Događaj
9. tra 15 - 10. tra 12
Programirajte budućnost s umjetnom inteligencijom i povežite se s Java kolegama i stručnjacima na JDConfu 2025.
Registrirajte se odmahOvaj preglednik više nije podržan.
Prijeđite na Microsoft Edge, gdje vas čekaju najnovije značajke, sigurnosna ažuriranja i tehnička podrška.
The objective of this article is to show the steps you need to perform to provision worker data from SuccessFactors Employee Central into Microsoft Entra ID, with optional write-back of email address to SuccessFactors.
Napomena
Use this article if the users you want to provision from SuccessFactors are cloud-only users who don't need an on-premises AD account. If the users require only on-premises AD account or both AD and Microsoft Entra account, then please refer to the article on configure SAP SuccessFactors to Active Directory user provisioning.
The following video provides a quick overview of the steps involved when planning your provisioning integration with SAP SuccessFactors.
The Microsoft Entra user provisioning service integrates with the SuccessFactors Employee Central in order to manage the identity life cycle of users.
The SuccessFactors user provisioning workflows supported by the Microsoft Entra user provisioning service enable automation of the following human resources and identity lifecycle management scenarios:
Hiring new employees - When a new employee is added to SuccessFactors, a user account is automatically created in Microsoft Entra ID and optionally Microsoft 365 and other SaaS applications supported by Microsoft Entra ID, with write-back of the email address to SuccessFactors.
Employee attribute and profile updates - When an employee record is updated in SuccessFactors (such as their name, title, or manager), their user account is automatically updated Microsoft Entra ID and optionally Microsoft 365 and other SaaS applications supported by Microsoft Entra ID.
Employee terminations - When an employee is terminated in SuccessFactors, their user account is automatically disabled in Microsoft Entra ID and optionally Microsoft 365 and other SaaS applications supported by Microsoft Entra ID.
Employee rehires - When an employee is rehired in SuccessFactors, their old account can be automatically reactivated or re-provisioned (depending on your preference) to Microsoft Entra ID and optionally Microsoft 365 and other SaaS applications supported by Microsoft Entra ID.
This SuccessFactors to Microsoft Entra user provisioning solution is ideally suited for:
Organizations that desire a pre-built, cloud-based solution for SuccessFactors user provisioning, including organizations that are populating SuccessFactors from SAP HCM using SAP Integration Suite
Organizations that will be deploying Microsoft Entra for user provisioning with SAP source and target apps, using Microsoft Entra to set up identities for workers so they can sign in to one or more SAP applications, such as SAP ECC or SAP S/4HANA, as well as optionally non-SAP applications
Organizations that require direct user provisioning from SuccessFactors to Microsoft Entra ID but do not require those users to also be in Windows Server Active Directory
Organizations that require users to be provisioned using data obtained from the SuccessFactors Employee Central (EC)
Organizations using Microsoft 365 for email
This section describes the end-to-end user provisioning solution architecture for cloud-only users. There are two related flows:
Authoritative HR Data Flow – from SuccessFactors to Microsoft Entra ID: In this flow worker events (such as New Hires, Transfers, Terminations) first occur in the cloud SuccessFactors Employee Central and then the event data flows into Microsoft Entra ID. Depending on the event, it may lead to create/update/enable/disable operations in Microsoft Entra ID.
Email Writeback Flow – from Microsoft Entra ID to SuccessFactors: Once the account creation is complete in Microsoft Entra ID, the email attribute value or UPN generated in Microsoft Entra ID can be written back to SuccessFactors.
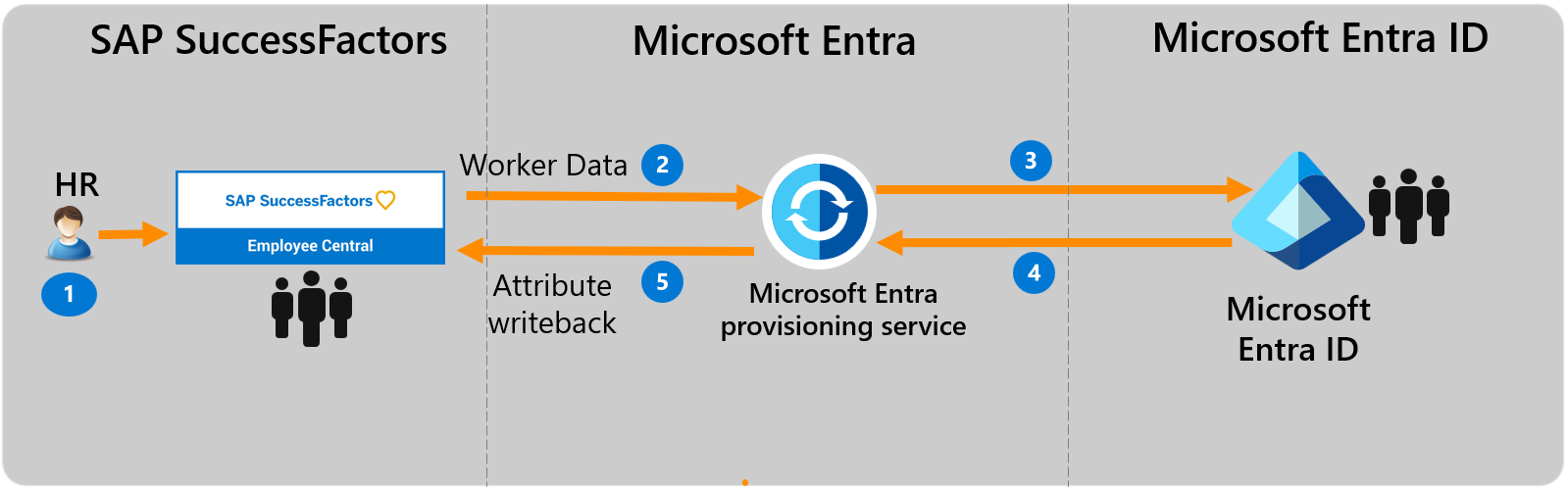
Configuring Cloud HR driven user provisioning from SuccessFactors to Microsoft Entra ID requires considerable planning covering different aspects such as:
Please refer to the cloud HR deployment plan for comprehensive guidelines around these topics. Please refer to the SAP SuccessFactors integration reference to learn about the supported entities, processing details and how to customize the integration for different HR scenarios.
A common requirement of all the SuccessFactors provisioning connectors is that they require credentials of a SuccessFactors account with the right permissions to invoke the SuccessFactors OData APIs. This section describes steps to create the service account in SuccessFactors and grant appropriate permissions.
Work with your SuccessFactors admin team or implementation partner to create or identify a user account in SuccessFactors to invoke the OData APIs. The username and password credentials of this account are required when configuring the provisioning apps in Microsoft Entra ID.
Log in to SAP SuccessFactors with a user account that has access to the Admin Center.
Search for Manage Permission Roles, then select Manage Permission Roles from the search results.
From the Permission Role List, click Create New.
Add a Role Name and Description for the new permission role. The name and description should indicate that the role is for API usage permissions.
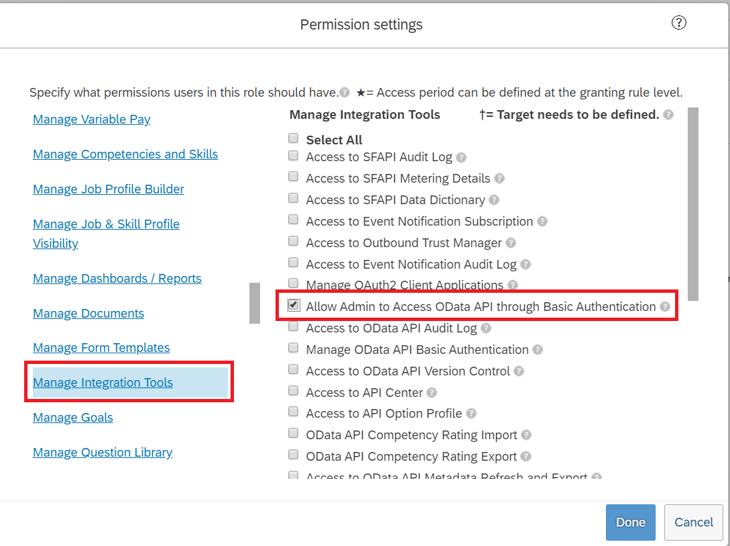
Under Permission settings, click Permission..., then scroll down the permission list and click Manage Integration Tools. Check the box for Allow Admin to Access to OData API through Basic Authentication.
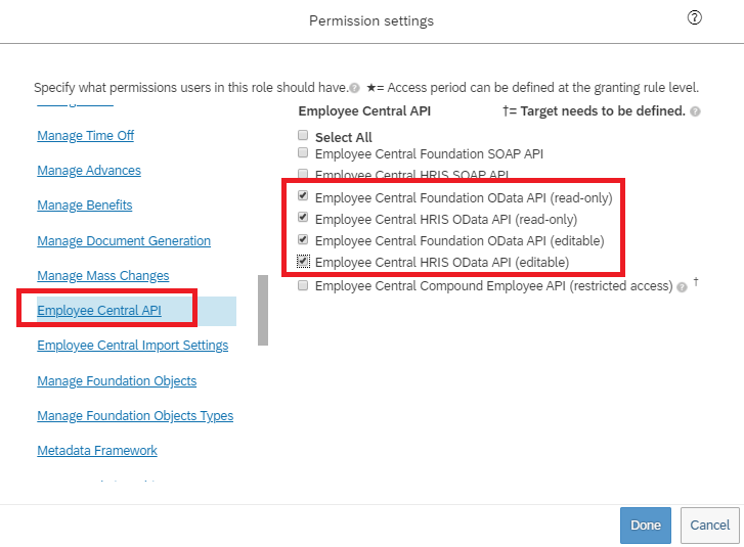
Scroll down in the same box and select Employee Central API. Add permissions as shown below to read using ODATA API and edit using ODATA API. Select the edit option if you plan to use the same account for the Writeback to SuccessFactors scenario.
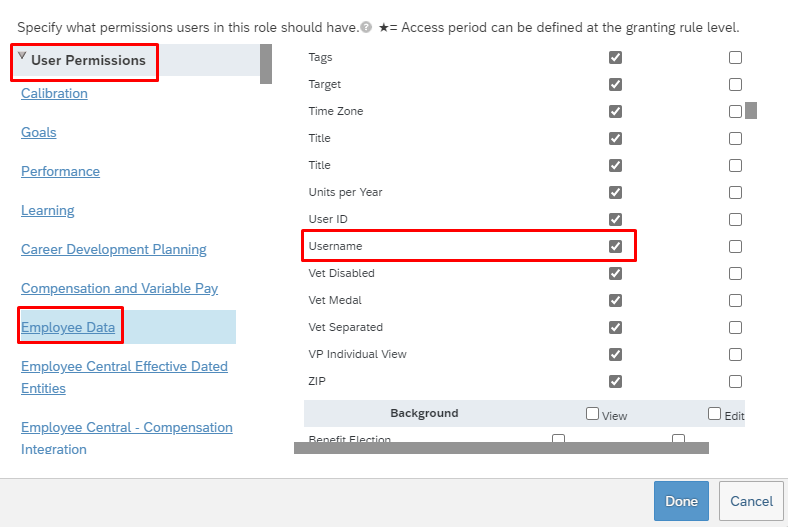
In the same permissions box, go to User Permissions -> Employee Data and review the attributes that the service account can read from the SuccessFactors tenant. For example, to retrieve the Username attribute from SuccessFactors, ensure that "View" permission is granted for this attribute. Similarly review each attribute for view permission.
Napomena
For the complete list of attributes retrieved by this provisioning app, please refer to SuccessFactors Attribute Reference
Click on Done. Click Save Changes.
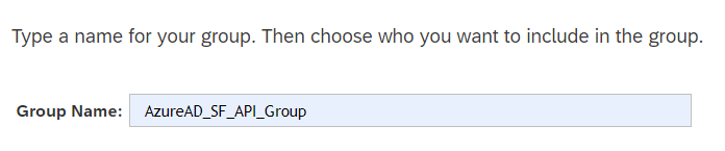
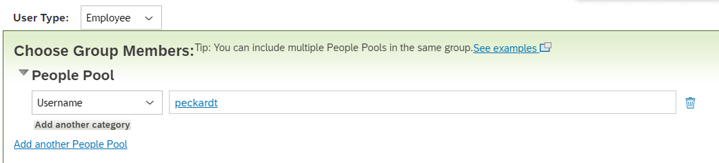
This section provides steps for user account provisioning from SuccessFactors to Microsoft Entra ID.
To configure SuccessFactors to Microsoft Entra provisioning:
Sign in to the Microsoft Entra admin center as at least a Cloud Application Administrator.
Browse to Identity > Applications > Enterprise applications > New application.
Search for SuccessFactors to Microsoft Entra user provisioning, and add that app from the gallery.
After the app is added and the app details screen is shown, select Provisioning
Change the Provisioning Mode to Automatic
Complete the Admin Credentials section as follows:
Admin Username – Enter the username of the SuccessFactors API user account, with the company ID appended. It has the format: username@companyID
Admin password – Enter the password of the SuccessFactors API user account.
Tenant URL – Enter the name of the SuccessFactors OData API services endpoint. Only enter the host name of server without http or https. This value should look like: api-server-name.successfactors.com.
Notification Email – Enter your email address, and check the "send email if failure occurs" checkbox.
Napomena
The Microsoft Entra provisioning service sends email notification if the provisioning job goes into a quarantine state.
Click the Test Connection button. If the connection test succeeds, click the Save button at the top. If it fails, double-check that the SuccessFactors credentials and URL are valid.
Once the credentials are saved successfully, the Mappings section displays the default mapping Synchronize SuccessFactors Users to Microsoft Entra ID
In this section, you'll configure how user data flows from SuccessFactors to Microsoft Entra ID.
On the Provisioning tab under Mappings, click Synchronize SuccessFactors Users to Microsoft Entra ID.
In the Source Object Scope field, you can select which sets of users in SuccessFactors should be in scope for provisioning to Microsoft Entra ID, by defining a set of attribute-based filters. The default scope is "all users in SuccessFactors". Example filters:
Example: Scope to users with personIdExternal between 1000000 and 2000000 (excluding 2000000)
Attribute: personIdExternal
Operator: REGEX Match
Value: (1[0-9][0-9][0-9][0-9][0-9][0-9])
Example: Only employees and not contingent workers
Attribute: EmployeeID
Operator: IS NOT NULL
Savjet
When you are configuring the provisioning app for the first time, you'll need to test and verify your attribute mappings and expressions to make sure that it's giving you the desired result. Microsoft recommends using the scoping filters under Source Object Scope to test your mappings with a few test users from SuccessFactors. Once you've verified that the mappings work, then you can either remove the filter or gradually expand it to include more users.
Oprez
The default behavior of the provisioning engine is to disable/delete users that go out of scope. This may not be desirable in your SuccessFactors to Microsoft Entra integration. To override this default behavior refer to the article Skip deletion of user accounts that go out of scope
In the Target Object Actions field, you can globally filter what actions are performed in Microsoft Entra ID. Create and Update are most common.
In the Attribute mappings section, you can define how individual SuccessFactors attributes map to Microsoft Entra attributes.
Napomena
For the complete list of SuccessFactors attribute supported by the application, please refer to SuccessFactors Attribute Reference
Click on an existing attribute mapping to update it, or click Add new mapping at the bottom of the screen to add new mappings. An individual attribute mapping supports these properties:
Mapping Type
Direct – Writes the value of the SuccessFactors attribute to the Microsoft Entra attribute, with no changes
Constant - Write a static, constant string value to the Microsoft Entra attribute
Expression – Allows you to write a custom value to the Microsoft Entra attribute, based on one or more SuccessFactors attributes. For more info, see this article on expressions.
Source attribute - The user attribute from SuccessFactors
Default value – Optional. If the source attribute has an empty value, the mapping writes this value instead. Most common configuration is to leave this blank.
Target attribute – The user attribute in Microsoft Entra ID.
Match objects using this attribute – Whether or not this mapping should be used to uniquely identify users between SuccessFactors and Microsoft Entra ID. This value is typically set on the Worker ID field for SuccessFactors, which is typically mapped to one of the Employee ID attributes in Microsoft Entra ID.
Matching precedence – Multiple matching attributes can be set. When there are multiple, they are evaluated in the order defined by this field. As soon as a match is found, no further matching attributes are evaluated.
Apply this mapping
Always – Apply this mapping on both user creation and update actions
Only during creation - Apply this mapping only on user creation actions
To save your mappings, click Save at the top of the Attribute-Mapping section.
Once your attribute mapping configuration is complete, you can now enable and launch the user provisioning service.
Once the SuccessFactors provisioning app configurations have been completed, you can turn on the provisioning service.
Savjet
By default when you turn on the provisioning service, it will initiate provisioning operations for all users in scope. If there are errors in the mapping or SuccessFactors data issues, then the provisioning job might fail and go into the quarantine state. To avoid this, as a best practice, we recommend configuring Source Object Scope filter and testing your attribute mappings with a few test users before launching the full sync for all users. Once you have verified that the mappings work and are giving you the desired results, then you can either remove the filter or gradually expand it to include more users.
In the Provisioning tab, set the Provisioning Status to On.
Click Save.
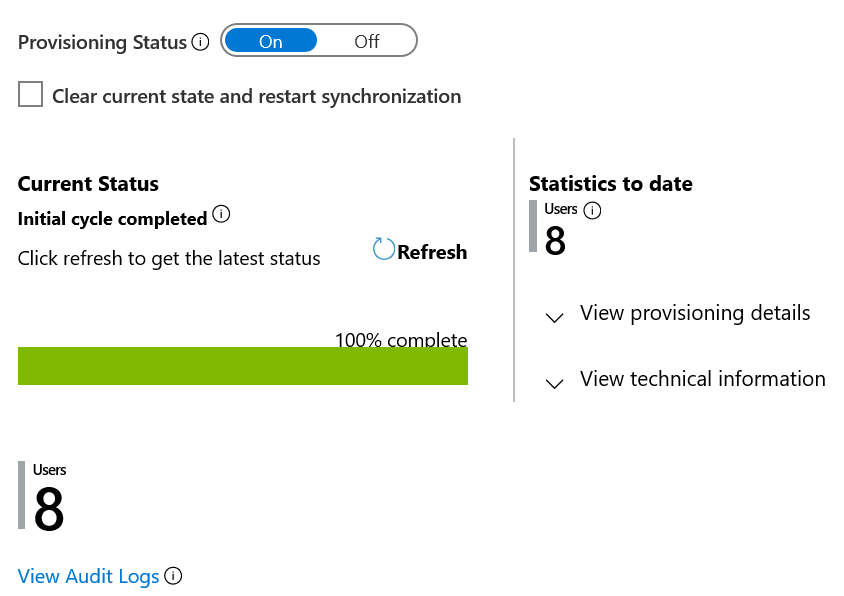
This operation starts the initial sync, which can take a variable number of hours depending on how many users are in the SuccessFactors tenant. You can check the progress bar to the track the progress of the sync cycle.
At any time, check the Provisioning tab in the Entra admin center to see what actions the provisioning service has performed. The provisioning logs lists all individual sync events performed by the provisioning service, such as which users are being read out of SuccessFactors and then subsequently added or updated to Microsoft Entra ID.
Once the initial sync is completed, it writes an audit summary report in the Provisioning tab, as shown below.
Događaj
9. tra 15 - 10. tra 12
Programirajte budućnost s umjetnom inteligencijom i povežite se s Java kolegama i stručnjacima na JDConfu 2025.
Registrirajte se odmahObuka
Modul
Prepare for identity synchronization to Microsoft 365 - Training
This module examines all the planning aspects that must be considered when implementing directory synchronization between on-premises Active Directory and Microsoft Entra ID.
Certifikacija
Microsoft Certified: Azure for SAP Workloads Specialty - Certifications
Muestre la planeación, la migración y el funcionamiento de una solución de SAP en Microsoft Azure mientras aprovecha los recursos de Azure.
Dokumentacija
Obtenga más información sobre cómo configurar la escritura diferida de atributos en SAP SuccessFactors desde Microsoft Entra ID
Aprenda a configurar el aprovisionamiento de entrada de SuccessFactors
Referencia de atributo de SAP SuccessFactors para Microsoft Entra ID - Microsoft Entra ID
Obtenga más información sobre qué atributos de SuccessFactors son compatibles con el aprovisionamiento impulsado por SuccessFactors-HR en Microsoft Entra ID.