Configure encryption with sensitivity labels
In tightening data security, the global consulting firm uses Microsoft Purview Information Protection to implement encryption with sensitivity labels. This is an important step in safeguarding sensitive information. This approach allows them to:
- Restrict content access to authorized staff, ensuring that sensitive information remains encrypted, regardless of its location or how it's shared.
- Balance security with collaboration by designating editing rights and controlling access to meetings and documents in a remote work environment.
Administrators have the flexibility to assign permissions now for immediate enforcement or let users assign permissions, adapting protections to suit different data sensitivity levels.
Understand encryption with sensitivity labels
Sensitivity labels rely on the Azure Rights Management service (Azure RMS) from Azure Information Protection to encrypt documents, emails, and meeting invites. This service uses encryption, identity, and authorization policies.
The super user feature within Azure RMS allows authorized users and services to access and manage your organization's encrypted data consistently. This feature includes being able to change or delete encryption when needed.
Sensitivity labels also encrypt audio and video streams in Teams meetings, using a different encryption method than Azure RMS. This type is specially designed for the unique needs of Teams meetings.
Prerequisites
Before configuring encryption, ensure:
- Azure Information Protection is activated.
- Your network, including firewalls, is configured properly.
- Microsoft Entra settings support encrypted content access.
- Exchange is set up for Azure Information Protection, enhancing email and meeting invite encryption.
Configuring a label for encryption
Start by creating or editing a sensitivity label. Make sure to select Items as the scope for the label:
On the Choose protection settings for labeled items page, select Apply or remove encryption. This choice determines how the labels interact with encryption.
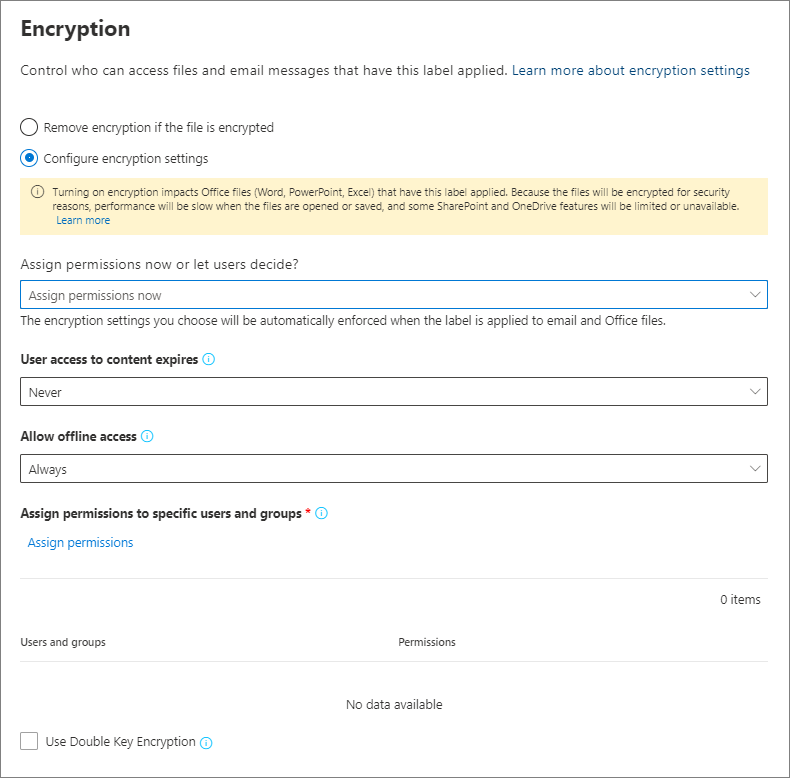
On the Encryption page, select one of these options:
Remove encryption if the file or email is encrypted: Use this option to remove existing encryption from a file or email when applying the label. Note: Users might be unable to apply this label if they don’t have permission to remove existing encryption.
Configure encryption settings: Turns on encryption and makes the encryption settings visible.
Configure encryption settings
When creating or editing a sensitivity label, you have two main options in the Encryption page:
- Assign permissions now: Specify the user permissions for the labeled content in advance. Useful for highly sensitive content that requires strict access control.
- Let users assign permissions: Gives users flexibility to set permissions when applying labels, useful for collaborative environments.
Consider the global consulting firm launching a confidential project, named Client X Initiative - Confidential. By choosing to Assign permissions now for documents related to this initiative, the firm ensures only the project team can edit them, effectively preventing unauthorized access while preserving the project's confidentiality.
Assign permissions now
With this option, you can set up access controls for labeled content in advance, such as choosing when they expire and controlling offline access. You can:
Use the following options to control who can access email, meeting invites (if enabled), or documents to which this label is applied. You can:
Allow access to labeled content to expire, either on a specific date or after a specific number of days after the label is applied. After this time, users won't be able to open the labeled item. If you specify a date, it's effective midnight on that date in your current time zone. Some email clients might not enforce expiration and show emails past their expiration date, due to their caching mechanisms.
Allow offline access never, always, or for a specific number of days after the label is applied. Use this setting to balance any security requirements you have with the ability for users to open encrypted content when they don't have an internet connection. If you restrict offline access to never or to a specific number of days a threshold is established. Once that threshold is reached, users must be reauthenticated, and their access is logged.
Settings for access control for encrypted content:
You can grant permissions to specific people so that only they can interact with the labeled content. To do this:
- Add users or groups who need access to the labeled content.
- Choose their permission levels, from viewing only to full editing rights.
Options range from general categories like Everyone in your organization or specific users or groups. When choosing Any authenticated users, keep in mind its wider access effects.
Updating encryption settings on labels
When updating a label's encryption settings:
- Changes to Assign permissions now directly affect how newly labeled or relabeled content is encrypted. Existing content's encryption updates upon user reauthentication.
- Switching a label's configuration, like from Do Not Forward to Encrypt-Only, applies only to content labeled after the change. This action ensures your encryption aligns with current security policies without redoing existing labels.
Consider, as the consulting firm wraps up a high-profile project for a major client, it decides to adjust the sensitivity label settings to reflect the project's completion. The firm chooses to modify the label to limit document access to read-only for most team members, ensuring the project's findings remain secure and unaltered. This decision affects all previously labeled documents related to the project, demonstrating the firm's ability to dynamically manage document permissions in response to evolving project requirements and security considerations.
Knowledge check
Select the best response to the question, then select Check your answers.