Configure mirroring with a switch SPAN port
This article is one in a series of articles describing the deployment path for OT monitoring with Microsoft Defender for IoT.
Configure a SPAN port on your switch to mirror local traffic from interfaces on the switch to a different interface on the same switch.
This article provides sample configuration processes and procedures for configuring a SPAN port, using either the Cisco CLI or GUI, for a Cisco 2960 switch with 24 ports running IOS.
Important
This article is intended only as sample guidance and not as instructions. Mirror ports on other Cisco operating systems and other switch brands are configured differently. For more information, see your switch documentation.
Prerequisites
Before you start, make sure that you understand your plan for network monitoring with Defender for IoT, and the SPAN ports you want to configure.
For more information, see Traffic mirroring methods for OT monitoring.
Sample CLI SPAN port configuration (Cisco 2960)
The following commands show a sample process for configuring a SPAN port on a Cisco 2960 via CLI:
Cisco2960# configure terminal
Cisco2960(config)# monitor session 1 source interface fastehernet 0/2 - 23 rx
Cisco2960(config)# monitor session 1 destination interface fastethernet 0/24
Cisco2960(config)# end
Cisco2960# show monitor session 1
Cisco2960# running-copy startup-config
Sample GUI SPAN port configuration (Cisco 2960)
This procedure describes the high-level steps for configuring a SPAN port on a Cisco 2960 via the GUI. For more information, see the relevant Cisco documentation.
From the switch's configuration GUI:
- Enter the global configuration mode.
- Configure the first 23 ports as a session source, mirroring only RX packets.
- Configure port 24 to be a session destination.
- Return to privileged EXEC mode.
- Verify the port mirroring configuration.
- Save the configuration.
Sample CLI SPAN port configuration with multiple VLANs (Cisco 2960)
Defender for IoT can monitor multiple VLANs configured in your network without any extra configuration, as long as the network switch is configured to send VLAN tags to Defender for IoT.
For example, the following commands must be configured on a Cisco switch to support monitoring VLANs in Defender for IoT:
Monitor session: The following commands configure your switch to send VLANs to the SPAN port.
monitor session 1 source interface Gi1/2
monitor session 1 filter packet type good Rx
monitor session 1 destination interface fastEthernet1/1 encapsulation dot1q
Monitor Trunk Port F.E. Gi1/1: The following commands configure your switch to support VLANs configured on the trunk port:
interface GigabitEthernet1/1
switchport trunk encapsulation dot1q
switchport mode trunk
Validate traffic mirroring
After configuring traffic mirroring, make an attempt to receive a sample of recorded traffic (PCAP file) from the switch SPAN or mirror port.
A sample PCAP file will help you:
- Validate the switch configuration
- Confirm that the traffic going through your switch is relevant for monitoring
- Identify the bandwidth and an estimated number of devices detected by the switch
Use a network protocol analyzer application, such as Wireshark, to record a sample PCAP file for a few minutes. For example, connect a laptop to a port where you've configured traffic monitoring.
Check that Unicast packets are present in the recording traffic. Unicast traffic is traffic sent from address to another.
If most of the traffic is ARP messages, your traffic mirroring configuration isn't correct.
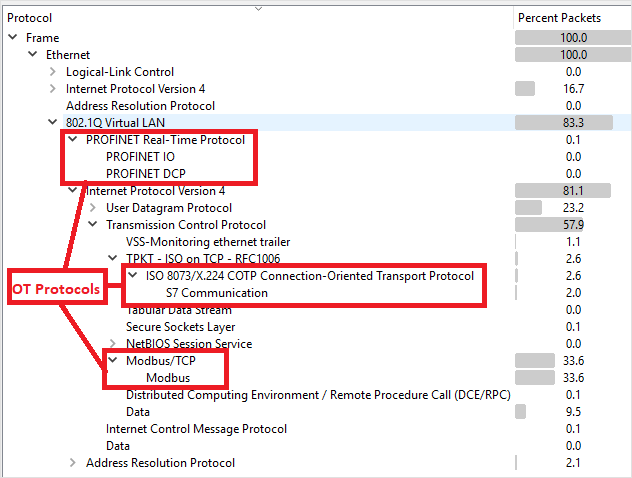
Verify that your OT protocols are present in the analyzed traffic.
For example:
Deploy with unidirectional gateways/data diodes
You might deploy Defender for IoT with unidirectional gateways, also known as data diodes. Data diodes provide a secure way to monitor networks as they only allow data to flow in one direction. This means data can be monitored without compromising the security of the network, as data cannot be sent back in the opposite direction. Examples of data diode solutions are Waterfall, Owl Cyber Defense, or Hirschmann.
If unidirectional gateways are needed, we recommend deploying your data diodes on the SPAN traffic going to the sensor monitoring port. For example, use a data diode to monitor traffic from a sensitive system, such as an industrial control system, while keeping the system completely isolated from the monitoring system.
Place your OT sensors outside the electronic perimeter and have them receive traffic from the diode. In this scenario, you’ll be able to manage your Defender for IoT sensors from the cloud, keeping them automatically updated with the latest threat intelligence packages.
