Create exemptions and disable vulnerability assessment findings on Container registry images and running images
Note
You can customize your vulnerability assessment experience by exempting management groups, subscriptions, or specific resources from your secure score. Learn how to create an exemption for a resource or subscription.
If you have an organizational need to ignore a finding, rather than remediate it, you can optionally disable it. Disabled findings don't affect your secure score or generate unwanted noise.
When a finding matches the criteria you defined in your disable rules, it doesn't appear in the list of findings. Typical scenario examples include:
- Disable findings with severity below medium
- Disable findings for images that the vendor won't fix
Important
To create a rule, you need permissions to edit a policy in Azure Policy. Learn more in Azure RBAC permissions in Azure Policy.
You can use a combination of any of the following criteria:
- CVE - Enter the CVEs of the findings you want to exclude. Ensure the CVEs are valid. Separate multiple CVEs with a semicolon. For example, CVE-2020-1347; CVE-2020-1346.
- Image digest - Specify images for which vulnerabilities should be excluded based on the image digest. Separate multiple digests with a semicolon, for example:
sha256:9b920e938111710c2768b31699aac9d1ae80ab6284454e8a9ff42e887fa1db31;sha256:ab0ab32f75988da9b146de7a3589c47e919393ae51bbf2d8a0d55dd92542451c - OS version - Specify images for which vulnerabilities should be excluded based on the image OS. Separate multiple versions with a semicolon, for example: ubuntu_linux_20.04;alpine_3.17
- Minimum Severity - Select low, medium, high, or critical to exclude vulnerabilities less than the specified severity level.
- Fix status - Select the option to exclude vulnerabilities based on their fix status.
Disable rules apply per recommendation, for example, to disable CVE-2017-17512 both on the registry images and runtime images, the disable rule has to be configured in both places.
Note
The Azure Preview Supplemental Terms include additional legal terms that apply to Azure features that are in beta, preview, or otherwise not yet released into general availability.
To create a rule
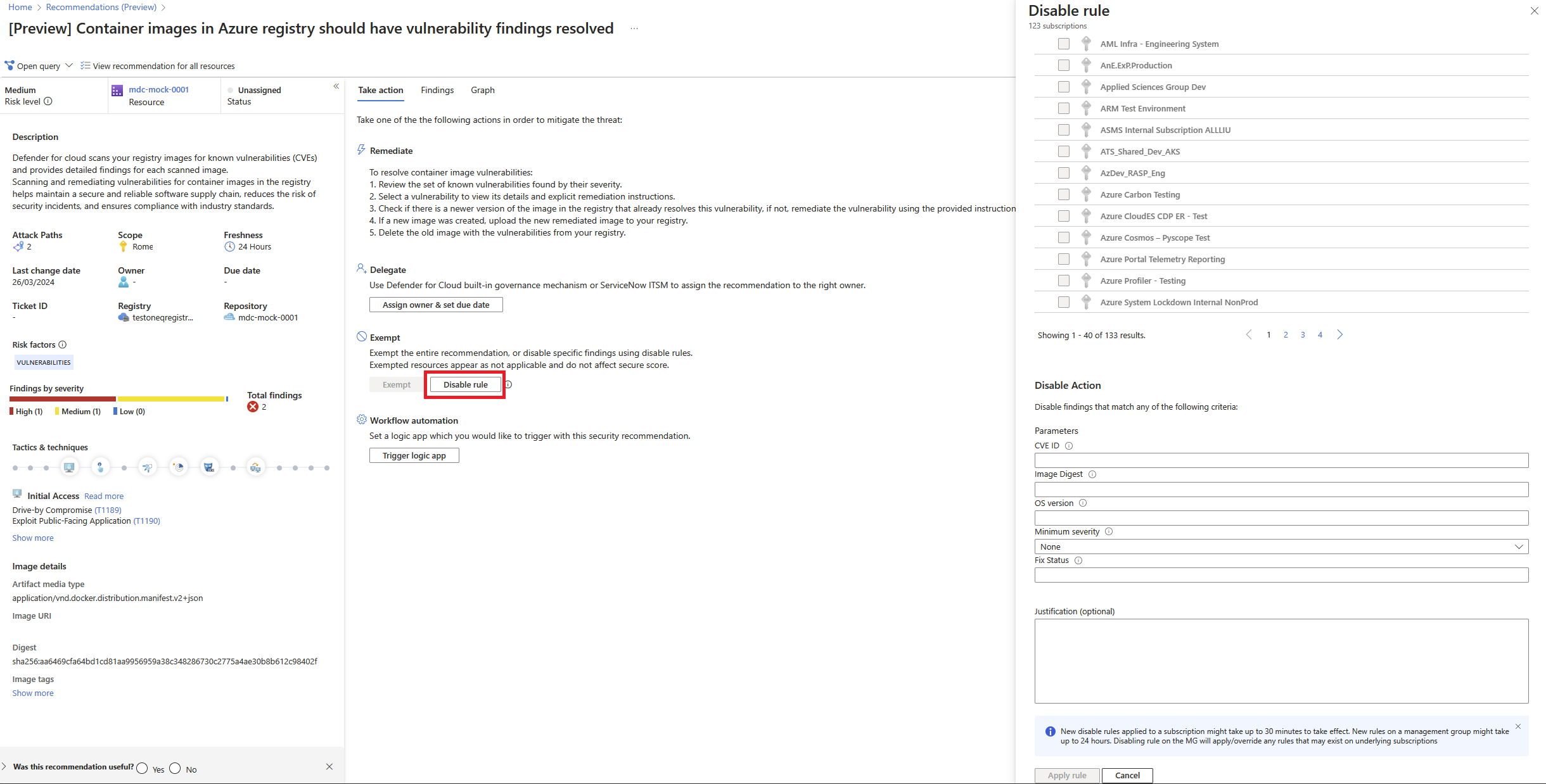
From the recommendations detail page for Container registry images should have vulnerability findings resolved powered by Microsoft Defender Vulnerability Management or Containers running in Azure should have vulnerability findings resolved, select Disable rule.
Select the relevant scope.
Define your criteria. You can use any of the following criteria:
- CVE - Enter the CVEs of the findings you want to exclude. Ensure the CVEs are valid. Separate multiple CVEs with a semicolon. For example, CVE-2020-1347; CVE-2020-1346.
- Image digest - Specify images for which vulnerabilities should be excluded based on the image digest. Separate multiple digests with a semicolon, for example:
sha256:9b920e938111710c2768b31699aac9d1ae80ab6284454e8a9ff42e887fa1db31;sha256:ab0ab32f75988da9b146de7a3589c47e919393ae51bbf2d8a0d55dd92542451c - OS version - Specify images for which vulnerabilities should be excluded based on the image OS. Separate multiple versions with a semicolon, for example: ubuntu_linux_20.04;alpine_3.17
- Minimum Severity - Select low, medium, high, or critical to exclude vulnerabilities less than and equal to the specified severity level.
- Fix status - Select the option to exclude vulnerabilities based on their fix status.
In the justification text box, add your justification for why a specific vulnerability was disabled. This provides clarity and understanding for anyone reviewing the rule.
Select Apply rule.
Important
Changes might take up to 24 hours to take effect.
To view, override, or delete a rule
From the recommendations detail page, select Disable rule.
From the scope list, subscriptions with active rules show as Rule applied.
To view or delete the rule, select the ellipsis menu ("...").
Do one of the following:
- To view or override a disable rule - select View rule, make any changes you want, and select Override rule.
- To delete a disable rule - select Delete rule.
Next steps
- Learn how to view and remediate vulnerability assessment findings for registry images.
- Learn about agentless container posture.