Investigate Defender for Identity security alerts in Microsoft Defender XDR
Note
Defender for Identity is not designed to serve as an auditing or logging solution that captures every single operation or activity on the servers where the sensor is installed. It only captures the data required for its detection and recommendation mechanisms.
This article explains the basics of how to work with Microsoft Defender for Identity security alerts in Microsoft Defender XDR.
Defender for Identity alerts are natively integrated into Microsoft Defender XDR with a dedicated Identity alert page format.
The Identity alert page gives Microsoft Defender for Identity customers better cross-domain signal enrichment and new automated identity response capabilities. It ensures that you stay secure and helps improve the efficiency of your security operations.
One of the benefits of investigating alerts through Microsoft Defender XDR is that Microsoft Defender for Identity alerts are further correlated with information obtained from each of the other products in the suite. These enhanced alerts are consistent with the other Microsoft Defender XDR alert formats originating from Microsoft Defender for Office 365 and Microsoft Defender for Endpoint. The new page effectively eliminates the need to navigate to another product portal to investigate alerts associated with identity.
Alerts originating from Defender for Identity can now trigger the Microsoft Defender XDR automated investigation and response (AIR) capabilities, including automatically remediating alerts and the mitigation of tools and processes that can contribute to the suspicious activity.
Important
As part of the convergence with Microsoft Defender XDR, some options and details have changed from their location in the Defender for Identity portal. Please read the details below to discover where to find both the familiar and new features.
Review security alerts
Alerts can be accessed from multiple locations, including the Alerts page, the Incidents page, the pages of individual Devices, and from the Advanced hunting page. In this example, we'll review the Alerts page.
In Microsoft Defender XDR, go to Incidents & alerts and then to Alerts.
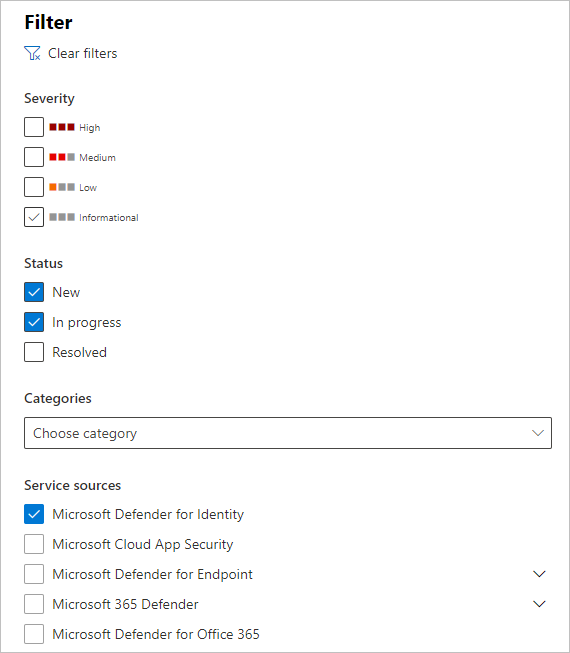
To see alerts from Defender for Identity, on the top-right select Filter, and then under Service sources select Microsoft Defender for Identity, and select Apply:
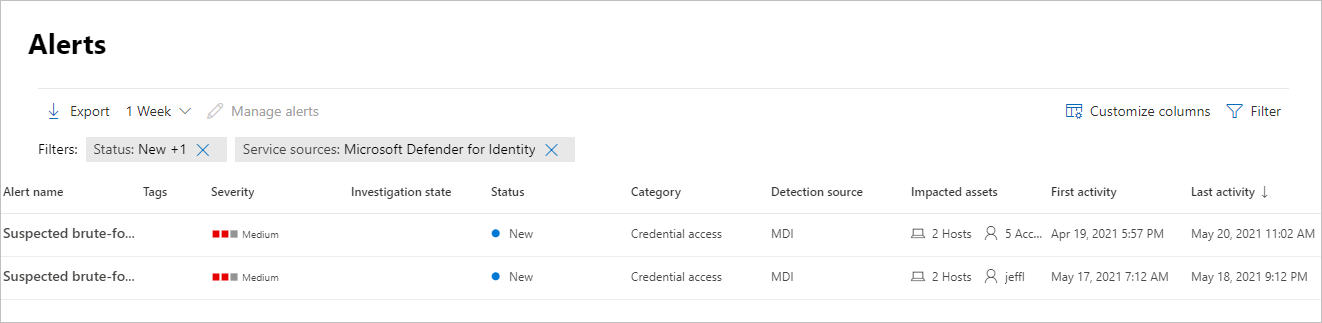
The alerts are displayed with information in the following columns: Alert name, Tags, Severity, Investigation state, Status, Category, Detection source, Impacted assets, First activity, and Last activity.
Security alert categories
Defender for Identity security alerts are divided into the following categories or phases, like the phases seen in a typical cyber-attack kill chain.
- Reconnaissance alerts
- Compromised credential alerts
- Lateral movement alerts
- Domain dominance alerts
- Exfiltration alerts
Manage alerts
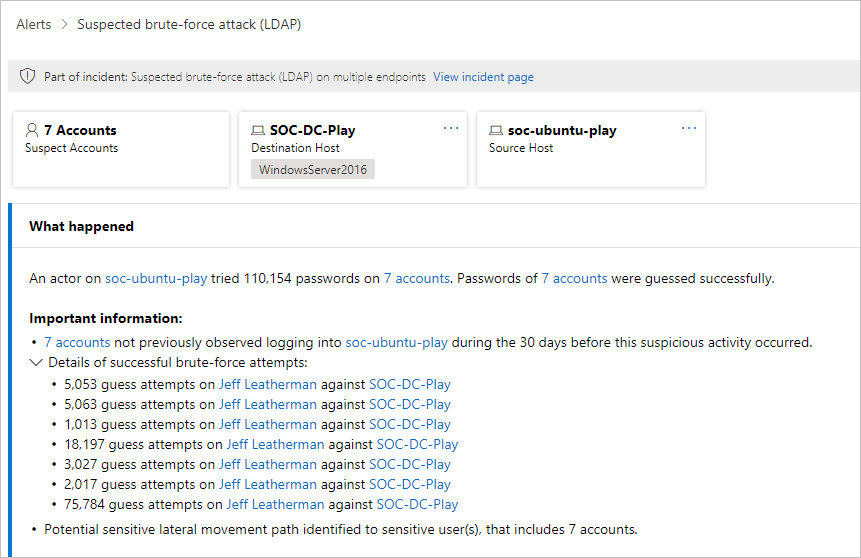
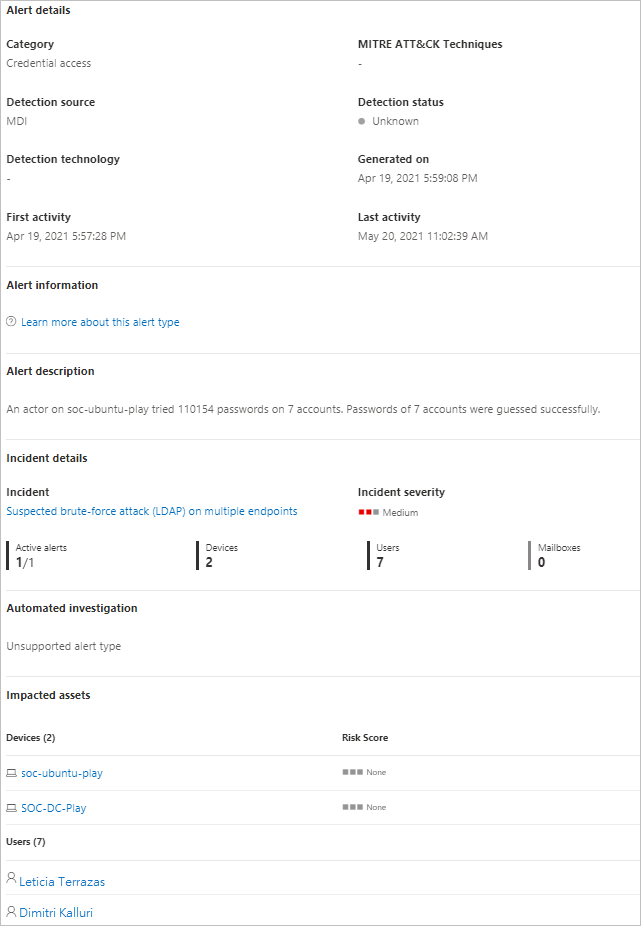
If you select the Alert name for one of the alerts, you'll go to the page with details about the alert. In the left pane, you'll see a summary of What happened:
Above the What happened box are buttons for the Accounts, Destination Host and Source Host of the alert. For other alerts, you might see buttons for details about additional hosts, accounts, IP addresses, domains, and security groups. Select any of them to get more details about the entities involved.
On the right pane, you'll see the Alert details. Here you can see more details and perform several tasks:
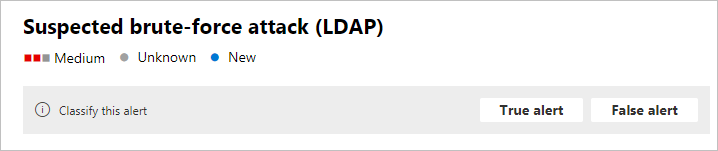
Classify this alert - Here you can designate this alert as a True alert or False alert
Alert state - In Set Classification, you can classify the alert as True or False. In Assigned to, you can assign the alert to yourself or unassign it.
Alert details - Under Alert details, you can find more information about the specific alert, follow a link to documentation about the type of alert, see which incident the alert is associated with, review any automated investigations linked to this alert type, and see the impacted devices and users.
Comments & history - Here you can add your comments to the alert, and see the history of all actions associated with the alert.
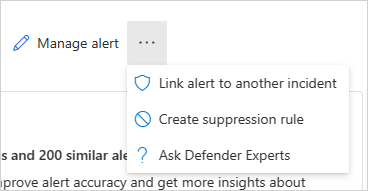
Manage alert - If you select Manage alert, you'll go to a pane that will allow you to edit the:
Status - You can choose New, Resolved or In progress.
Classification - You can choose True alert or False alert.
Comment - You can add a comment about the alert.
If you select the three dots next to Manage alert, you can Link alert to another incident, Create suppression rule (available for preview customers only), or Ask Defender Experts.
You can also export the alert to an Excel file. To do this, select Export.
Note
In the Excel file, you now have two links available: View in Microsoft Defender for Identity and View in Microsoft Defender XDR. Each link will bring you to the relevant portal, and provide information about the alert there.
Tuning alerts
Tune your alerts to adjust and optimize them, reducing false positives. Alert tuning allows your SOC teams to focus on high-priority alerts and improve threat detection coverage across your system. In Microsoft Defender XDR, create rule conditions based on evidence types, and then apply your rule on any rule type that matches your conditions.
For more information, see Tune an alert.
See also
Learn more
- Try our interactive guide: Detect suspicious activities and potential attacks with Microsoft Defender for Identity