Microsoft Defender for Cloud Apps istuntokäytäntöjen luominen
Microsoft Defender for Cloud Apps istuntokäytännöt tarjoavat yksityiskohtaisen näkyvyyden pilvisovelluksiin reaaliaikaisella istuntotason valvonnalla. Istuntokäytäntöjen avulla voit tehdä erilaisia toimintoja käyttäjäistunnolle määrittämäsi käytännön mukaan.
Toisin kuin käyttöoikeuskäytännöt, jotka sallivat tai estävät käytön kokonaan, istuntokäytännöt sallivat käytön istunnon valvonnan aikana. Lisää ehdollisen käyttöoikeuden sovelluksen ohjausobjekti istuntokäytäntöihin, jotta voit rajoittaa tiettyjä istuntotoimintoja.
Saatat esimerkiksi haluta antaa käyttäjille mahdollisuuden käyttää sovellusta hallitsemattomista laitteista tai tietyistä sijainneista. Saatat kuitenkin haluta rajoittaa luottamuksellisten tiedostojen lataamista kyseisten istuntojen aikana tai edellyttää, että tietyt asiakirjat on suojattu lataamis-, lataamis- tai kopiointiolta, kun sovellus lopetetaan.
Isäntäsovellukselle luotuja käytäntöjä ei ole yhdistetty mihinkään liittyviin resurssisovelluksiin. Esimerkiksi Teamsille, Exchangelle tai Gmailille luomasi käyttöoikeuskäytännöt eivät ole yhteydessä SharePointiin, OneDriveen tai Google Driveen. Jos tarvitset isäntäsovelluksen lisäksi resurssisovellukselle käytännön, luo erillinen käytäntö.
Käytettävien käytäntöjen määrää ei ole rajoitettu.
Ennen kuin aloitat, varmista, että sinulla on seuraavat edellytykset:
Defender for Cloud Apps käyttöoikeus joko erillisenä käyttöoikeutena tai osana toista käyttöoikeutta
Microsoft Entra ID P1 -käyttöoikeus joko erillisenä käyttöoikeutena tai osana toista käyttöoikeutta.
Jos käytät muuta kuin Microsoft IdP:tä, käyttäjätietopalvelusi (IdP) edellyttämä käyttöoikeus.
Aiheeseen liittyvät sovellukset, jotka on otettu käyttöön ehdollisten käyttöoikeuksien sovelluksen ohjausobjektissa. Microsoft Entra ID sovellukset otetaan automaattisesti käyttöön, kun taas muut kuin Microsoft IdP -sovellukset on otettava käyttöön manuaalisesti.
Jos käytät muuta kuin Microsoft IdP:tä, varmista, että olet myös määrittänyt IdP:si toimimaan Microsoft Defender for Cloud Apps kanssa. Lisätietoja on seuraavissa artikkeleissa:
Jotta istuntokäytäntö toimisi, sinulla on oltava myös Microsoft Entra ID Ehdollinen käyttöoikeus -käytäntö, joka luo liikenteen hallintaoikeudet.
Esimerkki: Microsoft Entra ID ehdollisten käyttöoikeuskäytäntöjen luominen Defender for Cloud Apps kanssa käytettäväksi
Tämä toimintosarja on korkean tason esimerkki siitä, miten voit luoda ehdollisen käyttöoikeuden käytännön käytettäväksi Defender for Cloud Apps kanssa.
Valitse ehdollisten käyttöoikeuksien Microsoft Entra ID Luo uusi käytäntö.
Anna käytännölle kuvaava nimi ja lisää sitten käytäntöön ohjausobjekteja valitsemalla Istunto-kohdasta linkki.
Valitse Istunto-alueellaKäytä ehdollisten käyttöoikeuksien sovellusten hallintaa.
Valitse Käyttäjät-alueella , jos haluat sisällyttää vain kaikki käyttäjät tai vain tietyt käyttäjät ja ryhmät.
Valitse Ehdot - ja Asiakassovellukset-alueilta ehdot ja asiakassovellukset, jotka haluat sisällyttää käytäntöön.
Tallenna käytäntö ottamalla Vain raportti - asetus käyttöön ja valitsemalla sitten Luo.
Microsoft Entra ID tukee sekä selainpohjaisia että ei-selainpohjaisia käytäntöjä. Suosittelemme, että luot molemmat tyypit tietoturvan lisäämiseksi.
Toista tämä toimintosarja, jos haluat luoda ehdollisten käyttöoikeuksien käytännön, joka ei ole jäsennyspohjainen. Vaihda Asiakassovellukset-alueellaMääritä-asetukseksiKyllä. Poista sitten Modernin todennuksen asiakasohjelmat -kohdassa Selain-vaihtoehto . Jätä kaikki muut oletusvalinnat valituksi.
Lisätietoja on tiedoissa Ehdollisten käyttöoikeuksien käytännöt ja Ehdollisen käyttöoikeuden käytännön luominen.
Huomautus
Microsoft Defender for Cloud Apps käyttää sovellusta Microsoft Defender for Cloud Apps – Istunnon ohjausobjektit osana käyttäjän sisäänkirjautumisen ehdollisten käyttöoikeuksien sovellusvalvontapalvelua. Tämä sovellus sijaitsee Entra-tunnuksen Yrityssovellukset-osassa. Jotta voit suojata SaaS-sovelluksia istunnon ohjausobjekteilla, sinun on sallittava tämän sovelluksen käyttö.
Jos sinulla on ehdollisia käyttöoikeuskäytäntöjä, joiden Käyttöoikeuden myöntäminen -ohjausobjektissa on valittuna tähän sovellukseen kohdistettu Microsoft Entra ID Ehdollinen käyttöoikeus -käytäntö, käyttäjät eivät voi käyttää suojattuja sovelluksia istunnon ohjausobjekteissa.
On tärkeää varmistaa, että ehdollisten käyttöoikeuksien käytännöt eivät rajoita tätä sovellusta tahattomasti. Jos käytännöt rajoittavat kaikkia tai tiettyjä sovelluksia, varmista, että tämä sovellus näkyy poikkeuksena Kohde-resursseissa , tai varmista, että estokäytäntö on tarkoituksellinen.
Jos haluat varmistaa, että sijaintiin perustuvat ehdolliset käyttöoikeuskäytännöt toimivat oikein, sisällytä näihin käytäntöihin Microsoft Defender for Cloud Apps – Istunnon hallinta -sovellus.
Näissä ohjeissa kuvataan uuden istuntokäytännön luominen Defender for Cloud Apps.
Valitse Microsoft Defender XDR Pilvisovellusten > käytännötKäytännön > hallinta > Ehdollisen käyttöoikeuden välilehti.
Valitse Luo käytäntö>Istuntokäytäntö. Esimerkki:
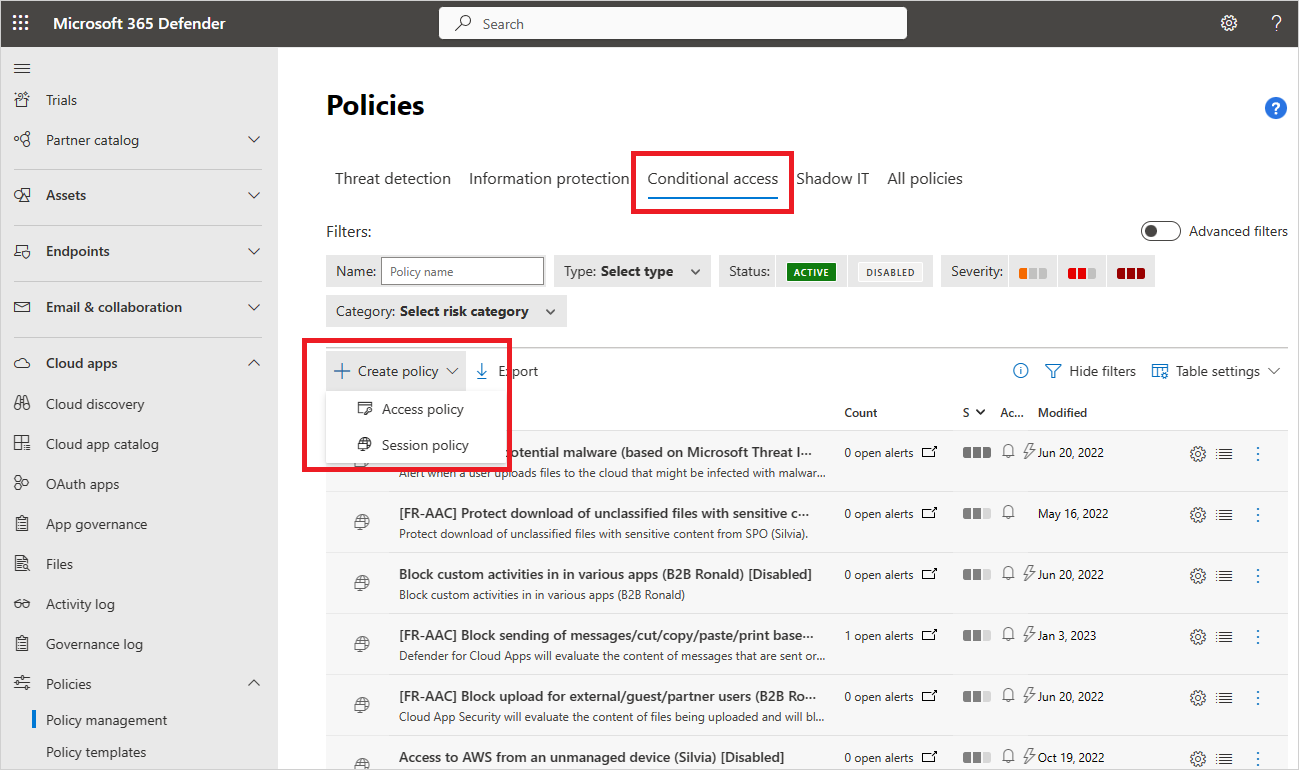
Aloita Luo istuntokäytäntö -sivulla joko valitsemalla malli avattavasta Käytäntömalli-valikosta tai kirjoittamalla kaikki tiedot manuaalisesti.
Anna seuraavat käytännön perustiedot. Jos käytät mallia, suuri osa sisällöstä on jo täytetty puolestasi.
Nimi Kuvaus Käytännön nimi Käytännölle kuvaava nimi, kuten Luottamuksellisten asiakirjojen lataamisen estäminen markkinoinnin käyttäjille -ruudussa Käytännön vakavuus Valitse käytäntöön käytettävä vakavuus. Luokka Valitse luokka, jota haluat käyttää. Kuvaus Anna valinnainen ja merkityksellinen kuvaus käytännöllesi, jotta ryhmäsi ymmärtää sen tarkoituksen. Istunnon ohjausobjektin tyyppi Valitse jokin seuraavista:
- Vain näyttö. Valvoo vain käyttäjien toimintaa ja luo Vain valvonta -käytännön valitsemiasi sovelluksia varten.
- Estä aktiviteetit. Estää tietyt toiminnot, jotka on määritetty Toimintotyyppi-suodattimella . Kaikkia valittujen sovellusten toimintoja valvotaan ja raportoidaan toimintolokissa.
- Hallitse tiedoston lataamista (tarkastuksissa). Valvoo tiedostojen latauksia, ja ne voidaan yhdistää muihin toimintoihin, kuten latausten estämiseen tai suojaamiseen.
- Ohjausobjektitiedoston lataaminen palvelimeen (tarkastuksissa). Valvoo tiedostojen latauksia, ja ne voidaan yhdistää muihin toimintoihin, kuten latausten estämiseen tai suojaamiseen.
Lisätietoja on kohdassa Istuntokäytäntöjen tuetut toiminnot.Valitse toiminnot, jotka vastaavat kaikkia seuraavia -aluetta, käytäntöön sovellettavat muut toimintosuodattimet. Suodattimet sisältävät seuraavat asetukset:
Nimi Kuvaus Toimintotyyppi Valitse käytettävä toimintotyyppi, kuten:
-Painos
- Leikepöydän toiminnot, kuten leikkaaminen, kopiointi, liittäminen
– lähettää, jakaa, peruuttaa ja muokata tuettujen sovellusten kohteita.
Käytä esimerkiksi ehtojen lähetä kohteet -toimintoa saadaksesi kiinni käyttäjän, joka yrittää lähettää tietoja Teams-keskustelussa tai Slack-kanavalla, ja estää viestin, jos se sisältää arkaluonteisia tietoja, kuten salasanan tai muita tunnistetietoja.Sovellus Suodattimet tietylle sovellukselle, joka sisällytetään käytäntöön. Valitse sovellukset valitsemalla ensin, käyttävätkö ne automaattista Azure AD perehdytystä Microsoft Entra ID sovelluksiin vai manuaaliseen perehdytykseen muissa kuin Microsoft IdP -sovelluksissa. Valitse sitten luettelosta sovellus, jonka haluat sisällyttää suodattimeen.
Jos luettelosta puuttuu muu kuin Microsoft IdP -sovelluksesi, varmista, että olet perehdyttänyt sen kokonaan. Lisätietoja on seuraavissa artikkeleissa:
- Muiden kuin Microsoft IdP -luettelosovellusten ottaminen käyttöön ehdollisten käyttöoikeuksien sovellusohjausta varten.
- Muut kuin Microsoft IdP:n mukautetut sovellukset ehdollisten käyttöoikeuksien sovellusohjausta varten
Jos päätät olla käyttämättä sovellussuodatinta, käytäntö koskee kaikkia sovelluksia, jotka on merkitty käytössä-asetuksiksi Asetukset > Pilvisovellukset > Yhdistetyt sovellukset > Ehdollisen käytön sovelluksen hallinta -sivulla.
Huomautus: Perehdyttävien sovellusten ja manuaalista perehdytystä tarvitsevien sovellusten välillä saattaa näkyä päällekkäisyyksiä. Jos suodattimessa on ristiriita sovellusten välillä, manuaalisesti perehdytyt sovellukset ovat etusijalla.Laite Suodata laitetunnisteet, kuten tietyn laitehallintamenetelmän tai laitetyyppien, kuten TIETOKONEEN, mobiililaitteen tai tabletin, osalta. IP-osoite Suodata IP-osoitteen mukaan tai käytä aiemmin määritettyjä IP-osoitetunnisteita. Sijainti Suodata maantieteellisen sijainnin mukaan. Se, että selkeästi määritettyä sijaintia ei ole, voi tunnistaa riskialttiita toimintoja. Rekisteröity IsP Suodata tietyn IsP:n aktiviteetit. Käyttäjä Suodata tietylle käyttäjälle tai käyttäjäryhmälle. Käyttäjäagentin merkkijono Suodata tietyn käyttäjäagentin merkkijono. Käyttäjäagentin tunniste Suodata käyttäjäagentin tunnisteet, kuten vanhentuneet selaimet tai käyttöjärjestelmät. Esimerkki:
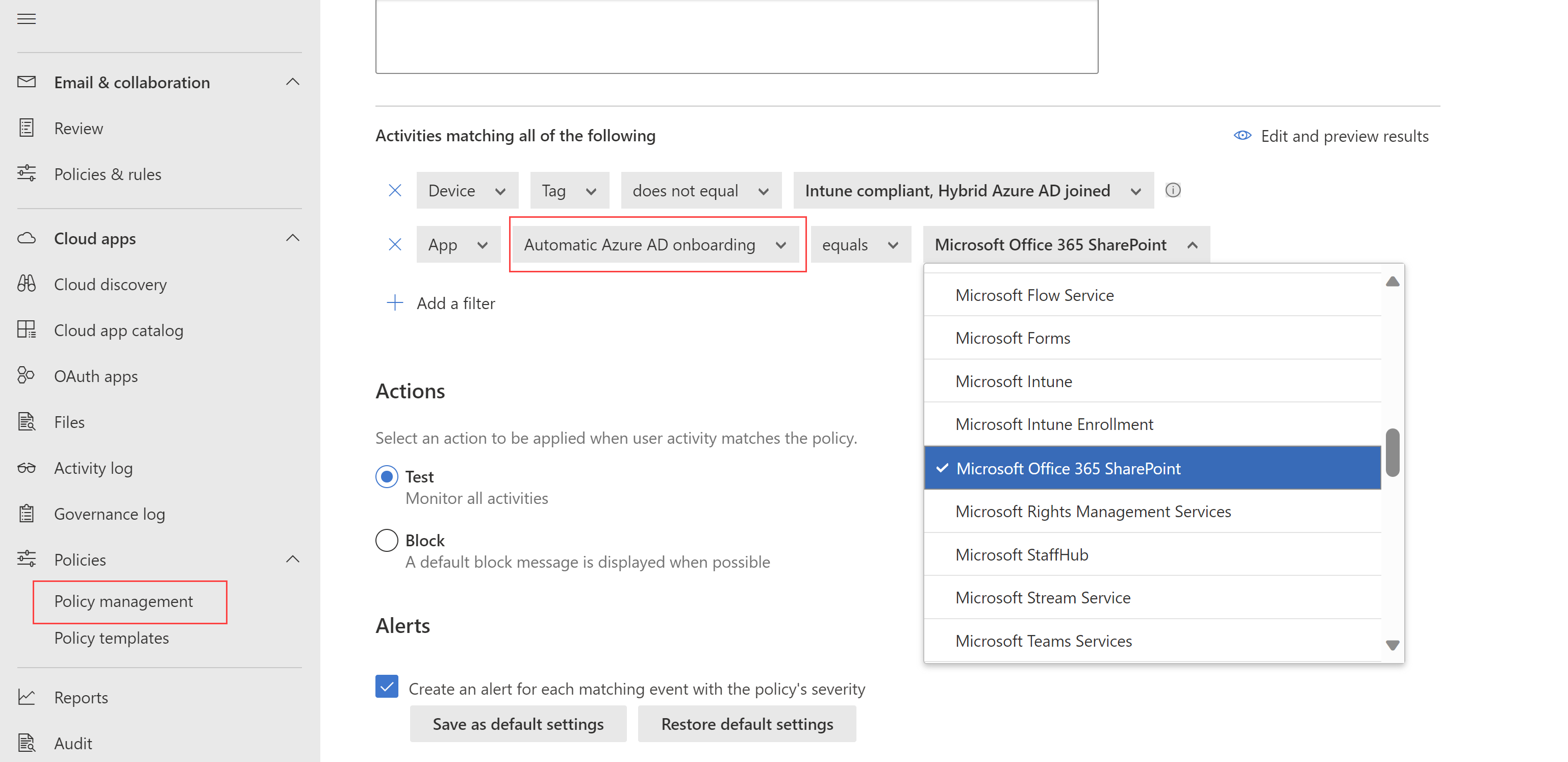
Valitse Muokkaa ja esikatsele tuloksia , jos haluat esikatsella nykyisen valintasi yhteydessä palautettavien aktiviteettien tyyppejä.
Määritä lisäasetuksia, jotka ovat käytettävissä mille tahansa tietylle istunnon ohjausobjektityypille.
Jos olet esimerkiksi valinnut Estotoiminnot, valitse Käytä sisällön tarkastusta toiminnan sisällön tarkistamiseksi ja määritä sitten asetukset tarvittaessa. Tässä tapauksessa haluat ehkä tarkistaa tekstin, joka sisältää tiettyjä lausekkeita, kuten sosiaaliturvatunnuksen.
Jos valitsit Ohjaustiedoston lataamisen (tarkastuksissa) tai Ohjausobjektin tiedoston lataamisen (tarkastuksissa), määritä tiedostot, jotka vastaavat kaikkia seuraavia asetuksia.
Määritä jokin seuraavista tiedostosuodattimista:
Nimi Kuvaus Luottamuksellisuustunniste Suodata Microsoft Purview Information Protection luottamuksellisuustunnisteiden mukaan, jos käytät myös Microsoft Purview'a ja tiedot on suojattu sen luottamuksellisuustunnisteilla. Tiedoston nimi Suodata tietyt tiedostot. Laajennus Suodata tietyt tiedostotyypit, esimerkiksi estä kaikkien .xls tiedostojen lataaminen. Tiedoston koko (Mt) Suodata tietyt tiedostokoot, kuten suuret tai pienet tiedostot. Käytä kohteeseen -alueella (esikatselu):
- Valitse, käytetäänkö käytäntöä vain määritettyjen kansioiden kaikissa tiedostoissa vai tiedostoissa
- Valitse käytettävä tarkastusmenetelmä, kuten tietojen luokituspalvelut tai haittaohjelma. Lisätietoja on artikkelissa Microsoft Data Classification Services -integrointi.
- Määritä käytännölle tarkempia asetuksia, kuten skenaarioita, jotka perustuvat esimerkiksi sormenjälkiin tai harjoitettäviin luokituksiin.
Valitse Toiminnot-alueella jokin seuraavista vaihtoehdoista:
Nimi Kuvaus Valvonta Valvoo kaikkia toimintoja. Valitse tämä, jos haluat nimenomaisesti sallia lataamisen määrittämieni käytäntösuodattimien mukaan. Estä Estää tiedostojen lataamisen ja valvoo kaikkia toimintoja. Valitse tämä, jos haluat eksplisiittisesti estää lataukset määrittämieni käytäntösuodattimien mukaan.
Estä käytännöt -ruudun avulla voit myös ilmoittaa käyttäjille sähköpostitse ja mukauttaa estoviestin.Suojaa Käyttää lataukseen luottamuksellisuustunnistetta ja valvoo kaikkia toimintoja. Käytettävissä vain, jos olet valinnut Ohjausobjektitiedoston lataamisen (tarkastuksissa)
Jos käytät Microsoft Purview Information Protection, voit myös käyttää luottamuksellisuustunnistetta vastaaviin tiedostoihin, käyttää mukautettuja käyttöoikeuksia käyttäjälle, joka lataa tiedostoja, tai estää tiettyjen tiedostojen lataamisen.
Jos sinulla on Microsoft Entra ID Ehdollinen käyttöoikeus -käytäntö, voit myös vaatia vaiheittaista todennusta (esikatselu).Vaihtoehtoisesti voit valita Käytä aina valittua toimintoa, vaikka tietoja ei voi tarkistaa käytännön tarpeen mukaan.
Määritä Ilmoitukset-alueella jokin seuraavista toiminnoista tarvittaessa:
- Luo hälytys kullekin vastaavalle tapahtumalle, jolla on käytännön vakavuus
- Lähetä ilmoitus sähköpostiviestinä
- Päivittäinen ilmoitusrajoitus käytäntöä kohti
- Ilmoitusten lähettäminen Power Automateen
Kun olet valmis, valitse Luo.
Kun olet luonut istuntokäytännön, testaa sitä todentamalla se uudelleen jokaiseen käytännössä määritettyihin sovelluksiin ja testaamalla käytännössä määrittämäsi skenaario.
Suosittelemme, että teet seuraavaa:
- Kirjaudu ulos kaikista nykyisistä istunnoista ennen sovelluksiin todentamista uudelleen.
- Kirjaudu sisään mobiili- ja työpöytäsovelluksiin sekä hallituista että hallitsemattomista laitteista varmistaaksesi, että toiminnot tallennetaan täysin toimintalokiin.
Varmista, että kirjaudut sisään käyttäjällä, joka vastaa käytäntöäsi.
Voit testata käytäntöä sovelluksessasi:
Tarkista, näkyykö
 lukituskuvake selaimessasi vai käytätkö muuta selainta kuin Microsoft Edgeä, tarkista, että sovelluksen URL-osoitteessa
lukituskuvake selaimessasi vai käytätkö muuta selainta kuin Microsoft Edgeä, tarkista, että sovelluksen URL-osoitteessa .mcason jälkiliite. Lisätietoja on artikkelissa selaimen suojaus Microsoft Edge for Business (esikatselu) avulla.Käy kaikilla sovelluksen sivuilla, jotka ovat osa käyttäjän työprosessia, ja varmista, että sivut hahmonnetaan oikein.
Varmista, että yleisten toimintojen, kuten tiedostojen lataaminen ja lataaminen, suorittaminen ei vaikuta haitallisesti sovelluksen toimintaan.
Jos käytät mukautettuja muita kuin Microsoft IdP -sovelluksia, tarkista jokainen toimialue, jonka olet lisännyt manuaalisesti sovellukseen.
Jos kohtaat virheitä tai ongelmia, kerää järjestelmänvalvojan työkalurivin avulla resursseja, kuten .har tiedostoja ja tallennettuja istuntoja tukipalvelupyynnön tekemistä varten.
Päivitysten tarkistaminen Microsoft Defender XDR:
Siirry Microsoft Defender-portaalinPilvisovellukset-kohdassakohtaan Käytännöt ja valitse sitten Käytäntöjen hallinta.
Valitse luomasi käytäntö, jotta voit tarkastella käytäntöraporttia. Istuntokäytännön vastaavuus pitäisi näkyä pian.
Käytäntöraportti näyttää, mitkä kirjautumiset on ohjattu Microsoft Defender for Cloud Apps istunnon hallintaa varten, sekä muita toimintoja, kuten se, mitkä tiedostot ladattiin tai estettiin valvotuista istunnoista.
Oletusarvoisesti käyttäjille ilmoitetaan, kun heidän istuntojaan valvotaan. Jos haluat, että käyttäjille ei ilmoiteta asiasta, tai jos haluat mukauttaa ilmoitussanomaa, määritä ilmoitusasetukset.
Valitse Microsoft Defender XDR Asetukset > Pilvisovellukset > Ehdollisten käyttöoikeuksien sovellusten valvonta > Käyttäjän valvonta.
Tee jokin seuraavista valintoista:
- Tyhjennä Ilmoita käyttäjille, että heidän toimintaansa valvotaan -vaihtoehto kokonaan
- Säilytä valinta ja valitse käyttääksesi joko oletusviestiä tai mukauttaaksesi viestiäsi.
Valitsemalla Esikatselu-linkin voit tarkastella määritetyn viestin esimerkkiä uudessa selainvälilehdessä.
Ehdollinen käyttöoikeussovellusten valvonta tallentaa jokaisen käyttäjäistunnon liikennelokit, jotka reititetään sen läpi. Liikennelokit sisältävät ajan, IP-osoitteen, käyttäjäagentin, vieraillut URL-osoitteet sekä ladattujen ja ladattujen tavujen määrän. Näitä lokeja analysoidaan, ja jatkuva raportti, Defender for Cloud Apps ehdollisten käyttöoikeuksien sovellusten hallinta, lisätään pilvianalyysiraporttien luetteloon pilvietsintäkoontinäytössä.
Pilvitietojen etsintälokien vieminen pilven resurssienetsinnän koontinäytöstä:
Valitse Microsoft Defender portaalissa Asetukset. Valitse sitten Pilvisovellukset. Valitse Yhdistetyt sovellukset -kohdassa Ehdollisen käyttöoikeuden sovellusten hallinta.
Valitse vientipainike taulukon yläpuolelta. Esimerkki:
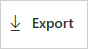
Valitse raportin alue ja valitse Vie. Tämä prosessi voi kestää jonkin aikaa.
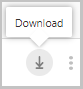
Jos haluat ladata viedyn lokin, kun raportti on valmis, siirry Microsoft Defender-portaalissa kohtaan Raportit –>Pilvisovellukset ja sitten Viedyt raportit.
Valitse taulukossa asianmukainen raportti ehdollisen käyttösovelluksen hallinnan liikennelokien luettelosta ja valitse Lataa. Esimerkki:
Seuraavissa osioissa on lisätietoja jokaisesta toiminnosta, jota Defender for Cloud Apps istuntokäytännöt tukevat.
Vain valvonta-istunnon ohjausobjektin tyyppi valvoo vain kirjautumistoimintoa.
Jos haluat valvoa muita toimintoja, valitse jokin muu istunnon ohjausobjektityyppi ja käytä Valvonta-toimintoa.
Jotta voit valvoa muita toimintoja kuin latauksia ja latauksia, valvontakäytännössä on oltava vähintään yksi esto toimintakäytäntöä kohden .
Kun Ohjausobjektin tiedoston lataaminen (tarkastuksen yhteydessä) määritetään istunnon ohjausobjektin tyypiksi ja toiminnoksi on määritetty Estä, Ehdollinen käyttö -sovelluksen valvonta estää käyttäjiä lataamasta tiedostoa käytäntötiedostosuodattimia kohden.
Kun käyttäjä käynnistää latauksen, käyttäjälle tulee näkyviin rajoitettu latausviesti ja ladattu tiedosto korvataan tekstitiedostolla. Määritä tekstitiedoston sanoma käyttäjälle organisaatiosi tarpeen mukaan.
Edellytä vaiheittaista todentamista -toiminto on käytettävissä, kun istunnon ohjausobjektin tyyppi on Block activities, Control file download (with inspection) tai Control file upload (ja tarkistus) .
Kun tämä toiminto on valittuna, Defender for Cloud Apps ohjaa istunnon uudelleen Microsoft Entra Ehdollinen käyttöoikeus käytännön uudelleenarviointia varten aina, kun valittu toiminto ilmenee.
Tämän asetuksen avulla voit tarkistaa istunnon aikana väitteet, kuten monimenetelmäisen todentamisen ja laitteiden yhteensopivuuden, Microsoft Entra ID määritetyn todennuskontekstin perusteella.
Kun Estä aktiviteetit on määritetty istunnon ohjausobjektin tyypiksi, valitse tietyt toiminnot, jotka estetään tietyissä sovelluksissa.
Kaikkia määritettyjen sovellusten toimintoja valvotaan ja raportoidaan pilvisovellusten > toimintalokissa.
Jos haluat estää tietyt aktiviteetit, valitse edelleen Estä-toiminto ja valitse aktiviteetit, jotka haluat estää.
Jos haluat herättää ilmoituksia tietyistä toiminnoista, valitse Valvonta-toiminto ja määritä ilmoitusasetukset.
Saatat esimerkiksi haluta estää seuraavat toimet:
Lähetti Teams-viestin. Estä käyttäjiä lähettämästä viestejä Microsoft Teamsista tai estä tiettyä sisältöä sisältäviä Teams-viestejä.
Tulosta. Estä kaikki tulostustoiminnot.
Selvä, selvä. Estä kaikki kopiointi leikepöydälle -toiminnot tai estä kopiointi vain tiettyä sisältöä varten.
Valitse Estä aktiviteetit-istunnon ohjausobjektityyppi, jos haluat estää tietyt toiminnot, jotka määrität Aktiviteettityyppi-suodattimen avulla.
Kaikkia määritettyjen sovellusten toimintoja valvotaan ja raportoidaan pilvisovellusten > toimintalokissa.
Valitse Estä-toiminto tiettyjen toimintojen estämiseksi tai valitse Valvonta-toiminto ja määritä ilmoitusasetukset tiettyjen toimintojen ilmoitusten nostamiseksi.
Valitse Suojaa-toiminto, jos haluat suojata tiedostot, joilla on luottamuksellisuustunnisteet ja muut suojaukset käytännön tiedostosuodattimien mukaan.
Luottamuksellisuustunnisteet on määritetty Microsoft Purview'ssa, ja ne on määritettävä käyttämään salausta, jotta ne näkyvät asetuksena Defender for Cloud Apps istuntokäytännössä.
Kun olet määrittänyt istuntokäytännön tietyllä tunnisteella ja käyttäjä lataa tiedoston, joka täyttää käytännön ehdot, tiedostossa käytetään tunnistetta ja sitä vastaavia suojauksia ja käyttöoikeuksia.
Alkuperäinen tiedosto säilyy sellaisena kuin se oli pilvisovelluksessa, kun ladattu tiedosto on suojattu. Käyttäjien, jotka yrittävät käyttää ladattua tiedostoa, on täytettävä käyttöön otetun suojauksen määrittämät käyttöoikeusvaatimukset.
Defender for Cloud Apps tukee tällä hetkellä luottamuksellisuustunnisteiden käyttämistä Microsoft Purview Information Protection seuraavissa tiedostotyypeissä:
- Word: docm, docx, dotm, dotx
- Excel: xlam, xlsm, xlsx, xltx
- PowerPoint: potm, potx, ppsx, ppsm, pptm, pptx
Huomautus
PDF-tiedostoissa on oltava yhdistetyt selitteet.
Suojaa-vaihtoehto ei tue tiedostojen korvaamista istuntokäytännöissä aiemmin luodulla tunnisteella.
Valitse Ohjausobjektitiedoston lataaminen palvelimeen (tarkastusta käyttäen)-istunnon ohjausobjektityyppi estääksesi käyttäjää lataamasta tiedostoa käytännön tiedostosuodattimien mukaisesti.
Jos ladattavassa tiedostossa on luottamuksellisia tietoja eikä sillä ole oikeaa tunnistetta, tiedoston lataaminen estetään.
Luo esimerkiksi käytäntö, joka tarkistaa tiedoston sisällön ja määrittää, sisältääkö se arkaluontoista sisältöä, kuten sosiaaliturvatunnuksen. Jos se sisältää luottamuksellista sisältöä eikä sen tunnisteena ole luottamuksellisuustunniste Microsoft Purview Information Protection Luottamuksellinen, tiedoston lataaminen estetään.
Vihje
Määritä käyttäjälle mukautettu viesti, kun tiedosto on estetty, opastamalla häntä nimeämään tiedosto latausta varten ja varmistamalla, että pilvisovelluksiin tallennetut tiedostot noudattavat käytäntöjäsi.
Lisätietoja on artikkelissa Käyttäjien kouluttaminen luottamuksellisten tiedostojen suojaamiseksi.
Valitse Valvontatiedoston lataaminen (tarkastuksella) tai Ohjausobjektin tiedoston lataus (tarkastuksella)istunnon ohjausobjektin tyypiksi ja Haittaohjelmien havaitseminentarkastusmenetelmäksi estääksesi käyttäjää lataamasta tai lataamasta tiedostoa haittaohjelmalla. Tiedostot skannataan haittaohjelmien takia Microsoftin uhkatietomoduulin avulla.
Näytä mahdolliset haittaohjelmaksi merkityt tiedostot pilvisovellusten > toimintalokissa suodattamalla mahdollisten haittaohjelmien havaittujen kohteiden mukaan. Lisätietoja on kohdassa Toimintosuodattimet ja kyselyt.
Suosittelemme, että koulutat käyttäjiä, kun he rikkovat käytäntöjäsi, jotta he oppivat noudattamaan organisaatiosi vaatimuksia.
Koska jokaisella yrityksellä on yksilöllisiä tarpeita ja käytäntöjä, Defender for Cloud Apps avulla voit mukauttaa käytännön suodattimia ja sanomaa, joka näytetään käyttäjälle, kun virhe havaitaan.
Anna käyttäjille erityisiä ohjeita, kuten ohjeet tiedoston asianmukaiseen merkitsemiseen tai hallitsemattoman laitteen rekisteröinti tiedostojen onnistuneen lataamisen varmistamiseksi.
Jos käyttäjä esimerkiksi lataa tiedoston ilman luottamuksellisuustunnistetta, määritä näytettävä viesti ja selitä, että tiedosto sisältää luottamuksellista sisältöä ja vaatii asianmukaisen tunnisteen. Vastaavasti jos käyttäjä yrittää ladata asiakirjan hallitsemattomasta laitteesta, määritä näytettävä viesti, joka sisältää ohjeet laitteen rekisteröintiin, tai viesti, joka antaa lisäselitystä siitä, miksi laite on rekisteröitävä.
Monet organisaatiot, jotka päättävät hallita istunnon sisäisiä toimintoja pilvisovellusten istunto-ohjausobjektien avulla, käyttävät myös käyttöoikeuksien hallintaa estääkseen samat sisäiset mobiili- ja työpöytäasiakassovellukset, mikä tarjoaa kattavan suojauksen sovelluksille.
Estä pääsy sisäisiin mobiili- ja työpöytäasiakassovelluksiin käyttöoikeuskäytännöillä määrittämällä Asiakassovellus-suodattimen arvoksi Mobiili ja työpöytä. Jotkin sisäiset asiakassovellukset voidaan tunnistaa yksitellen, kun taas toiset, jotka ovat osa sovelluspakettia, voidaan tunnistaa vain ylimmän tason sovellukseksi. Esimerkiksi SharePoint Onlinen kaltaiset sovellukset tunnistetaan vain luomalla Microsoft 365 -sovelluksiin sovellettava käyttöoikeuskäytäntö.
Huomautus
Ellei Asiakassovellus-suodatinta ole erikseen määritetty mobiili- ja työpöytäsovellukseen, käyttöoikeuskäytäntö koskee vain selainistuntoja. Tämän tarkoituksena on estää käyttäjäistuntojen välityspalvelinten välitysvälitys vahingossa.
Vaikka useimmat selaimet tukevat asiakasvarmenteiden tarkistusta, jotkin mobiili- ja työpöytäsovellukset käyttävät sisäisiä selaimia, jotka eivät ehkä tue tätä tarkistusta. Tämän vuoksi tämän suodattimen käyttäminen voi vaikuttaa näiden sovellusten todentamiseen.
Kun kahden istuntokäytännön välillä on ristiriita, rajoittavampi käytäntö voittaa.
Esimerkki:
- Jos käyttäjäistunto vastaa molempia käytäntöjä, joissa lataukset on estetty
- Ja käytäntö, jossa tiedostot merkitään ladattaessa tai joissa latauksia valvotaan,
- Tiedoston lataaminen on estetty, jotta se noudattaa rajoittavampaa käytäntöä.
Lisätietoja on seuraavissa artikkeleissa:
- Käyttöoikeuksien ja istunnon ohjausobjektien vianmääritys
- Opetusohjelma: Luottamuksellisten tietojen lataamisen estäminen ehdollisten käyttöoikeuksien sovellusohjausobjektilla
- Hallitsemattomien laitteiden latausten estäminen istunnon ohjausobjektien avulla
- Ehdollisten käyttöoikeuksien sovellusten hallinnan verkkoseminaari
Jos kohtaat ongelmia, olemme täällä auttamassa. Jos haluat apua tai tukea tuoteongelmaasi varten, avaa tukipyyntö.