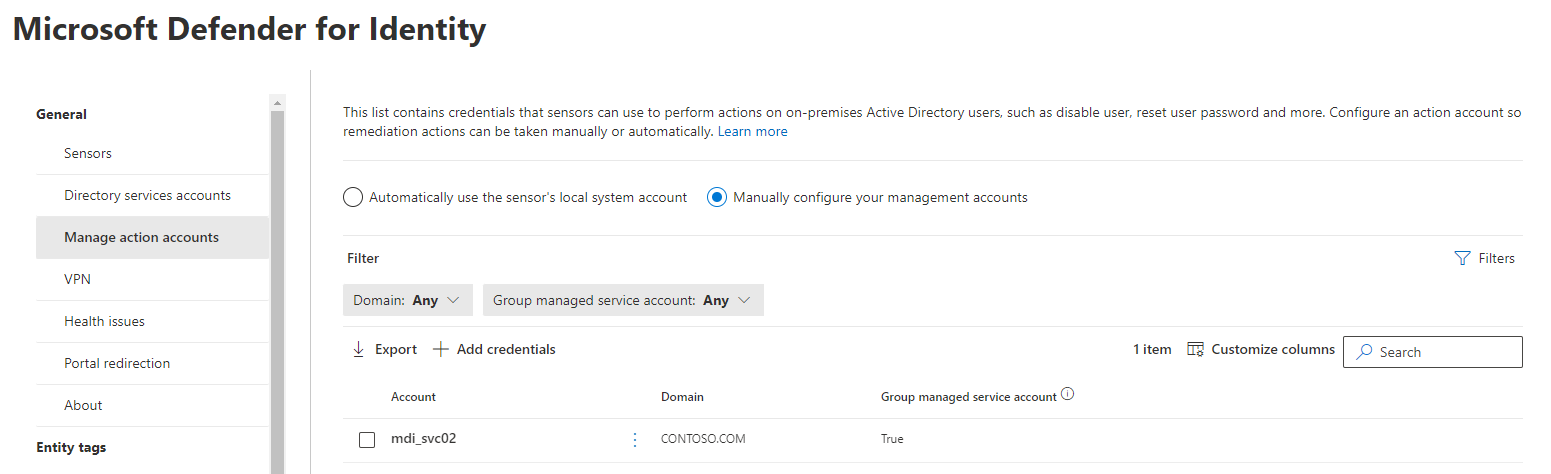
Configure Microsoft Defender for Identity action accounts
Defender for Identity allows you to take remediation actions targeting on-premises Active Directory accounts in the event that an identity is compromised. To take these actions, Microsoft Defender for Identity needs to have the required permissions to do so.
By default, the Microsoft Defender for Identity sensor impersonates the LocalSystem account of the domain controller and performs the actions, including attack disrupting scenarios from Microsoft Defender XDR.
If you need to change this behavior, set up a dedicated gMSA and scope the permissions that you need. For example:
Note
Using a dedicated gMSA as an action account is optional. We recommend that you use the default settings for the LocalSystem account.
Best practices for action accounts
We recommend that you avoid using the same gMSA account you configured for Defender for Identity managed actions on servers other than domain controllers. If you use the same account and the server is compromised, an attacker could retrieve the password for the account and gain the ability to change passwords and disable accounts.
We also recommend that you avoid using the same account as both the Directory Service account and the Manage Action account. This is because the Directory Service account requires only read-only permissions to Active Directory, and the Manage Action accounts needs write permissions on user accounts.
If you have multiple forests, your gMSA managed action account must be trusted in all of your forests, or create a separate one for each forest. For more information, see Microsoft Defender for Identity multi-forest support.
Create and configure a specific action account
Create a new gMSA account. For more information, see Getting started with Group Managed Service Accounts.
Assign the Log on as a service right to the gMSA account on each domain controller running the Defender for Identity sensor.
Grant the required permissions to the gMSA account as follows:
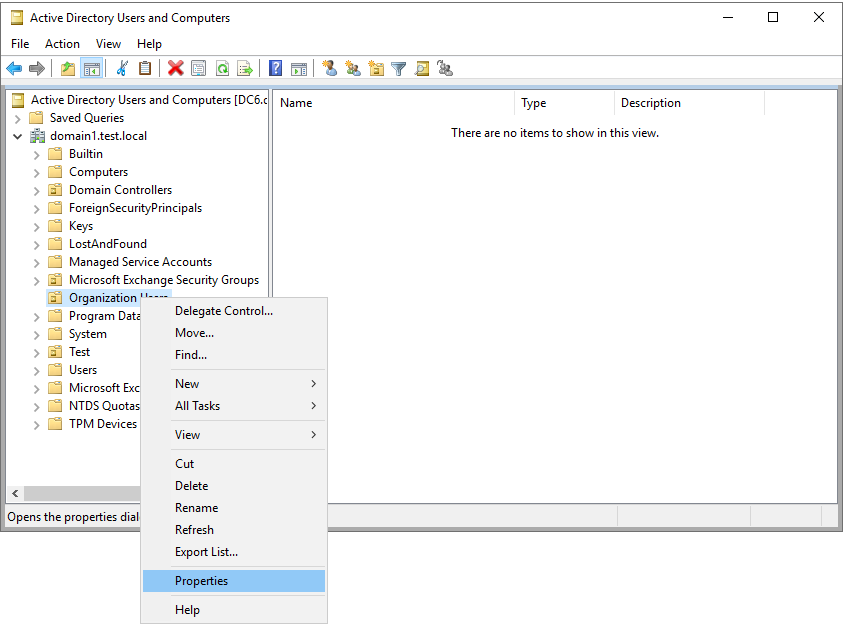
Open Active Directory Users and Computers.
Right-click the relevant domain or OU and select Properties. For example:
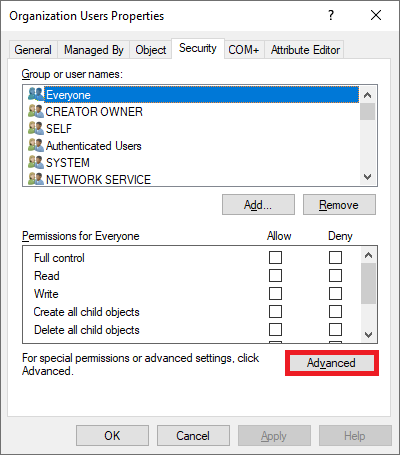
Go the Security tab and select Advanced. For example:
Select Add > Select a principal. For example:
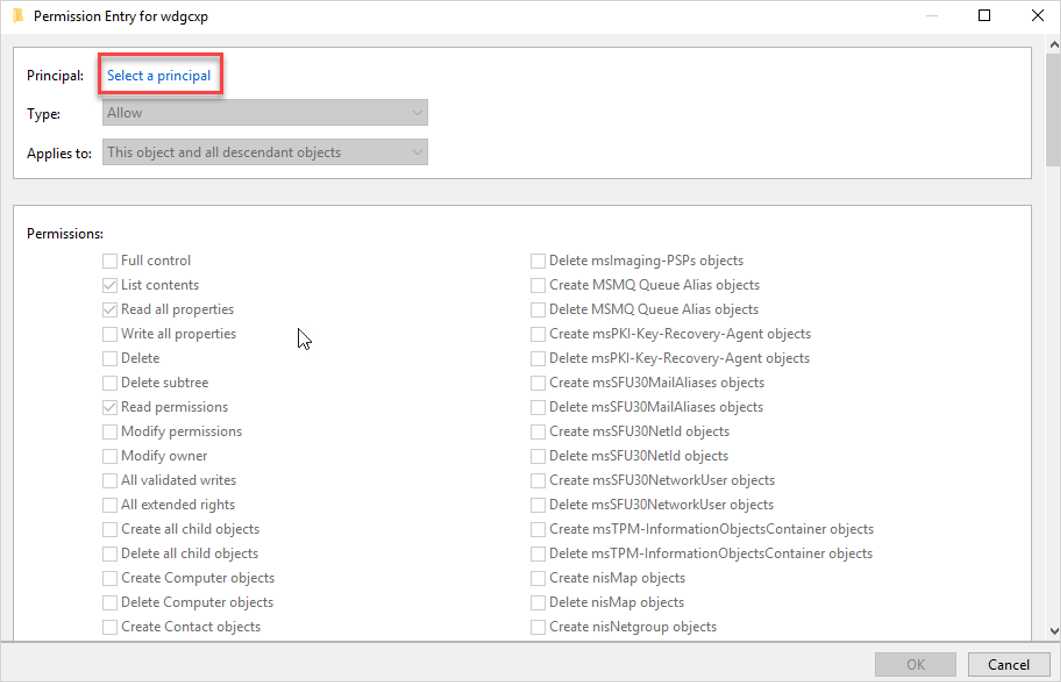
Make sure Service accounts is marked in Object types. For example:
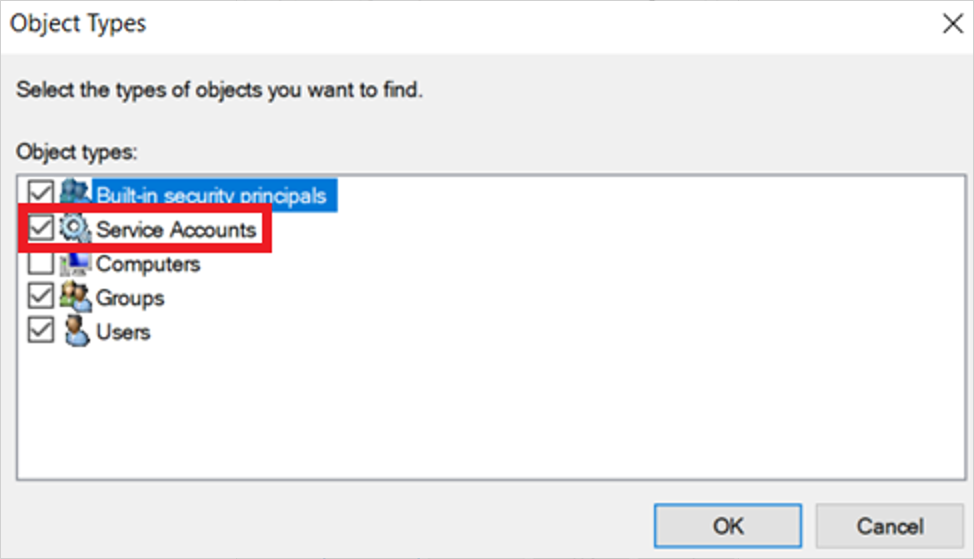
In the Enter the object name to select box, enter the name of the gMSA account and select OK.
In the Applies to field, select Descendant User objects, leave the existing settings, and add the permissions and properties shown in the following example:
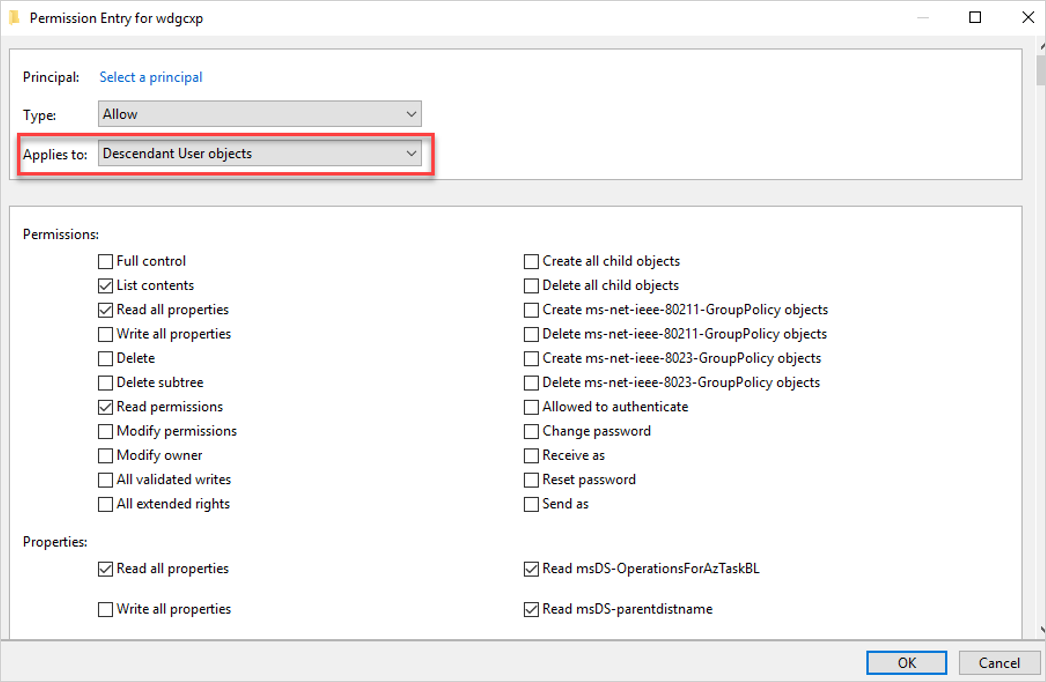
Required permissions include:
Action Permissions Properties Enable force password reset Reset password - Read pwdLastSet
-Write pwdLastSetTo disable user - - Read userAccountControl
-Write userAccountControl(Optional) In the Applies to field, select Descendant Group objects and set the following properties:
Read membersWrite members
Select OK.
Add the gMSA account in the Microsoft Defender portal
Go to the Microsoft Defender portal and select Settings -> Identities > Microsoft Defender for Identity > Manage action accounts > +Create new account.
For example:
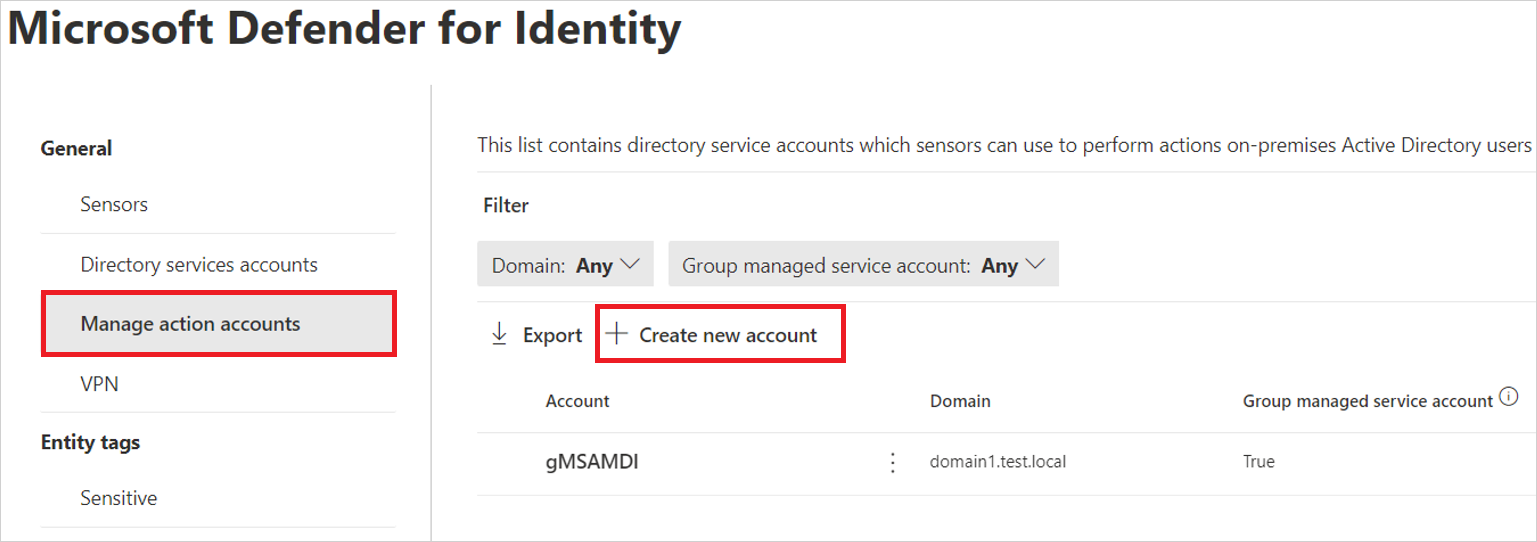
Enter the account name and domain and select Save.
Your action account is listed on the Manage action accounts page.
Related content
For more information, see Remediation actions in Microsoft Defender for Identity.
משוב
בקרוב: במהלך 2024, נפתור בעיות GitHub כמנגנון המשוב לתוכן ונחליף אותו במערכת משוב חדשה. לקבלת מידע נוסף, ראה: https://aka.ms/ContentUserFeedback.
שלח והצג משוב עבור