KDC_ERR_PREAUTH_REQUIRED vs. KDC_ERR_PREAUTH_FAILED
I often seen network admins look at a network trace and say we have a lot of authentication failures and point to the error – KDC_ERR_PREAUTH_REQUIRED. I have spent time educating on why this is not an authentication failure but instead the default behavior. The KDC (Key Distribution Center) requires all accounts to use pre-authentication. However, pre-authentication can be disabled for individual accounts when necessary for compatibility with other implementations of the protocol.
How to disable pre-authentication?
If the box “Do not require Kerberos pre-authentication” was checked on the user account properties then we would never see the error “KDC_ERR_PREAUTH_REQUIRED” message in a trace.
Let us look at the initial user authentication process using network traces.
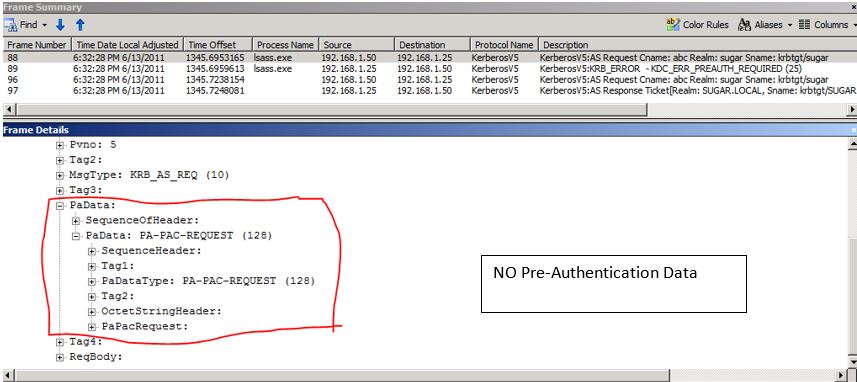
FRAME 1:
The above Frame shows you an AS_Request being sent to the domain controller - 192.168.1.25 from Client machine 192.168.1.25. As you observe there is nothing sent along with PaData.
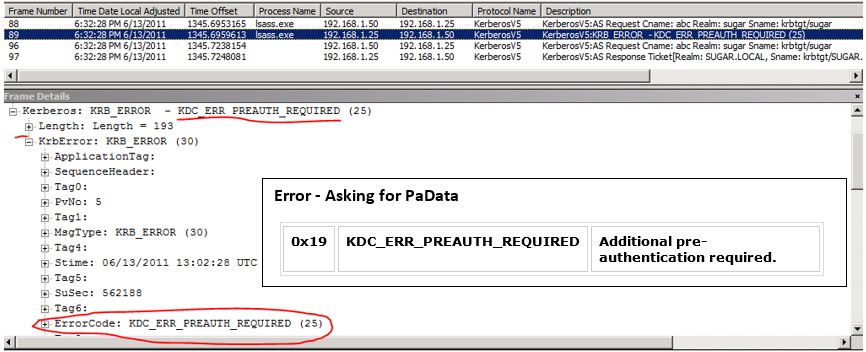
As a result the DC replies with the below error in the below frame – KDC_ERR_PREAUTH_REQUIRED.
FRAME 2:
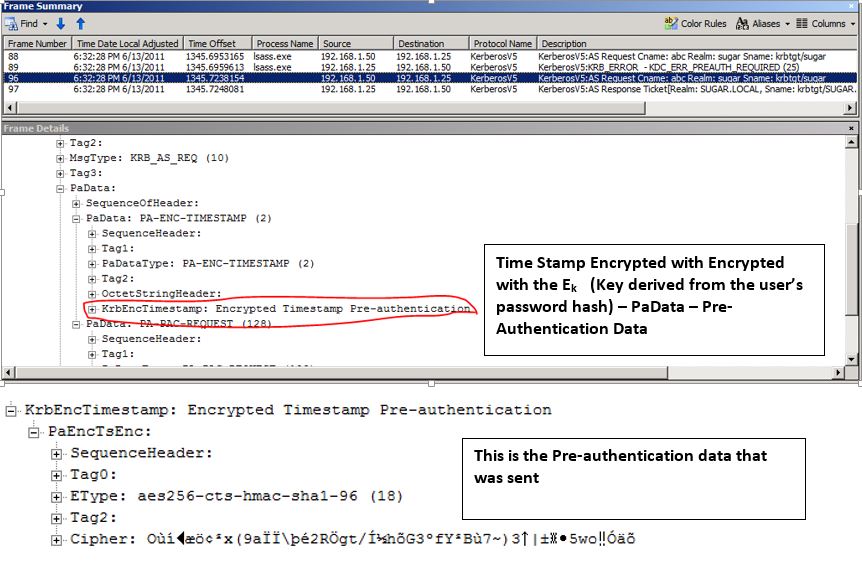
So the client then sends the AS_REQUEST again with the pre-authentication data as show in the below frame. – KrbEncTimestamp: Encrypted Time Stamp Pre-Authentication.
FRAME 3:
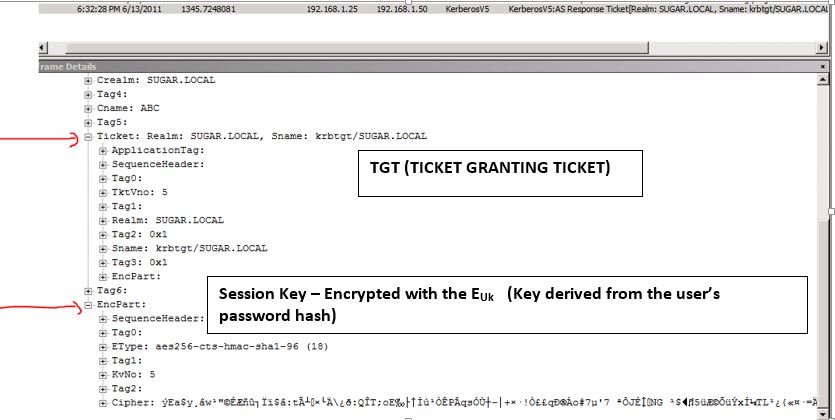
FRAME 4:
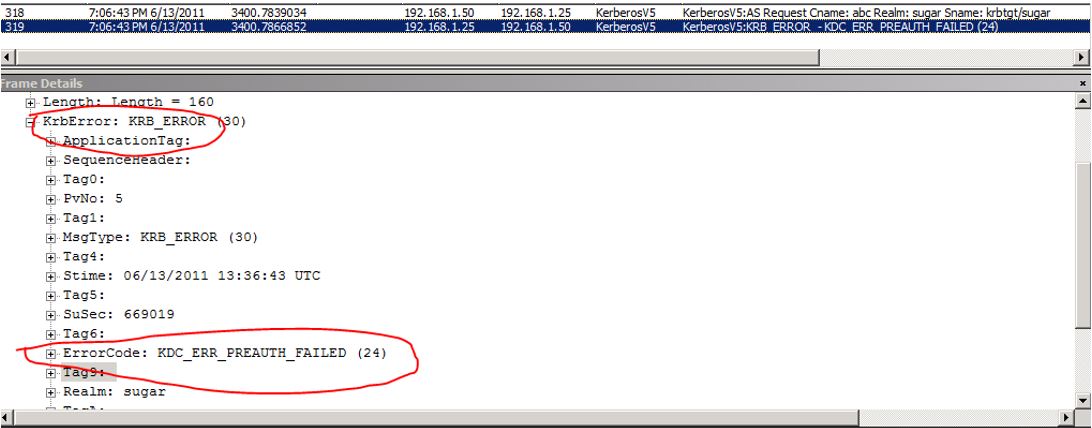
As see above the KDC_ERR_PREAUTH_REQUIRED is not exactly an authentication failure. If the Kerberos authentication fails (for example bad password) then you would see “KDC_ERR_PREAUTH_FAILED” in the trace as shown below.
FRAME 5:
Below is the error you will see in a trace when Authentication fails for the user – Now it’s time you investigate. J
Enable Auditing, and Kerberos logging if required.
I hope its better understood now and there is enough clarity now when you look at network captures that shows KDC_ERR_PREAUTH_REQUIRED & KDC_ERR_PREAUTH_FAILED frames in network traces.
Comments
- Anonymous
January 01, 2003
@Harmandeep - The Frame 1 shows that the client does not send pre-auth data ( KrnEncTimeStamp ) by default and in fram 3 it sends the pre-auth since it receievd pre-auth required from DC ( Frame 2 ). - Anonymous
January 01, 2003
The comment has been removed - Anonymous
March 12, 2014
That makes sense!! Thanks! - Anonymous
January 15, 2015
Thanks for sharing valuable information.
As per FRAME 1, lsass.exe process is AS_REQ with preauth data. How can i set the same i.e. force a client system not to send the preauth data to a discovered d.c. ?- Anonymous
October 25, 2016
By default the client does not send pre-auth data in Frame 1.
- Anonymous
- Anonymous
October 09, 2015
How do you capture these details. Can you tell me the tool to trace the kerberos authentication. - Anonymous
November 15, 2015
Hi Arasuraja -- You could use netmon or Message Analyzer - Anonymous
March 03, 2016
Hello,
great article.
We get the 0x19 KDC_ERR_PREAUTH_REQUIRED Error in a mixed environment (Novell DSFW + WinSrv2xxx - perhaps this is not relevant.
Authentication works and there are no issues. However, if we enable Kerberos logging, after each user-login an Error is produced that shows very weird Client-Times.
a) the time is ok on server and client
b) the times jump around: once it is 1987, then 2031 ...
Do you have any explanation for this?
...
Client Time: 16:18:46.0000 3/2/1976 Z
Server Time: 13:53:18.0000 3/3/2016 Z
Error Code: 0x19 KDC_ERR_PREAUTH_REQUIRED