Enable File Integrity Monitoring when using the Azure Monitor Agent (Deprecated)
To provide File Integrity Monitoring (FIM), the Azure Monitor Agent (AMA) collects data from machines according to data collection rules. When the current state of your system files is compared with the state during the previous scan, FIM notifies you about suspicious modifications.
Note
As part of our Defender for Cloud updated strategy, the Azure Monitor Agent will no longer be required to receive all the capabilities of Defender for Servers. All features that currently rely on the Azure Monitor Agent, including those described on this page, will be available through Microsoft Defender for Endpoint integration or agentless scanning, by August 2024. To access the full capabilities of Defender for SQL server on machines, the Azure monitoring agent (also known as AMA) is required. For more information about the feature road map, see this announcement.
File Integrity Monitoring with the Azure Monitor Agent offers:
- Compatibility with the unified monitoring agent - Compatible with the Azure Monitor Agent that enhances security, reliability, and facilitates multi-homing experience to store data.
- Compatibility with tracking tool- Compatible with the Change tracking (CT) extension deployed through the Azure Policy on the client's virtual machine. You can switch to Azure Monitor Agent (AMA), and then the CT extension pushes the software, files, and registry to AMA.
- Simplified onboarding- You can onboard FIM from Microsoft Defender for Cloud.
- Multi-homing experience – Provides standardization of management from one central workspace. You can transition from Log Analytics (LA) to AMA so that all VMs point to a single workspace for data collection and maintenance.
- Rules management – Uses Data Collection Rules to configure or customize various aspects of data collection. For example, you can change the frequency of file collection.
In this article you'll learn how to:
- Enable File Integrity Monitoring with AMA
- Edit the list of tracked files and registry keys
- Exclude machines from File Integrity Monitoring
Availability
| Aspect | Details |
|---|---|
| Release state: | Preview |
| Pricing: | Requires Microsoft Defender for Servers Plan 2 |
| Required roles and permissions: | Owner Contributor |
| Clouds: | australiaeast, australiasoutheast, canadacentral, centralindia, centralus, eastasia, eastus2euap, eastus, eastus2, francecentral, japaneast, koreacentral, northcentralus, northeurope, southcentralus, southeastasia, switzerlandnorth, uksouth, westcentralus, westeurope, westus, westus2 |
Prerequisites
To track changes to your files on machines with AMA:
Enable Defender for Servers Plan 2.
Install AMA on machines you want to monitor.
Enable File Integrity Monitoring with AMA
To enable File Integrity Monitoring (FIM), use the FIM recommendation to select machines to monitor:
From Defender for Cloud's sidebar, open the Recommendations page.
Select the recommendation File integrity monitoring should be enabled on machines. Learn more about Defender for Cloud recommendations.
Select the machines that you want to use File Integrity Monitoring on, select Fix, and select Fix X resources.
The recommendation fix:
- Installs the
ChangeTracking-WindowsorChangeTracking-Linuxextension on the machines. - Generates a data collection rule (DCR) for the subscription named
Microsoft-ChangeTracking-[subscriptionId]-default-dcrthat defines what files and registries should be monitored based on default settings. The fix attaches the DCR to all machines in the subscription that have AMA installed and FIM enabled. - Creates a new Log Analytics workspace with the naming convention
defaultWorkspace-[subscriptionId]-fimand with the default workspace settings.
You can update the DCR and Log Analytics workspace settings later.
- Installs the
From Defender for Cloud's sidebar, go to Workload protections > File integrity monitoring, and select the banner to show the results for machines with Azure Monitor Agent.
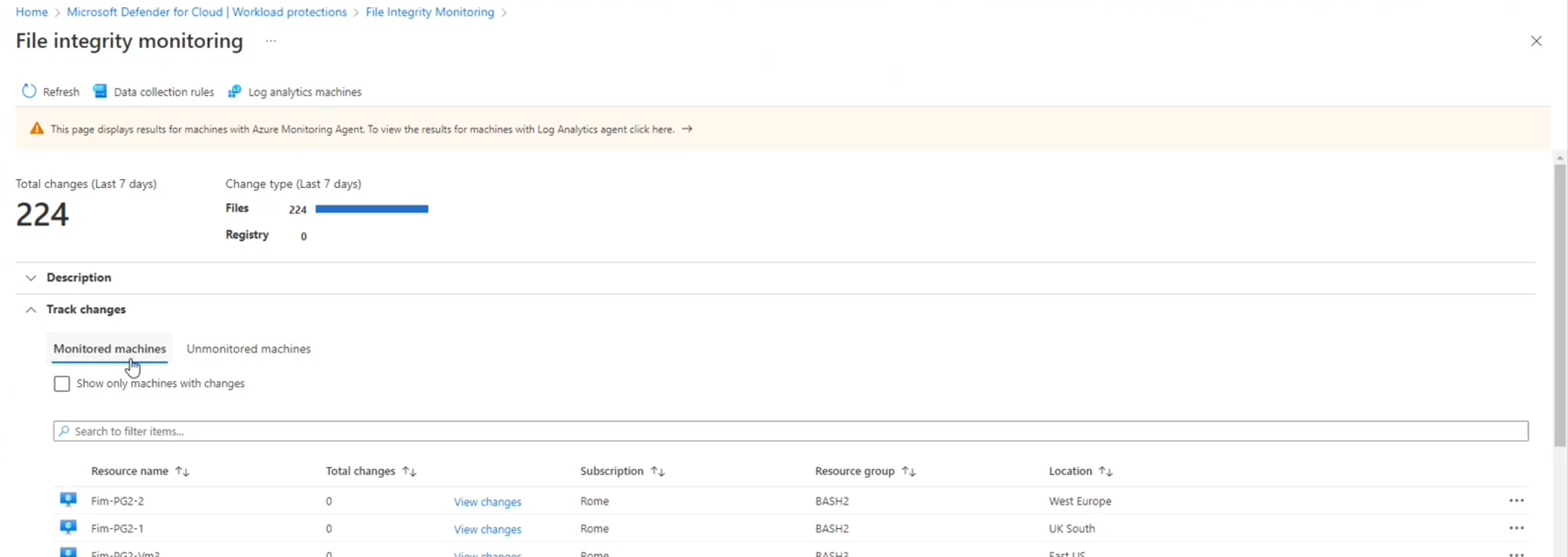
The machines with File Integrity Monitoring enabled are shown.
You can see the number of changes that were made to the tracked files, and you can select View changes to see the changes made to the tracked files on that machine.
Edit the list of tracked files and registry keys
File Integrity Monitoring (FIM) for machines with Azure Monitor Agent uses Data Collection Rules (DCRs) to define the list of files and registry keys to track. Each subscription has a DCR for the machines in that subscription.
FIM creates DCRs with a default configuration of tracked files and registry keys. You can edit the DCRs to add, remove, or update the list of files and registries that are tracked by FIM.
To edit the list of tracked files and registries:
In File integrity monitoring, select Data collection rules.
You can see each of the rules that were created for the subscriptions that you have access to.
Select the DCR that you want to update for a subscription.
Each file in the list of Windows registry keys, Windows files, and Linux files contains a definition for a file or registry key, including name, path, and other options. You can also set Enabled to False to untrack the file or registry key without removing the definition.
Learn more about system file and registry key definitions.
Select a file, and then add or edit the file or registry key definition.
Select Add to save the changes.
Exclude machines from File Integrity Monitoring
Every machine in the subscription that is attached to the DCR is monitored. You can detach a machine from the DCR so that the files and registry keys aren't tracked.
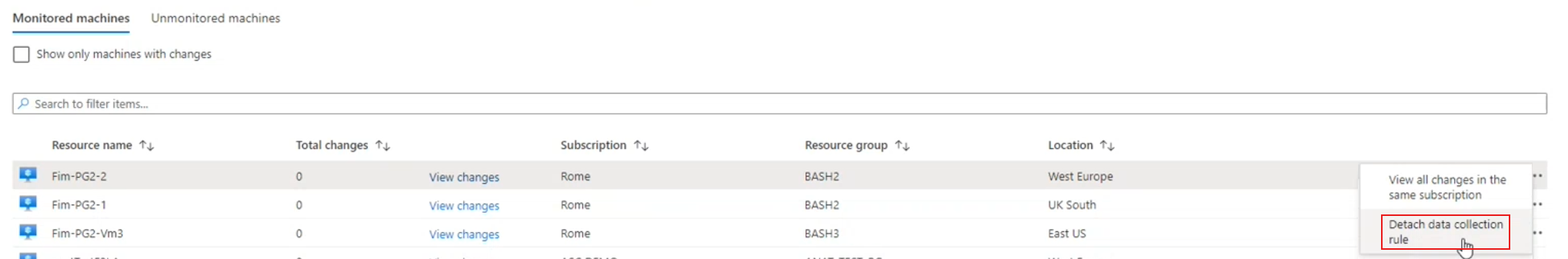
To exclude a machine from File Integrity Monitoring:
- In the list of monitored machines in the FIM results, select the menu (...) for the machine
- Select Detach data collection rule.
The machine moves to the list of unmonitored machines, and file changes aren't tracked for that machine anymore.
Next steps
Learn more about Defender for Cloud in:
- Setting security policies - Learn how to configure security policies for your Azure subscriptions and resource groups.
- Managing security recommendations - Learn how recommendations help you protect your Azure resources.
- Azure Security blog - Get the latest Azure security news and information.