Explore cloud authentication using password hash synchronization
Given the following considerations, password hash synchronization should be used for whichever authentication method an organization chooses:
- High availability and disaster recovery. Pass-Through Authentication (PTA) and Federation with ADFS rely on an on-premises infrastructure. For PTA, the on-premises footprint includes the server hardware and networking the PTA agents require. For Federation with ADFS, the on-premises footprint is even larger. It requires servers in your perimeter network to proxy authentication requests and the internal federation servers. To avoid single points of failures, you should deploy redundant servers. By doing so, authentication requests will always be serviced if any component fails. Both PTA and Federation also rely on domain controllers to respond to authentication requests, which can also fail. Many of these components need maintenance to stay healthy. Outages are more likely when maintenance isn't planned and implemented correctly. Avoid outages by using password hash synchronization because the Microsoft Entra cloud authentication service scales globally and is always available.
- On-premises outage survival. The consequences of an on-premises outage that's caused by a cyber-attack or disaster can be significant. Issues can range from reputational brand damage to a paralyzed organization unable to deal with the attack. Many organizations have recently been victims of malware attacks, including targeted ransomware, that caused their on-premises servers to go down. When Microsoft helps customers deal with these kinds of attacks, it sees two categories of organizations:
- Organizations that previously turned on password hash synchronization changed their authentication method to use password hash synchronization. They were back online in a matter of hours. By using access to email through Microsoft 365, they worked to resolve issues and access other cloud-based workloads.
- Organizations that didn’t previously enable password hash synchronization had to resort to untrusted external consumer email systems for communications and issue resolution. In those cases, it took them weeks or more to be up and running again.
- Identity protection. One of the best ways to protect users in the cloud is Microsoft Entra ID Protection. Microsoft continually scans the Internet for user and password lists that bad actors sell and make available on the dark web. Microsoft Entra ID can use this information to verify whether any of the usernames and passwords in your organization are compromised. So it's critical to enable password hash synchronization no matter what authentication method you use, whether that's Federated with ADFS or PTA. Leaked credentials are presented as a report. Use this information to block or force users to change their passwords when they try to sign in with leaked passwords.
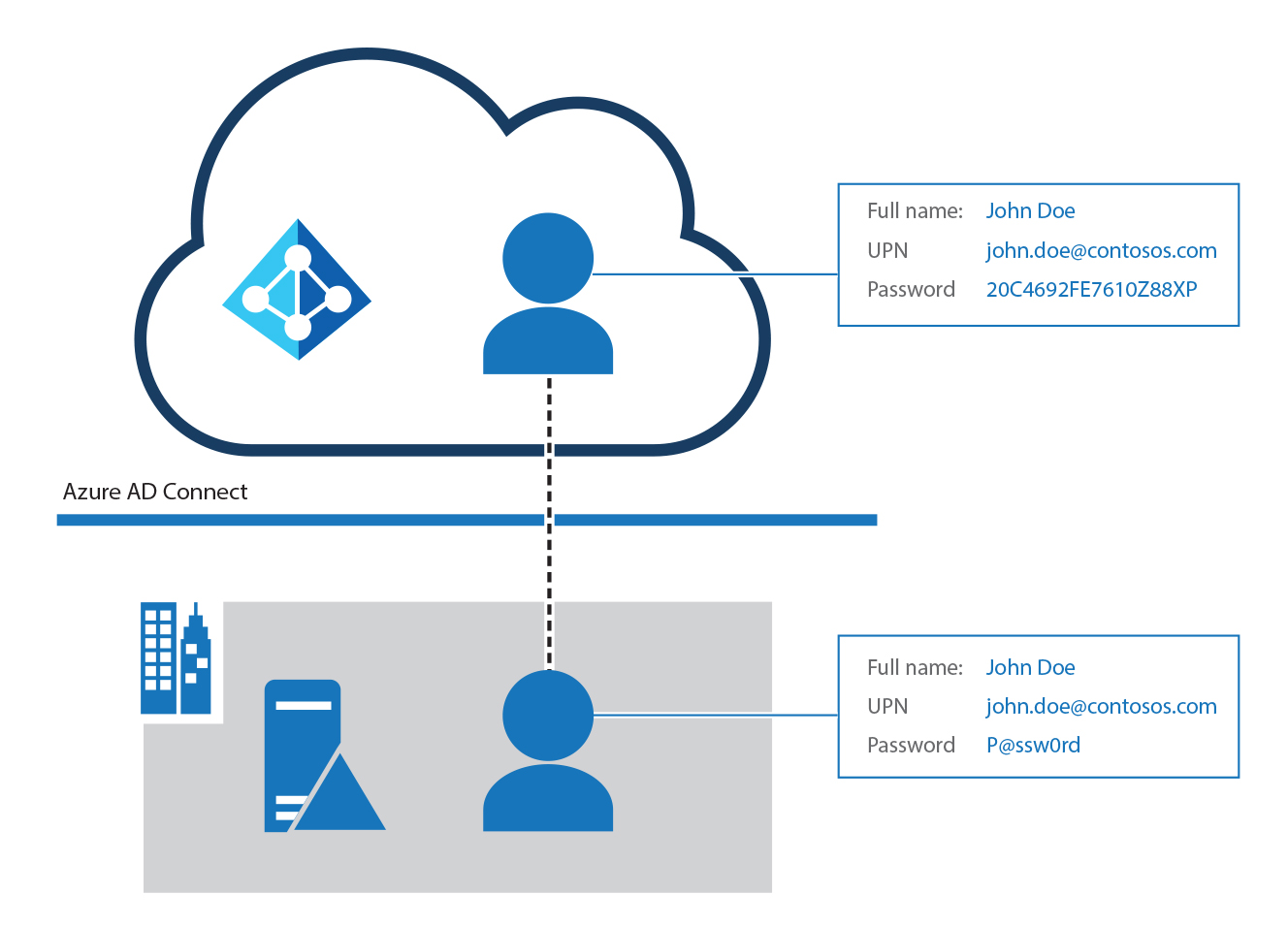
The following diagram reinforces the concept that when implementing password hash synchronization, only password hashes are synced; the actual passwords are NOT synced. The rest of the attributes, such as the user's full name and UPN, are kept in sync.