Migración de servidores de Microsoft Defender para punto de conexión a Microsoft Defender for Cloud
Se aplica a:
- Microsoft Defender para punto de conexión Plan 1
- Microsoft Defender para punto de conexión Plan 2
- Microsoft Defender XDR
Este artículo le guía en la migración de servidores de Microsoft Defender para punto de conexión a Defender for Cloud.
Microsoft Defender para punto de conexión es una plataforma de seguridad de punto de conexión empresarial diseñada para ayudar a las redes empresariales a prevenir, detectar, investigar y responder a amenazas avanzadas.
Microsoft Defender for Cloud es una solución para la administración de la posición de seguridad en la nube (CSPM) y la protección de cargas de trabajo en la nube (CWP) que encuentra puntos débiles en la configuración de la nube. También ayuda a reforzar la posición de seguridad general del entorno y puede proteger las cargas de trabajo en entornos híbridos y multinube frente a amenazas en constante evolución.
Aunque ambos productos ofrecen funcionalidades de protección de servidores, Microsoft Defender for Cloud es nuestra solución principal para proteger los recursos de infraestructura, incluidos los servidores.
Cómo migrar mis servidores de Microsoft Defender para punto de conexión a Microsoft Defender for Cloud?
Si tiene servidores incorporados a Defender para punto de conexión, el proceso de migración varía según el tipo de máquina, pero hay un conjunto de requisitos previos compartidos.
Microsoft Defender for Cloud es un servicio basado en suscripciones en Microsoft Azure Portal. Por lo tanto, Defender for Cloud y los planes subyacentes, como Microsoft Defender para el plan 2 de servidores, deben estar habilitados en las suscripciones de Azure.
Para habilitar Defender para servidores para máquinas virtuales de Azure y máquinas que no son de Azure conectadas a través de servidores habilitados para Azure Arc, siga esta guía:
Si aún no usa Azure, planee el entorno siguiendo azure Well-Architected Framework.
Habilite Microsoft Defender for Cloud en su suscripción.
Habilite un Microsoft Defender para el plan de servidor en sus suscripciones. En caso de que use el plan 2 de Defender para servidores, asegúrese de habilitarlo también en el área de trabajo de Log Analytics a la que están conectadas las máquinas; le permite usar características opcionales como supervisión de integridad de archivos, controles de aplicación adaptables y mucho más.
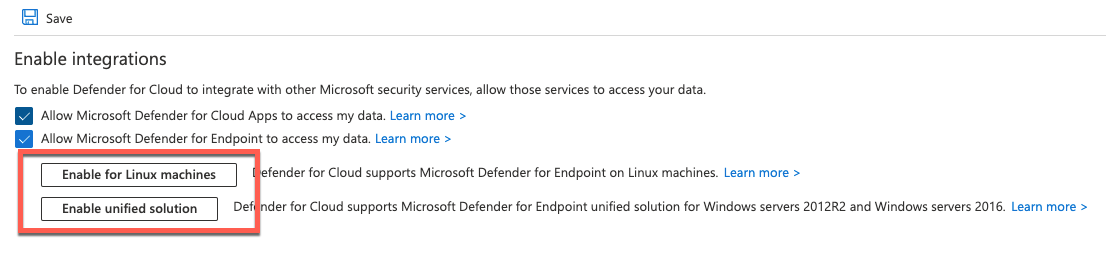
Asegúrese de que la integración de MDE está habilitada en la suscripción. Si tiene suscripciones de Azure preexistedas, es posible que vea uno (o ambos) de los dos botones de participación que se muestran en la imagen siguiente.
Si tiene cualquiera de estos botones en el entorno, asegúrese de habilitar la integración para ambos. En las nuevas suscripciones, ambas opciones están habilitadas de forma predeterminada. En este caso, no verá estos botones en su entorno.
Asegúrese de que se cumplen los requisitos de conectividad de Azure Arc. Microsoft Defender for Cloud requiere que todas las máquinas locales y que no sean de Azure se conecten a través del agente de Azure Arc. Además, Azure Arc no admite todos MDE sistemas operativos compatibles. Por lo tanto, aprenda a planear las implementaciones de Azure Arc aquí.
Recomienda: Si desea ver los resultados de vulnerabilidades en Defender for Cloud, asegúrese de habilitar Administración de vulnerabilidades de Microsoft Defender para Defender for Cloud.
Cómo migrar máquinas virtuales de Azure existentes a Microsoft Defender for Cloud?
En el caso de las máquinas virtuales de Azure, no se requieren pasos adicionales, que se incorporan automáticamente a Microsoft Defender for Cloud, gracias a la integración nativa entre la plataforma de Azure y Defender for Cloud.
Cómo migrar máquinas locales a Microsoft Defender para servidores?
Una vez cumplidos todos los requisitos previos, conecte las máquinas locales a través de servidores conectados a Azure Arc.
Cómo migrar máquinas virtuales desde entornos de AWS o GCP?
Create un nuevo conector multinube en la suscripción. (Para obtener más información sobre el conector, consulte Cuentas de AWS o proyectos de GCP.
En el conector multinube, habilite Defender para servidores en conectores AWS o GCP .
Habilite el autoaprovisionamiento en el conector multinube para el agente de Azure Arc, Microsoft Defender para punto de conexión extensión, evaluación de vulnerabilidades y, opcionalmente, extensión de Log Analytics.
Para obtener más información, consulte Las funcionalidades multinube de Defender for Cloud.
¿Qué ocurre una vez completados todos los pasos de migración?
Después de completar los pasos de migración pertinentes, Microsoft Defender for Cloud implementa la MDE.Windows extensión o MDE.Linux en las máquinas virtuales de Azure y las máquinas que no son de Azure conectadas a través de Azure Arc (incluidas las máquinas virtuales en proceso de AWS y GCP).
La extensión actúa como interfaz de administración e implementación, que organiza y encapsula los scripts de instalación de MDE dentro del sistema operativo y refleja su estado de aprovisionamiento en el plano de administración de Azure. El proceso de instalación reconoce una instalación existente de Defender para punto de conexión y la conecta a Defender for Cloud agregando automáticamente etiquetas de servicio de Defender para punto de conexión.
En caso de que tenga dispositivos que ejecutan Windows Server 2012 R2 o Windows Server 2016, y esos dispositivos se aprovisionan con la solución Microsoft Defender para punto de conexión heredada basada en Log Analytics, Microsoft Defender para el proceso de implementación de cloud implementa la solución unificada de Defender para punto de conexión. Después de una implementación correcta, detendrá y deshabilitará el proceso heredado de Defender para punto de conexión en estas máquinas.
Sugerencia
¿Desea obtener más información? Engage con la comunidad de seguridad de Microsoft en nuestra comunidad tecnológica: Microsoft Defender para punto de conexión Tech Community.
Comentarios
Próximamente: A lo largo de 2024 iremos eliminando gradualmente GitHub Issues como mecanismo de comentarios sobre el contenido y lo sustituiremos por un nuevo sistema de comentarios. Para más información, vea: https://aka.ms/ContentUserFeedback.
Enviar y ver comentarios de