Device profiles
You can think of device profiles as being part of a hierarchy of device configuration options.
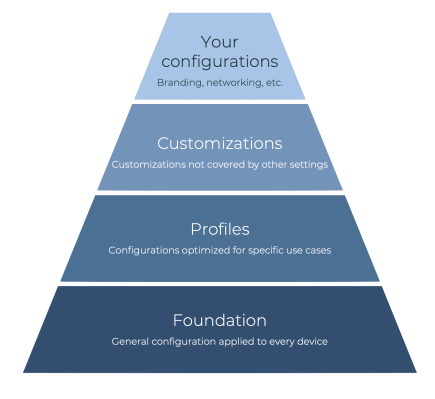
| Device configuration options | Description |
|---|---|
| Your configurations | At the top are your own configurations, such as network details or applications. A device can have any number of these configurations, which aren't managed or blocked by Microsoft Managed Desktop. |
| Customizations | The next higher level is more customizations. Each device can have one or more (or no) customizations. The customizations can either:
|
| Device profiles | Every Microsoft Managed Desktop device must have one, and only one, profile assigned. Admins can select which profile a device is assigned. You can assign different pre-set profiles to devices. Each profile is optimized for the needs of specific types of users. Three device profiles are available:
|
| Foundation | Fundamentally, every Microsoft Managed Desktop device has a foundation that includes:
To work with Microsoft Managed Desktop, every device must include all of these elements. These elements can't be changed by admins. You must submit a request to Microsoft Managed Desktop. |
Device profile details
The following table summarizes the settings and their default values for each setting configured by device profiles. Behind the scenes, these settings are configured with OMA-URIs by using Custom Configuration Profiles in the Microsoft Intune admin center.
| Feature | Sensitive Data | Power User | Standard | Kiosk |
|---|---|---|---|---|
| Block External Storage | Yes | Yes | No | Yes |
| Cloud Block Level | High | High | High | High |
| Disable Microsoft Accounts | Yes | Yes | No | Yes |
| Disable personal OneDrive | Yes | Yes | No | Yes |
| Switch to secure desktop for elevation | No | Yes | No | No |
| Microsoft Defender for Endpoint Device Tag | M365Managed-SensitiveData | M365Managed-PowerUser | M365Managed-Standard | M365Managed-Kiosk |
| Admin on the device? | No | Yes | No | No |
| Autopilot Profile | Modern Workplace Autopilot Profile | Modern Workplace Autopilot Profile Power User | Modern Workplace Autopilot Profile | Modern Workplace Autopilot Profile Kiosk |
| AppLocker | Yes | No | No | No |
| Block Public Store | Yes | Yes | No | Yes |
Each device profile also involves these items:
- A dynamic membership Microsoft Entra device group.
- A static membership Microsoft Entra device group.
- A Microsoft Intune configuration profile.
Important
Don't modify the membership of these groups directly. Use the interface as described in Reassign profiles.
Note
To fully turn on the Power User profile on a Windows 365 device, you must set the Enable Local Admin in the Windows 365 User Settings and add the user to the assigned group. For more information, see Make a user a local admin.
Limitations
You can request exceptions to the device profiles and their details as you would with any other policy.
You can only have one of each device profile in your Microsoft Entra organization ("tenant"). For example, you can't request that the Sensitive data device profile disables AppLocker for only some of your users. All devices with the sensitive data device profile must have the same configuration.
Each device can only have one profile. If a given device is used by more than one user, all users on that device will have the same configuration.
Export admin CSV
Devices that are assigned the Power user device profile also include user(s) in the administrator group. As an IT admin, you can download and view all users and groups assigned to the local administrators group.
To export the CSV file:
- In Microsoft Intune admin center, select Devices in the left pane.
- In the Microsoft Managed Desktop section, select Devices.
- Select the Export menu option and select Export admins. A CSV file is downloaded.
The CSV includes:
- Information retrieved from all devices that have been active in the last 28 days.
- Data that's refreshed once a day at midnight. The content is refreshed every 24 hours.
- The device profile names and can be filtered for Power user device profiles.
- Members of the local administrators' group that include Microsoft Entra groups, the group will include a (G) suffix. Disabled accounts will include a (D) suffix.
- Some data that will appear as GUIDs. Data that appears as GUIDs is because we're unable to determine the usernames. We only gather the usernames as displayed on the local device.