Quickstart: Create a private endpoint by using the Azure CLI
Get started with Azure Private Link by creating and using a private endpoint to connect securely to an Azure web app.
In this quickstart, create a private endpoint for an Azure App Services web app and then create and deploy a virtual machine (VM) to test the private connection.
You can create private endpoints for various Azure services, such as Azure SQL and Azure Storage.
Prerequisites
An Azure account with an active subscription. If you don't already have an Azure account, create an account for free.
An Azure web app with a PremiumV2-tier or higher app service plan, deployed in your Azure subscription.
For more information and an example, see Quickstart: Create an ASP.NET Core web app in Azure.
The example webapp in this article is named webapp-1. Replace the example with your webapp name.
Use the Bash environment in Azure Cloud Shell. For more information, see Quickstart for Bash in Azure Cloud Shell.
If you prefer to run CLI reference commands locally, install the Azure CLI. If you're running on Windows or macOS, consider running Azure CLI in a Docker container. For more information, see How to run the Azure CLI in a Docker container.
If you're using a local installation, sign in to the Azure CLI by using the az login command. To finish the authentication process, follow the steps displayed in your terminal. For other sign-in options, see Sign in with the Azure CLI.
When you're prompted, install the Azure CLI extension on first use. For more information about extensions, see Use extensions with the Azure CLI.
Run az version to find the version and dependent libraries that are installed. To upgrade to the latest version, run az upgrade.
Create a resource group
An Azure resource group is a logical container where Azure resources are deployed and managed.
First, create a resource group by using az group create:
az group create \
--name test-rg \
--location eastus2
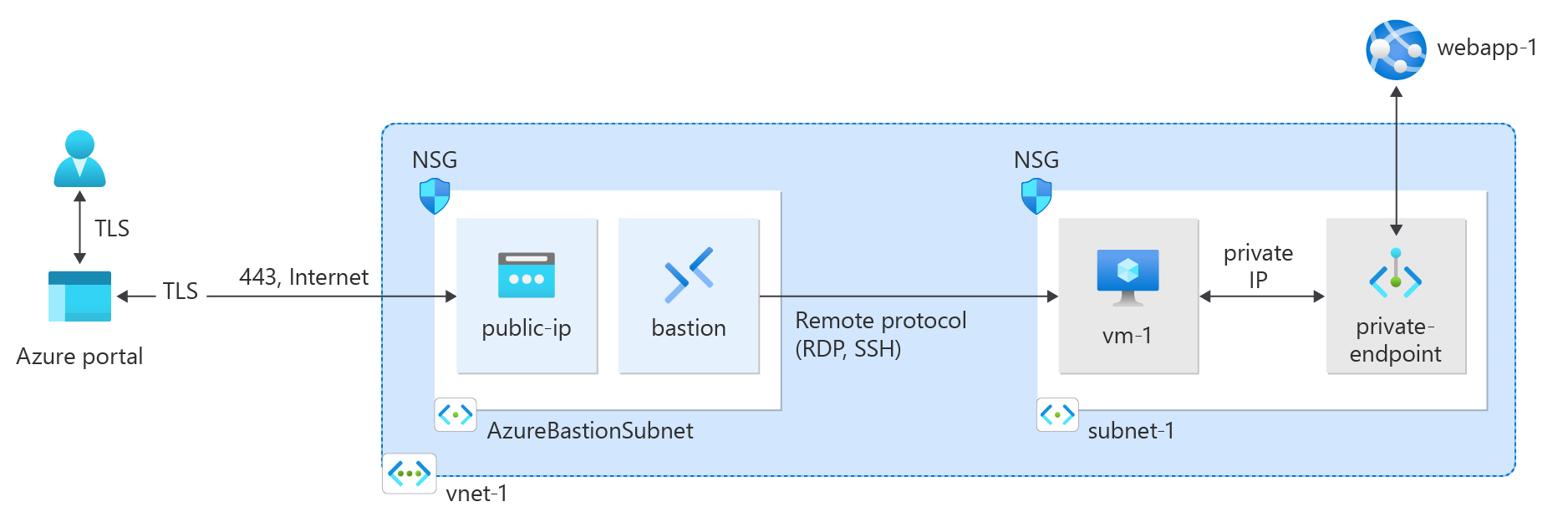
Create a virtual network and bastion host
A virtual network and subnet is required for to host the private IP address for the private endpoint. You create a bastion host to connect securely to the virtual machine to test the private endpoint. You create the virtual machine in a later section.
Note
Hourly pricing starts from the moment that Bastion is deployed, regardless of outbound data usage. For more information, see Pricing and SKUs. If you're deploying Bastion as part of a tutorial or test, we recommend that you delete this resource after you finish using it.
Create a virtual network with az network vnet create.
az network vnet create \
--resource-group test-rg \
--location eastus2 \
--name vnet-1 \
--address-prefixes 10.0.0.0/16 \
--subnet-name subnet-1 \
--subnet-prefixes 10.0.0.0/24
Create a bastion subnet with az network vnet subnet create.
az network vnet subnet create \
--resource-group test-rg \
--name AzureBastionSubnet \
--vnet-name vnet-1 \
--address-prefixes 10.0.1.0/26
Create a public IP address for the bastion host with az network public-ip create.
az network public-ip create \
--resource-group test-rg \
--name public-ip \
--sku Standard \
--zone 1 2 3
Create the bastion host with az network bastion create.
az network bastion create \
--resource-group test-rg \
--name bastion \
--public-ip-address public-ip \
--vnet-name vnet-1 \
--location eastus2
It can take a few minutes for the Azure Bastion host to deploy.
Create a private endpoint
An Azure service that supports private endpoints is required to set up the private endpoint and connection to the virtual network. For the examples in this article, use the Azure WebApp from the prerequisites. For more information on the Azure services that support a private endpoint, see Azure Private Link availability.
A private endpoint can have a static or dynamically assigned IP address.
Important
You must have a previously deployed Azure App Services WebApp to proceed with the steps in this article. For more information, see Prerequisites .
Place the resource ID of the web app that you created earlier into a shell variable with az webapp list. Create the private endpoint with az network private-endpoint create.
id=$(az webapp list \
--resource-group test-rg \
--query '[].[id]' \
--output tsv)
az network private-endpoint create \
--connection-name connection-1 \
--name private-endpoint \
--private-connection-resource-id $id \
--resource-group test-rg \
--subnet subnet-1 \
--group-id sites \
--vnet-name vnet-1
Configure the private DNS zone
A private DNS zone is used to resolve the DNS name of the private endpoint in the virtual network. For this example, we're using the DNS information for an Azure WebApp, for more information on the DNS configuration of private endpoints, see Azure Private Endpoint DNS configuration].
Create a new private Azure DNS zone with az network private-dns zone create.
az network private-dns zone create \
--resource-group test-rg \
--name "privatelink.azurewebsites.net"
Link the DNS zone to the virtual network you created previously with az network private-dns link vnet create.
az network private-dns link vnet create \
--resource-group test-rg \
--zone-name "privatelink.azurewebsites.net" \
--name dns-link \
--virtual-network vnet-1 \
--registration-enabled false
Create a DNS zone group with az network private-endpoint dns-zone-group create.
az network private-endpoint dns-zone-group create \
--resource-group test-rg \
--endpoint-name private-endpoint \
--name zone-group \
--private-dns-zone "privatelink.azurewebsites.net" \
--zone-name webapp
Create a test virtual machine
To verify the static IP address and the functionality of the private endpoint, a test virtual machine connected to your virtual network is required.
Create the virtual machine with az vm create.
az vm create \
--resource-group test-rg \
--name vm-1 \
--image Win2022Datacenter \
--public-ip-address "" \
--vnet-name vnet-1 \
--subnet subnet-1 \
--admin-username azureuser
Note
Virtual machines in a virtual network with a bastion host don't need public IP addresses. Bastion provides the public IP, and the VMs use private IPs to communicate within the network. You can remove the public IPs from any VMs in bastion hosted virtual networks. For more information, see Dissociate a public IP address from an Azure VM.
Note
Azure provides a default outbound access IP for VMs that either aren't assigned a public IP address or are in the backend pool of an internal basic Azure load balancer. The default outbound access IP mechanism provides an outbound IP address that isn't configurable.
The default outbound access IP is disabled when one of the following events happens:
- A public IP address is assigned to the VM.
- The VM is placed in the backend pool of a standard load balancer, with or without outbound rules.
- An Azure NAT Gateway resource is assigned to the subnet of the VM.
VMs that you create by using virtual machine scale sets in flexible orchestration mode don't have default outbound access.
For more information about outbound connections in Azure, see Default outbound access in Azure and Use Source Network Address Translation (SNAT) for outbound connections.
Test connectivity to the private endpoint
Use the virtual machine that you created earlier to connect to the web app across the private endpoint.
In the search box at the top of the portal, enter Virtual machine. Select Virtual machines.
Select vm-1.
On the overview page for vm-1, select Connect, and then select the Bastion tab.
Select Use Bastion.
Enter the username and password that you used when you created the VM.
Select Connect.
After you've connected, open PowerShell on the server.
Enter
nslookup webapp-1.azurewebsites.net. You receive a message that's similar to the following example:Server: UnKnown Address: 168.63.129.16 Non-authoritative answer: Name: webapp-1.privatelink.azurewebsites.net Address: 10.0.0.10 Aliases: webapp-1.azurewebsites.netA private IP address of 10.0.0.10 is returned for the web app name if you chose static IP address in the previous steps. This address is in the subnet of the virtual network you created earlier.
In the bastion connection to vm-1, open the web browser.
Enter the URL of your web app,
https://webapp-1.azurewebsites.net.If your web app hasn't been deployed, you get the following default web app page:
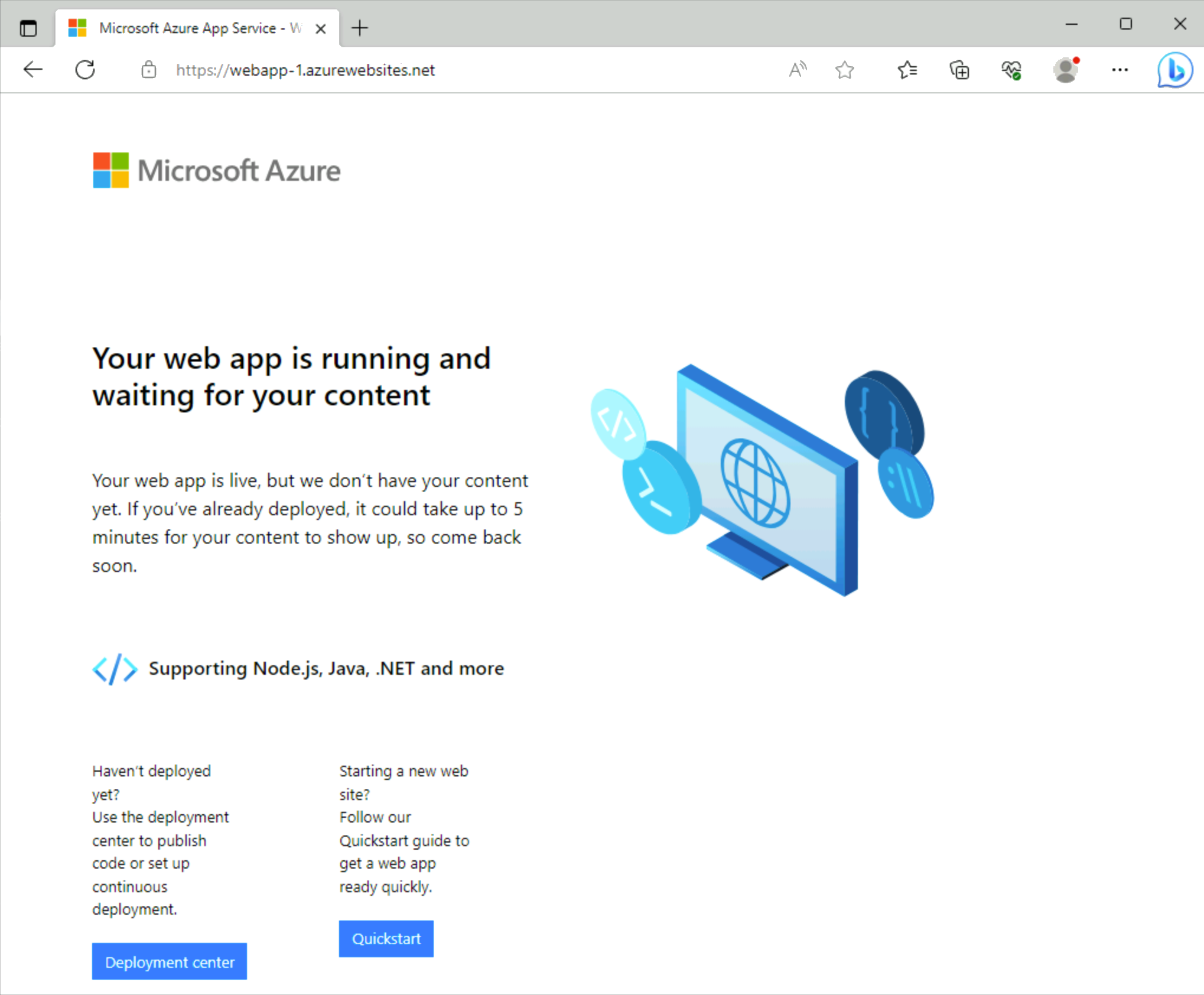
Close the connection to vm-1.
Clean up resources
When no longer needed, use the az group delete command to remove the resource group, private link service, load balancer, and all related resources.
az group delete \
--name test-rg
Next steps
For more information about the services that support private endpoints, see: