Huomautus
Tämän sivun käyttö edellyttää valtuutusta. Voit yrittää kirjautua sisään tai vaihtaa hakemistoa.
Tämän sivun käyttö edellyttää valtuutusta. Voit yrittää vaihtaa hakemistoa.
Azure Data Box devices are secured with a password to prevent unwanted intrusion. This password is formally known as the device unlock key and is protected by using an encryption key. By default, the encryption key is a Microsoft managed key. For more direct control, you can provide your own managed key.
Using your own customer-managed key only affects how the device unlock key is encrypted. It doesn't affect how data stored on the device is encrypted.
To keep this level of control throughout the order process, use a customer-managed key when you create your order. For more information, see Tutorial: Order Azure Data Box.
This article describes how you can use customer-managed keys with an existing Azure Data Box order via the Azure portal. This article applies to Azure Data Box, Data Box Next-gen, and Data Box Heavy devices.
Requirements
The customer-managed key for a Data Box order must meet the following requirements:
- The key must be an RSA key of 2,048 bits or larger.
- The key must be created and stored in an Azure Key Vault that has Soft delete and Do not purge behaviors enabled. You can create a key vault and key while creating or updating your order. For more information, see What is Azure Key Vault?.
- The
Get,UnwrapKey, andWrapKeypermissions for the key must be enabled in the associated Azure Key Vault. These permissions must remain in place for the lifetime of the order. Modifying these permissions prevents the customer-managed key from being accessible during the Data Copy process.
Enable key
To enable a customer-managed key for an existing Data Box order in the Azure portal, follow these steps:
Navigate to the Overview page for a Data Box order.
Within the Settings group, select Encryption. Within the Encryption type pane, select the Customer managed key option. Next, select Select a key and key vault to open the Select key from Azure Key Vault page.
The Select key from Azure Key Vault page opens, and your subscription is automatically populated in the drop-down list. Select an existing key vault in the Key vault drop-down list, or select Create new to create a new key vault.
To create a new key vault, select your subscription and resource group form the corresponding Subscription and Resource group drop-down lists. Alternatively, you can create a new resource group by selecting Create new instead of populating the Resource group option.
Select the desired values for the Key vault name, Region, and Pricing tier drop-down lists. In the Recovery options group, ensure that Soft delete and Purge protection are enabled. Provide a value for the Days to retain deleted vaults field, and then select Review + Create.
Review the information for your key vault, then select Create. You're notified that the key vault creation is completed.
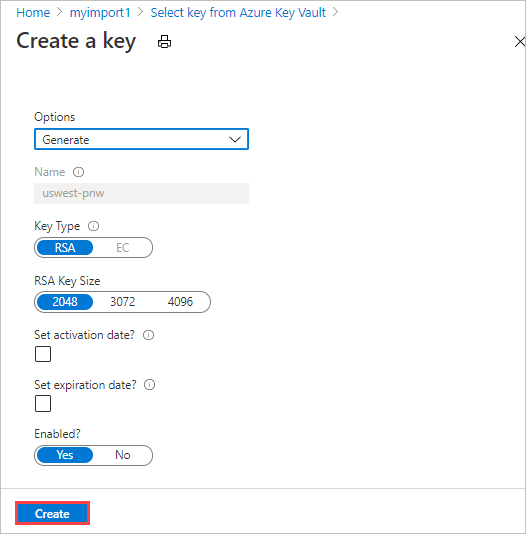
On the Select key from Azure Key Vault screen, you can select an existing key from the key vault or create a new one.
If you want to create a new key, select Create new. You must use an RSA key of 2,048 bits or greater.
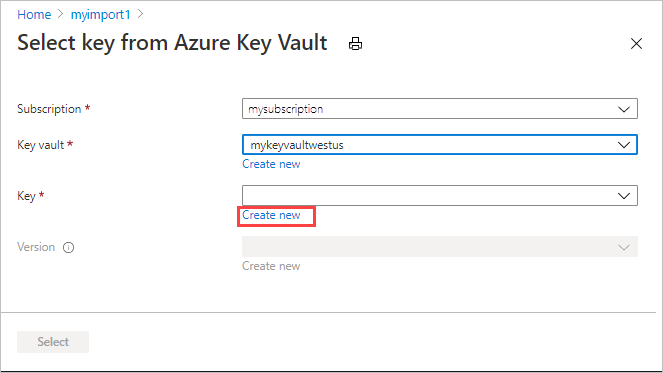
Enter a name for your key, accept the other defaults, and select Create. You're notified that a key is created within your key vault.
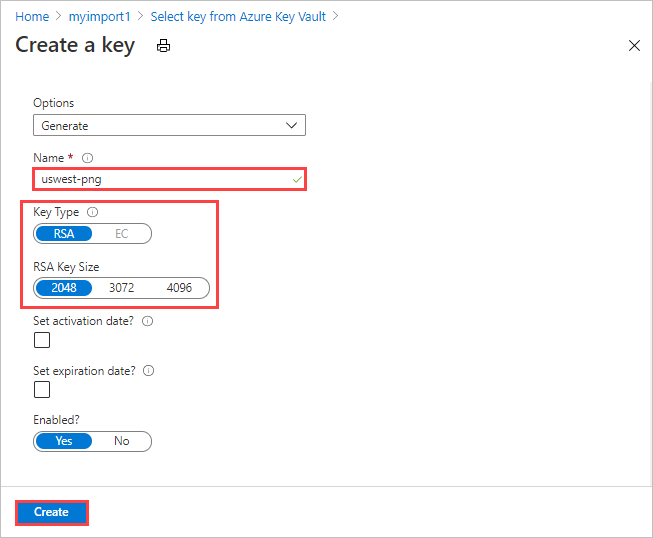
For Version, you can select an existing key version from the drop-down list.
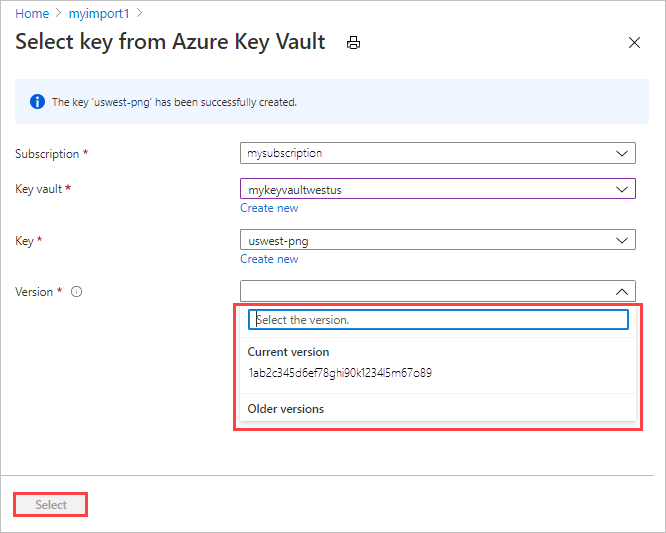
If you want to generate a new key version, select Create new.
Choose settings for the new key version, and select Create.
After selecting a key vault, key, and key version, choose Select.
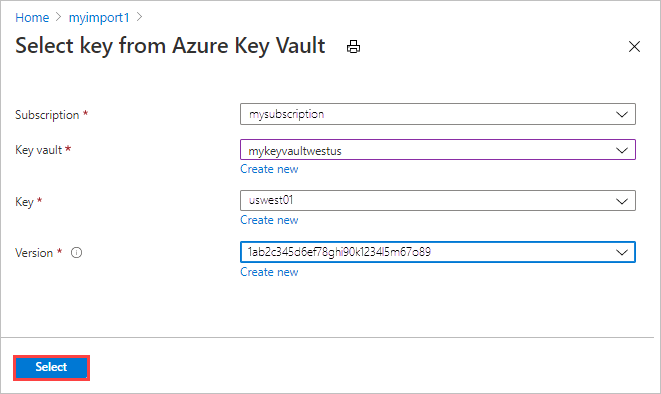
The Encryption type settings show the key vault and key that you chose.
Select the type of identity to use to manage the customer-managed key for this resource. You can use the system assigned identity that was generated during order creation or choose a user-assigned identity.
A user-assigned identity is an independent resource that you can use to manage access to resources. For more information, see Managed identity types.
To assign a user identity, select User assigned. Then select Select a user identity, and select the managed identity that you want to use.
You can't create a new user identity here. To find out how to create one, see Create, list, delete, or assign a role to a user-assigned managed identity using the Azure portal.
The selected user identity is shown in the Encryption type settings.
Select Save to save the updated Encryption type settings.
The key URL is displayed under Encryption type.
Important
You must enable the Get, UnwrapKey, and WrapKey permissions on the key. To set the permissions in Azure CLI, see az keyvault set-policy.
Change key
To change the key vault, key, and key version for the customer-managed key you're currently using, follow these steps:
On the Overview screen for your Data Box order, go to Settings > Encryption, and select Change key.
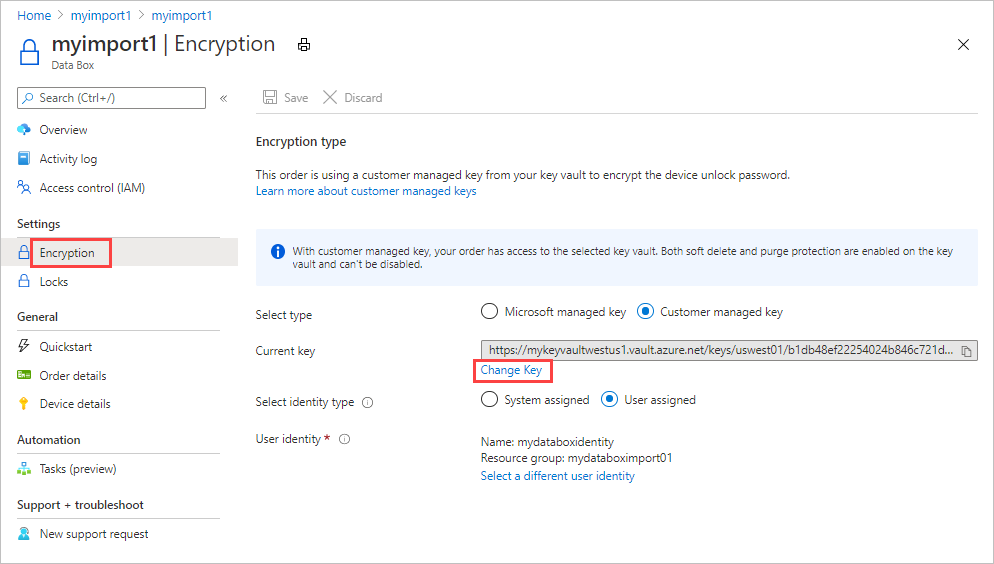
Choose Select a different key vault and key.
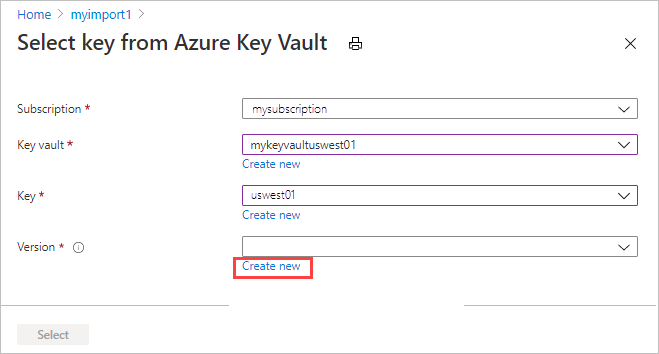
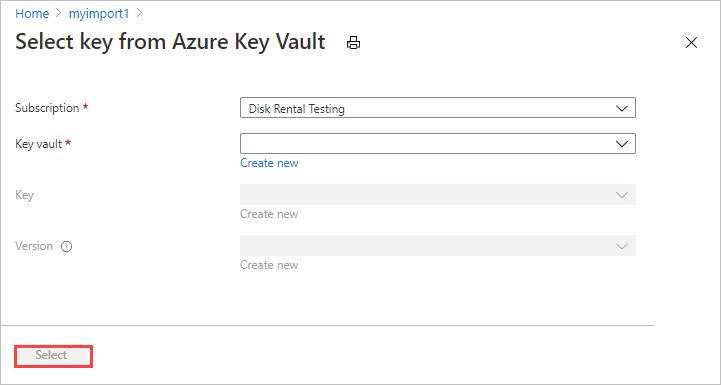
The Select key from key vault screen shows the subscription but no key vault, key, or key version. You can make any of the following changes:
Select a different key from the same key vault. Select the key vault before selecting the key and version.
Select a different key vault and assign a new key.
Change the version for the current key.
When you finish your changes, choose Select.
Select Save.
Important
You must enable the Get, UnwrapKey, and WrapKey permissions on the key. To set the permissions in Azure CLI, see az keyvault set-policy.
Change identity
Use the following steps to update the identity that manages access to the customer-managed key for this order:
On the Overview screen for your completed Data Box order, go to Settings > Encryption.
Make either of the following changes:
To change to a different user identity, select Select a different user identity. Then select a different identity in the panel on the right side of the screen, and choose Select.
To switch to the system-assigned identity generated during order creation, select System assigned by Select identity type.
Select Save.
Use Microsoft managed key
To change from using a customer-managed key to the Microsoft managed key for your order, follow these steps:
On the Overview screen for your completed Data Box order, go to Settings > Encryption.
By Select type, select Microsoft managed key.
Select Save.
Troubleshoot errors
If you receive any errors related to your customer-managed key, use the following table to troubleshoot.
| Error code | Error details | Resolution |
|---|---|---|
| SsemUserErrorEncryptionKeyDisabled | Couldn't fetch the passkey: the customer-managed key is disabled. | Enable the key version. |
| SsemUserErrorEncryptionKeyExpired | Couldn't fetch the passkey: the customer-managed key is expired. | Enabling the key version. |
| SsemUserErrorKeyDetailsNotFound | Couldn't fetch the passkey: the customer-managed key can't be found. | If the key vault is deleted:
If the key vault underwent a tenant migration, it can be recovered using one of the following methods:
|
| SsemUserErrorKeyVaultBadRequestException | Applied a customer-managed key but the key access hasn't been granted or has been revoked, or unable to access key vault due to firewall being enabled. | To enable access to the customer-managed key, add the selected identity to your key vault. If key vault has firewall enabled, switch to a system assigned identity and then add a customer-managed key. For more information, see how to Enable the key. |
| SsemUserErrorKeyVaultDetailsNotFound | Couldn't fetch the passkey as the associated key vault for the customer-managed key couldn't be found. | If you deleted the key vault, you can't recover the customer-managed key. If you migrated the key vault to a different tenant, see Change a key vault tenant ID after a subscription move. If you deleted the key vault:
Else if the key vault underwent a tenant migration, yes, it can be recovered using one of the below steps:
|
| SsemUserErrorSystemAssignedIdentityAbsent | Couldn't fetch the passkey as the customer-managed key couldn't be found. | Yes, check if:
|
| SsemUserErrorUserAssignedLimitReached | Adding new User Assigned Identity failed as you have reached the limit on the total number of user assigned identities that can be added. | Retry the operation with fewer user identities, or remove some user-assigned identities from the resource before retrying. |
| SsemUserErrorCrossTenantIdentityAccessForbidden | Managed identity access operation failed. Note: This error can occur when a subscription is moved to different tenant. The customer has to manually move the identity to the new tenant. |
Try adding a different user-assigned identity to your key vault to enable access to the customer-managed key. Or move the identity to the new tenant under which the subscription is present. For more information, see how to Enable the key. |
| SsemUserErrorKekUserIdentityNotFound | Applied a customer-managed key but the user assigned identity that has access to the key wasn't found in the active directory. Note: This error can occur when a user identity is deleted from Azure. |
Try adding a different user-assigned identity to your key vault to enable access to the customer-managed key. For more information, see how to Enable the key. |
| SsemUserErrorUserAssignedIdentityAbsent | Couldn't fetch the passkey as the customer-managed key couldn't be found. | Couldn't access the customer-managed key. Either the User Assigned Identity (UAI) associated with the key is deleted or the UAI type has changed. |
| SsemUserErrorKeyVaultBadRequestException | Applied a customer-managed key, but key access hasn't been granted or has been revoked, or the key vault couldn't be accessed because a firewall is enabled. | To enable access to the customer-managed key, add the selected identity to your key vault. If the key vault has a firewall enabled, switch to a system-assigned identity and then add a customer-managed key. For more information, see how to Enable the key. |
| SsemUserErrorEncryptionKeyTypeNotSupported | The encryption key type isn't supported for the operation. | Enable a supported encryption type on the key - for example, RSA or RSA-HSM. For more information, see Key types, algorithms, and operations. |
| SsemUserErrorSoftDeleteAndPurgeProtectionNotEnabled | Key vault doesn't have soft delete or purge protection enabled. | Ensure that both soft delete and purge protection are enabled on the key vault. |
| SsemUserErrorInvalidKeyVaultUrl (Command-line only) |
An invalid key vault URI was used. | Get the correct key vault URI. To get the key vault URI, use Get-AzKeyVault in PowerShell. |
| SsemUserErrorKeyVaultUrlWithInvalidScheme | Only HTTPS is supported for passing the key vault URI. | Pass the key vault URI over HTTPS. |
| SsemUserErrorKeyVaultUrlInvalidHost | The key vault URI host isn't an allowed host in the geographical region. | In the public cloud, the key vault URI should end with vault.azure.net. In the Azure Government cloud, the key vault URI should end with vault.usgovcloudapi.net. |
| Generic error | Couldn't fetch the passkey. | This error is a generic error. Contact Microsoft Support to troubleshoot the error and determine the next steps. |

















