Tutorial: Configure certificate auto-rotation in Key Vault
You can easily provision, manage, and deploy digital certificates by using Azure Key Vault. The certificates can be public and private Secure Sockets Layer (SSL)/Transport Layer Security (TLS) certificates signed by a certificate authority (CA), or a self-signed certificate. Key Vault can also request and renew certificates through partnerships with CAs, providing a robust solution for certificate lifecycle management. In this tutorial, you'll update a certificate's validity period, auto-rotation frequency, and CA attributes.
The tutorial shows you how to:
- Manage a certificate by using the Azure portal.
- Add a CA provider account.
- Update the certificate's validity period.
- Update the certificate's auto-rotation frequency.
- Update the certificate's attributes by using Azure PowerShell.
Before you begin, read Key Vault basic concepts.
If you don't have an Azure subscription, create a free account before you begin.
Sign in to Azure
Sign in to the Azure portal.
Create a vault
Create a key vault using one of these three methods:
- Create a key vault using the Azure portal
- Create a key vault using the Azure CLI
- Create a key vault using Azure PowerShell
Create a certificate in Key Vault
Create a certificate or import a certificate into the key vault (see Steps to create a certificate in Key Vault. In this case, you'll work on a certificate called ExampleCertificate.
Update certificate lifecycle attributes
In Azure Key Vault, you can update a certificate's lifecycle attributes both at the time of certificate creation or after.
A certificate created in Key Vault can be:
- A self-signed certificate.
- A certificate created with a CA that's partnered with Key Vault.
- A certificate with a CA that isn't partnered with Key Vault.
The following CAs are currently partnered providers with Key Vault:
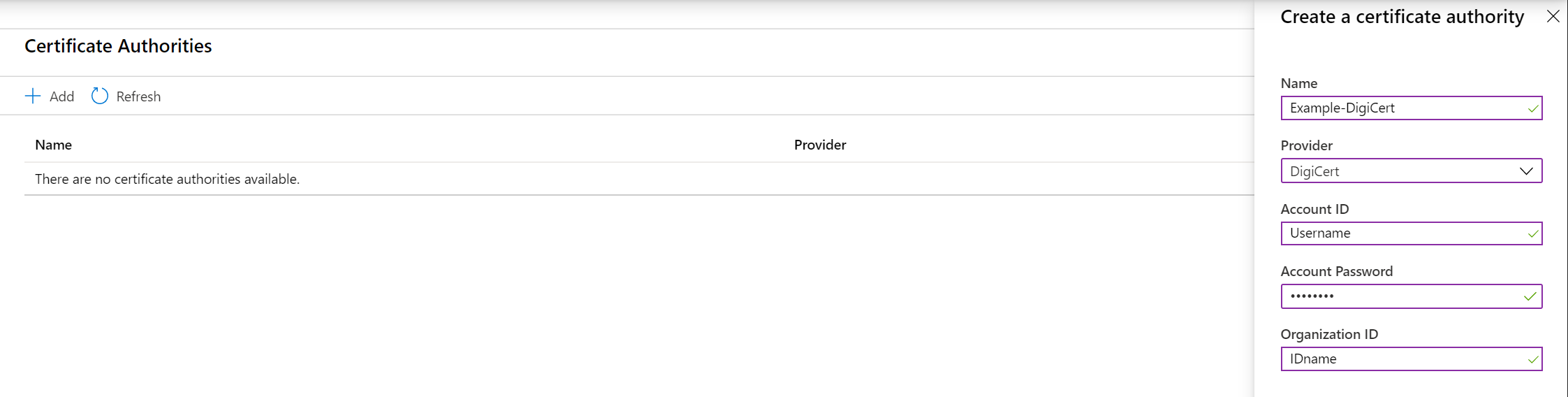
- DigiCert: Key Vault offers OV or EV TLS/SSL certificates.
- GlobalSign: Key Vault offers OV or EV TLS/SSL certificates.
Key Vault auto-rotates certificates through established partnerships with CAs. Because Key Vault automatically requests and renews certificates through the partnership, auto-rotation capability isn't applicable for certificates created with CAs that aren't partnered with Key Vault.
Note
An account admin for a CA provider creates credentials that Key Vault uses to create, renew, and use TLS/SSL certificates.
Update certificate lifecycle attributes at the time of creation
On the Key Vault properties pages, select Certificates.
Select Generate/Import.
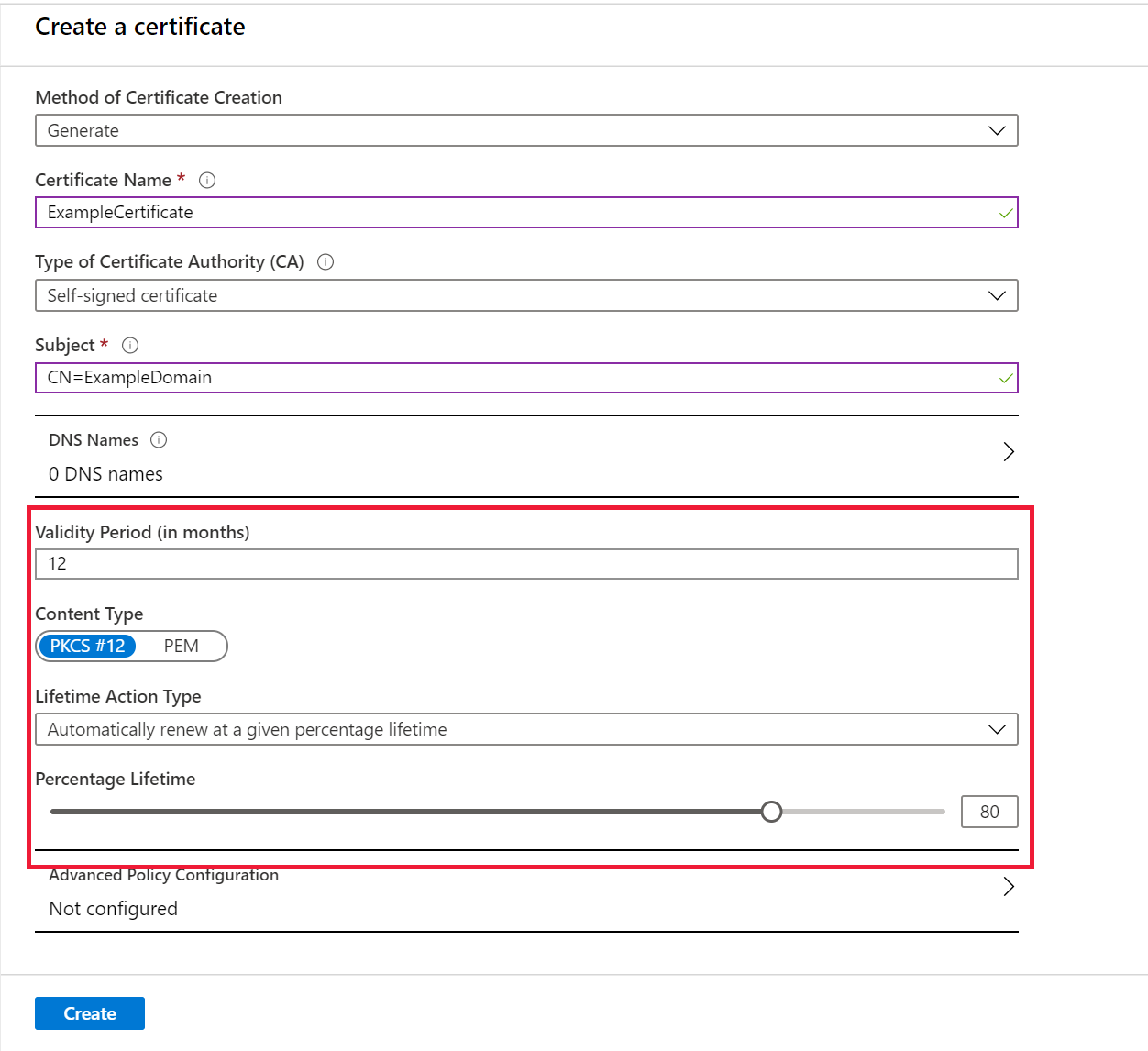
On the Create a certificate screen, update the following values:
Validity Period: Enter the value (in months). Creating short-lived certificates is a recommended security practice. By default, the validity value of a newly created certificate is 12 months.
Lifetime Action Type: Select the certificate's auto-renewal and alerting action and then update percentage lifetime or Number of days before expiry. By default, a certificate's auto-renewal is set at 80 percent of its lifetime. From the drop-down menu, select one of the following options.
Automatically renew at a given time Email all contacts at a given time Selecting this option will turn on autorotation. Selecting this option will not auto-rotate but will only alert the contacts. You can learn about setting up Email contact here
Select Create.
Update lifecycle attributes of a stored certificate
Select the key vault.
On the Key Vault properties pages, select Certificates.
Select the certificate you want to update. In this case, you'll work on a certificate called ExampleCertificate.
Select Issuance Policy from the top menu bar.
On the Issuance Policy screen, update the following values:
- Validity Period: Update the value (in months).
- Lifetime Action Type: Select the certificate's auto-renewal and alerting action and then update the percentage lifetime or Number of days before expiry.
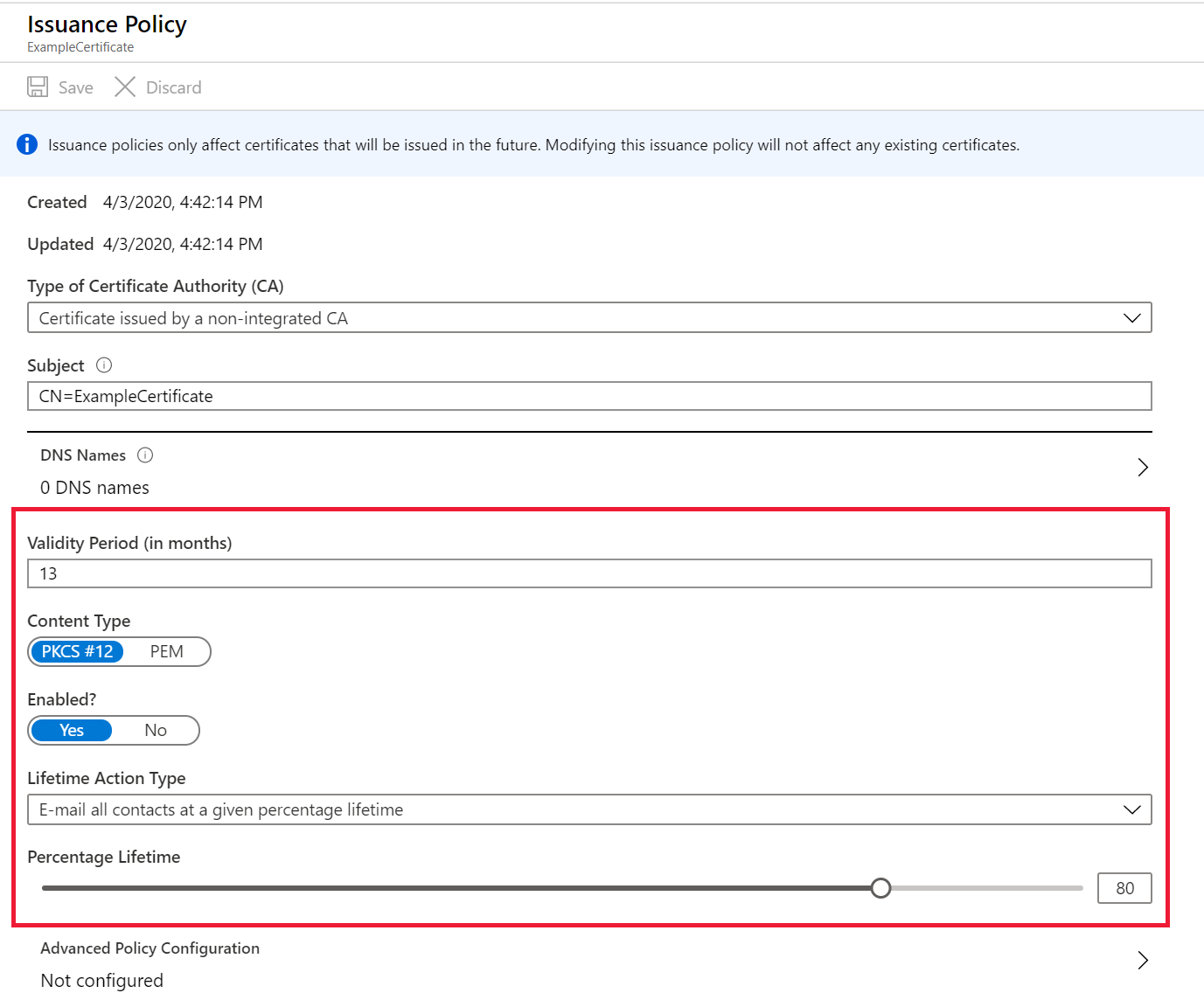
Select Save.
Important
Changing the Lifetime Action Type for a certificate will record modifications for the existing certificates immediately.
Update certificate attributes by using PowerShell
Set-AzureKeyVaultCertificatePolicy -VaultName $vaultName
-Name $certificateName
-RenewAtNumberOfDaysBeforeExpiry [276 or appropriate calculated value]
Tip
To modify the renewal policy for a list of certificates, enter File.csv containing
VaultName,CertName as in the following example:
vault1,Cert1
vault2,Cert2
$file = Import-CSV C:\Users\myfolder\ReadCSVUsingPowershell\File.csv
foreach($line in $file)
{
Set-AzureKeyVaultCertificatePolicy -VaultName $vaultName -Name $certificateName -RenewAtNumberOfDaysBeforeExpiry [276 or appropriate calculated value]
}
To learn more about the parameters, see az keyvault certificate.
Clean up resources
Other Key Vault tutorials build upon this tutorial. If you plan to work with these tutorials, you might want to leave these existing resources in place. When you no longer need them, delete the resource group, which deletes the key vault and related resources.
To delete the resource group by using the portal:
- Enter the name of your resource group in the Search box at the top of the portal. When the resource group used in this quickstart appears in the search results, select it.
- Select Delete resource group.
- In the TYPE THE RESOURCE GROUP NAME: box, type the name of the resource group and then select Delete.
Next steps
In this tutorial, you updated a certificate's lifecycle attributes. To learn more about Key Vault and how to integrate it with your applications, continue on to the following articles:
- Read more about Managing certificate creation in Azure Key Vault.
- Review the Key Vault Overview.