Deploy air-gapped OT sensor management (Legacy)
Important
Defender for IoT now recommends using Microsoft cloud services or existing IT infrastructure for central monitoring and sensor management, and plans to retire the on-premises management console on January 1st, 2025.
For more information, see Deploy hybrid or air-gapped OT sensor management.
When you're working with multiple, air-gapped OT sensors that can't be managed by the Azure portal, we recommend deploying an on-premises management console to manage your air-gapped OT sensors.
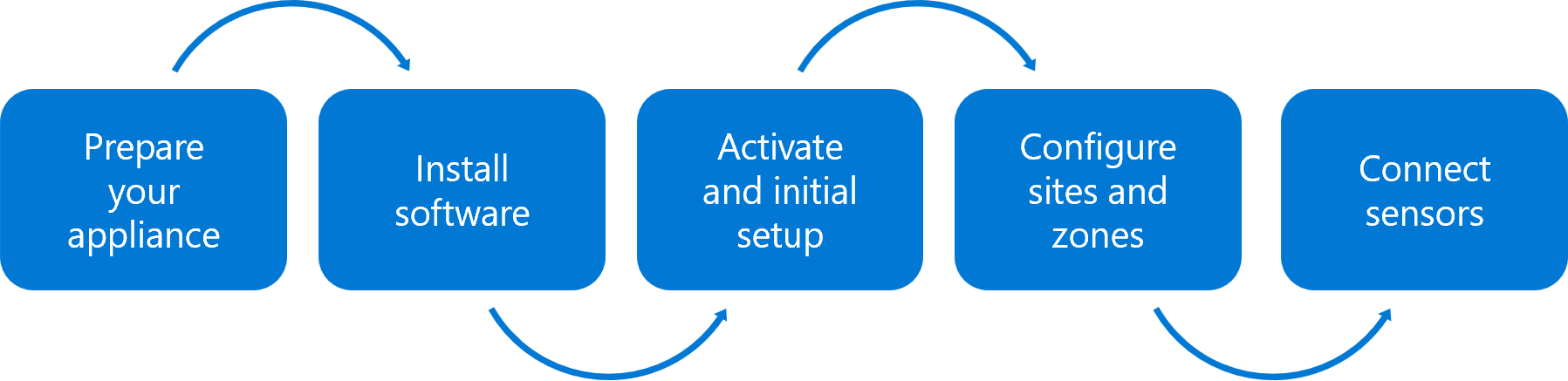
The following image describes the steps included in deploying an on-premises management console. Learn more about each deployment step in the sections below, including relevant cross-references for more details.
Deploying an on-premises management console is done by your deployment team. You can deploy an on-premises management console before or after you deploy your OT sensors, or in parallel.
Deployment steps
| Step | Description |
|---|---|
| Prepare an on-premises management console appliance | Just as you'd prepared an on-premises appliance for your OT sensors, prepare an appliance for your on-premises management console. To deploy a CA-signed certificate for production environments, make sure to prepare your certificate as well. |
| Install Microsoft Defender for IoT on-premises management console software | Download installation software from the Azure portal and install it on your on-premises management console appliance. |
| Activate and set up an on-premises management console | Use an activation file downloaded from the Azure portal to activate your on-premises management console. |
| Create OT sites and zones on an on-premises management console | If you're working with a large, air-gapped deployment, we recommend creating sites and zones on your on-premises management console, which help you monitor for unauthorized traffic crossing network segments, and is part of deploying Defender for IoT with Zero Trust principles. |
| Connect OT network sensors to the on-premises management console | Connect your air-gapped OT sensors to your on-premises management console to view aggregated data and configure further settings across all connected systems. |
Note
Sites and zones configured on the Azure portal are not synchronized with sites and zones configured on an on-premises management console.
When working with a large deployment, we recommend that you use the Azure portal to manage cloud-connected sensors, and an on-premises management console to manage locally-managed sensors.
Optional configurations
When deploying an on-premises management console, you may also want to configure the following options:
Active Directory integration, to allow Active Directory users to sign into your on-premises management console, use Active Directory groups, and configure global access groups.
Proxy tunneling access from OT network sensors, enhancing system security across your Defender for IoT system
High availability for on-premises management consoles, lowering the risk on your OT sensor management resources
Access OT network sensors via proxy tunneling
You might want to enhance your system security by preventing the on-premises management console to access OT sensors directly.
In such cases, configure proxy tunneling on your on-premises management console to allow users to connect to OT sensors via the on-premises management console. For example:
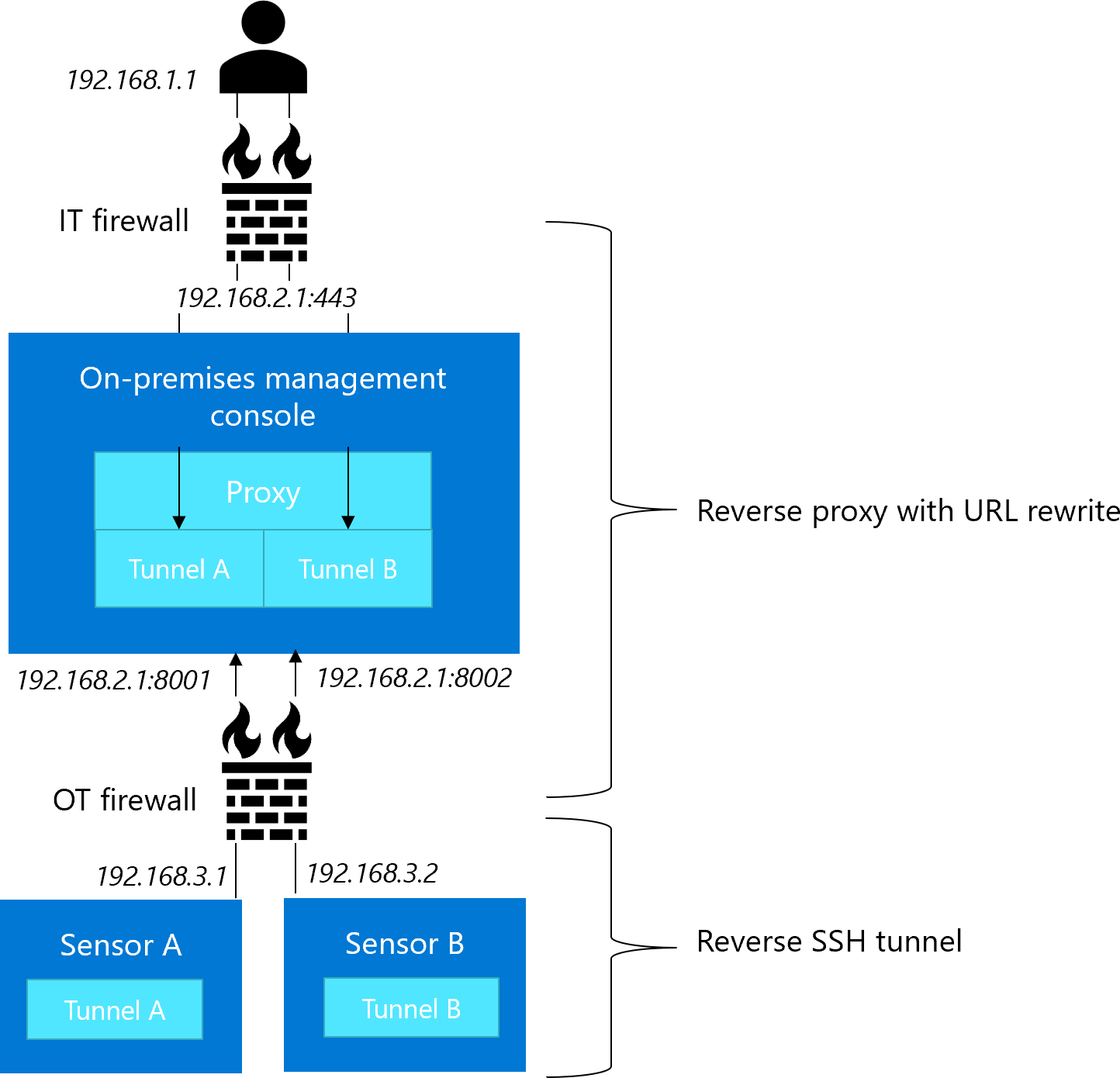
Once signed into the OT sensor, user experience remains the same. For more information, see Configure OT sensor access via tunneling.
High availability for on-premises management consoles
When deploying a large OT monitoring system with Defender for IoT, you may want to use a pair of primary and secondary machines for high availability on your on-premises management console.
When using a high availability architecture:
| Feature | Description |
|---|---|
| Secure connections | An on-premises management console SSL/TLS certificate is applied to create a secure connection between the primary and secondary appliances. Use a CA-signed certificate or the self-signed certificate generated during installation. For more information, see: - SSL/TLS certificate requirements for on-premises resources - Create SSL/TLS certificates for OT appliances - Manage SSL/TLS certificates |
| Data backups | The primary on-premises management console data is automatically backed up to the secondary on-premises management console every 10 minutes. For more information, see Backup and restore the on-premises management console. |
| System settings | The system settings defined on the primary on-premises management console are duplicated on the secondary. For example, if the system settings are updated on the primary, they're also updated on the secondary. |
For more information, see About high availability.