learn about high-risk usage.
- Manage apps: Enforce governance actions such as sanctioning, reviewing, or blocking apps.
This way, your organization can put itself in a position to discover and control all shadow IT used by its people.
Protect sensitive information and activities automatically
To protect sensitive information and activities, your organization has to monitor and control how it wants users to behave inside cloud applications. To do this, you can create a wide range of policies including:
- Access policies: Control access to user sign-ins to cloud apps. For example, you use role-based access controls to only give users the access they need, based on their role.
- Activity policies: Monitor specific user activities in apps.
- File policies: Scan cloud apps for specific files, file types, and data such as proprietary or personal information—then apply governance rules to those files.
These policies, which you can create using cloud app discovery tools, allow you to detect suspicious activities and respond appropriately across cloud applications.
Your organization should also enable real-time monitoring and control over access to cloud apps. It can then use adaptive access controls for all apps. For example, you can use real-time monitoring to dynamically adapt and restrict access based on multiple data points such as location, device, and app at point of sign-in. This enables you to stop leaks and breaches in real time.
Strengthen protection against cyberthreats and rogue apps
Cybercriminals continue to evolve their attack techniques and tools, to breach defenses and access business-critical and personal information in your applications. To strengthen your protection against the latest attacks and attack tools, your organization should use advanced cloud app security capabilities including:
- User and entity behavioral analytics (UEBA): Evaluate behavior and respond using many risk indicators such as IP addresses, sign-in failures, activities from inactive accounts, or suspicious admin sign-ins.
- Anomaly detection: Detect and respond to unusual activities across cloud apps. For example, a user suddenly uploads 500 GB of data into a cloud storage app when they've never done this before.
- Malware protection: Detect for malware using the most up-to-date information across all apps. For example, to detect activities associated with a new type of malware that holds critical data hostage for ransom.
- Automated investigation and remediation: Investigate and remediate security alerts automatically. Or allow a security admin to remediate specific types of security alerts after automated investigation.
Your organization can use these and other capabilities to continuously protect itself against an evolving threat landscape.