Service Connector internals
Service Connector is an Azure extension resource provider designed to provide a simple way to create and manage connections between Azure services.
Service Connector offers the following features:
- Lets you connect Azure services together with a single Azure CLI command or in a few steps using the Azure portal.
- Supports an increasing number of databases, storage, real-time services, state, and secret stores that are used with your cloud native application.
- Configures network settings, authentication, and manages connection environment variables or properties for you.
- Validates connections and provides suggestions to fix faulty connections.
Service connection overview
The concept of service connection is a key concept in the resource model of Service Connector. A service connection represents an abstraction of the link between two services. Service connections have the following properties:
| Property | Description |
|---|---|
| Connection Name | The unique name of the service connection. |
| Source Service Type | Source services are services you can connect to target services. They are usually Azure compute services and they include Azure App Service, Azure Container Apps, Azure Functions, Azure Kubernetes Service (AKS) and Azure Spring Apps. |
| Target Service Type | Target services are backing services or dependency services that your compute services connect to. Service Connector supports various target service types including major databases, storage, real-time services, state, and secret stores. |
| Client Type | Client type refers to your compute runtime stack, development framework, or specific type of client library that accepts the specific format of the connection environment variables or properties. |
| Authentication Type | The authentication type used for the service connection. It could be a secret/connection string, a managed identity, or a service principal. |
Source services and target services support multiple simultaneous service connections, which means that you can connect each resource to multiple resources.
Service Connector manages connections in the properties of the source instance. Creating, getting, updating and deleting connections is done directly by opening the source service instance in the Azure portal, or by using the CLI commands of the source service.
Connections can be made across subscriptions or tenants, meaning that source and target services can belong to different subscriptions or tenants. When you create a new service connection, the connection resource is created in the same region as your compute service instance by default.
Service connection creation and update
Service Connector runs multiple tasks while creating or updating service connections, including:
Configuring the network and firewall settings. Learn more about network solutions.
Configuring connection information. Learn more about connection configurations.
Configuring authentication information. Service Connector supports all available authentication types between source services and target services.
- System assigned managed identity. Service Connector enables system assigned managed identity on source services if not enabled yet, then grants RBAC roles of target services to the managed identity. The user can specify the roles to be granted.
- User assigned managed identity. Service Connector enables user assigned managed identity on source services if not enabled yet, then grants RBAC roles of target services to the managed identity. The user can specify the roles to be granted.
- Connection String. Service Connector retrieves connection strings from target services such as Storage, Redis Cache etc., or constructs connection strings based on user input, such as Azure database for SQL, PostgreSQL etc.
- Service principal. Service Connector grants RBAC roles of target services to the managed identity. The user can specify the roles to be granted.
Service Connector saves corresponding authentication configurations to source services, for example, saving AZURE_CLIENT_ID, AZURE_TENANT_ID, AZURE_STORAGEACCOUNT_ENDPOINT for Storage with authentication type user assigned managed identity.
Creating or updating connection rollback if failure occurs
If a step fails during this process, Service Connector rolls back all previous steps to keep the initial settings in the source and target instances.
Resource provider
Microsoft.ServiceLinker is the name of Service Connector's resource provider.
When a user opens the Service Connector tab in the Azure portal, the ServiceLinker resource provider is automatically registered in the user's active subscription. The user who generated the registration is listed as the initiator of the registration event.
Service Connector lets users connect services across subscriptions. When a user creates a connection to a target service registered in another subscription, Service Linker also gets registered in the target service's subscription. This registration occurs when the user selects the Review + create tab before finally creating the connection.
Connection configurations
Connection configurations are set in the source service.
In the Azure portal, open a source service and navigate to Service Connector. Expand each connection and view the connection configurations.
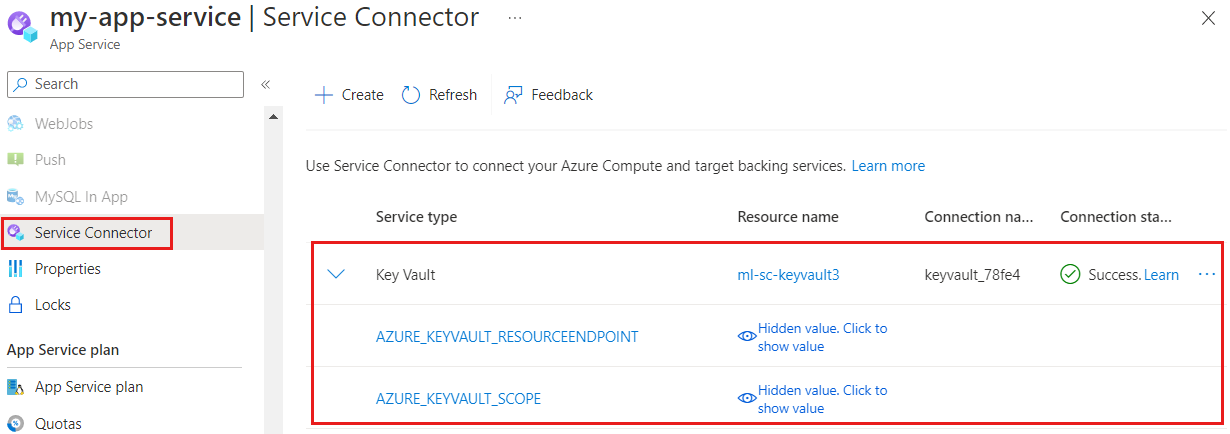
In the CLI, use the list-configuration command to get the connection configurations.
az webapp connection list-configuration --resource-group <source-service-resource-group> --name <source-service-name> --connection <connection-name>
az spring connection list-configuration --resource-group <source-service-resource-group> --name <source-service-name> --connection <connection-name>
az containerapp connection list-configuration --resource-group <source-service-resource-group> --name <source-service-name> --connection <connection-name>
Configuration naming convention
Service Connector sets the connection configuration when creating a connection. The environment variable key-value pairs are determined based on your client type and authentication type. For example, using the Azure SDK with a managed identity requires a client ID, client secret, etc. Using a JDBC driver requires a database connection string. Follow these conventions to name the configurations:
Spring Boot client: the Spring Boot library for each target service has its own naming convention. For example, MySQL connection settings would be
spring.datasource.url,spring.datasource.username,spring.datasource.password. Kafka connection settings would bespring.kafka.properties.bootstrap.servers.Other clients:
- The key name of the first connection configuration uses the format
<Cloud>_<Type>_<Name>. For example,AZURE_STORAGEBLOB_RESOURCEENDPOINT,CONFLUENTCLOUD_KAFKA_BOOTSTRAPSERVER. - For the same type of target resource, the key name of the second connection configuration uses the format
<Cloud>_<Type>_<Connection Name>_<Name>. For example,AZURE_STORAGEBLOB_CONN2_RESOURCEENDPOINT,CONFLUENTCLOUD_KAFKA_CONN2_BOOTSTRAPSERVER.
- The key name of the first connection configuration uses the format
Service network solution
Service Connector offers three network solutions for users to choose from when creating a connection. These solutions are designed to facilitate secure and efficient communication between resources.
Firewall: This solution allows connection through public network and compute resource accessing target resource with public IP address. When selecting this option, Service Connector verifies the target resource's firewall settings and adds a rule to allow connections from the source resource's public IP address. If the resource's firewall supports allowing all Azure resources accessing, Service Connector enables this setting. However, if the target resource denies all public network traffic by default, Service Connector doesn't modify this setting. In this case, you should choose another option or update the network settings manually before trying again.
Service Endpoint: This solution enables compute resource to connect to target resources via a virtual network, ensuring that connection traffic doesn't pass through the public network. It's only available if certain preconditions are met:
- The compute resource must have virtual network integration enabled. For Azure App Service, it can be configured in its networking settings; for Azure Spring Apps, users must set Virtual Network injection during the resource creation stage.
- The target service must support Service Endpoint. For a list of supported services, refer to Virtual Network service endpoints.
When selecting this option, Service Connector adds the private IP address of the compute resource in the virtual network to the target resource's Virtual Network rules, and enables the service endpoint in the source resource's subnet configuration. If the user lacks sufficient permissions or the resource's SKU or region doesn't support service endpoints, connection creation fails.
Private Endpoint: This solution is a recommended way to connect resources via a virtual network and is only available if certain preconditions are met:
The compute resource must have virtual network integration enabled. For Azure App Service, it can be configured in its networking settings; for Azure Spring Apps, users must set VNet injection during the resource creation stage.
The target service must support private endpoints. For a list of supported services, refer to Private-link resource.
When selecting this option, Service Connector doesn't perform any more configurations in the compute or target resources. Instead, it verifies the existence of a valid private endpoint and fails the connection if not found. For convenience, users can select the "New Private Endpoint" checkbox in the Azure portal when creating a connection. With it, Service Connector automatically creates all related resources for the private endpoint in the proper sequence, simplifying the connection creation process.
Service connection validation
When validating a connection, Service connector checks the following elements:
- The source and target resources exist.
- Source: correct connection information is registered.
- Target: correct network and firewall settings are registered.
- Source and target resources: correct authentication information is registered.
Connection deletion
When a service connection is deleted, the connection information is also deleted.
Next steps
See the following concept article to learn more about Service Connector.