Introduction
At their most simplistic, networks are a collection of connected devices. These devices can range from ones you've heard of like laptops, desktops, smartphones, and tablets, to things you might not use directly every day, such as routers, network printers, and switches.
Networks provide the backbone that enables communication between people, services, and devices. They empower us to stream videos, send messages, purchase items, make banking payments, and much more. The world's largest network, the internet, has connected us all and made the world a much smaller place.
As the boundaries of our networks expand, devices, services, and apps can now all connect to our networks via the cloud. As a result, securing networks has become more challenging. That's where a Zero Trust strategy can help.
Zero Trust isn't a tool, but a security model that employs three principles:
- Verify explicitly – always authenticate and authorize using all available information including location, identity, service or device health, and more.
- Use least privilege access – provide only enough network access to enable users, services, and apps to do what they need and only when they need it.
- Assume breach – assume that everyone and everything trying to access your network is a cybercriminal or malware and limit access.
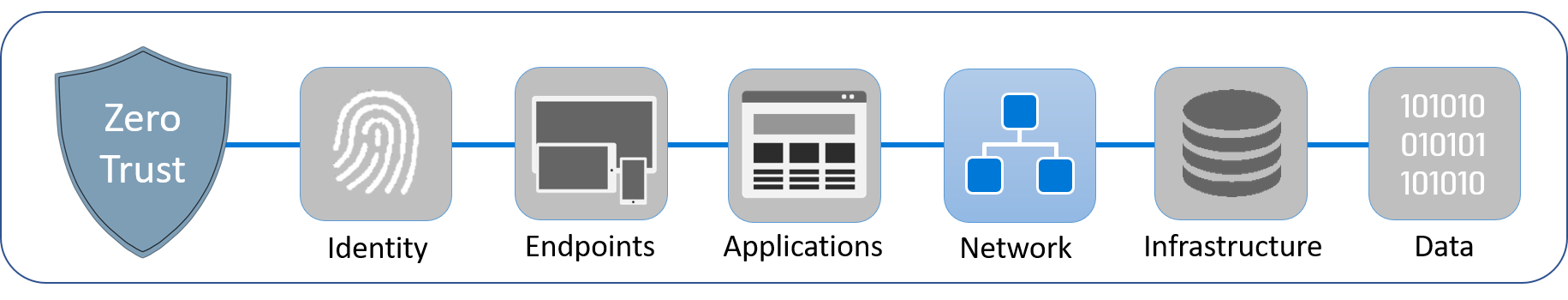
A network following Zero Trust principles assumes that cyberattack breaches are inevitable and that each network access request comes from an untrusted source. Working on this principle, Zero Trust lets you build a strong defense against attacks before they happen and minimizes the effects of a malicious attack.
In this module, you'll learn how the Zero Trust approach can protect your network through segmentation. You'll also understand network boundaries, use threat protection to spot weaknesses, and see how encrypting your data can minimize data loss.