Explore insider risk management
Microsoft Purview Insider Risk Management is a compliance solution that helps organizations minimize internal risks by enabling them to detect, investigate, and act on malicious and inadvertent activities. Insider risk policies enable an organization to define the types of risks to identify and detect, including acting on cases and escalating cases to Microsoft eDiscovery (Premium) if needed. Risk analysts in an organization can quickly take appropriate actions to ensure users are compliant with their organization's compliance standards.
Modern risk pain points
Managing and minimizing risk in an organization starts with understanding the types of risks found in the modern workplace. External events and factors that are outside of an organization's direct control drive some risks. Internal events and user activities that organizations can minimize and avoid drive other risks. Some examples are risks from illegal, inappropriate, unauthorized, or unethical behavior and actions by an organization's users. These behaviors include a broad range of internal risks from users:
- Leaks of sensitive data and data spillage
- Confidentiality violations
- Intellectual property (IP) theft
- Fraud
- Insider trading
- Regulatory compliance violations
Users in the modern workplace have access to create, manage, and share data across a broad spectrum of platforms and services. In most cases, organizations have limited resources and tools to identify and mitigate organization-wide risks while also meeting user privacy standards.
Insider risk management uses the full breadth of service and third-party indicators. These indicators help organizations quickly identify, triage, and act on risk activity. By using logs from Microsoft 365 and Microsoft Graph, Insider risk management enables an organization to define specific policies to identify risk indicators. These policies enable it to identify risky activities and to act to mitigate these risks.
Insider risk management centers around the following principles:
- Transparency. Balance user privacy versus organization risk with privacy-by-design architecture.
- Configurable. Configurable policies based on industry, geographical, and business groups.
- Integrated. Integrated workflow across Microsoft Purview solutions.
- Actionable. Provides insights to enable reviewer notifications, data investigations, and user investigations.
Identifying potential risks with analytics
Insider risk management analytics enables an organization to conduct an evaluation of potential insider risks without configuring any insider risk policies. This evaluation can help an organization:
- Identify potential areas of higher user risk.
- Determine the type and scope of Insider risk management policies it may consider configuring.
- Determine needs for extra licensing or future optimization of existing policies.
Note
Analytics scan results may take up to 48 hours before insights are available as reports for review.
Additional reading. For more information about analytics insights, see Insider risk management settings: Analytics.
Additional viewing. For more information on how analytics can accelerate the identification of potential insider risks and help organizations quickly take action, watch the following short Insider Risk Management Analytics video.
To enable insider risk analytics, you must be a member of the Insider Risk Management, Insider Risk Management Admin, or Microsoft 365 Global admin role group.
Complete the following steps to enable insider risk analytics:
- In the Microsoft Purview compliance portal, select Insider risk management in the navigation pane.
- Select Run scan on the Scan for insider risks in your organization card on the Insider risk management Overview tab. This action turns on analytics scanning for your organization. You can also turn on scanning in your organization by navigating to Insider risk settings, then Analytics and enabling the option titled: Scan your tenant's user activity to identify potential insider risks.
- On the Analytics details pane, select Run scan to start the scan for your organization. Analytics scan results may take up to 48 hours before insights are available as reports for review.
After reviewing the analytics insights, choose the insider risk policies and configure the associated prerequisites that best meet your organization's insider risk mitigation strategy.
Get started with recommended actions
The recommended actions experience can help organizations get the most out of Insider risk management capabilities. Organizations find this feature beneficial whether they're setting up Insider risk management for the first time or getting started with creating new policies. Recommended actions include setting up permissions, choosing policy indicators, creating a policy, and more.
The Overview tab on Insider risk management page includes the recommended actions feature, which guides an organization through the steps to configure and deploy policies.
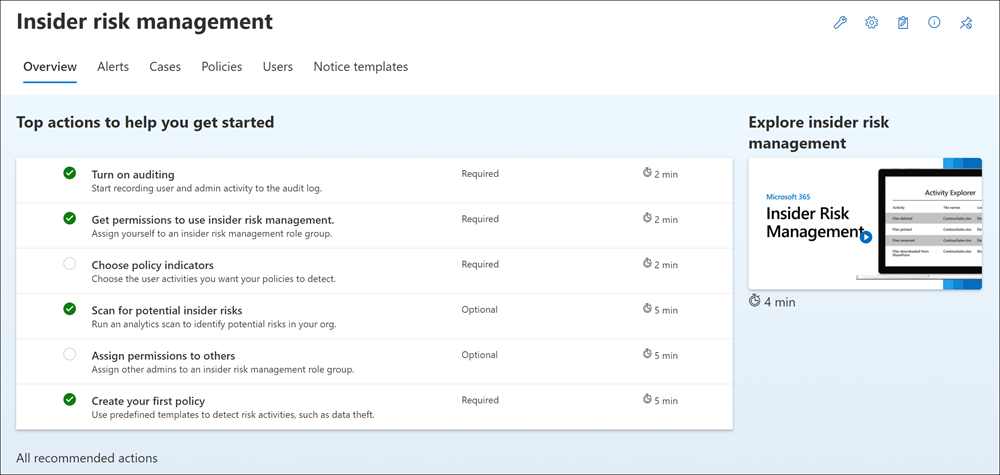
The Overview tab includes a section titled Top actions to help you get started. The options included in this section help an organization get started with or maximize its Insider risk management configuration. These options include:
- Turn on auditing. When turned on, Insider risk management records user and administrator activity in the Microsoft 365 audit log. Insider risk policies and analytics scans use this log to detect risk activities.
- Get permissions to user risk management. The level of access a user has to Insider risk management features depends on which role group an administrator assigned the user to. Only users assigned to either the Insider Risk Management or Insider Risk Management Admins role groups can access Insider risk management features.
- Choose policy indicators. Indicators are essentially the user activities that an organization wants to detect and investigate. An organization can choose indicators to track activity across several Microsoft 365 locations and services.
- Scan for potential insider risks. An organization should run an analytics scan to discover potential insider risks occurring within the company. After evaluating results, review recommended policies to set up.
- Assign permissions to others. If there are other team members responsible for managing insider risk features, administrators must assign them to the appropriate role groups.
- Create your first policy. To receive alerts on potentially risky activities, an organization must set up policies based on predefined templates that define the user activities it wants to detect and investigate.
Each recommended action included in this experience has four attributes:
- Action. The name and description of the recommended action.
- Status. The status of the recommended action. Status values include:
- Not started
- In progress
- Saved for later
- Completed
- Required or optional. For Insider risk management features to function as expected, the system requires certain recommended actions. Other recommended actions are optional for those features to work.
- Estimated time to complete. Estimated time to complete the recommended action in minutes.
Select a recommendation from the list to get started with configuring Insider risk management. Each recommended action guides an organization through the required activities for the recommendation, including:
- Any requirements
- What to expect
- The effect of configuring the feature in the organization
When you configure each recommended action, the system automatically marks it as complete. Or, you must manually select the action as complete when configured.
Workflow
The Insider risk management workflow helps organizations identify, investigate, and take action to address internal risks. Organizations can use actionable insights to quickly identify and act on risky behavior with:
- Focused policy templates
- Comprehensive activity signaling across the Microsoft 365 service
- Alert and case management tools
The following diagram outlines how Insider risk management identifies and resolves internal risk activities and compliance issues.
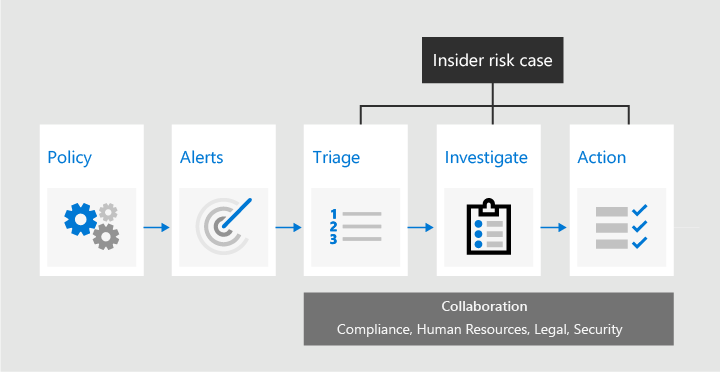
The following sections introduce each of the tasks identified in the workflow diagram.
Policies
You create Insider risk management policies using predefined templates and policy conditions. These policies define what triggering events and risk indicators an organization examines. These conditions include:
- How alerts use risk indicators.
- The users included in the policy.
- The services the organization prioritized.
- The monitoring time period.
Organizations can select from the following policy templates to quickly get started with Insider risk management:
- Data theft by departing users.
- General data leaks.
- Data leaks by priority users.
- Data leaks by disgruntled users.
- General security policy violations.
- General patient data misuse.
- Security policy violations by departing users.
- Security policy violations by priority users.
- Security policy violations by disgruntled users.
A later unit in this training examines Insider risk management policies in greater detail.
Alerts
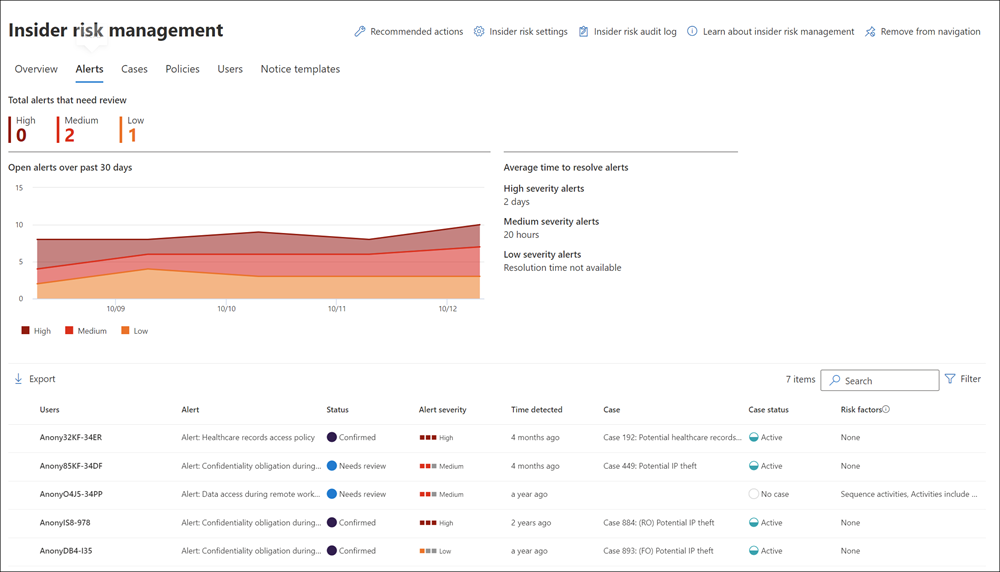
Risk indicators automatically generate alerts that match policy conditions. They're also displayed in the Alerts dashboard. This dashboard enables a quick view of:
- All alerts needing review.
- Open alerts over time.
- Alert statistics for the organization.
The Alerts dashboard displays all policy alerts with the following information. This data helps organizations quickly identify the status of existing alerts and new alerts that require action:
- Status
- Severity
- Time detected
- Case
- Case status
Triage
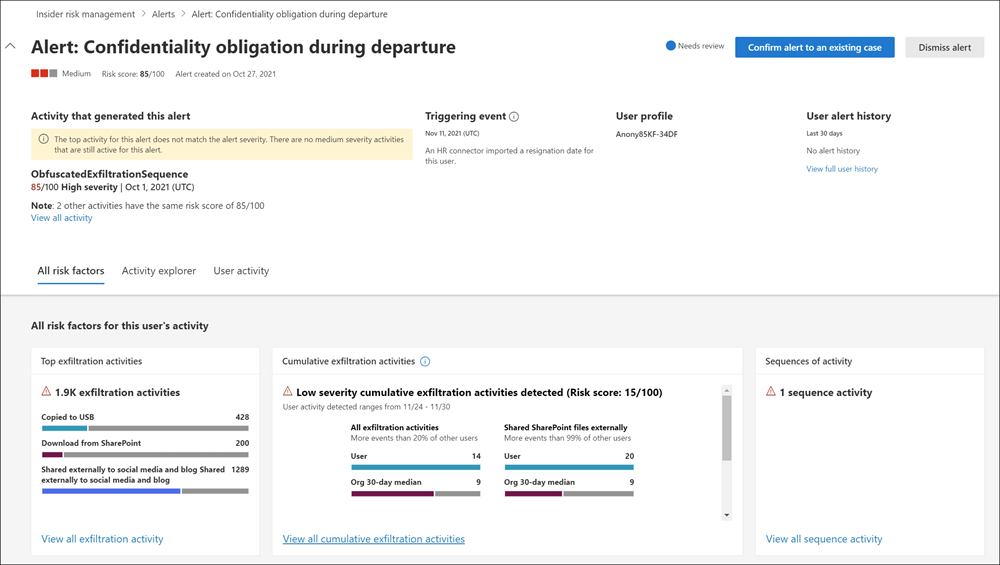
New user activities that need investigation automatically generate alerts. The system assigns these alerts a Needs review status. Reviewers can quickly identify and review, evaluate, and triage these alerts.
Alerts are resolved by opening a new case, assigning the alert to an existing case, or dismissing the alert. Using alert filters, it's easy to quickly identify alerts by status, severity, or time detected. As part of the triage process, reviewers can:
- View alert details for the activities identified by the policy.
- View user activity associated with the policy match.
- See the severity of the alert.
- Review user profile information.
Investigate
Organizations can quickly investigate all activities for a selected user with User activity reports. These reports allow investigators in an organization to examine activities for specific users. You can examine the activities for a defined time period without having to assign them temporarily or explicitly to an Insider risk management policy. After investigators examine activities for a user, they can:
- Dismiss individual activities as benign.
- Share or email a link to the report with other investigators.
- Choose to assign the user temporarily or explicitly to an Insider risk management policy.
Organizations create cases for alerts that require deeper review and investigation of the activity details and circumstances around the policy match. The Case dashboard provides an all-up view of all active cases, open cases over time, and case statistics for your organization. Reviewers can quickly filter cases by status, the date the company opened the case, and the date the company last updated the case.
Important
Selecting a case on the Case dashboard opens the case for investigation and review. This step is the heart of the Insider risk management workflow. This area is where the system synthesizes risk activities, policy conditions, alerts details, and user details into an integrated view for reviewers. A later unit in this training examines cases.
The primary investigation tools in this area include:
- User activity. User activity is automatically displayed in an interactive chart. It plots activities over time and by risk level for current or past risk activities. Reviewers can quickly filter and view the entire risk history for the user. They can also drill into specific activities for more details.
- Content explorer. The Content explorer automatically captures and displays all data files and email messages associated with alert activities. Reviewers can filter and view files and messages by data source, file type, tags, conversation, and many more attributes.
- Case notes. Reviewers can provide notes for a case in the Case Notes section. This list consolidates all notes in a central view and includes reviewer and date submitted information.

Additionally, the Audit log enables organizations to stay informed of the actions taken on Insider risk management features. The Audit log allows for an independent review of users assigned to one or more Insider risk management role groups. The purpose of the review is to analyze the users' actions.
Action
After an organization investigates a case, reviewers can quickly act to resolve the case or collaborate with other risk stakeholders in the organization. If users accidentally or inadvertently violate policy conditions, the system sends a simple reminder notice o the user from notice templates that an organization can customize. These notices can serve as simple reminders. They can also direct the user to refresher training or guidance to help prevent future risky behavior. For more information, see Insider risk management notice templates.
In the more serious situations, a reviewer may need to share the Insider risk management case information with other reviewers or services in their organization. Microsoft 365 tightly integrates Insider risk management with the following Microsoft Purview solutions to help reviewers with end-to-end risk resolution.
- eDiscovery (Premium). Escalating a case for investigation allows an organization to transfer data and management of the case to Microsoft Purview eDiscovery (Premium). eDiscovery (Premium) provides an end-to-end workflow to preserve, collect, review, analyze, and export content that's responsive to an organization's internal and external investigations. It allows legal teams to manage the entire legal hold notification workflow. To learn more about eDiscovery (Premium) cases, see Overview of Microsoft Purview eDiscovery (Premium).
- Office 365 Management APIs integration. Insider risk management supports exporting alert information to security information and event management (SIEM) services through the Office 365 Management APIs. Having access to alert information in the platform that best fits an organization's risk processes gives it more flexibility in how to act on risk activities. To learn more about exporting alert information with Office 365 Management APIs, see Export alerts.
Knowledge check
Choose the best response for the following question. Then select “Check your answers.”