Intune role-based access control for tenant-attached clients
Applies to: Configuration Manager (current branch)
Starting in Configuration Manager version 2207, you can use Intune role-based access control (RBAC) when interacting with tenant attached devices from the Microsoft Intune admin center. For example, when using Intune as the role-based access control authority, a user with the Help Desk Operator role doesn't need an assigned security role or additional permissions from Configuration Manager. Intune role-based access control manages the permissions to all cloud-attached device pages in the Microsoft Intune admin center, such as device timeline, CMPivot, and scripts.
Important
Currently, any enforcement of Intune role-based access control for displaying and taking actions on tenant-attached devices from the Microsoft Intune admin center is optional. We recommend all admins with cloud-connected Configuration Manager environments begin verifying the role-based access control permissions from Intune.
The three high-level steps to configure Intune as the role-based access control authority for tenant-attached devices are:
- From the Configuration Manager console, disable enforcement of Configuration Manager role-based access control for cloud-attached clients
- From Intune, enable managing the user permissions for cloud-attached devices
- From Intune, verify role-based access control permissions for cloud-attached devices
Prerequisites
- Configuration Manager version 2207 or later
- Tenant attached devices
Limitations
- Currently scoping isn't supported when using only Intune role-based access control for for displaying and taking actions on tenant-attached devices from the Microsoft Intune admin center.
- Currently, the Software updates page isn't available for cloud-only users when using the early update ring of Configuration Manager version 2207.
Disable enforcement of Configuration Manager role-based access control for cloud-attached clients
To use Intune role-based access control for tenant attach rather than Configuration Manager role-based access control, use the instructions below:
From the Configuration Manager console, go to, Administration > Cloud Services > Cloud Attach.
The location of the role-based access control option varies depending on if your environment is already cloud-attached or not.
- If your environment is already cloud-attached, open the properties for CoMgmtSettingsProd. If you don't have devices uploaded to the admin center, configure that option first. For more information, see Enable cloud attach.
- If your environment isn't cloud-attached, select Configure Cloud Attach to open the Cloud Attach Configuration wizard.
On the Configure upload tab, or page in the wizard, clear the checkbox for the following option under the Role-based Access Control heading:
Enforce Configuration Manager RBAC for cloud console requests that interact with Configuration Manager
Choose OK to save the change to the CoMgmtSettingsProd properties, or continue on to complete the cloud attach wizard.
Enable role-based access control from Intune
To enable Intune to manage user permissions for cloud-attached devices, use the following steps:
- Open the Microsoft Intune admin center and sign in as a user that has the Roles/Update permission. For more information about the permission, see custom role permissions in Intune.
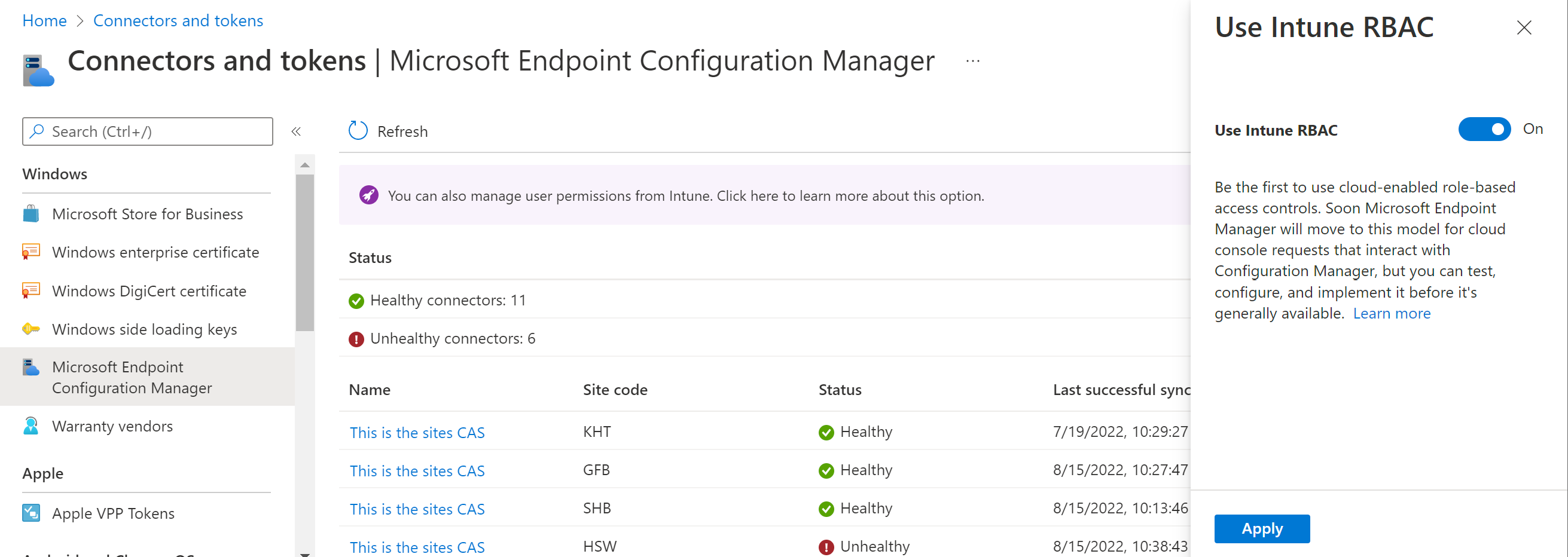
- Select Tenant administration > Connectors and tokens > Microsoft Endpoint Configuration Manager.
- In the banner, select You can also manage user permissions from Intune. Click here to learn more about this option.
- The Use Intune RBAC flyout appears.
- Select On for the Use Intune RBAC option, then choose Apply.
- The change may take about 10 minutes to take effect.
Verify role-based access control permissions from Intune
Once Intune is set to the role-based access control authority, verify the permissions for your roles. If needed, you can add these permissions to custom roles you created in Intune.
- Open the Microsoft Intune admin center and sign in.
- Select Tenant administration > Roles.
- Select a role, such as Application Manager, and review the permissions listed for Cloud attached devices. If needed, edit permissions for any custom roles you created in Intune.
The following Intune permissions control access to the Configuration Manager cloud-attached devices:
| Permission | Description | Intune built-in roles with the permission |
|---|---|---|
| Cloud attached devices\View collections | Displays the Collections page for Configuration Manager cloud attached devices | Application Manager, Endpoint Security Manager, Read Only Operator, School Administrator, Policy Profile Manager, Help Desk Operator |
| Cloud attached devices\View resource explorer | Displays the Resource explorer page for Configuration Manager cloud attached devices | Application Manager, Endpoint Security Manager, Read Only Operator, School Administrator, Policy Profile Manager, Help Desk Operator |
| Cloud attached devices\View timeline | Displays the Timeline page for Configuration Manager cloud attached devices | Application Manager, Endpoint Security Manager, Read Only Operator, School Administrator, Policy Profile Manager, Help Desk Operator |
| Cloud attached devices\View software updates | Displays the Software updates page for Configuration Manager cloud attached devices | Application Manager, Endpoint Security Manager, Read Only Operator, School Administrator, Help Desk Operator |
| Cloud attached devices\View scripts | Displays the Scripts page for Configuration Manager cloud attached devices | Endpoint Security Manager, Read Only Operator, School Administrator, Policy Profile Manager, Help Desk Operator |
| Cloud attached devices\Run script | Displays the Run script action and allows the user to run scripts on Configuration Manager cloud attached devices | School Administrator, Help Desk Operator |
| Cloud attached devices\Run CMPivot query | Displays the CMPivot page for Configuration Manager cloud attached devices | Endpoint Security Manager, School Administrator, Help Desk Operator |
| Cloud attached devices\View client details | Displays the Client details page for Configuration Manager cloud attached devices | Application Manager, Endpoint Security Manager, Read Only Operator,School Administrator, Policy Profile Manager, Help Desk Operator |
| Cloud attached devices\View applications | Displays the Applications page for Configuration Manager cloud attached devices | Application Manager, Read Only Operator, School Administrator, Policy Profile Manager, Help Desk Operator |
| Cloud attached devices\Take application actions | Displays application actions in the Applications page and allows the user to take application actions on Configuration Manager cloud attached devices | Application Manager, School Administrator, Help Desk Operator |
| Remote tasks/Rotate BitLockerKeys (preview) | Initiates a key rotation for BitLocker Recovery Passwords on the device. Displays the Recovery keys page for Configuration Manager cloud attached devices. | Endpoint Security Manager, Help Desk Operator |
Frequently asked questions
I have cloud-only users that need access to tenant-attached devices in Intune, will this give them access?
Yes. When a user is cloud only, in this scenario meaning they are in Microsoft Entra ID and can access Intune, using Intune RBAC will give them access to tenant-attached devices.
What if I have multiple Configuration Manager hierarchies connected to my tenant?
The Use Intune RBAC setting in the Microsoft Intune admin center applies to all of the Configuration Manager hierarchies listed in the tenant.
What happens if the Configuration Manager and Intune settings are mismatched?
If the Use Intune RBAC toggle in Intune is set to Off, then Configuration Manager role-based access will be enforced, even if the Enforce Configuration Manager RBAC for cloud console requests that interact with Configuration Manager checkbox is cleared. Disabling the Enforce Configuration Manager RBAC for cloud console requests that interact with Configuration Manager option doesn't have any effect until the Use Intune RBAC toggle in Intune is set to On.
What happens if my test hierarchy is configured to use Intune RBAC, but my production hierarchy isn't and they are in the same tenant?
The Use Intune RBAC setting applies to all of the Configuration Manager hierarchies listed in the tenant. Cloud-only users can access tenant-attached devices that are uploaded from the test hierarchy because you've also cleared the checkbox to enforce Configuration Manager RBAC. If a cloud-only user tries to access a tenant-attached device uploaded from the production environment, they'll receive an error since production devices are enforcing Configuration Manager RBAC. The cloud-only user will receive an error similar to the following message:
Unable to get device information. Make sure Azure AD and AD user discovery are configured and the user is discovered by both. Verify that the user has proper permissions in Configuration Manager.