Use the settings catalog to configure settings on Windows, iOS/iPadOS, and macOS devices
The settings catalog lists all the settings you can configure all in one place. This feature simplifies how you create a policy and how you see all the available settings. For example, you can use the settings catalog to create a BitLocker policy with all BitLocker settings.
You can also use Microsoft Copilot in Intune. When you use the Copilot features with the settings catalog, you can use Copilot to:
- Learn more about each setting, get impact what if analysis, and find potential conflicts.
- Summarize existing policies and get impact analysis on users and security.
If you prefer to configure settings at a granular level, similar to using on-premises Group Policy Objects (GPOs), the settings catalog is a natural transition to cloud-based policy.
When you create the policy, you start from scratch. You add only the settings you want to control and manage.
To manage and secure devices in your organization, use the settings catalog as part of your mobile device management (MDM) solution. More settings are continually being added to the settings catalog. For a current list of the settings, see the IntunePMFiles/DeviceConfig GitHub repository.
This feature applies to:
iOS/iPadOS
Includes device settings that are directly generated from Apple Profile-Specific Payload Keys. More settings and keys are continually being added. To learn more, see Profile-Specific Payload Keys on Apple's website.
Apple's declarative device management (DDM) is built into the settings catalog. When you configure settings from the settings catalog on iOS/iPadOS 15+ devices enrolled using User Enrollment, you're automatically using DDM. If DDM doesn't work, these devices will use Apple's standard MDM protocol. All other iOS/iPadOS devices continue to use Apple's standard MDM protocol.
macOS
Includes device settings that are directly generated from Apple Profile-Specific Payload Keys. More settings and keys are continually being added. To learn more about profile-specific payload keys, see Profile-Specific Payload Keys on Apple's website.
Apple's declarative device management (DDM) is available in the settings catalog. You can use DDM to manage software updates, passcode restrictions, and more.
You can also use the settings catalog to configure newer versions of Microsoft Edge and other features, instead of property list (plist) files. For more information, see:
- Built-in macOS features replacing plist files
- Add a property list file to macOS devices using Microsoft Intune.
You can continue using the preference file to:
- Configure earlier versions of Microsoft Edge.
- Configure Microsoft Edge browser settings that aren't in the settings catalog.
Windows 10/11
There are thousands of settings, including settings that weren't previously available. These settings are directly generated from the Windows configuration service providers (CSPs). You can also configure Administrative Templates and have more Administrative Template settings available. As Windows adds or exposes more settings to MDM providers, these settings are added to Microsoft Intune for you to configure.
Tip
- For a list of the settings in the settings catalog, see the IntunePMFiles/DeviceConfig GitHub repository.
- To see the Microsoft Edge policies you have configured, open Microsoft Edge and go to
edge://policy.
This article describes the steps to create a policy, shows how to search and filter the settings in Intune, and shows how to use Copilot.
When you create the policy, it creates a device configuration profile. You can then assign or deploy this profile to devices in your organization.
For information about features you can configure using the settings catalog, see Tasks you can complete using the Settings Catalog in Intune.
Create the policy
You create the policy by using the settings catalog profile type.
Sign in to the Microsoft Intune admin center.
Select Devices > Manage devices > Configuration > Create > New policy.
Enter the following properties:
- Platform: Select iOS/iPadOS, macOS, or Windows 10 and later.
- Profile type: Select Settings catalog.
Select Create.
In Basics, enter the following properties:
- Name: Name your profiles so you can easily identify them later. For example, a good profile name is macOS: Microsoft Edge settings or Win10: BitLocker settings for all Win10 devices.
- Description: Enter a description for the profile. This setting is optional but recommended.
Select Next.
In Configuration settings, select Add settings. In the settings picker, select a category to see all the available settings.
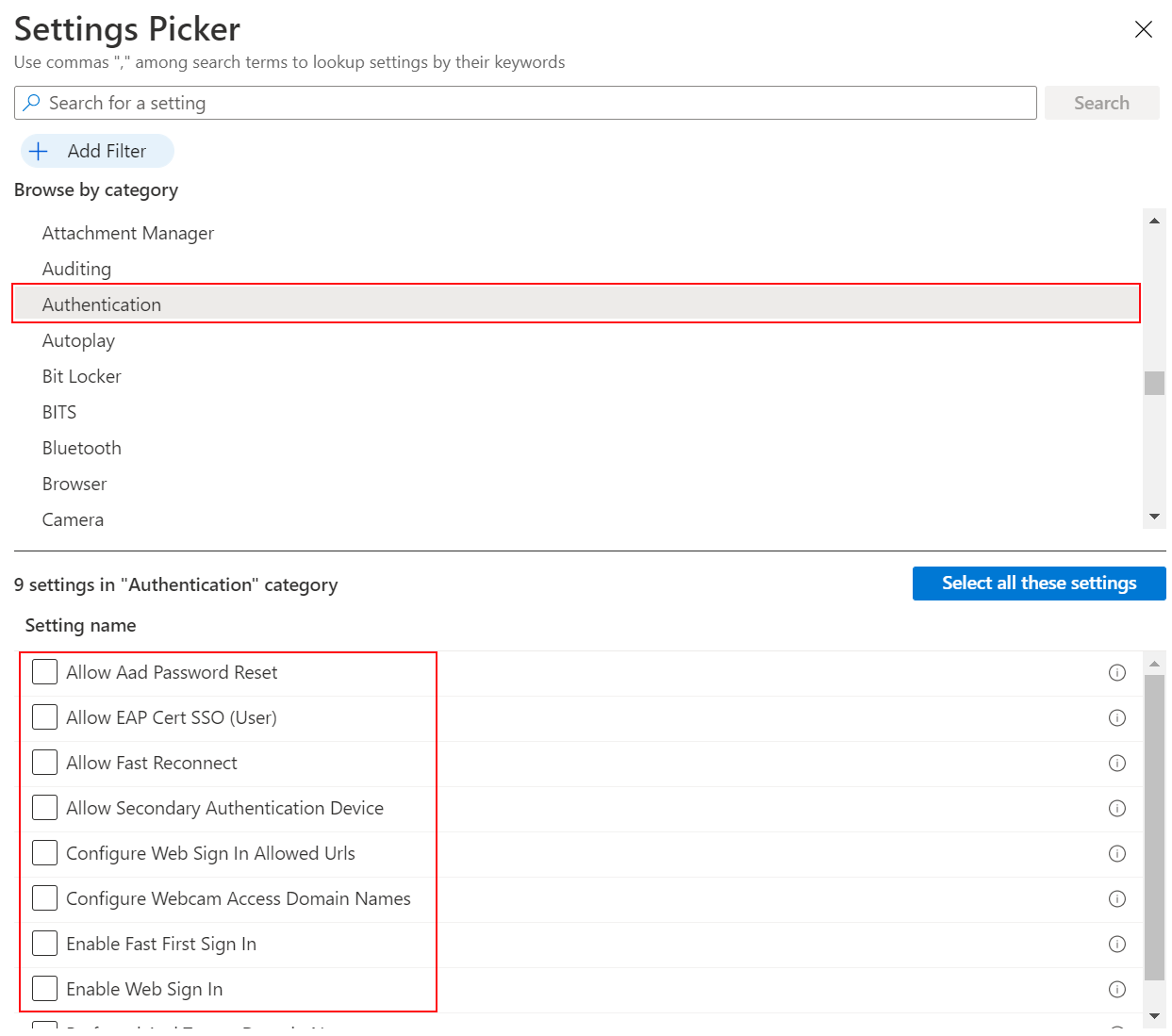
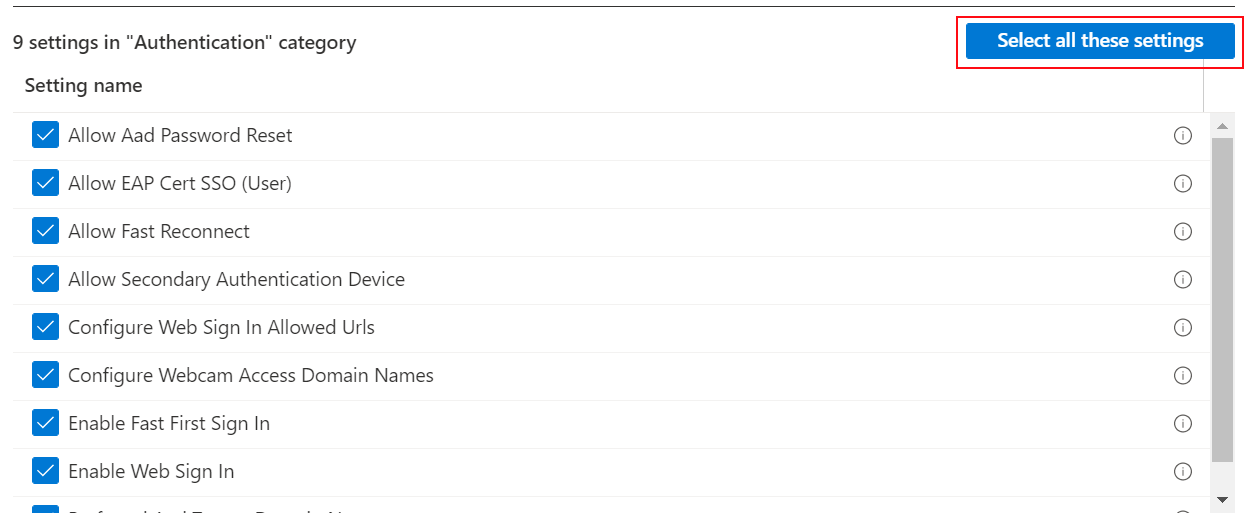
For example, select Windows 10 and later, and then select Authentication to see all the settings in this category:
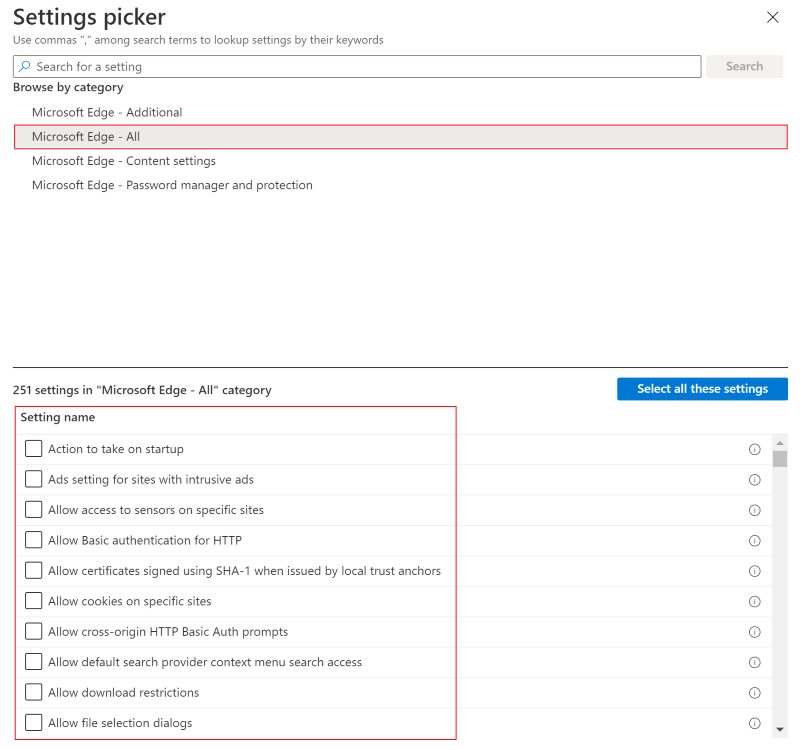
For example, select macOS. The Microsoft Edge - All category lists all the settings you can configure. The other categories include settings that are obsolete or that apply to older versions:
Tip
On macOS, the categories are temporarily removed. To find a specific setting, use the Microsoft Edge - All category, or search for the setting name. For a list of the setting names, see Microsoft Edge - Policies.
Use the Learn more link in the tooltip to see if a setting is obsolete and to see the supported versions.
Select any setting you want to configure. Or, choose Select all these settings:
After you add your settings, close the settings picker. All the settings are shown and configured with a default value, such as Block or Allow. These defaults values are the same default values in the OS. If you don't want to configure a setting, select the minus sign (
-):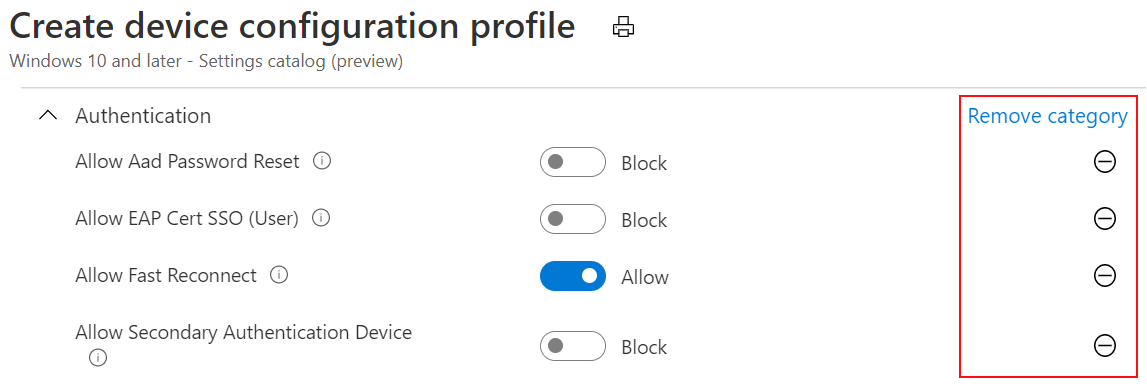
When you select the minus:
- Intune doesn't change or update this setting. The minus is the same as Not configured. When set to Not configured, the setting is no longer managed.
- The setting is removed from the policy. The next time you open your policy, the setting isn't shown. But you can re-add it.
- The next time devices check in, the setting is no longer locked. Another policy or device user can change the policy.
Tip
In the Windows setting tooltips, Learn more links to the CSP.
When a setting allows multiple values, we recommend that you add each value separately. For example, you can enter multiple values in the Bluetooth > Services Allowed List setting. Enter each value on a separate line:
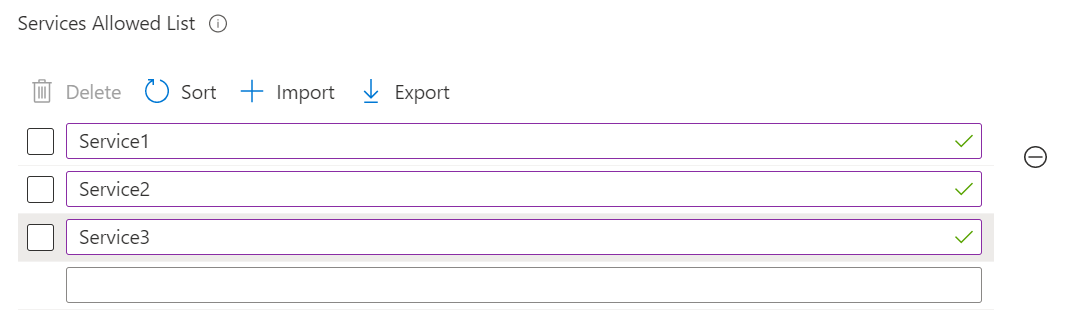
You can add multiple values in a single field, but you may experience a character limit.
Select Next.
In Scope tags (optional), assign a tag to filter the profile to specific IT groups, such as
US-NC IT TeamorJohnGlenn_ITDepartment. For more information about scope tags, see Use RBAC roles and scope tags for distributed IT.Select Next.
In Assignments, select the users or groups that will receive your profile. For more information, see Assign user and device profiles.
Select Next.
In Review + create, review your settings. When you select Create, your changes are saved, and the profile is assigned. The policy is also shown in the profiles list.
The next time the device checks for configuration updates, the settings you configured are applied.
Find some settings and learn more about each setting
There are thousands of settings available in the settings catalog. To find the settings you want, use the search and filter features.
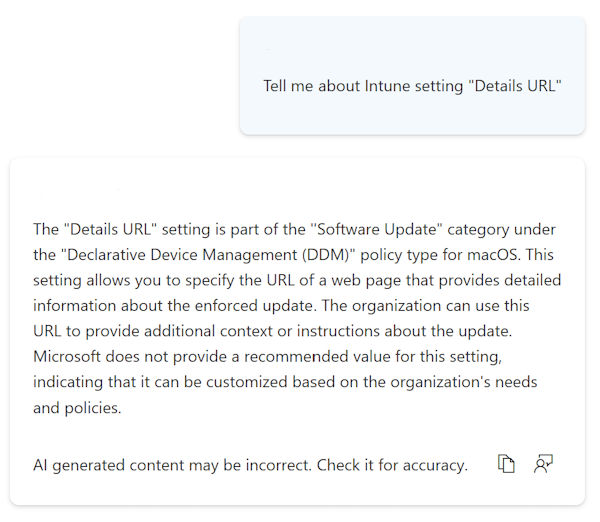
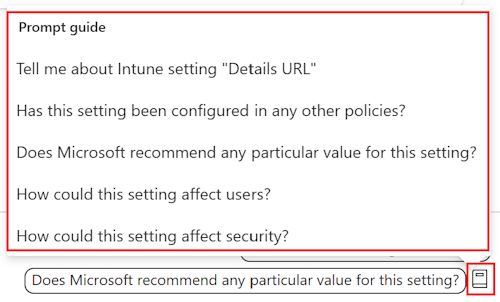
If you use Copilot, you can get AI-generated information about each setting.
When you create a new policy or update an existing policy, there are built-in search and filter features to help you find settings.
To find specific settings in your policy, you can use Add settings > Search. You can search by category, such as
browser; search for a keyword, such asofficeorgoogle; and search for specific settings.For example, search for
internet explorer. All the settings withinternet explorerare shown. Select a category to see the available settings: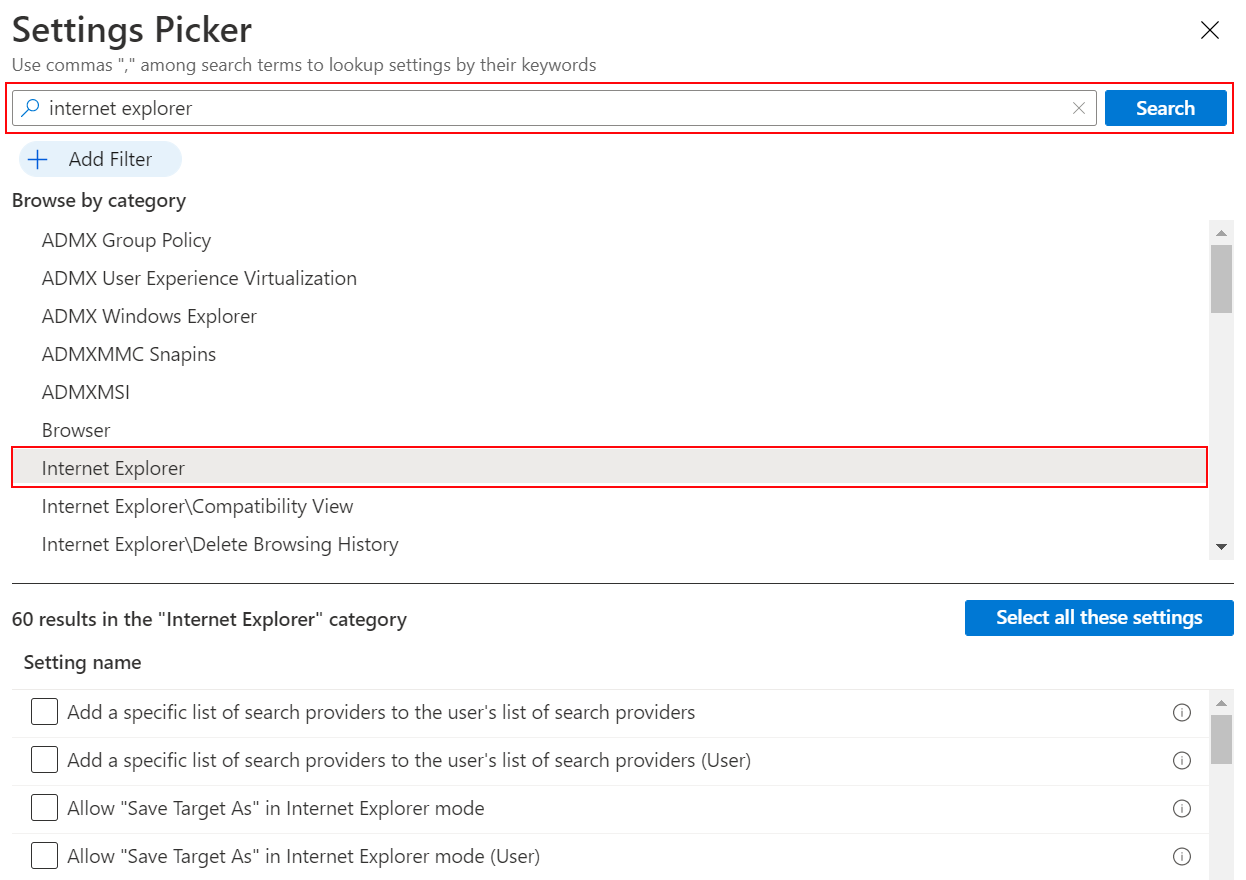
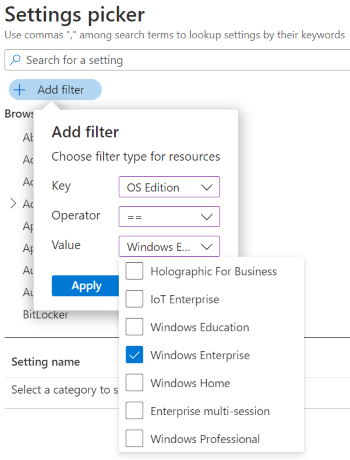
In your policy, use Add settings > Add filter. Select the key, operator, and value.
When you filter on OS Edition, you can filter the settings that apply to specific Windows editions:
Note
For the Edge, Office, and OneDrive settings, the OS version or edition doesn't determine if the settings apply. So, if you filter to a specific edition, like Windows Professional, the Edge, Office, and OneDrive settings aren't shown.
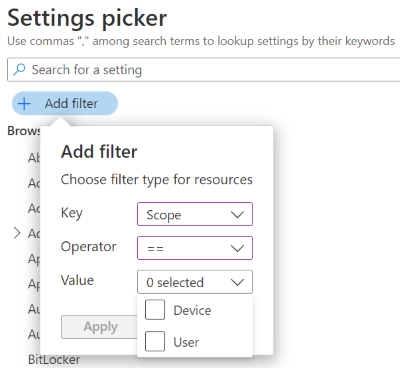
You can also filter the settings by device or user scope. For more information, see Device scope vs. user scope settings (in this article):
Copy a profile
Select Duplicate to create a copy of an existing profile. Duplicating is useful when you need a profile that's similar to the original one. The copy contains the same setting configurations and scope tags as the original profile but doesn't have assignments attached to it.
After you give the new profile a name, you can edit the profile to adjust the settings and add assignments.
- Go to Devices > Manage devices > Configuration.
- Find the profile that you want to copy. Right-click the profile or select the ellipses context menu (
…). - Select Duplicate.
- Enter a new name and description for the policy.
- Save your changes.
Import and export a profile
This feature applies to:
- Windows 11
- Windows 10
When you create a settings catalog policy, you can export the policy to a .json file. You can then import this file to create a new policy. This feature is useful if you want to create a policy that's similar to an existing policy. For example, you export a policy, import it to create a new policy, and then make changes to the new policy.
Go to Devices > Manage devices > Configuration.
To export an existing policy, select the Windows settings catalog policy and then select the ellipsis/context menu (
…) > Export JSON: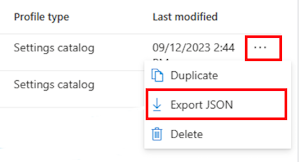
To import a previously exported settings catalog policy, select Create > Import policy:
Select the JSON file you exported and name your new policy. Save your changes.
Conflicts and reporting
Conflicts happen when the same setting is updated to different values, including policies configured using the settings catalog. In the Intune admin center, you can check the status of your existing policies. The data is refreshed automatically, nearly in real time.
There are built-in features that can help you troubleshoot conflicts, including per-setting status reporting.
If you use Copilot, you can use built-in prompts to get more information about existing policies, including their impact.
In the Intune admin center, you can use the built-in reporting features to help find and resolve conflicts.
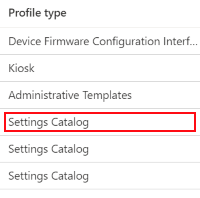
In the Intune admin center, select Devices > Manage devices > Configuration. In the list, select the policy you created using the settings catalog. The Profile type column shows Settings Catalog:
When you select the policy, the device status is displayed. It shows a summary of your policy state and the policy properties. You can also change or update your policy in the Configuration settings section:
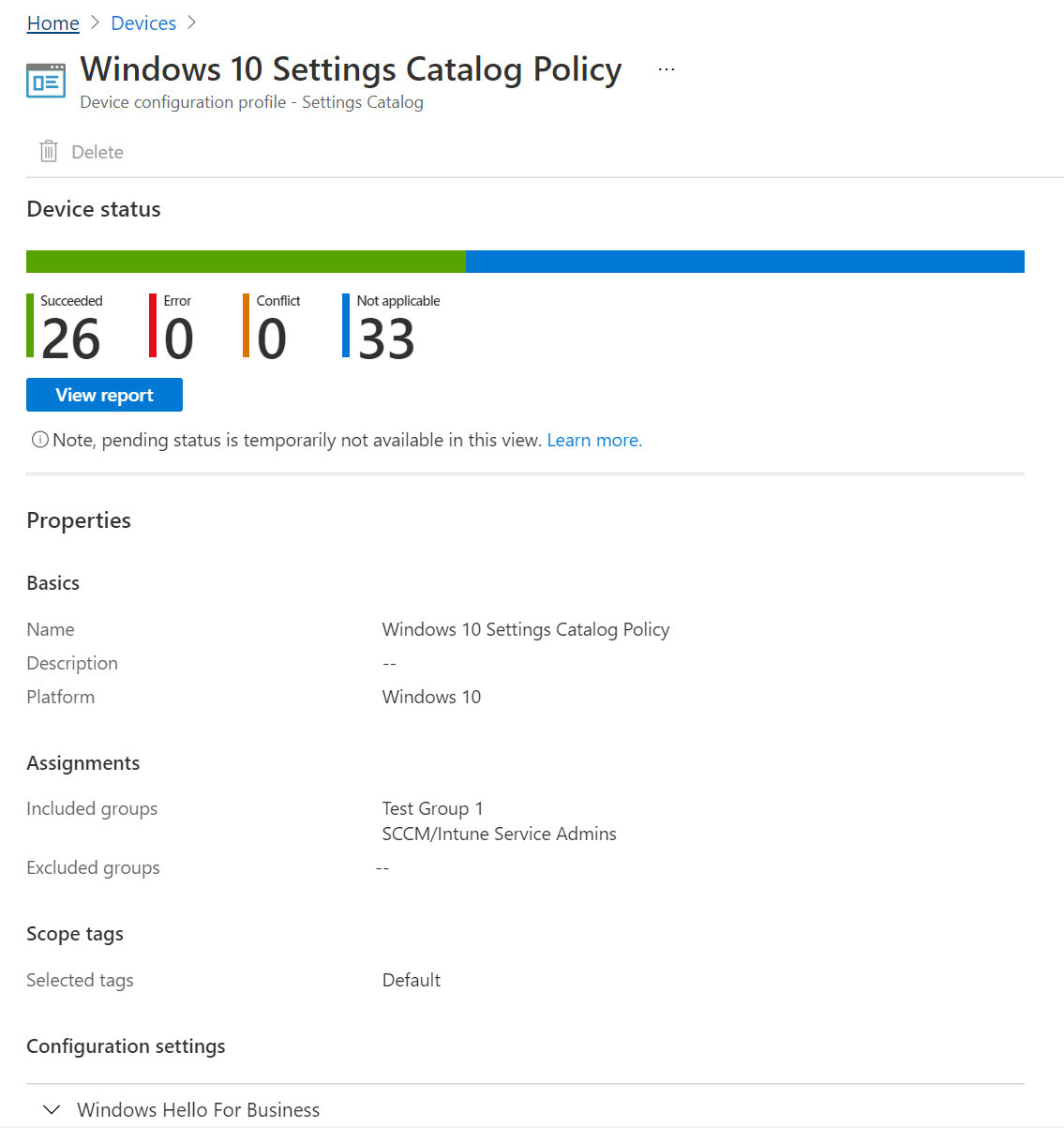
Select View report. The report shows detailed information, including the device name, the policy status, and more. You can also filter on the deployment status and Export the report to a
.csvfile:You can also look at the status of each setting using the per-setting status, which is the number of devices affected by each setting in the policy.
You can:
- See the number of devices with the setting successfully applied, in conflict, or in error.
- Select the number of devices in compliance, conflict, or error. See a list of users or devices in that state.
- Search, sort, filter, export, and go to the next and previous pages.
In the admin center, select Devices > Monitor > Assignment failures. If your settings catalog policy failed to deploy because of an error or conflict, it shows in this list. You can also Export to a
.csvfile.Select the policy to see the devices. Then, select a specific device to see the setting that failed and possibly an error code.
Tip
Intune reports is a great resource. For information about all the reporting data you can view, go to Intune reports.
For more information about conflict resolution, see:
Settings catalog vs. templates
When you create the policy, you have two policy types to choose from: Settings catalog and Templates:
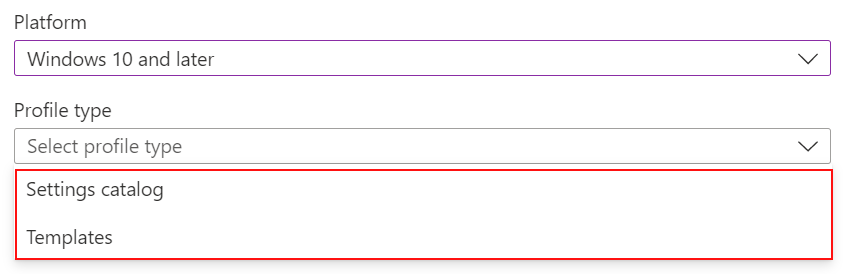
The Templates include a logical group of settings, such as kiosk, VPN, Wi-Fi, and more. Use this option if you want to use these groupings to configure your settings.
The Settings catalog lists all the available settings. If you want to see all the available firewall settings or all the available BitLocker settings, use this option. Also, use this option if you're looking for specific settings.
Device scope vs. user scope settings
When you select a setting, some settings have a (User) or (Device) tag in the setting name, such as Allow EAP Cert SSO (User) or Grouping (Device). When you see these tags, the policy only affects the user scope or the device scope.
For more information about user scope and device scope, see the Policy CSP.
Device and user groups are used when you assign your policies. Device and user scopes describe how a policy is enforced.
Scope assignment behavior
When you deploy policy from Intune, you can assign user scope or device scope to any type of target group. Behavior of the policy per user depends on the scope of the setting:
- User scoped policy writes to
HKEY_CURRENT_USER (HKCU). - Device scoped policy writes to
HKEY_LOCAL_MACHINE (HKLM).
When a device checks in to Intune, the device always presents a deviceID. The device might or might not present a userID, depending on the check-in timing and whether a user is signed in.
The following list includes some possible combinations of scope, assignment, and the expected behavior:
- If a device scope policy is assigned to a device, all users on that device have that setting applied.
- If a device scoped policy is assigned to a user, once that user signs in and an Intune sync occurs, the device scope settings apply to all users on the device.
- If a user scope policy is assigned to a device, all users on that device have that setting applied. This behavior is like a loopback set to merge.
- If a user scoped policy is assigned to a user, only that user has that setting applied.
- There are some settings that are available in the user scope and the device scope. If one of these settings is assigned to both user and device scope, user scope takes precedence over device scope.
If there isn't a user hive during initial check-ins, you can see some user scope settings marked as not applicable. This behavior happens in the early moments of device activity before a user is present.