Delegate Azure role assignment management to others with conditions
As an administrator, you might get several requests to grant access to Azure resources that you want to delegate to someone else. You could assign a user the Owner or User Access Administrator roles, but these are highly privileged roles. This article describes a more secure way to delegate role assignment management to other users in your organization, but add restrictions for those role assignments. For example, you can constrain the roles that can be assigned or constrain the principals the roles can be assigned to.
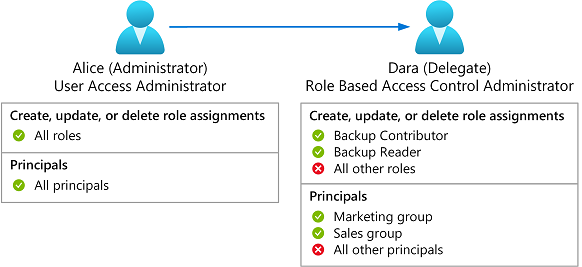
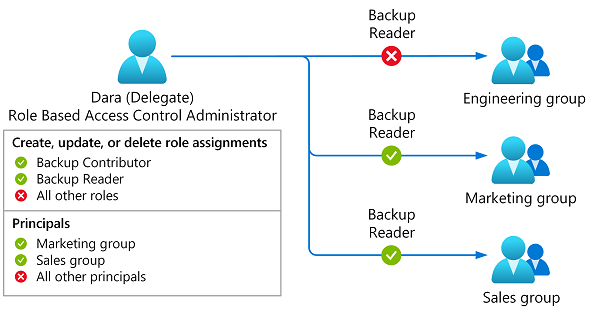
The following diagram shows how a delegate with conditions can only assign the Backup Contributor or Backup Reader roles to only the Marketing or Sales groups.
Prerequisites
To assign Azure roles, you must have:
Microsoft.Authorization/roleAssignments/writepermissions, such as Role Based Access Control Administrator or User Access Administrator
Step 1: Determine the permissions the delegate needs
To help determine the permissions the delegate needs, answer the following questions:
- What roles can the delegate assign?
- What types of principals can the delegate assign roles to?
- Which principals can the delegate assign roles to?
- Can delegate remove any role assignments?
Once you know the permissions that delegate needs, you use the following steps to add a condition to the delegate's role assignment. For example conditions, see Examples to delegate Azure role assignment management with conditions.
Step 2: Start a new role assignment
Sign in to the Azure portal.
Follow the steps to open the Add role assignment page.
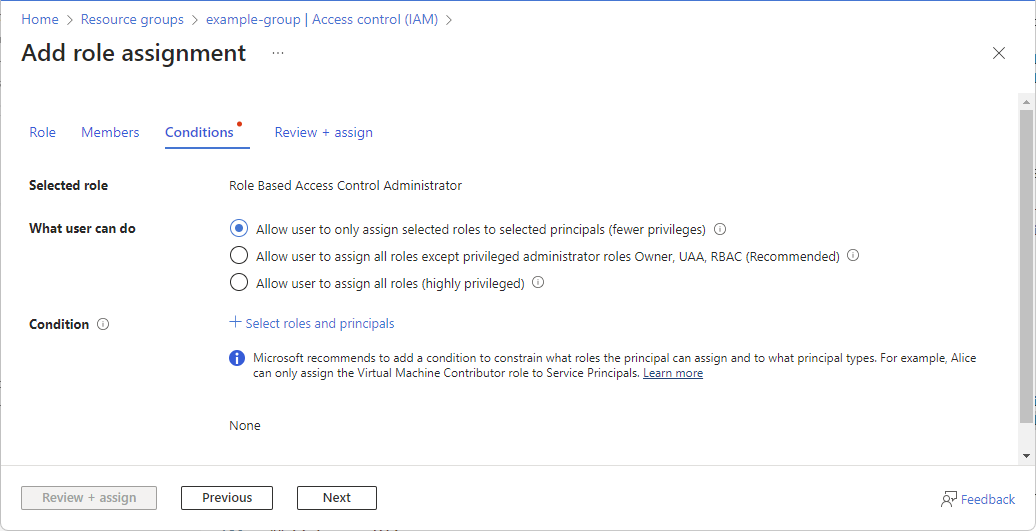
On the Roles tab, select the Privileged administrator roles tab.
Select the Role Based Access Control Administrator role.
The Conditions tab appears.
You can select any role that includes the
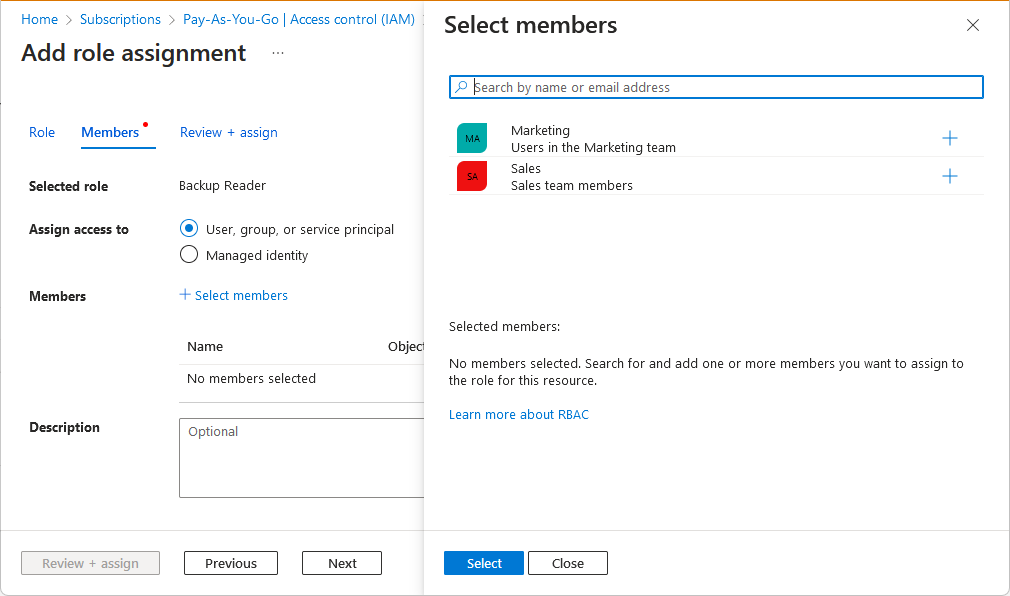
Microsoft.Authorization/roleAssignments/writeorMicrosoft.Authorization/roleAssignments/deleteactions, such as User Access Administrator, but Role Based Access Control Administrator has fewer permissions.On the Members tab, find and select the delegate.
Step 3: Add a condition
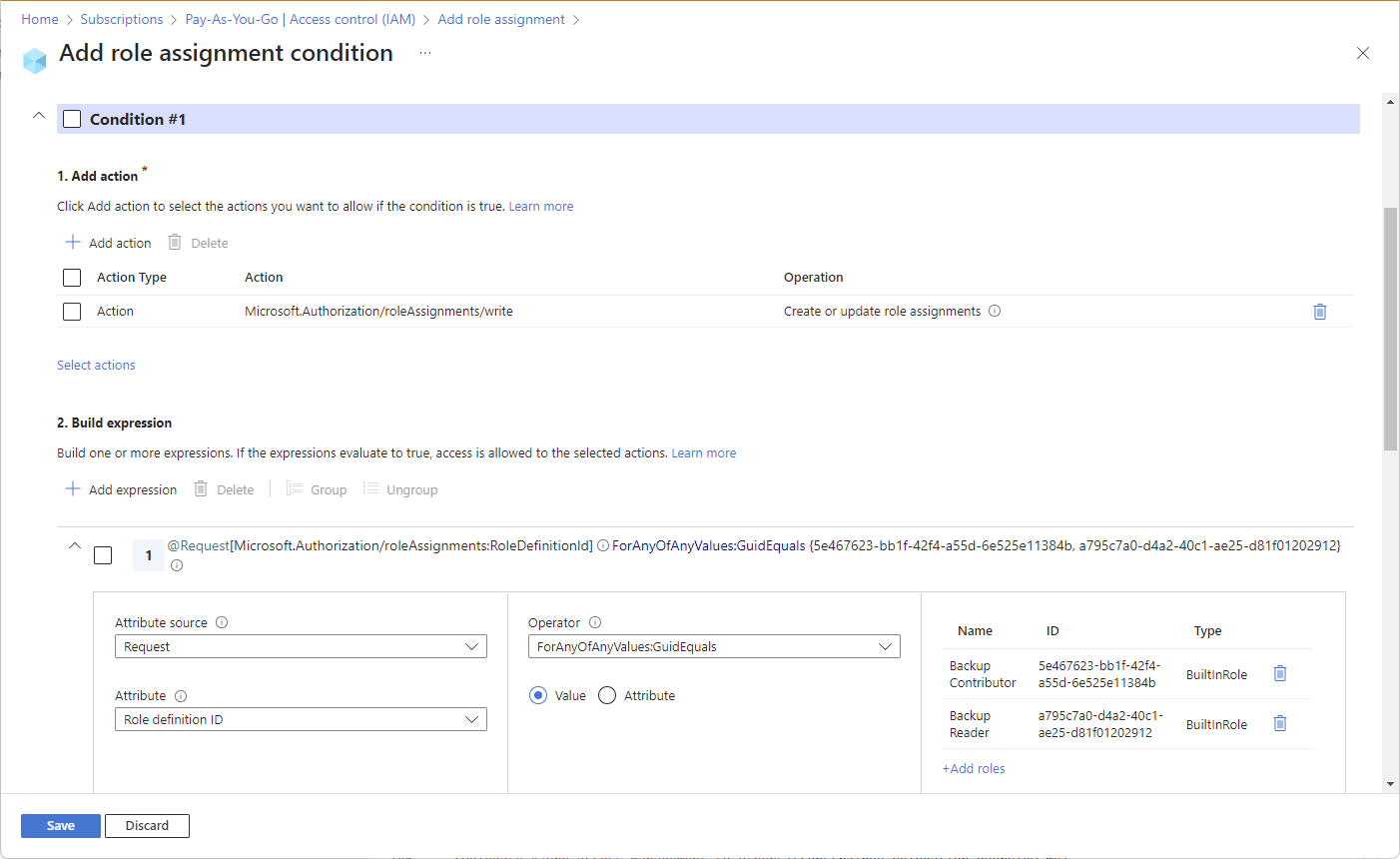
There are two ways that you can add a condition. You can use a condition template or you can use an advanced condition editor.
On the Conditions tab under What user can do, select the Allow user to only assign selected roles to selected principals (fewer privileges) option.
Select Select roles and principals.
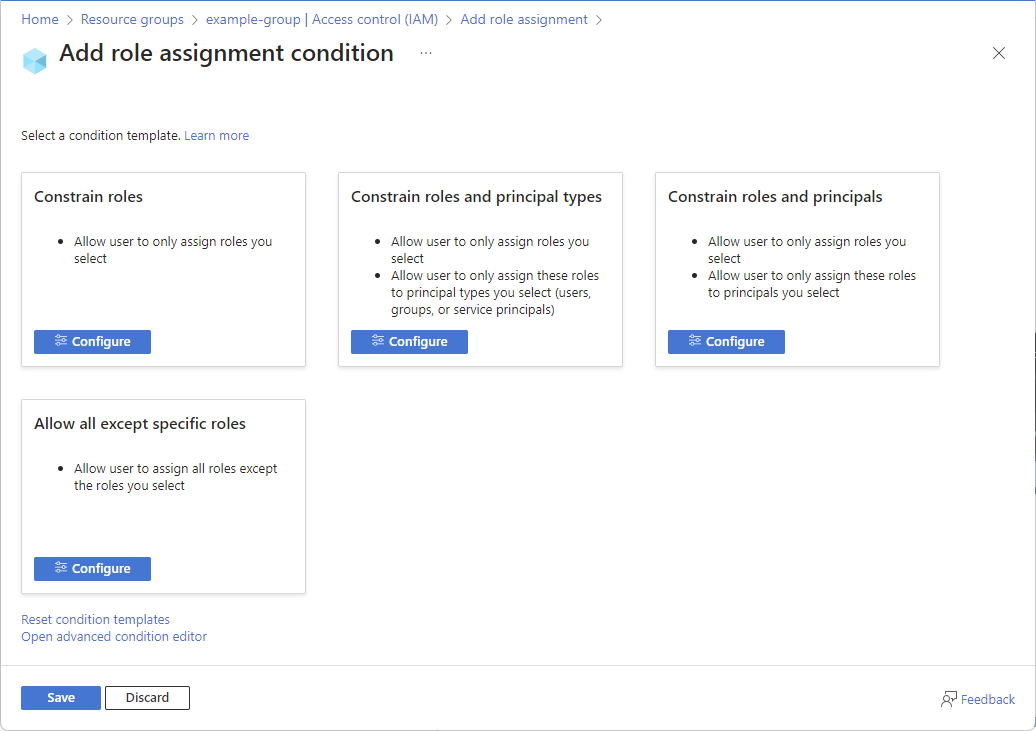
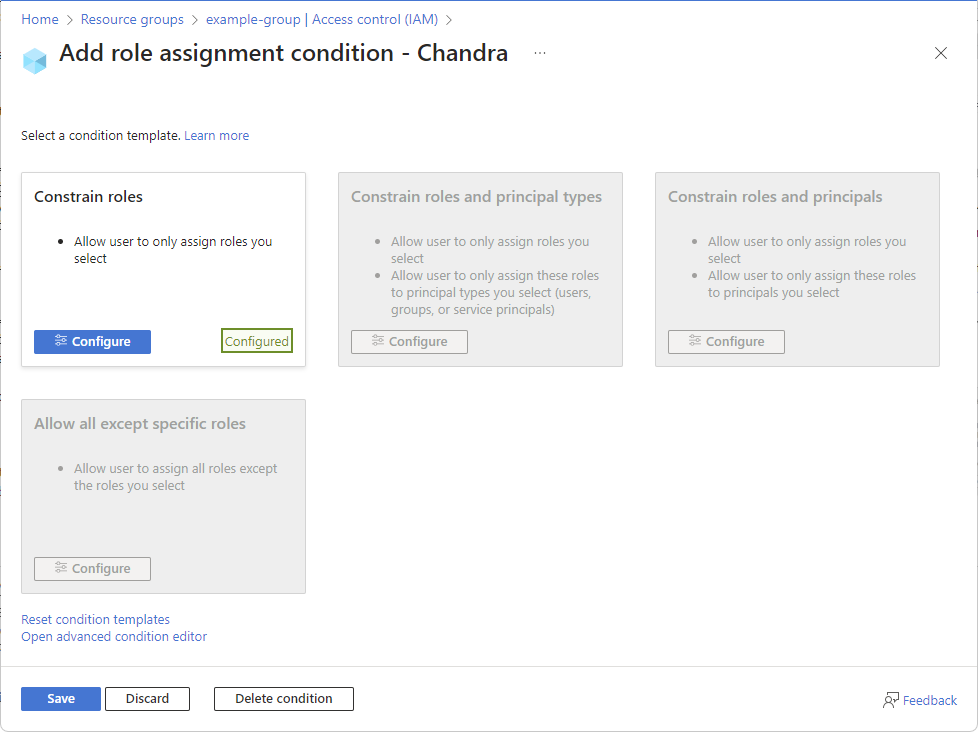
The Add role assignment condition page appears with a list of condition templates.
Select a condition template and then select Configure.
Condition template Select this template to Constrain roles Allow user to only assign roles you select Constrain roles and principal types Allow user to only assign roles you select
Allow user to only assign these roles to principal types you select (users, groups, or service principals)Constrain roles and principals Allow user to only assign roles you select
Allow user to only assign these roles to principals you selectAllow all except specific roles Allow user to assign all roles except the roles you select In the configure pane, add the required configurations.
Select Save to add the condition to the role assignment.
Step 4: Assign role with condition to delegate
On the Review + assign tab, review the role assignment settings.
Select Review + assign to assign the role.
After a few moments, the delegate is assigned the Role Based Access Control Administrator role with your role assignment conditions.
Step 5: Delegate assigns roles with conditions
Delegate can now follow steps to assign roles.
When the delegate tries to assign roles in the Azure portal, the list of roles will be filtered to just show the roles they can assign.
If there is a condition for principals, the list of principals available for assignment are also filtered.
If the delegate attempts to assign a role that is outside the conditions using an API, the role assignment fails with an error. For more information, see Symptom - Unable to assign a role.
Edit a condition
There are two ways that you can edit a condition. You can use the condition template or you can use the condition editor.
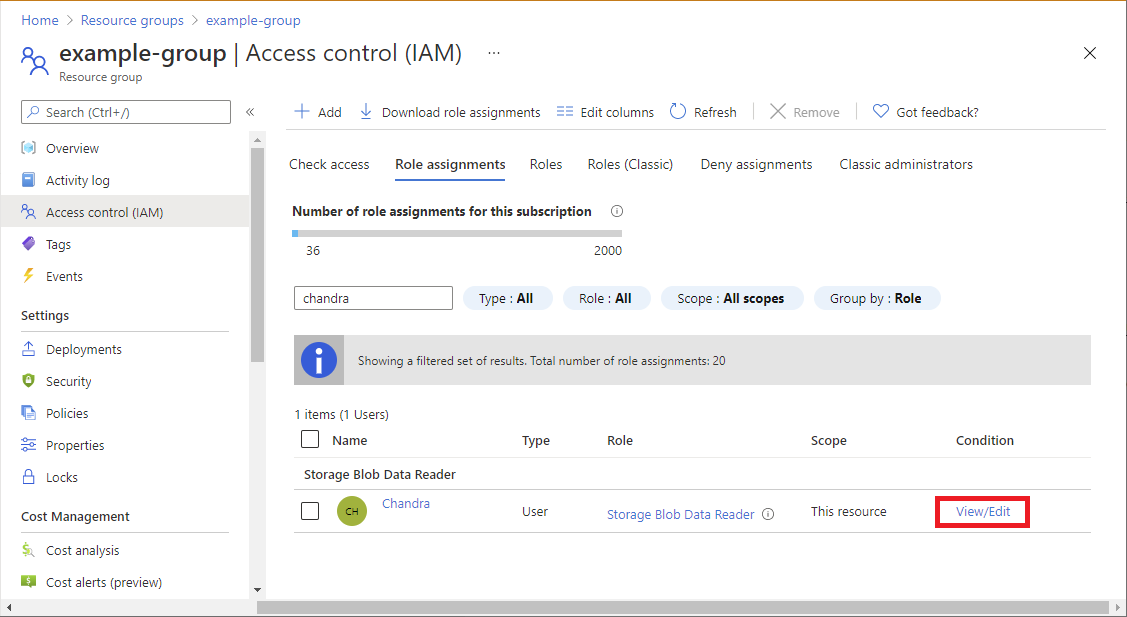
In the Azure portal, open Access control (IAM) page for the role assignment that has a condition that you want to view, edit, or delete.
Select the Role assignments tab and find the role assignment.
In the Condition column, select View/Edit.
If you don't see the View/Edit link, be sure you're looking at the same scope as the role assignment.
The Add role assignment condition page appears. This page will look different depending on whether the condition matches an existing template.
If the condition matches an existing template, select Configure to edit the condition.
If the condition doesn't match an existing template, use the advanced condition editor to edit the condition.
For example, to edit a condition, scroll down to the build expression section and update the attributes, operator, or values.
To edit the condition directly, select the Code editor type and then edit the code for the condition.
When finished, click Save to update the condition.