Require secure transfer to ensure secure connections
You can configure your storage account to accept requests from secure connections only by setting the Secure transfer required property for the storage account. When you require secure transfer, any requests originating from an insecure connection are rejected. Microsoft recommends that you always require secure transfer for all of your storage accounts, unless you're using NFS Azure file shares. The Secure transfer required property must be disabled in order for NFS Azure file shares to work.
When secure transfer is required, a call to an Azure Storage REST API operation must be made over HTTPS. Any request made over HTTP is rejected. By default, the Secure transfer required property is enabled when you create a storage account.
Azure Policy provides a built-in policy to ensure that secure transfer is required for your storage accounts. For more information, see the Storage section in Azure Policy built-in policy definitions.
Connecting to an Azure file share over SMB without encryption fails when secure transfer is required for the storage account. Examples of insecure connections include those made over SMB 2.1 or SMB 3.x without encryption.
Note
Because Azure Storage doesn't support HTTPS for custom domain names, this option isn't applied when you're using a custom domain name.
This secure transfer setting doesn't apply to TCP. Connections via NFS 3.0 protocol support in Azure Blob Storage using TCP, which isn't secured, will succeed.
Require secure transfer in the Azure portal
You can turn on the Secure transfer required property when you create a storage account in the Azure portal. You can also enable it for existing storage accounts.
Require secure transfer for a new storage account
Open the Create storage account pane in the Azure portal.
In the Advanced page, select the Enable secure transfer checkbox.
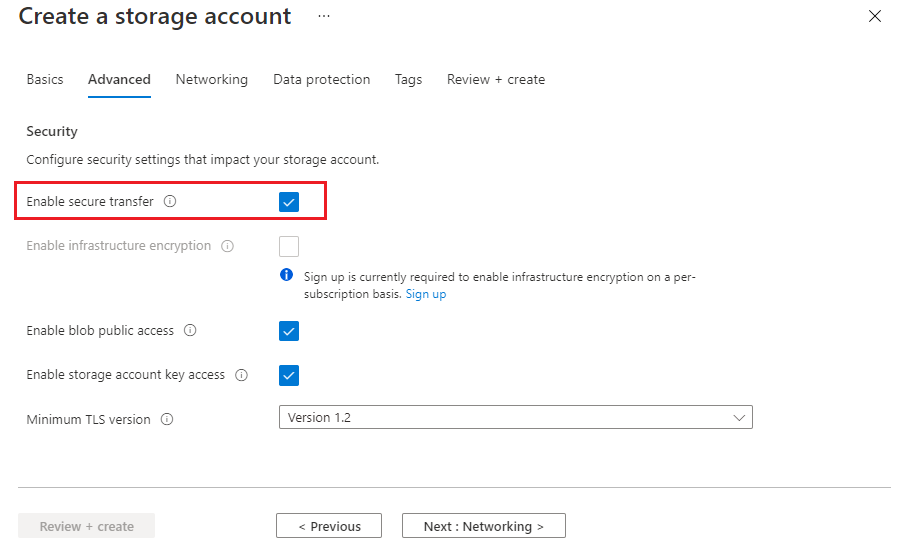
Require secure transfer for an existing storage account
Select an existing storage account in the Azure portal.
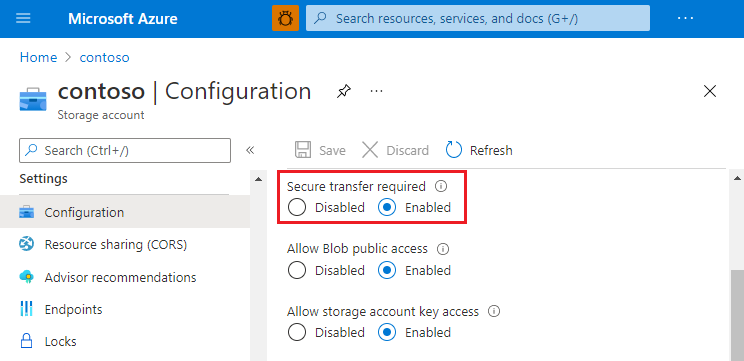
In the storage account menu pane, under Settings, select Configuration.
Under Secure transfer required, select Enabled.
Require secure transfer from code
To require secure transfer programmatically, set the enableHttpsTrafficOnly property to True on the storage account. You can set this property by using the Storage Resource Provider REST API, client libraries, or tools:
Require secure transfer with PowerShell
Note
We recommend that you use the Azure Az PowerShell module to interact with Azure. To get started, see Install Azure PowerShell. To learn how to migrate to the Az PowerShell module, see Migrate Azure PowerShell from AzureRM to Az.
This sample requires the Azure PowerShell module Az version 0.7 or later. Run Get-Module -ListAvailable Az to find the version. If you need to install or upgrade, see Install Azure PowerShell module.
Run Connect-AzAccount to create a connection with Azure.
Use the following command line to check the setting:
Get-AzStorageAccount -Name "{StorageAccountName}" -ResourceGroupName "{ResourceGroupName}"
StorageAccountName : {StorageAccountName}
Kind : Storage
EnableHttpsTrafficOnly : False
...
Use the following command line to enable the setting:
Set-AzStorageAccount -Name "{StorageAccountName}" -ResourceGroupName "{ResourceGroupName}" -EnableHttpsTrafficOnly $True
StorageAccountName : {StorageAccountName}
Kind : Storage
EnableHttpsTrafficOnly : True
...
Require secure transfer with Azure CLI
To run this sample, install the latest version of the Azure CLI. To start, run az login to create a connection with Azure.
Samples for the Azure CLI are written for the bash shell. To run this sample in Windows PowerShell or Command Prompt, you may need to change
elements of the script.
If you don't have an Azure subscription, create an Azure free account before you begin.
Use the following command to check the setting:
az storage account show -g {ResourceGroupName} -n {StorageAccountName}
{
"name": "{StorageAccountName}",
"enableHttpsTrafficOnly": false,
"type": "Microsoft.Storage/storageAccounts"
...
}
Use the following command to enable the setting:
az storage account update -g {ResourceGroupName} -n {StorageAccountName} --https-only true
{
"name": "{StorageAccountName}",
"enableHttpsTrafficOnly": true,
"type": "Microsoft.Storage/storageAccounts"
...
}