Sündmused
9. apr, 15 - 10. apr, 12
Saate tuleviku tehte-ga koodi lisada ning suhelda JDConf 2025 Java partnerite ja ekspertidega.
Registreeruge koheSeda brauserit enam ei toetata.
Uusimate funktsioonide, turbevärskenduste ja tehnilise toe kasutamiseks võtke kasutusele Microsoft Edge.
In this article, you learn how to configure the admin consent workflow to enable users to request access to applications that require admin consent. You enable the ability to make requests by using an admin consent workflow. For more information on consenting to applications, see User and admin consent.
The admin consent workflow gives admins a secure way to grant access to applications that require admin approval. When a user tries to access an application but is unable to provide consent, they can send a request for admin approval. The request is sent via email to admins who are designated as reviewers. A reviewer takes action on the request, and the user is notified of the action.
To approve requests, a reviewer must have the permissions required to grant admin consent for the application requested. Simply designating them as a reviewer doesn't elevate their privileges.
To configure the admin consent workflow, you need:
Oluline
Microsoft recommends that you use roles with the fewest permissions. This practice helps improve security for your organization. Global Administrator is a highly privileged role that should be limited to emergency scenarios or when you can't use an existing role.
To enable the admin consent workflow and choose reviewers:
Sign in to the Microsoft Entra admin center as a Global Administrator.
Browse to Identity > Applications > Enterprise applications > Consent and permissions > Admin consent settings.
Under Admin consent requests, select Yes for Users can request admin consent to apps they are unable to consent to .
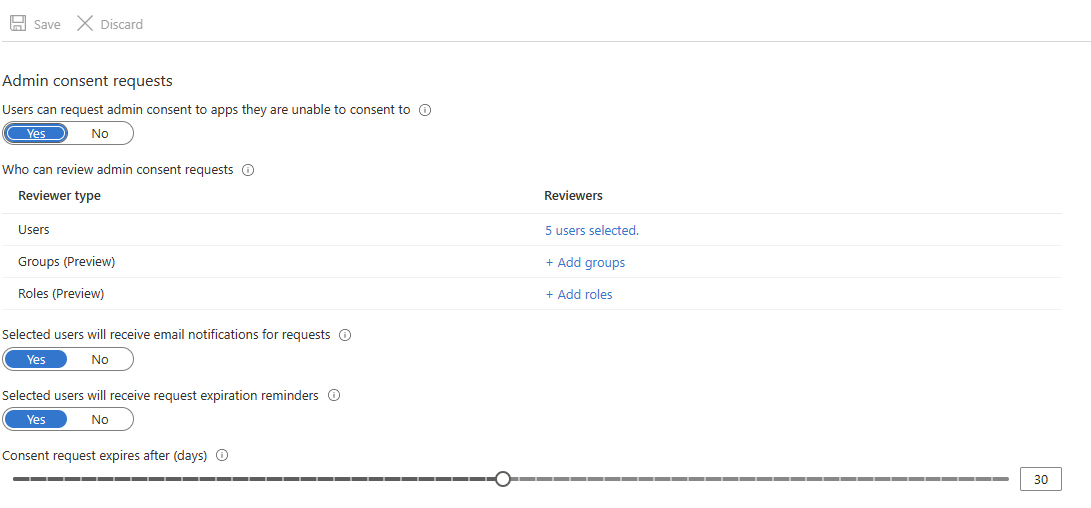
Configure the following settings:
Select Save. It can take up to an hour for the workflow to become enabled.
Märkus
You can add or remove reviewers for this workflow by modifying the Who can review admin consent requests list. A current limitation of this feature is that a reviewer retains the ability to review requests that were made while they were designated as a reviewer and will receive expiration reminder emails for those requests after they're removed from the reviewers list. Additionally, new reviewers won't be assigned to requests that were created before they were set as a reviewer.
To configure the admin consent workflow programmatically, use the Update adminConsentRequestPolicy API in Microsoft Graph.
Sündmused
9. apr, 15 - 10. apr, 12
Saate tuleviku tehte-ga koodi lisada ning suhelda JDConf 2025 Java partnerite ja ekspertidega.
Registreeruge koheKoolitus
Moodul
Manage user consent across digital platforms - Training
Manage user consent across digital platforms.
Sertimine
Microsoft Certified: Identity and Access Administrator Associate - Certifications
Demonstrate the features of Microsoft Entra ID to modernize identity solutions, implement hybrid solutions, and implement identity governance.