Transparency logs (preview)
Important
This is a preview feature. This information relates to a prerelease feature that may be substantially modified before it's released. Microsoft makes no warranties, expressed or implied, with respect to the information provided here.
Governments across the world want to use the benefits of the hyperscale cloud but require assurances that Microsoft as their cloud provider handles data in a manner that respects their sovereignty requirements and also allows them to audit Microsoft engineers' access to their cloud resources.
To earn the trust of sovereign customers, Microsoft uses transparency logs to provide customers with visibility into occasions when Microsoft engineers accessed customer resources using the Just-In-Time access service. These transparency logs give sovereign customers visibility above and beyond what the Azure commercial cloud currently provides.
On rare occasions, Microsoft engineers need to directly access customer resources. The access is typically required in response to customer support requests. In such situations, Microsoft engineers can be granted temporary access with valid business justification. Along with providing details of the access to customer resources, the transparency logs also inform you when there's no access, which is the most likely case.
What you can do with transparency logs
Transparency logs provide details of when Microsoft engineers accessed your resources, to assist with sovereign compliance and other regulatory requirements. The logs help answer the following questions related to the accessed resources and the Microsoft engineers who accessed them:
Resource details:
- Which subscriptions were accessed?
- When did the access occur?
- On what Azure service did the access occur?
Microsoft engineer details:
- What is the role of the engineer who accessed the resource?
- What is the assigned office location of the engineer?
- How long did the engineer have access to the resource?
Details covered in transparency logs
The following screenshot shows session details of a support engineer's access to the Azure kubernetes service in the customer environment.
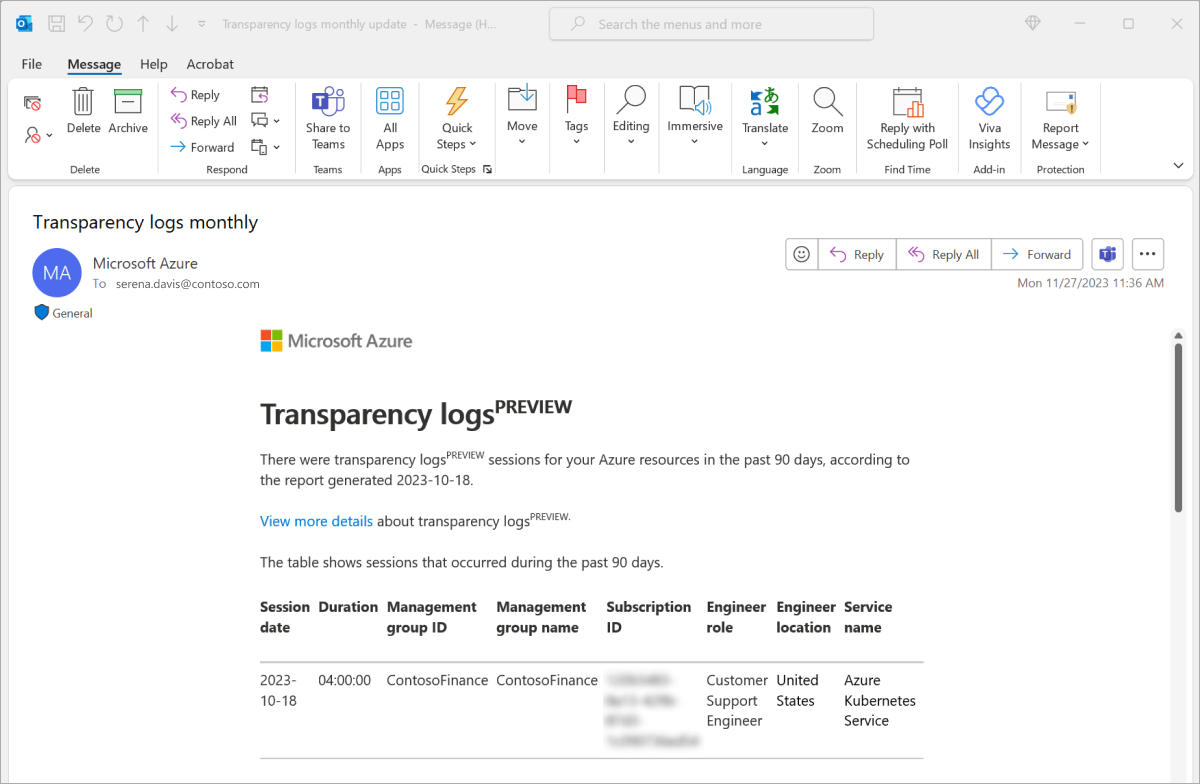
Transparency logs typically contain the following details:
- Tenant ID: Unique identifier of the tenant for which the report was generated.
- Tenant name: Name of the tenant for which the report was generated.
- Session date: Date and time the access was granted.
- Duration: Maximum duration of access.
- Management group ID: Management group ID that the subscription belongs to. The value of this field might be Not available in cases where this detail isn't available.
- Management group name: Management group name that the subscription belongs to. The value of this field might be Not available in cases where this detail isn't available.
- Subscription ID: Unique identifier of the subscription that was accessed.
- Engineer role: Customer Support Engineer or DevOps Engineer.
- Engineer location: Assigned office location of the engineer that requested access.
- Service name: Public name of the Azure service.
Scope of transparency logs
The transparency logs are scoped to Microsoft Azure resources in your Azure tenant. The logs provide access details by Microsoft engineers within 90 days of the report generation date. You'll receive the updated logs via email on the first Wednesday of every month.
The report doesn't contain details of a Microsoft engineer's access to the following resources and services:
- Hardware in the Azure data center. To learn about the access privileges for Microsoft data center engineers, see Service-management-and-service-teams.
- Microsoft 365 services
- Microsoft Dynamics 365 services
- Microsoft Power Platform
The report also doesn't contain information about the following accesses and requests:
- Access by the customer's engineers or other identities. See Entra sign-in logs.
- Government requests for data. For more information on how Microsoft responds to government requests for data, see Law Enforcement Requests Report.
Enablement
To request access to this preview feature, follow these instructions:
Sign into the Azure portal.
Search for Regulated Environment Manager in the search bar of the home page, and select the particular service from the list of search results.
Select Transparency logs in the Regulated Environment Management | Getting Started screen.
Select Request Private Preview and fill out the form to request access.
FAQs on transparency logs
1. What do transparency logs add to the observability capabilities that Microsoft already offers?
Transparency logs provide customers with visibility into the operational activities of Microsoft engineers to support customer service and service reliability issues, including a record of such accesses to their resources via the the Just-In-Time access service. The access records augment the information available in other logs, such as activity logs, resource logs, security event logs, Microsoft Entra logs, and Customer Lockbox for Azure logs.
2. Who are the intended customers and users?
Transparency logs support public sector and regulated industry organizations. These customers have strict requirements around auditability and access control.
3. Is every customer support case represented in the transparency logs?
No. Most customer support cases are resolved without the need for the engineer to directly access the customer resources. So, transparency log records aren't created.