Turn on app governance for Microsoft Defender for Cloud Apps
This article describes how to turn on Microsoft Defender for Cloud Apps app governance.
Note
By default, the Microsoft Defender for Cloud Apps instance in the US Government environments cannot connect to resources in Azure commercial and is FedRAMP compliant. However, App Governance is not FedRAMP certified. App Governance will only store and process data in secure locations within the United States and the data will only be accessible by approved Microsoft employees.
Prerequisites
Before you start, verify that you satisfy the following prerequisites:
Microsoft Defender for Cloud Apps must be present in your account as either a standalone product or as part of the various license packages.
If you aren't already a Defender for Cloud Apps customer, you can sign up for a free trial.
You must have one of the appropriate roles to turn on app governance and access it.
Your organization's billing address must be in a region other than Brazil, Singapore, Latin America, South Korea, Switzerland, Norway, South Africa, Sweden or United Arab Emirates.
Turn on app governance
If your organization satisfies the prerequisites, go to Microsoft Defender XDR > Settings > Cloud Apps > App governance and select Use app governance. For example:
After you've signed up for app governance, you'll need to wait up to 10 hours to see and use the product.
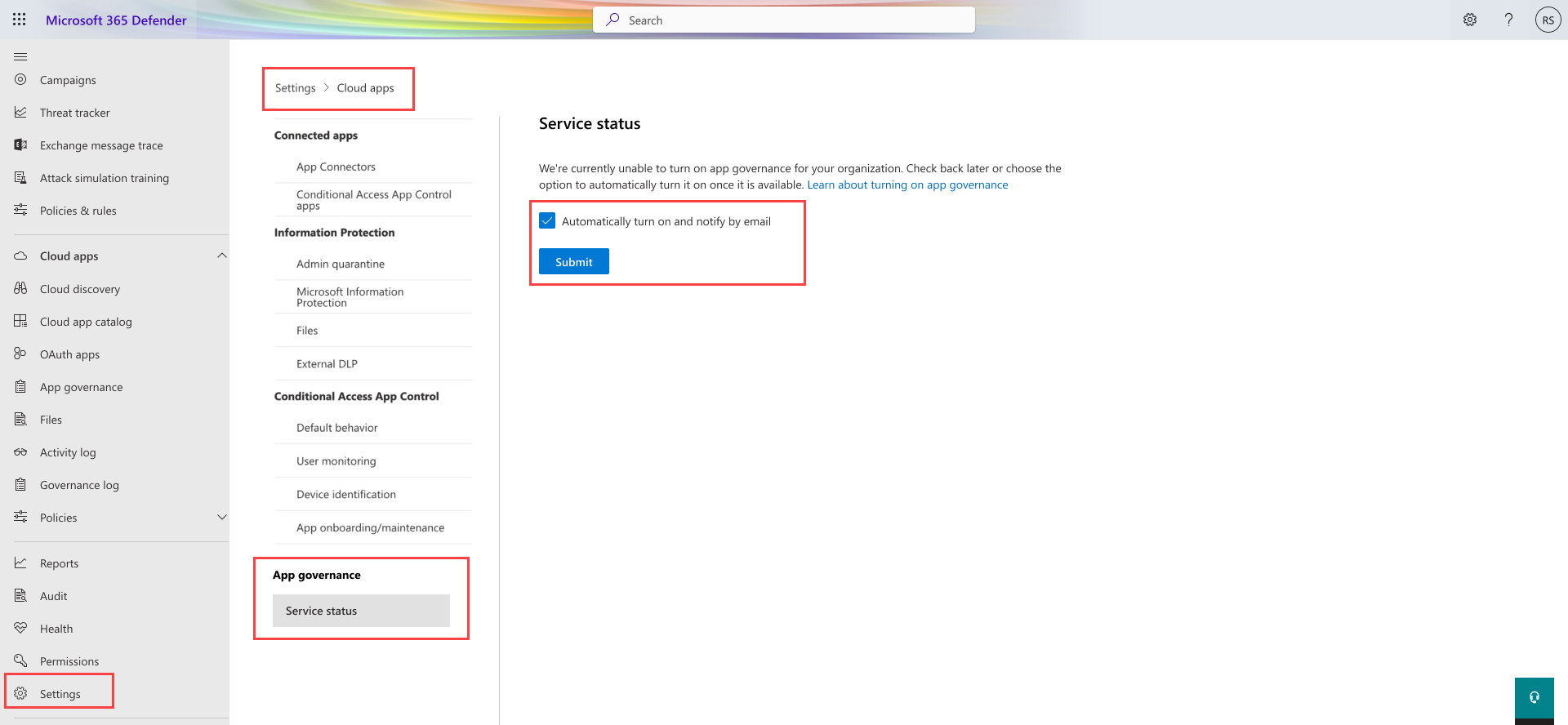
If you're unable to see the app governance option in the settings page, it might be due to one or more of the following reasons:
App governance isn't yet supported in your region.
We're unable to serve you at the moment due to capacity constraints.
You can join the waitlist and provide your consent, so that we can turn on app governance for your organization automatically when app governance becomes available for you. When we turn on app governance, we'll notify you by email.
For example:
Licensing
App governance is available to organizations with a valid Defender for Cloud Apps license. For more information, see the Microsoft 365 licensing datasheet.
Roles
You must have at least one of these roles to turn on app governance:
- Company Admin
- Security Admin
- Compliance Admin
- Compliance Data Admin
- Cloud App Security admin
The following table lists the app governance capabilities for each role.
| Role | Read the dashboard | Read all apps | Read policies | Create, update, or delete policies | Read alerts | Update alerts | Read settings | Update settings | Read Remediation | Update Remediation |
|---|---|---|---|---|---|---|---|---|---|---|
| Company or Global Administrator |  |
 |
 |
 |
 |
 |
 |
 |
 |
 |
| Compliance Administrator |  |
 |
 |
 |
 |
 |
 |
 |
 |
|
| Compliance Data Administrator |  |
 |
 |
 |
 |
 |
 |
 |
 |
|
| Global Reader |  |
 |
 |
 |
 |
|||||
| Security Administrator |  |
 |
 |
 |
 |
 |
 |
 |
 |
|
| Security Operator |  |
 |
 |
 |
 |
 |
 |
 |
 |
|
| Security Reader |  |
 |
 |
 |
 |
 |
For more information about each role, see Administrator role permissions.
Important
Microsoft recommends that you use roles with the fewest permissions. This helps improve security for your organization. Global Administrator is a highly privileged role that should be limited to emergency scenarios when you can't use an existing role.
Note
App governance alerts will not flow to Microsoft Defender XDR or show up in app governance until you have provisioned both Defender for Cloud Apps and Microsoft Defender XDR by accessing their respective portals at least once.