Decrypting SSL/TLS sessions with Wireshark - Reloaded
Hi there,
In a previous blog post of mine, I went through the steps of decrypting SSL/TLS traffic by using wireshark and openssl tools. In this blog post, I wanted to talk about the same procedure again because it got even easier to decrypt encrypted traffic with Wireshark since then.
Here are the steps to export a certificate with private key included and using that certificate to decrypt SSL/TLS session in Wireshark:
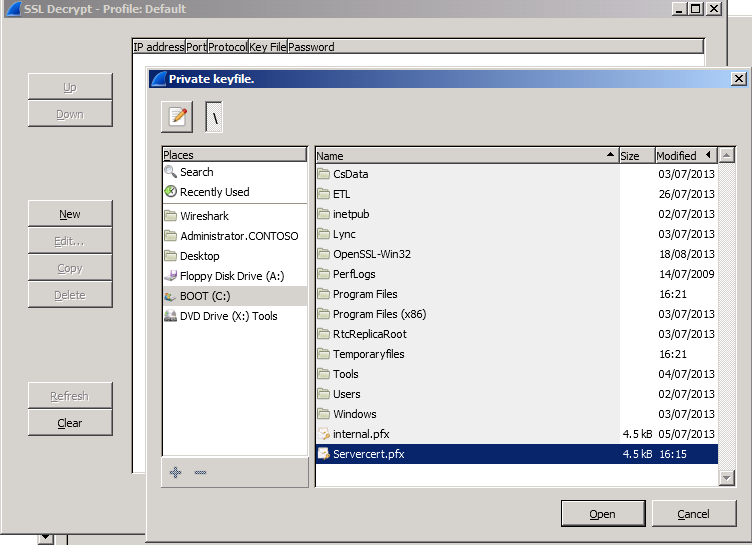
=> Exporting the certificate with its private key:
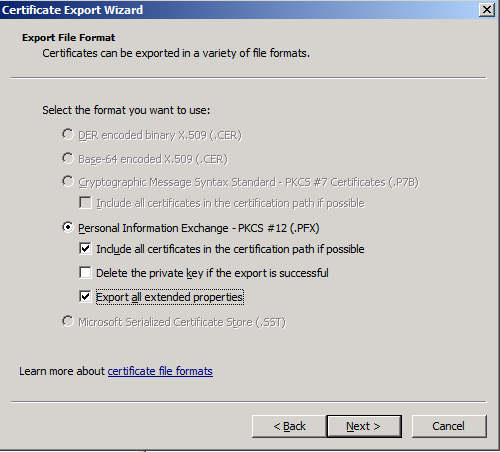
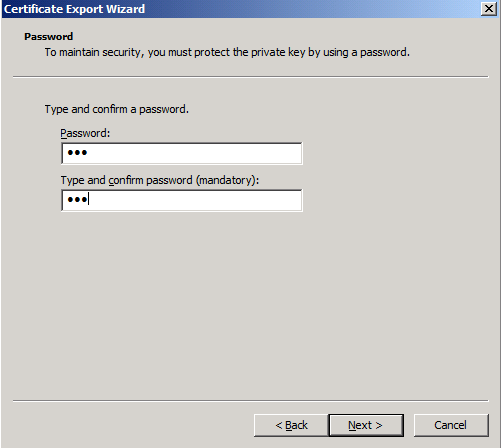
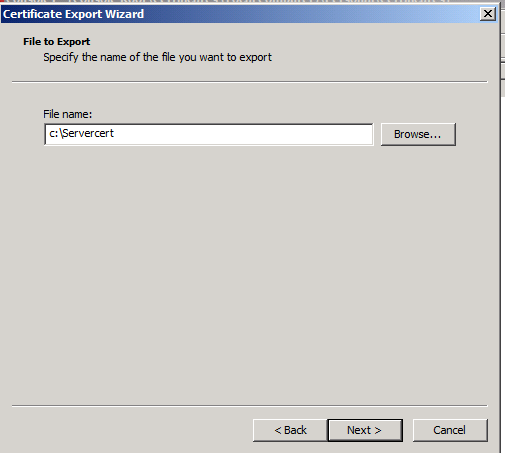
The certificate could be exported by using certificates mmc on Windows:
The exported certificate (with private key included) is c:\servercert.pfx
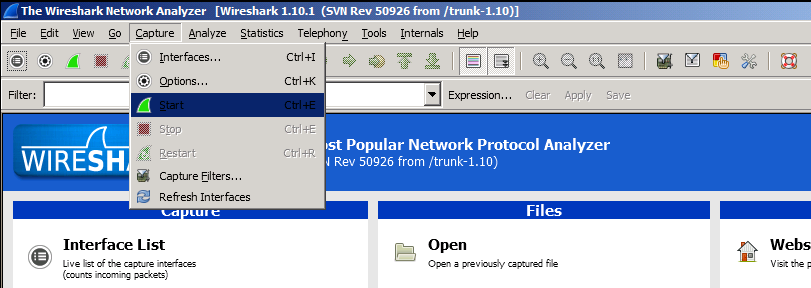
=> Capturing a network trace where an SSL/TLS session is established:
- To start capturing network traffic:
- Reproduce the issue
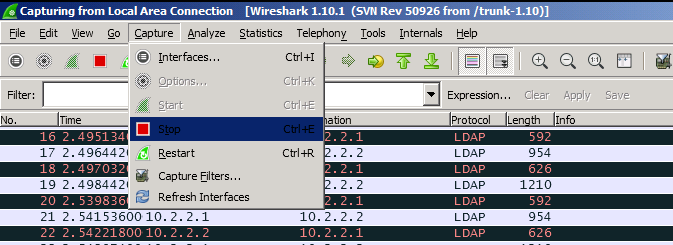
- To stop capturing network traffic:
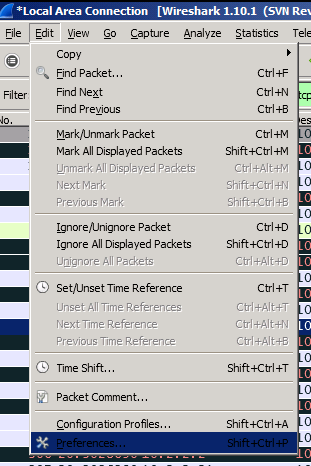
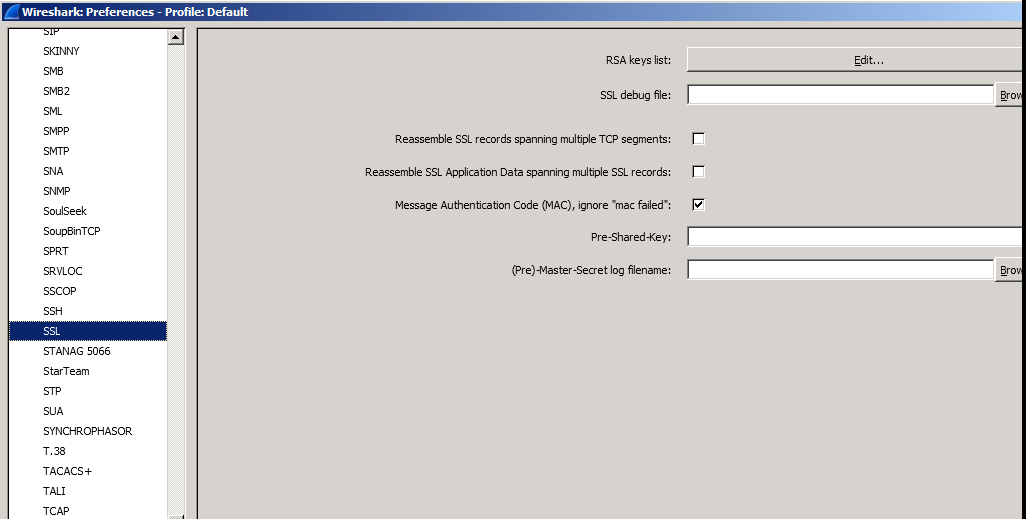
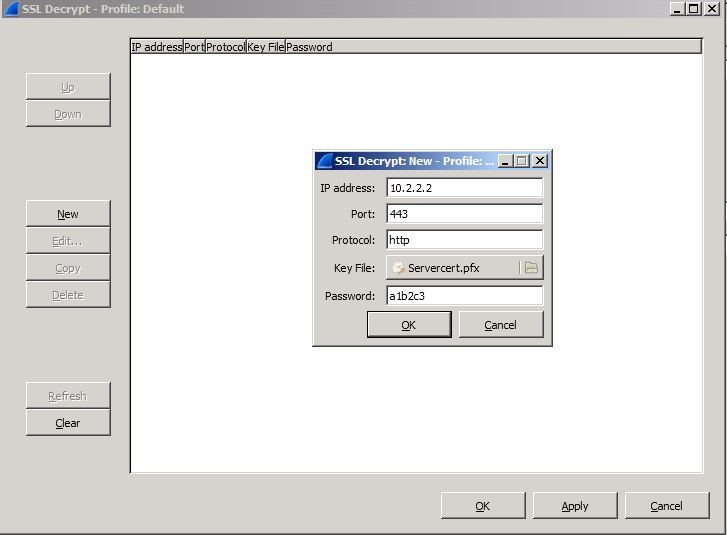
=> Decrypting the SSL/TLS session by using Wireshark and the given certificate with private key:
- In the below example
Server IP is 10.2.2.2 and TCP port is 443.
Note: The password shown below is the one that you assigned while exporting the server certificate:
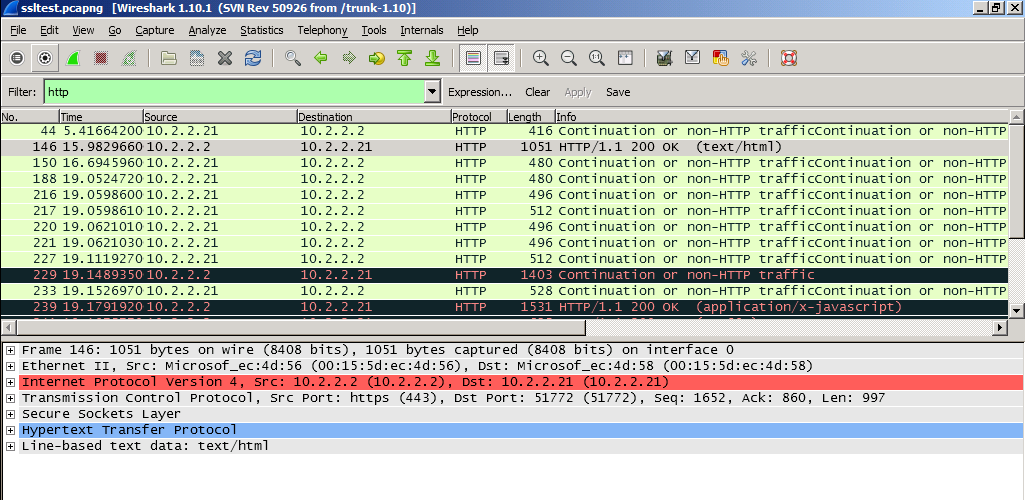
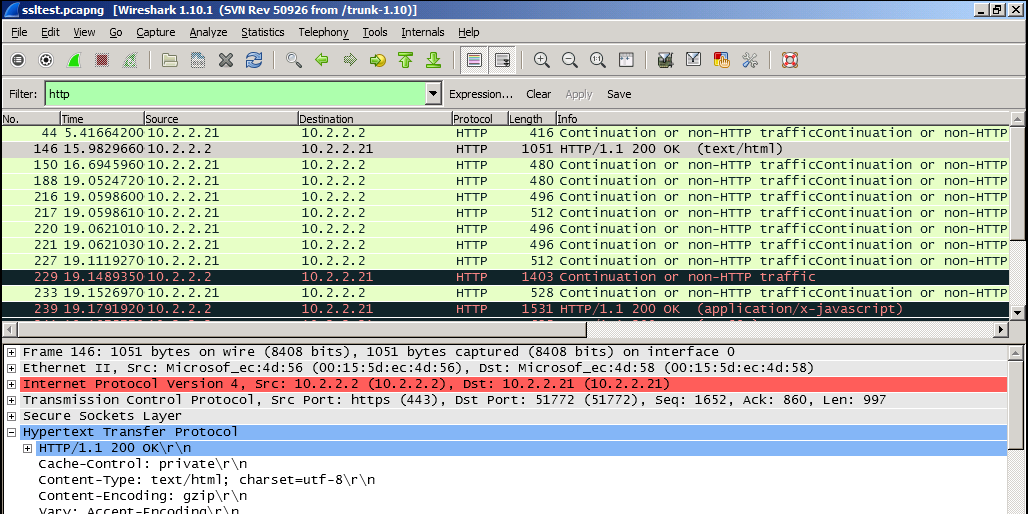
Once the certificate is applied to Wireshark, then an appropriate Wireshark filter (the filter is “http” in this example) could be applied to see the traffic in clear text:
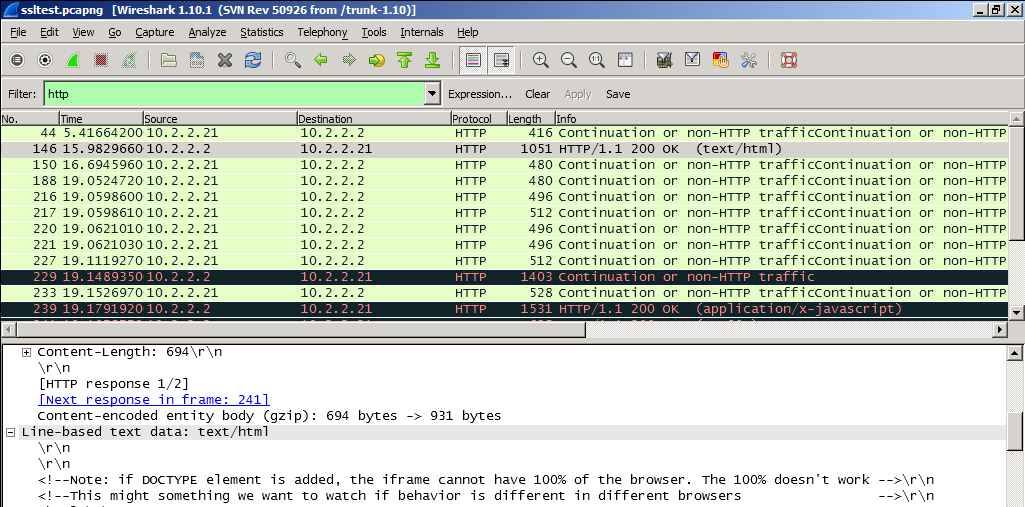
The problem with decrypted SSL/TLS sessions is that you cannot save the network trace in an unencrypted format (best to my knowledge that’s also something Wireshark dev’s to do list) for later analysis or for sharing with someone external to your company, so if you want to save the output in clear text, you might want to print the packets to a text file. But it would also be good to expand all relevant protocol headers before doing so so that the text file will include all application layer protocol header lines expanded. You can see an example below for HTTP protocol:
We expand “Hypertext Transfer Protocol” and “Line-based text data: text/html” lines:
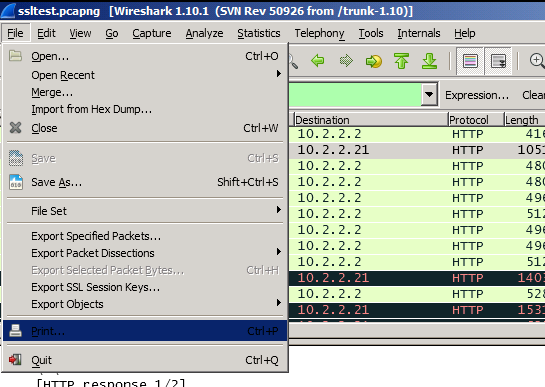
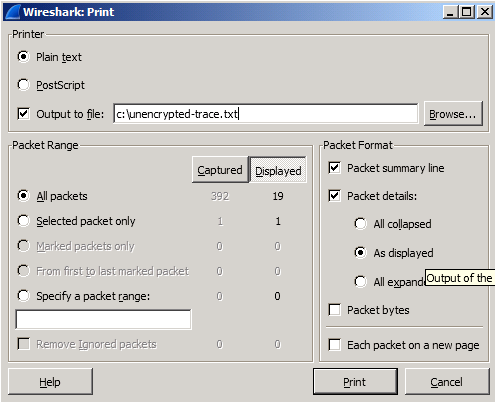
Now we can print the packets to a text file as given below:
with the following options set:
Now the output will be written to a text file where the HTTP request/response header+payloads will be visible in clear test:
Hope this helps
Thanks,
Murat
Comments
- Anonymous
December 30, 2013
I collaborated with a colleague recently where the IE client was failing to authenticate to IIS and I - Anonymous
December 30, 2013
Pingback from Blog Post: How it works on the wire: IIS HTTP Client certificate authentication | klinews.com - Anonymous
December 30, 2013
Pingback from Blog Post: How it works on the wire: IIS HTTP Client certificate authentication | klinews.com - Anonymous
December 30, 2013
Pingback from Blog Post: How it works on the wire: IIS HTTP Client certificate authentication | klinews.com - Anonymous
May 16, 2014
Pingback from Decrypting SSL/TLS sessions with Wireshark – Reloaded – nettracer – Site Home – TechNet Blogs | Log - Anonymous
August 01, 2014
sv - Anonymous
September 22, 2014
Nice piece of work Murat.
I am trying to look into LDAP Communications, but am having trouble getting the packets decrypted - all I get is "Application Data" with "Encrypted Application Data" under the SSL portion of the packet.
No Clear text here :-(
I have tried specifying the port as "636" or "start_tls" under the RSA-keys list in Wireshark.
The trace is captured from the server side of communications.
I have also verified that the Client Key Exhange is part of my trace - and I am using the private key of the server (exported as per your instructions).
Any idea what I am doing wrong?
Any and all help appreciated :-) - Anonymous
October 15, 2014
Thank you Skjalg
Possibly the LDAP payloads are also encrypted (with NTLM/Kerberos session key negotiated at the initial authentication phase) inside the SSL/TLS channel so even if you decrypt the SSL/TLS session, you will still not be able to see the LDAP payloads. TO be able to see LDAP payloads unecnrypted, you may want to give the following post a try:
http://blogs.msdn.com/b/spatdsg/archive/2008/08/12/ldap-client-tracing.aspx
Hope this helps
Thanks,
Murat - Anonymous
June 01, 2015
Hi Murat,
I applied your solution in my lab, but SSL stays encrypted. It shows as TLSv1.2 in WireShark. I see Client Hello, Server Hello , but data is encrypted.
I log file I see this:
decrypt_ssl3_record: using client decoder
decrypt_ssl3_record: no decoder available
Any ideas?
Thanks,
Alex - Anonymous
August 20, 2015
Hi Alexander,
Most likely you're failing to decrypt because Ephemeral DHE key exchange is negotiated between the client and the server. Best to my knowledge it's only possible to decrypt SSL/TLS sessions when key exchange protocol is RSA (and hence the client and server uses the same pre-master secret). You can find below more details about this issue:
http://security.stackexchange.com/questions/35639/decrypting-tls-in-wireshark-when-using-dhe-rsa-ciphersuites
Also you can see which key exchange protocol was negotiated at the Server Hello message coming back from the server.
Thanks,
Murat - Anonymous
January 13, 2016
HI Murat, it's been long time :)
now in same case of TLS1.2 i have read your reply above so is there any other possibility or mar be another way that can decrypt all SSL traffic? by the way i have tried the message analyzer but i'm also getting error "cipher suite is unsupported" and it was "TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA" so decryption fails also!