Deployment
Azure App Configuration supports the following methods to read and manage your configuration during deployment:
- ARM template
- Bicep
- Terraform
Manage Azure App Configuration resources in deployment
Azure Resource Manager Authorization
You must have Azure Resource Manager permissions to manage Azure App Configuration resources. Azure role-based access control (Azure RBAC) roles that provide these permissions include the Microsoft.AppConfiguration/configurationStores/write or Microsoft.AppConfiguration/configurationStores/* action. Built-in roles with this action include:
- Owner
- Contributor
To learn more about Azure RBAC and Microsoft Entra ID, see Authorize access to Azure App Configuration using Microsoft Entra ID.
Manage Azure App Configuration data in deployment
Azure App Configuration data, such as key-values and snapshots, can be managed in deployment. When managing App Configuration data using this method, it's recommended to set your configuration store's Azure Resource Manager authentication mode to Pass-through. This authentication mode ensures that data access requires a combination of data plane and Azure Resource Manager management roles and ensuring that data access can be properly attributed to the deployment caller for auditing purpose.
Azure Resource Manager authentication mode
To configure the Azure Resource Manager authentication mode of an Azure App Configuration resource in the Azure portal, follow these steps:
Navigate to your Azure App Configuration resource in the Azure portal
Locate the Access settings setting under Settings
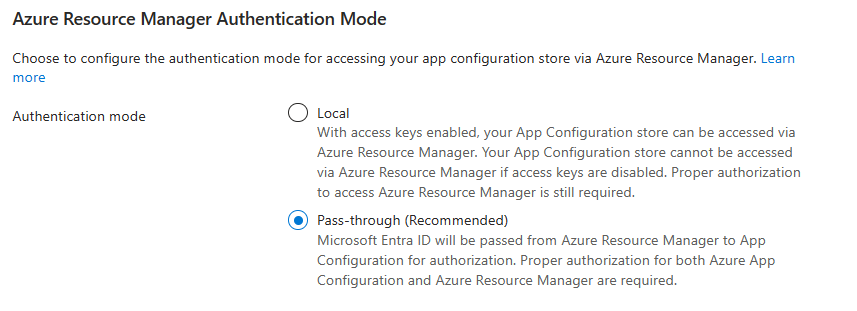
Select the recommended Pass-through authentication mode under Azure Resource Manager Authentication Mode
Note
Local authentication mode is for backward compatibility and has several limitations. It does not support proper auditing for accessing data in deployment. Under local authentication mode, key-value data access inside an ARM template/Bicep/Terraform is disabled if access key authentication is disabled. Azure App Configuration data plane permissions are not required for accessing data under local authentication mode.
Azure App Configuration Authorization
When your App Configuration resource has its Azure Resource Manager authentication mode set to Pass-through, you must have Azure App Configuration data plane permissions to read and manage Azure App Configuration data in deployment. This requirement is in addition to baseline management permission requirements of the resource. Azure App Configuration data plane permissions include Microsoft.AppConfiguration/configurationStores/*/read and Microsoft.AppConfiguration/configurationStores/*/write. Built-in roles with this action include:
- App Configuration Data Owner
- App Configuration Data Reader
To learn more about Azure RBAC and Microsoft Entra ID, see Authorize access to Azure App Configuration using Microsoft Entra ID.
Private network access
When an App Configuration resource is restricted to private network access, deployments accessing App Configuration data through public networks will be blocked. To enable successful deployments when access to an App Configuration resource is restricted to private networks the following actions must be taken:
- Azure Resource Management Private Link must be set up
- The App Configuration resource must have Azure Resource Manager authentication mode set to Pass-through
- The App Configuration resource must have Azure Resource Manager private network access enabled
- Deployments accessing App Configuration data must run through the configured Azure Resource Manager private link
If all of these criteria are met, then deployments accessing App Configuration data will be successful.
To enable Azure Resource Manager private network access for an Azure App Configuration resource in the Azure portal, follow these steps:
Navigate to your Azure App Configuration resource in the Azure portal
Locate the Networking setting under Settings
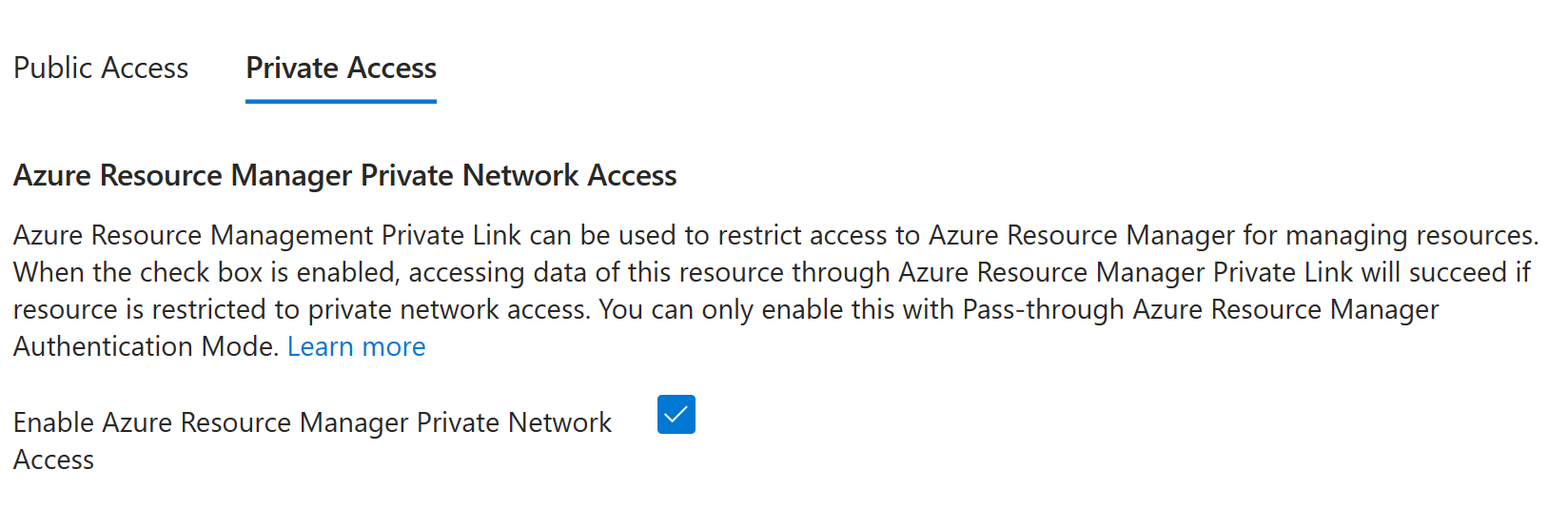
Check Enable Azure Resource Manager Private Access under Private Access
Note
Azure Resource Manager private network access can only be enabled under Pass-through authentication mode.
Next steps
To learn about deployment using ARM template and Bicep, check the documentations linked below.
Povratne informacije
Stiže uskoro: Tijekom 2024. postupno ćemo ukinuti servis Problemi sa servisom GitHub kao mehanizam za povratne informacije za sadržaj i zamijeniti ga novim sustavom za povratne informacije. Dodatne informacije potražite u članku: https://aka.ms/ContentUserFeedback.
Pošaljite i pogledajte povratne informacije za