ATA:n asentaminen - vaihe 8
Koskee: Advanced Threat Analytics -versio 1.9
Vaihe 8: IP-osoitteen poissulkemisten ja Honeytoken-käyttäjän määrittäminen
ATA mahdollistaa tiettyjen IP-osoitteiden tai käyttäjien poissulkemisen useista tunnistamisista.
Esimerkiksi DNS Reconnaissance -poikkeus voi olla suojausskanneri, joka käyttää DNS:ää skannausmekanismina. Poissulkeminen auttaa ATA:a ohittamaan tällaiset skannerit. Esimerkki Pass-the-Ticket-poikkeuksesta on NAT-laite .
ATA mahdollistaa myös Honeytoken-käyttäjän määrityksen, jota käytetään pahantahtoisten toimijoiden kohdistusvarana – kaikki tähän tiliin liittyvät (yleensä lepotilassa olevat) todennukset käynnistävät hälytyksen.
Voit määrittää tämän seuraavasti:
Napsauta ATA-konsolissa asetukset-kuvaketta ja valitse Määritys.
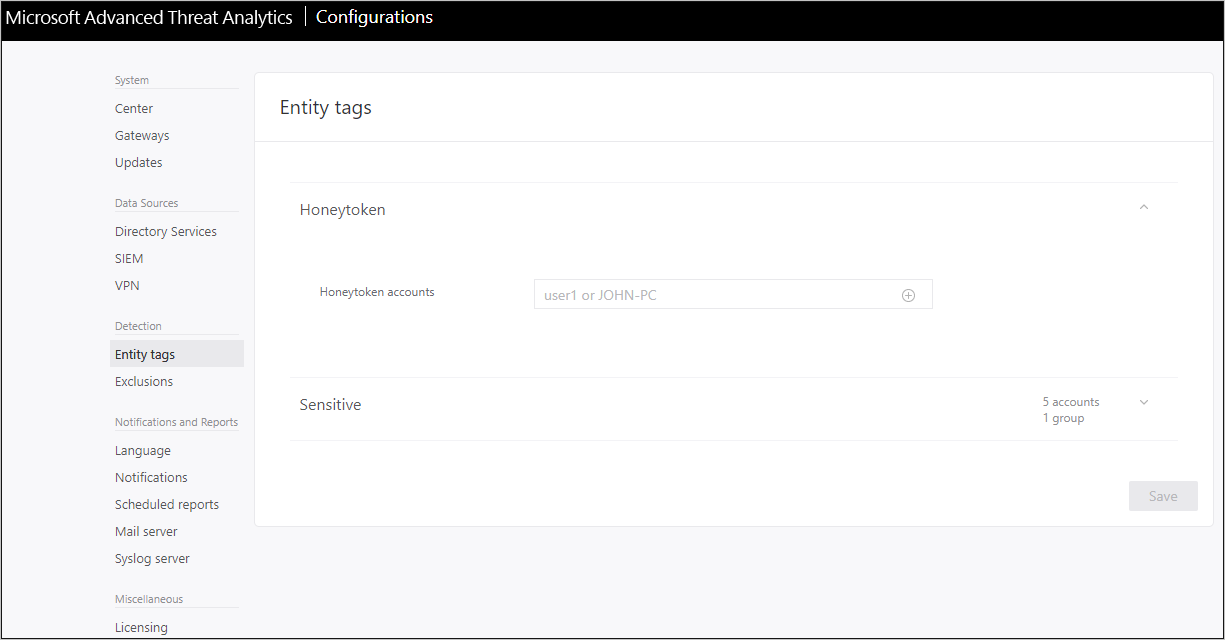
Valitse Tunnistaminen-kohdastaEntiteettitunnisteet.
Anna Honeytoken-tilien kohdassa Honeytoken-tilin nimi. Honeytoken-tilit-kenttä on haettavissa, ja se näyttää automaattisesti verkon entiteetit.
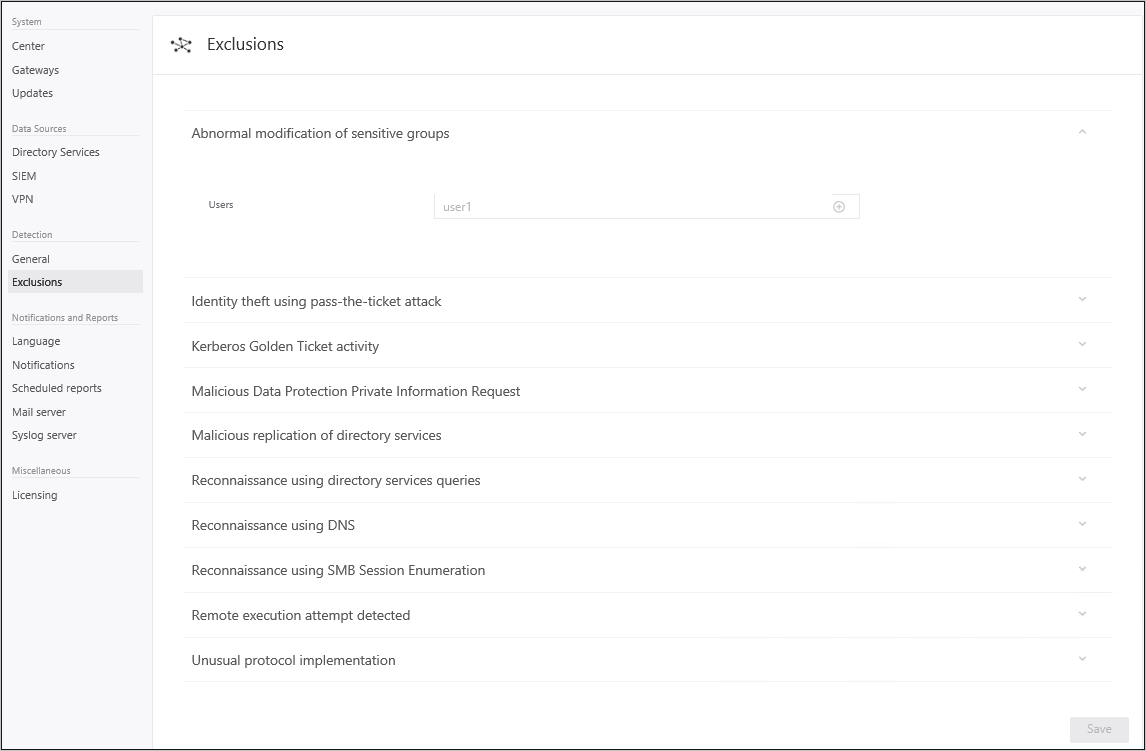
Valitse Poikkeukset. Anna kullekin uhkatyypille käyttäjätili tai IP-osoite, joka jätetään pois näiden uhkien havaitsemisesta, ja napsauta plusmerkkiä . Lisää entiteetti (käyttäjä tai tietokone) -kenttä on haettavissa, ja se lisätään automaattisesti verkkosi entiteetteihin. Lisätietoja on kohdassa Entiteettien jättäminen pois tunnisuksista
Valitse Tallenna.
Onnittelut! Olet onnistuneesti ottanut käyttöön Microsoft Advanced Threat Analyticsin!
Tarkista hyökkäyksen aikaraja, jotta voit tarkastella havaittuja epäilyttäviä toimintoja ja etsiä käyttäjiä tai tietokoneita ja tarkastella heidän profiilejaan.
ATA aloittaa epäilyttävän toiminnan skannaamisen välittömästi. Jotkin toiminnot, kuten epäilyttävät toimintatoiminnot, eivät ole käytettävissä, ennen kuin ATA on ehtinyt luoda käyttäytymisprofiileja (vähintään kolme viikkoa).
Jos haluat tarkistaa, että ATA on toiminnassa ja kiinni verkossasi olevia rikkomuksia, voit tutustua ATA-hyökkäyssimulaatioiden pelikirjaan.