Using promptbooks in Microsoft Security Copilot
Security Copilot comes with prebuilt promptbooks, a series of prompts that have been put together to accomplish specific security-related tasks. They can function in a similar way as security playbooks—ready-to-use workflows that can serve as templates to automate repetitive steps—for instance, with regard to incident response or investigations. Each prebuilt promptbook requires a specific input (for example, a code snippet or a threat actor name).
You can find the different promptbooks by going to the promptbook library or by selecting the Prompts icon  at the prompt bar. You can then search for a promptbook or select See all promptbooks to view all.
at the prompt bar. You can then search for a promptbook or select See all promptbooks to view all.
Available promptbooks include:
- Check impact of an external threat article
- Incident investigation
- Microsoft User analysis
- Suspicious script analysis
- Threat actor profile
- Threat Intelligence 360 report based on MDTI article
- Vulnerability impact assessment
Watch the following video to learn more about promptbooks:
Check impact of an external threat article
Using this promptbook, you can analyze any external threat intelligence articles to extract indicators from it and gather any relevant Microsoft Defender Threat Intelligence article.
To run this promptbook:
Make sure that you have turned on the Microsoft Threat Intelligence plugin by following the steps in Enable the Security Copilot integration in Defender TI.
In Security Copilot, select the Prompts button in the prompt bar and start to type a few letters of the promptbook named Check impact of an external threat article until the promptbook appears in the list.
Provide the URL of the external threat intelligence article you want to analyze and extract indicators from.
Next, select Submit.
Wait for Security Copilot to run the URL through the different prompts. If you see a round progress indicator in place of the response, then the promptbook is still running. Security Copilot generates responses for each of the prompts, building on each response until it gets to the last prompt.
Read the responses by Security Copilot. You can use the generated KQL queries to aid in investigation.
Incident investigation
You can run the incident investigation promptbook after supplying an incident number to either the Microsoft Sentinel or Microsoft Defender XDR plugin. Use the appropriate promptbook for the plugin you want to use. The incident investigation promptbooks contain several prompts to generate an executive report for a nontechnical audience that summarizes the investigation. Each prompt builds on the previous prompt.
To run the Microsoft Sentinel incident investigation promptbook:
Select the Prompts button in the prompt bar and start to type "incident investigation" until the promptbooks appear in the list.
Select Microsoft Sentinel incident investigation. (To use the Microsoft Defender XDR plugin instead, select Microsoft Defender XDR incident investigation.)
Supply the incident number that you want to investigate in the input box that says Sentinel Incident ID.
Next, select Submit in the upper left corner of the dialog box.
Wait for Security Copilot to run the incident number through the different prompts. If you see a round progress indicator in place of the response, then the promptbook is still running. Security Copilot generates responses for each of the prompts, building on each response until it gets to the last prompt.
Read the responses by Security Copilot. The last prompt by Security Copilot generates an executive report summarizing the investigation based on the responses. Review and verify whether the responses are accurate and meet your needs.
Microsoft User analysis
The Microsoft User analysis promptbook can be used by an IT Admin to analyze and get detailed insights about a user and associated devices across multiple Microsoft 365 products. This includes sign-in and authentication data from Microsoft Entra ID, device information from Intune, unusual activity details from Microsoft Purview, and a Microsoft Defender summary highlighting important detections.
To get a comprehensive response from this promptbook, you first need to activate or make sure that you have the following roles:
- Security Reader role for Microsoft Entra ID, Intune and Defender at a minimum
- Insider Risk Management Investigator or Analyst role for Microsoft Purview
To run this promptbook:
Go to the Promptbook library and look for the Microsoft User Analysis promptbook.
Select Start new session.
You need the following inputs:
- the user principal name or UPN of the user
- the time range you want Security Copilot to look up the information.
Next, select the Submit button in the upper right corner of the dialog box.
Wait for Security Copilot to run your inputs through the different prompts. If you see a round progress indicator in place of the response, then the promptbook is still running. Security Copilot generates responses for each of the prompts and builds on each until it gets to the last prompt.
Read the response from Security Copilot. Using the response from the prompts, you can deduce faster whether the user being investigated has been performing suspicious activities so you can focus on your next steps in securing your system.
Suspicious script analysis
The suspicious script analysis promptbook is useful when you're investigating a PowerShell or Windows command-line script. For example, if a PowerShell script was involved in a critical incident in your network, you can copy the body of the script and run the promptbook to find out more about it.
To run the promptbook: 1.Select the Prompts button in the prompt bar and start to type "suspicious script analysis" until the promptbooks appear in the list.
Select Suspicious script analysis.
Paste the script string that you want analyzed in the input box saying Script to analyze.
Next, select Submit in the upper left corner of the dialog box.
Wait for Security Copilot to run the script content through the different prompts. If you see a round progress indicator in place of the response, then the promptbook is still running. Security Copilot generates responses for each of the prompts, building on each response until it gets to the last prompt.
Read the responses by Security Copilot. The last prompt by Security Copilot generates a full report of what the script does, any related threat activities, and recommended next steps based on the assessment about file intent. Review and verify whether the responses are accurate and meet your needs.
Threat actor profile
The threat actor profile promptbook is a quick way to get an executive summary about a specific threat actor. The promptbook looks for any existing threat intelligence articles about the actor, including known tools, tactics, and procedures (TTPs) and indicators, including remediation suggestions. It then summarizes the findings into a report for less technical readers.
To run the threat actor profile promptbook:
Select the Prompts button in the prompt bar and start to type "threat actor profile" until the promptbooks appear in the list.
Select Threat actor profile.
Type the name of the threat actor in the input box that says Threat actor name.
Next, select the Submit button in the upper left corner of the dialog box.
Wait forSecurity Copilot to run the threat actor name through the different prompts. If you see a round progress indicator in place of the response, then the promptbook is still running. Security Copilot generates responses for each of the prompts and builds on each until it gets to the last prompt.
Read the response by Security Copilot. The last prompt by Security Copilot generates an easily readable report that includes pertinent information about the identified threat actor. Review and verify whether the responses are accurate and meet your needs.
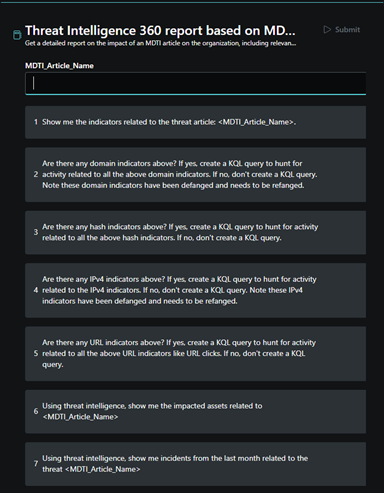
Threat Intelligence 360 report based on MDTI article
By using this promptbook, you can get a detailed report about whether the threats discussed in a given Microsoft Defender Threat Intelligence article is affecting the organization. including relevant indicators and hunting queries.
To run this promptbook:
Make sure that you have turned on the Microsoft Threat Intelligence plugin by following the steps in Enable the Security Copilot integration in Defender TI.
In Security Copilot, select the Prompts button in the prompt bar and start to type the promptbook name until the promptbook appears in the list.
Select the promptbook named Threat Intelligence 360 report based on MDTI article.
Type the name of the Defender Threat Intelligence article in the input box that says MDTI Article Name.
Next, select the Submit button in the upper left corner of the dialog box.
Wait for Security Copilot to run the article through the different prompts. If you see a round progress indicator in place of the response, then the promptbook is still running. Security Copilot generates responses for each of the prompts and builds on each until it gets to the last prompt.
Read the response by Security Copilot.
Vulnerability impact assessment
The vulnerability impact assessment promptbook accepts a CVE number or known vulnerability name to find out if the vulnerability has been publicly disclosed or exploited and whether it has been used by threat actors in their campaigns. It can then provide recommendations to address or mitigate the threat and summarize these findings in an executive summary.
To run this promptbook:
Select the Prompts button in the prompt bar and start to type "vulnerability impact assessment" until the promptbooks appear in the list.
Select Vulnerability impact assessment.
Type the CVE number or common vulnerability name that you want to learn about in the input box saying CVEID.
Next, select the Submit button in the upper left corner of the dialog box.
Wait for Security Copilot to run the vulnerability name or CVE through the different prompts. If you see a round progress indicator in place of the response, then the promptbook is still running. Security Copilot generates responses for each of the prompts and builds on each until it gets to the last prompt.
Read the response from Security Copilot. The last prompt generates an easily readable report about the vulnerability. The report includes details about known exploitation activities, including mitigation suggestions. Review and verify whether the responses are accurate and meet your needs.