Office 365 Groups are glorious creations. There are, however, some instances where they don't work as you anticipate (or hope). One of those scenarios is when you are configured in hybrid coexistence with the following scenario:
- Office 365 Group Writeback is enabled (for configuring permissions, see this script)
- RequireSenderAuthenticationEnabled is set to False for an Office 365 group
- Your organization's MX record is configured to point on-premises
In this scenario, external emails sent to Office 365 groups (via your organization's MX record pointing on-premises) will be returned with an NDR with the following error text: "You do not have permission to send to this recipient." This happens because the RequireSenderAuthentication attribute (which maps to msExchRequireAuthToSendTo) written to the synced group object is set to the constant True inside of AAD Connect (as shown in the rule "Out to AD - Group SOAInAAD"): 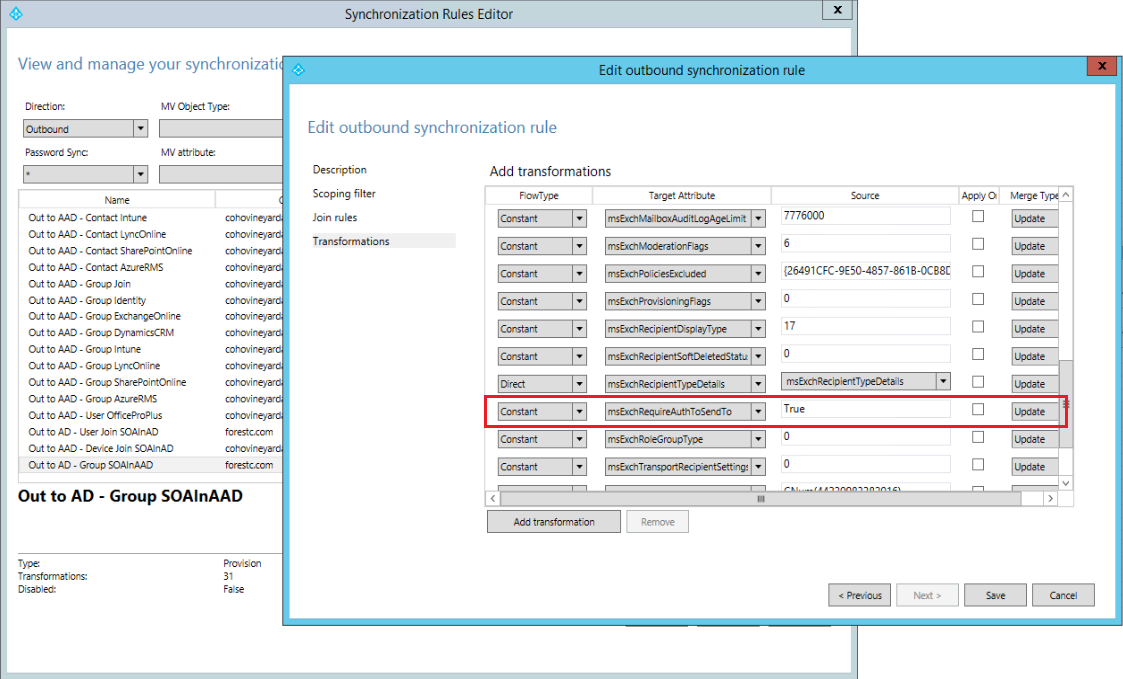 Which translates to this on written-back group objects:
Which translates to this on written-back group objects: 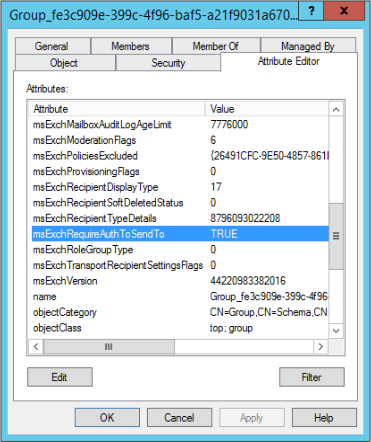 In order to fix this, you need to either update the rule (Edit | Disable and Make a Copy) or update the msExchRequireAuthToSendTo attribute on the synced group objects if you are keeping your MX pointed on-premises, or update the MX to point to Office 365. If you choose to edit the rule, you'll be configuring all Office 365 groups to be open to the public. If that's not something you want, then you can make a copy of the rule and give it a higher priority, and add an attribute scoping filter. That way, you can set an attribute on Office 365 groups that you want to be open and only modify those.
In order to fix this, you need to either update the rule (Edit | Disable and Make a Copy) or update the msExchRequireAuthToSendTo attribute on the synced group objects if you are keeping your MX pointed on-premises, or update the MX to point to Office 365. If you choose to edit the rule, you'll be configuring all Office 365 groups to be open to the public. If that's not something you want, then you can make a copy of the rule and give it a higher priority, and add an attribute scoping filter. That way, you can set an attribute on Office 365 groups that you want to be open and only modify those.
Comments
- Anonymous
December 02, 2017
thanks - Anonymous
February 02, 2018
Thanks for posting this. Please do be sure to report this design bug to the AAD Connect team. This isn't even listed on the "Notes during the preview" section on the documentation.- Anonymous
February 03, 2018
Unfortunately, this falls into the "known." The PM changed late last year, so maybe we can get some traction on it.
- Anonymous
- Anonymous
February 03, 2018
The AAD Connecty team does not own the functionality of the Office Groups writeback, this is owned by the Office Groups team. I have forwarded this conversation to them.- Anonymous
February 04, 2018
Excellent. I had originally forwarded one of our internal conversations to Chun, and we reference this workaround in the Office 365 Administration Inside Out book. Any way that we can get traction is a good one. :-)
- Anonymous
- Anonymous
February 11, 2018
Thank you for guidance - Anonymous
August 06, 2018
Aaron, do you have any update or solution on getting Azure AD Connect to sync attribute msExchRequireAuthToSendTo changes to on-premise AD? I'm looking for ways to automate from Azure AD Connect as we pointed the MX to on-premise SMTP gateway in which msExchRequireAuthToSendTo value on-premise AD takes precedence over O365 Group RequireSenderAuthenticationEnabled value. I'm hoping the latest version of Azure AD Connect would address this requirement.- Anonymous
August 09, 2018
I'm working on a solution for this for another customer. I should have it up in a few days. :-)
- Anonymous