Set up self-service group management in Microsoft Entra ID
Microsoft Entra ID provides self-service group management features that enable users to create and manage their own security groups or Microsoft 365 groups. The owner of the group can approve or deny membership requests and delegate control of group membership. Self-service group management features aren't available for mail-enabled security groups or distribution lists.
Self-service group membership
You can allow users to create security groups to manage access to shared resources. Users can create security groups from the Microsoft Entra admin center, using PowerShell, or from the My Groups portal.
Only the group's owners can update membership. You can give group owners the ability to approve or deny membership requests from the My Groups portal. Security groups created by self-service through the My Groups portal are available to join for all users, whether owner-approved or autoapproved. In the My Groups portal, you can change membership options when you create the group.
Microsoft 365 groups provide collaboration opportunities for your users. You can create groups in any of the Microsoft 365 applications, such as SharePoint, and Microsoft Teams. You can also create Microsoft 365 groups in Azure portals by using Microsoft Graph PowerShell or from the My Groups portal. For more information on the difference between security groups and Microsoft 365 groups, see Learn about groups.
| Groups created in | Security group default behavior | Microsoft 365 group default behavior |
|---|---|---|
| Microsoft Graph PowerShell | Only owners can add members. Visible but not available to join in MyApp Groups Access Panel. |
Open to join for all users. |
| Azure portal | Only owners can add members. Visible but not available to join in My Groups portal. Owner isn't assigned automatically at group creation. |
Open to join for all users. |
| My Groups portal | Users can manage groups and request access to join groups here. Membership options can be changed when a group is created. |
Open to join for all users. Membership options can be changed when a group is created. |
Self-service group management scenarios
Two scenarios help to explain self-service group management.
Delegated group management
In this example scenario, an administrator manages access to a Software as a Service (SaaS) application that the company is using. Managing the access rights is cumbersome, so the administrator asks the business owner to create a new group. The administrator assigns access for the application to the new group and adds to the group all people already accessing the application. The business owner then can add more users, and those users are automatically provisioned to the application.
The business owner doesn't need to wait for the administrator to manage access for users. If the administrator grants the same permission to a manager in a different business group, that person can also manage access for their own group members. The business owner and the manager can't view or manage each other's group memberships. The administrator can still see all users who have access to the application and block access rights, if needed.
Note
For delegated scenarios, the administrator needs to have at least a Privileged Role Administrator Microsoft Entra role.
Self-service group management
In this example scenario, two users have SharePoint Online sites that they set up independently. They want to give each other's teams access to their sites. To accomplish this task, they can create one group in Microsoft Entra ID. In SharePoint Online, each of them selects that group to provide access to their sites.
When someone wants access, they request it from the My Groups portal. After approval, they get access to both SharePoint Online sites automatically. Later, one of them decides that all people accessing the site should also get access to a particular SaaS application. The administrator of the SaaS application can add access rights for the application to the SharePoint Online site. From then on, any requests that get approved give access to the two SharePoint Online sites and also to the SaaS application.
Make a group available for user self-service
Sign in to the Microsoft Entra admin center as at least a Global Administrator.
Select Microsoft Entra ID.
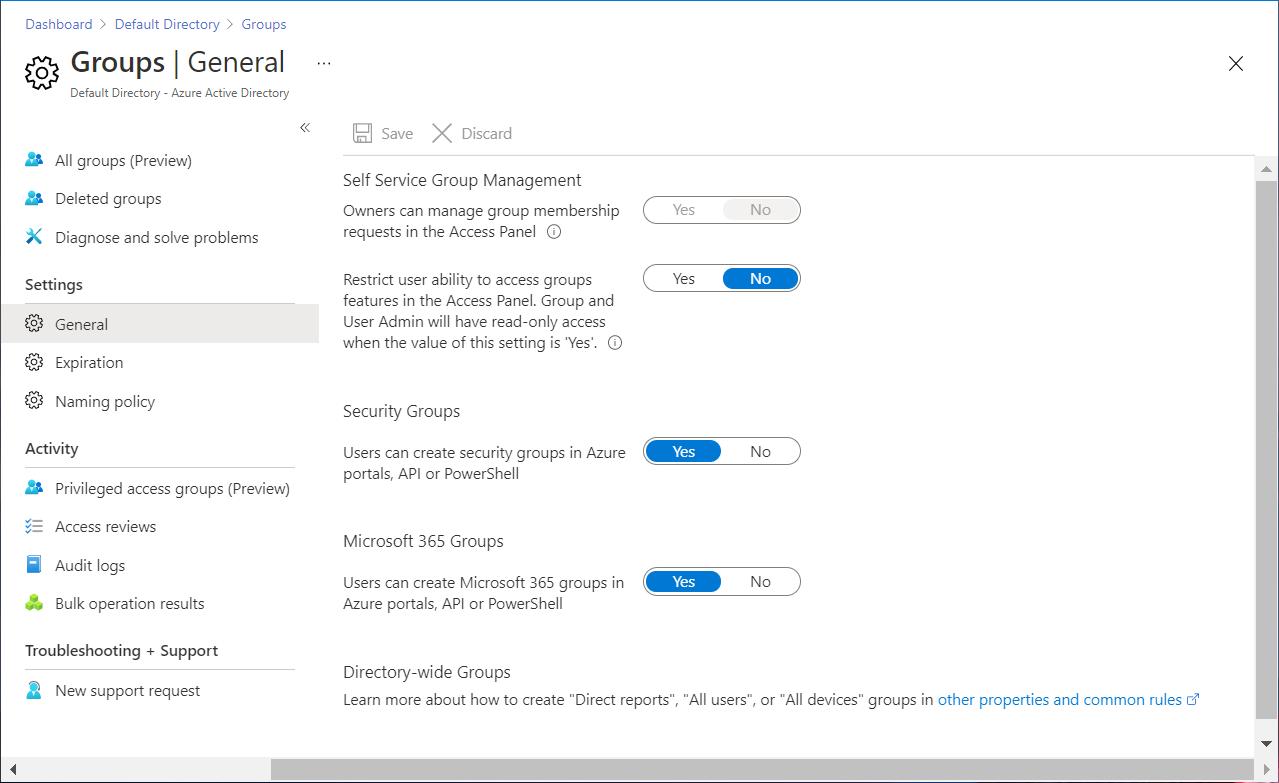
Select All groups > Groups, and then select General settings.
Note
This setting only restricts access of group information in My Groups. It doesn't restrict access to group information via other methods like Microsoft Graph API calls or the Microsoft Entra admin center.
Note
Changes regarding the Self Service Group Management setting, are currently under review and won't take place as originally planned. A deprecation date will be announced in the future.
Set Owners can manage group membership requests in the Access Panel to Yes.
Set Restrict user ability to access groups features in the Access Panel to No.
Set Users can create security groups in Azure portals, API or PowerShell to Yes or No.
For more information about this setting, see Group settings.
Set Users can create Microsoft 365 groups in Azure portals, API or PowerShell to Yes or No.
For more information about this setting, see Group settings.
You can also use Owners who can assign members as group owners in the Azure portal to achieve more granular access control over self-service group management for your users.
When users can create groups, all users in your organization are allowed to create new groups. As the default owner, they can then add members to these groups. You can't specify individuals who can create their own groups. You can specify individuals only for making another group member a group owner.
Note
A Microsoft Entra ID P1 or P2 license is required for users to request to join a security group or Microsoft 365 group and for owners to approve or deny membership requests. Without a Microsoft Entra ID P1 or P2 license, users can still manage their groups in the MyApp Groups Access Panel. But they can't create a group that requires owner approval, and they can't request to join a group.
Group settings
The group settings enable you to control who can create security and Microsoft 365 groups.
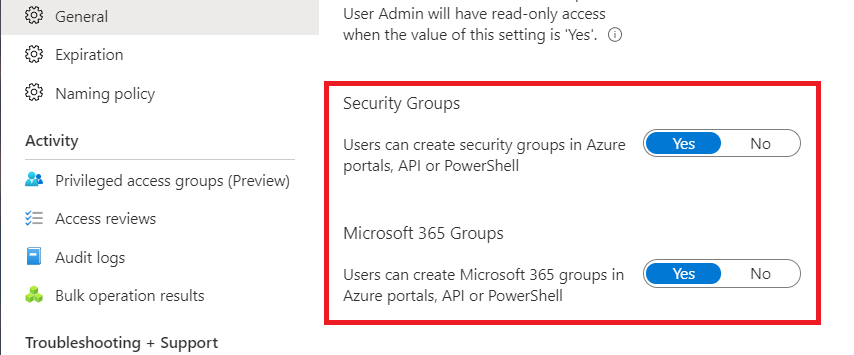
The following table helps you decide which values to choose.
| Setting | Value | Effect on your tenant |
|---|---|---|
| Users can create security groups in the Azure portal, API, or PowerShell. | Yes | All users in your Microsoft Entra organization are allowed to create new security groups and add members to these groups in the Azure portal, API, or PowerShell. These new groups also show up in the Access Panel for all other users. If the policy setting on the group allows it, other users can create requests to join these groups. |
| No | Users can’t create security groups. They can still manage the membership of groups for which they’re an owner and approve requests from other users to join their groups. | |
| Users can create Microsoft 365 groups in the Azure portal, API, or PowerShell. | Yes | All users in your Microsoft Entra organization are allowed to create new Microsoft 365 groups and add members to these groups in the Azure portal, API, or PowerShell. These new groups also show up in the Access Panel for all other users. If the policy setting on the group allows it, other users can create requests to join these groups. |
| No | Users can’t create Microsoft 365 Groups. They can still manage the membership of groups for which they’re an owner and approve requests from other users to join their groups. |
Here are some more details about these group settings:
- These settings can take up to 15 minutes to take effect.
- If you want to enable some, but not all, of your users to create groups, you can assign those users a role that can create groups, such as Groups Administrator.
- These settings are for users and don't affect service principals. For example, if you had a service principal with permissions to create groups, even if you set these settings to No, the service principal can still create groups.
Configure group settings by using Microsoft Graph
To configure the Users can create Microsoft 365 groups in Azure portals, API or PowerShell setting by using Microsoft Graph, configure the EnableGroupCreation object in the groupSettings object. For more information, see Overview of group settings.
To configure the Users can create security groups in Azure portals, API or PowerShell setting by using Microsoft Graph, update the allowedToCreateSecurityGroups property of defaultUserRolePermissions in the authorizationPolicy object.
Next steps
For more information on Microsoft Entra ID, see: