Using Microsoft Sentinel with Azure Web Application Firewall
Azure Web Application Firewall (WAF) combined with Microsoft Sentinel can provide security information event management for WAF resources. Microsoft Sentinel provides security analytics using Log Analytics, which allows you to easily break down and view your WAF data. Using Microsoft Sentinel, you can access pre-built workbooks and modify them to best fit your organization's needs. The workbook can show analytics for WAF on Azure Content Delivery Network (CDN), WAF on Azure Front Door, and WAF on Application Gateway across several subscriptions and workspaces.
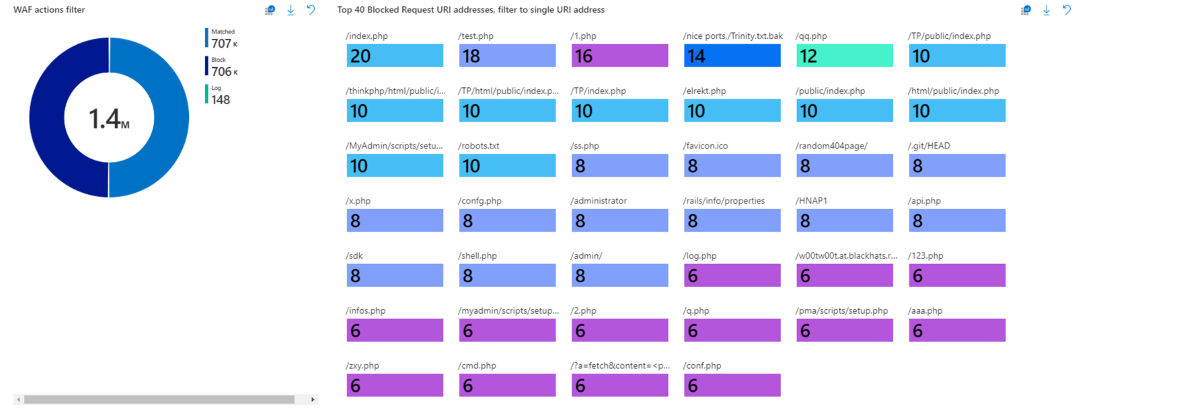
WAF log analytics categories
WAF log analytics are broken down into the following categories:
- All WAF actions taken
- Top 40 blocked request URI addresses
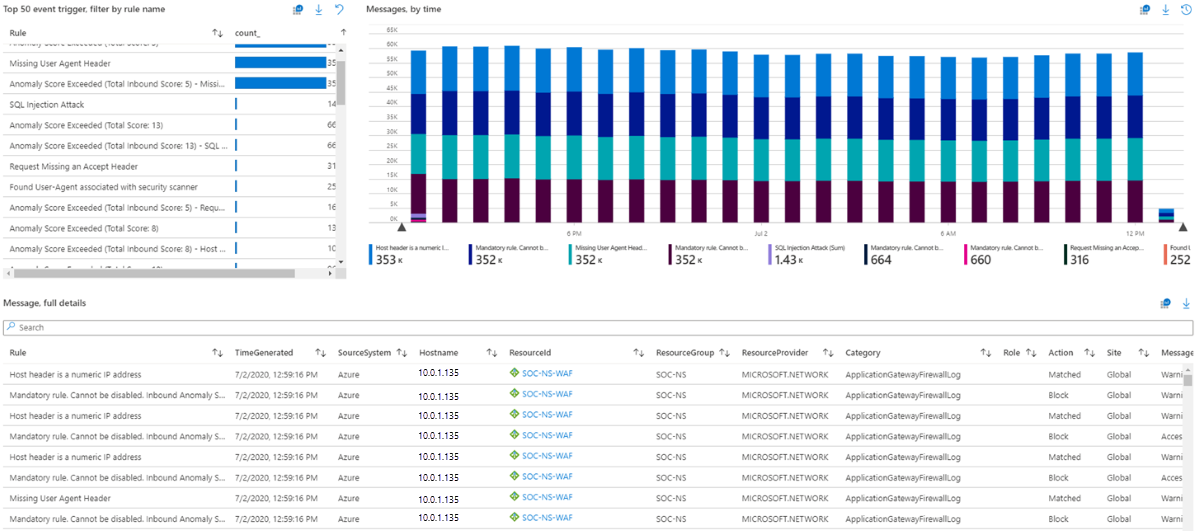
- Top 50 event triggers,
- Messages over time
- Full message details
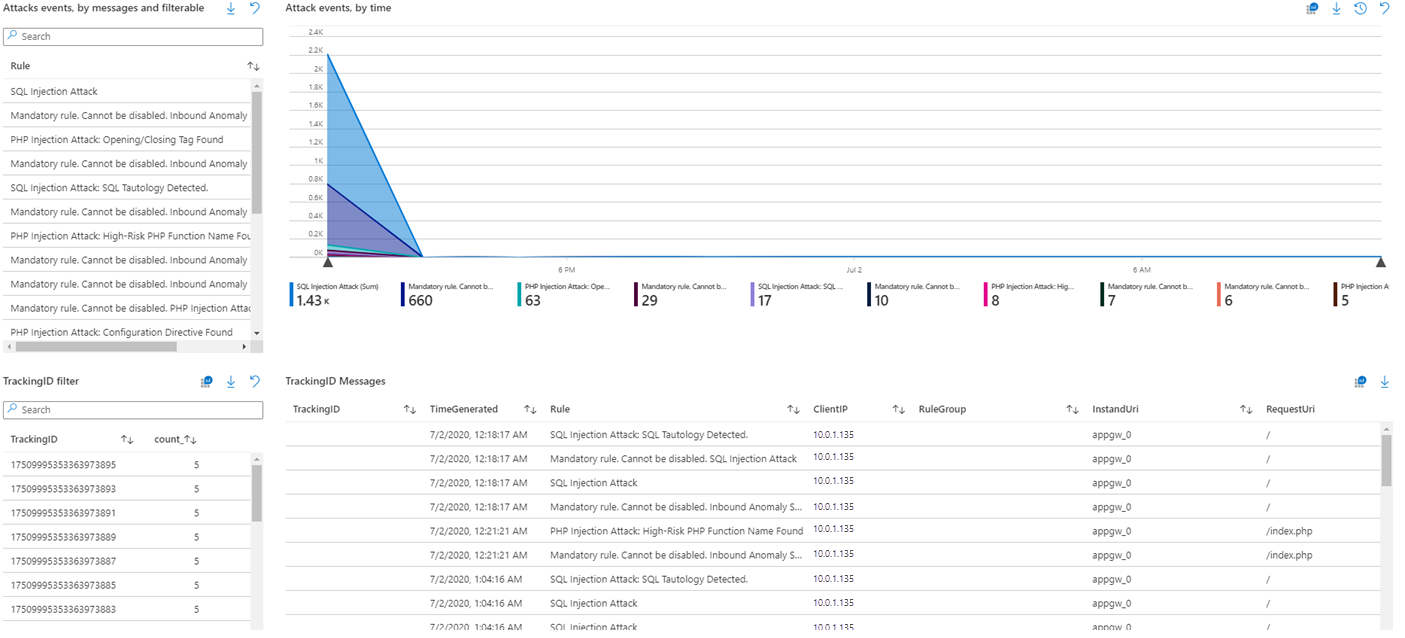
- Attack events by messages
- Attack events over time
- Tracking ID filter
- Tracking ID messages
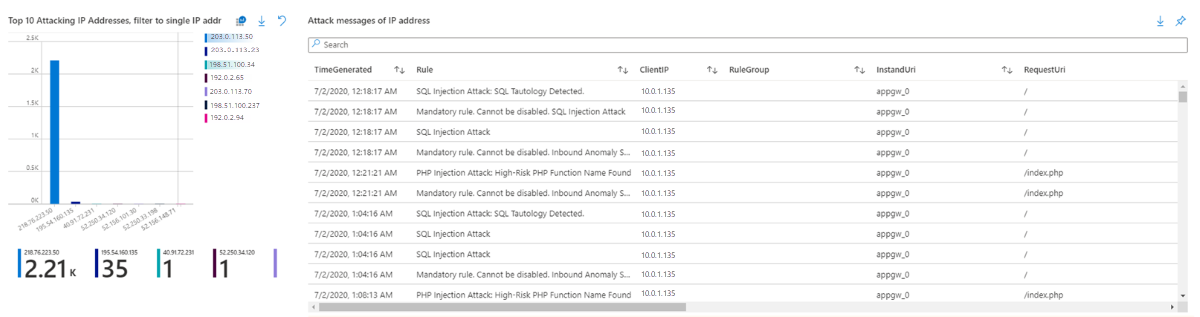
- Top 10 attacking IP addresses
- Attack messages of IP addresses
WAF workbook examples
The following WAF workbook examples show sample data:
Launch a WAF workbook
The WAF workbook works for all Azure Front Door, Application Gateway, and CDN WAFs. Before connecting the data from these resources, log analytics must be enabled on your resource.
To enable log analytics for each resource, go to your individual Azure Front Door, Application Gateway, or CDN resource:
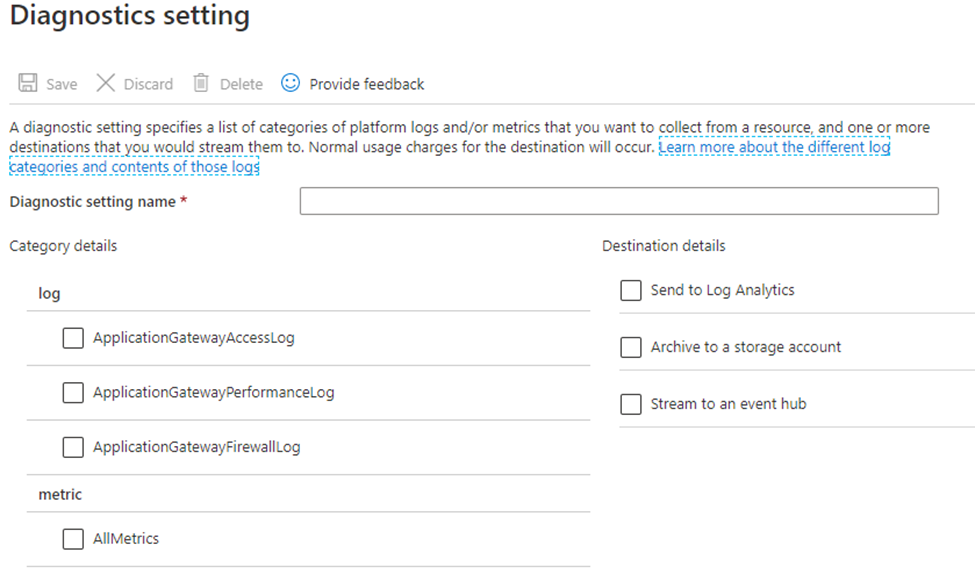
Select Diagnostic settings.
Select + Add diagnostic setting.
In the Diagnostic setting page:
- Type a name.
- Select Send to Log Analytics.
- Choose the log destination workspace.
- Select the log types that you want to analyze:
- Application Gateway: ‘ApplicationGatewayAccessLog’ and ‘ApplicationGatewayFirewallLog’
- Azure Front Door Standard/Premium: ‘FrontDoorAccessLog’ and ‘FrontDoorFirewallLog’
- Azure Front Door classic: ‘FrontdoorAccessLog’ and ‘FrontdoorFirewallLog’
- CDN: ‘AzureCdnAccessLog’
- Select Save.
On the Azure home page, type Microsoft Sentinel in the search bar and select the Microsoft Sentinel resource.
Select an already active workspace or create a new workspace.
In Microsoft Sentinel, under Content management, select Content hub.
Find and select the Azure Web Application Firewall solution.
On the toolbar at the top of the page, select Install/Update.
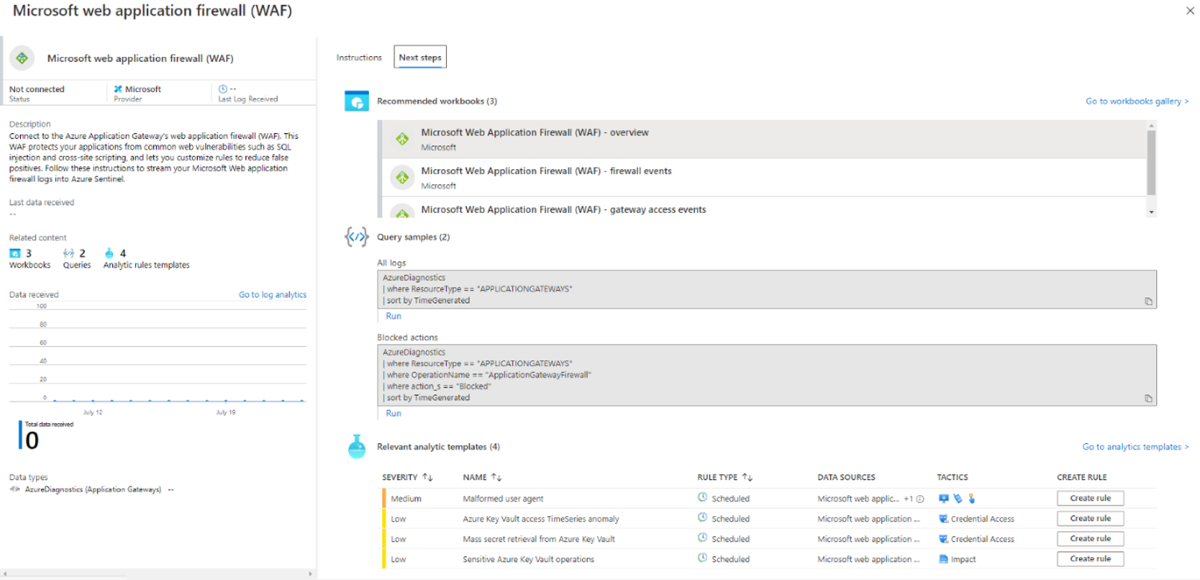
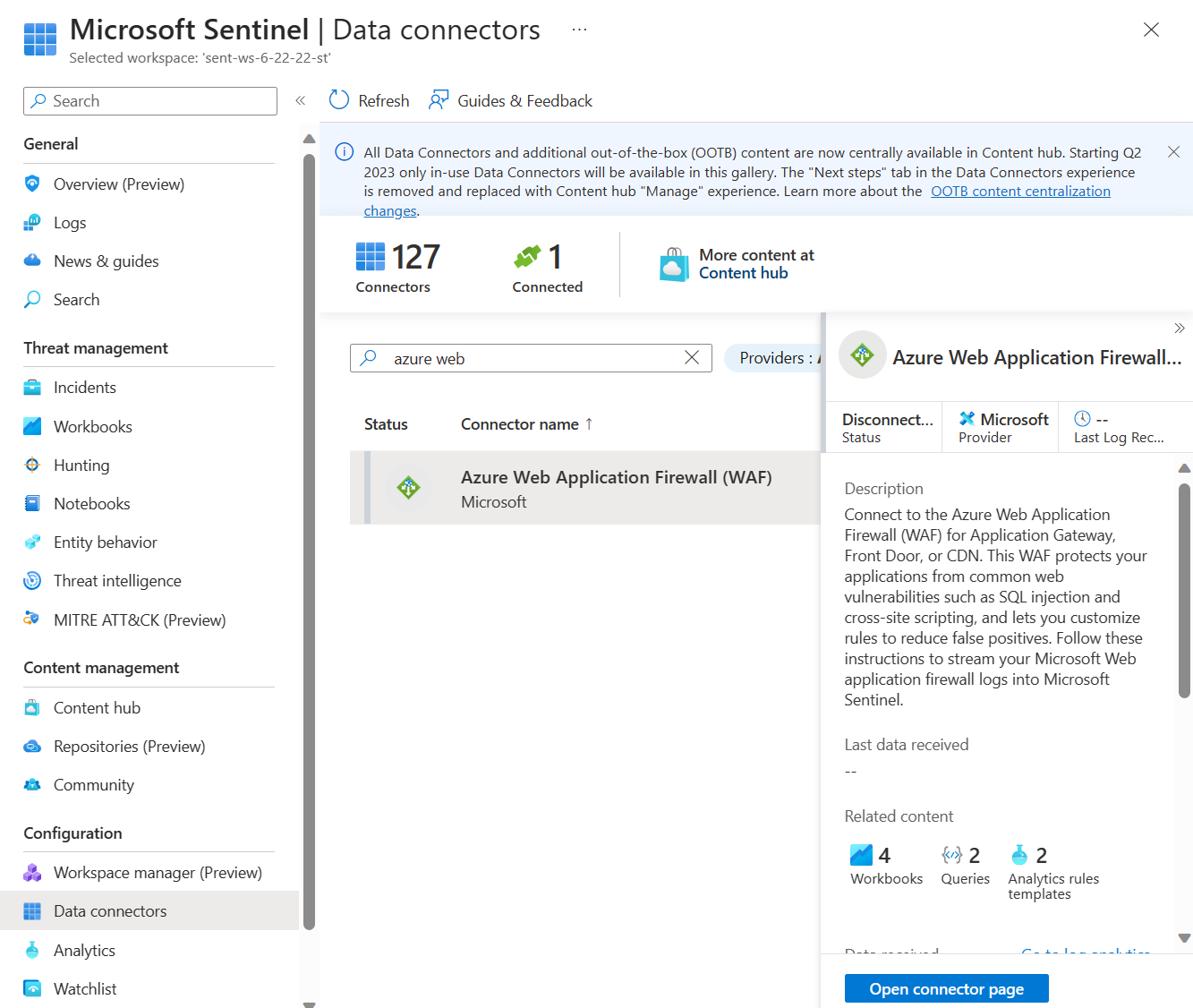
In Microsoft Sentinel, on the left-hand side under Configuration, select Data Connectors.
Search for and select Azure Web Application Firewall (WAF). Select Open connector page on the bottom right.
Follow the instructions under Configuration for each WAF resource that you want to have log analytic data for if you haven't done so previously.
Once finished configuring individual WAF resources, select the Next steps tab. Select one of the recommended workbooks. This workbook will use all log analytic data that was enabled previously. A working WAF workbook should now exist for your WAF resources.
Automatically detect and respond to threats
Using Sentinel ingested WAF logs, you can use Sentinel analytics rules to automatically detect security attacks, create security incident, and automatically respond to security incident using playbooks. Learn more Use playbooks with automation rules in Microsoft Sentinel.
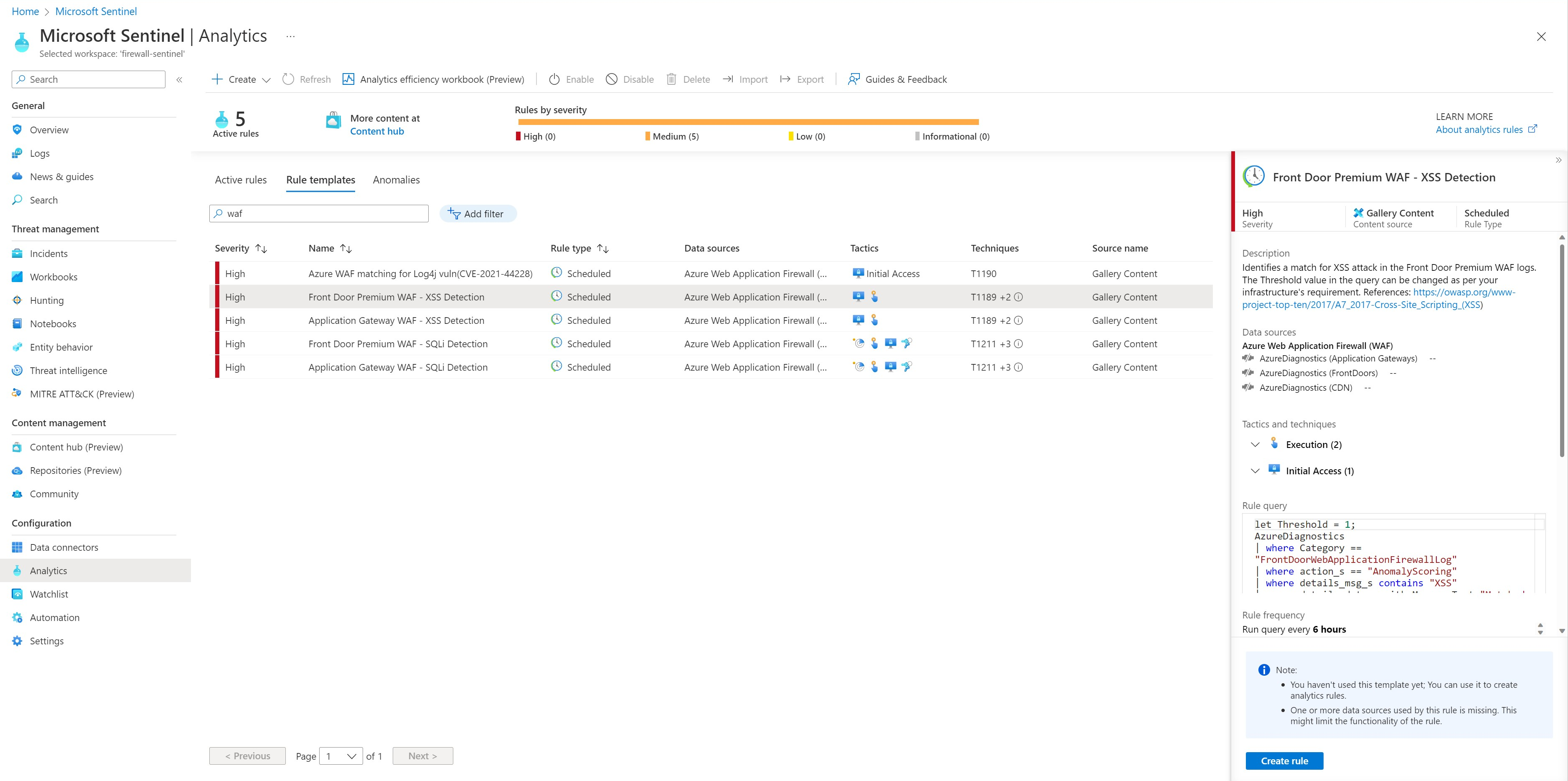
Azure WAF also comes in with built-in Sentinel detection rules templates for SQLi, XSS, and Log4J attacks. These templates can be found under the Analytics tab in the 'Rule Templates' section of Sentinel. You can use these templates or define your own templates based on the WAF logs.
The automation section of these rules can help you automatically respond to the incident by running a playbook. An example of such a playbook to respond to attack can be found in network security GitHub repository here. This playbook automatically creates WAF policy custom rules to block the source IPs of the attacker as detected by the WAF analytics detection rules.