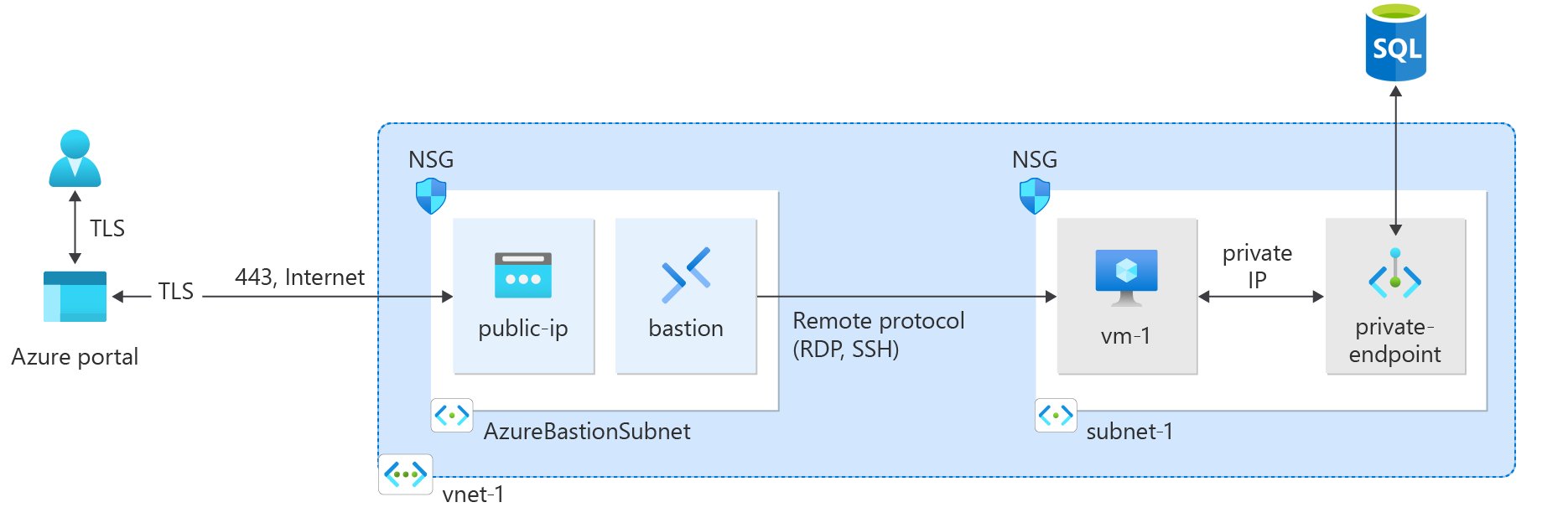
このクイック スタートでは、Terraform を使用してプライベート エンドポイントを作成します。 プライベート エンドポイントは、Azure SQL Database に接続します。 プライベート エンドポイントは、仮想ネットワークとプライベート ドメイン ネーム システム (DNS) ゾーンに関連付けられています。 プライベート DNS ゾーンは、プライベート エンドポイントの IP アドレスを解決します。 仮想ネットワークには、SQL Database のインスタンスへのプライベート エンドポイントの接続をテストするために使用する仮想マシンが含まれています。
このスクリプトでは、SQL サーバーのランダム なパスワードと、仮想マシンのランダムな SSH キーが生成されます。 作成されたリソースの名前は、スクリプトの実行時に出力されます。
Terraform を使用すると、クラウド インフラストラクチャの定義、プレビュー、デプロイが可能になります。 Terraform を使用して、 HCL 構文を使用して構成ファイルを作成します。 HCL 構文を使用すると、クラウド プロバイダー (Azure など) とクラウド インフラストラクチャを構成する要素を指定できます。 構成ファイルを作成したら、インフラストラクチャの変更をデプロイする前にプレビューできる 実行プラン を作成します。 変更を確認したら、実行プランを適用してインフラストラクチャをデプロイします。
[前提条件]
アクティブなサブスクリプションを含む Azure アカウントが必要です。 アカウントを無料で作成します。
Terraform コードを実装する
注
この記事のサンプル コードは、 Azure Terraform GitHub リポジトリにあります。
Terraform を使用して Azure リソースを管理する方法を示すその他の記事とサンプル コードを参照してください
サンプルの Terraform コードをテストして実行するディレクトリを作成し、それを現在のディレクトリにします。
main.tfという名前のファイルを作成し、次のコードを挿入します。resource "random_pet" "prefix" { prefix = var.resource_group_name_prefix length = 1 } # Resource Group resource "azurerm_resource_group" "rg" { location = var.resource_group_location name = "${random_pet.prefix.id}-rg" } # Virtual Network resource "azurerm_virtual_network" "my_terraform_network" { name = "${random_pet.prefix.id}-vnet" address_space = ["10.0.0.0/16"] location = azurerm_resource_group.rg.location resource_group_name = azurerm_resource_group.rg.name } # Subnet 1 resource "azurerm_subnet" "my_terraform_subnet_1" { name = "subnet-1" resource_group_name = azurerm_resource_group.rg.name virtual_network_name = azurerm_virtual_network.my_terraform_network.name address_prefixes = ["10.0.0.0/24"] } # Public IP address for NAT gateway resource "azurerm_public_ip" "my_public_ip" { name = "public-ip-nat" location = azurerm_resource_group.rg.location resource_group_name = azurerm_resource_group.rg.name allocation_method = "Static" sku = "Standard" } # NAT Gateway resource "azurerm_nat_gateway" "my_nat_gateway" { name = "nat-gateway" location = azurerm_resource_group.rg.location resource_group_name = azurerm_resource_group.rg.name } # Associate NAT Gateway with Public IP resource "azurerm_nat_gateway_public_ip_association" "example" { nat_gateway_id = azurerm_nat_gateway.my_nat_gateway.id public_ip_address_id = azurerm_public_ip.my_public_ip.id } # Associate NAT Gateway with Subnet resource "azurerm_subnet_nat_gateway_association" "example" { subnet_id = azurerm_subnet.my_terraform_subnet_1.id nat_gateway_id = azurerm_nat_gateway.my_nat_gateway.id } # Create public IP for virtual machine resource "azurerm_public_ip" "my_public_ip_vm" { name = "public-ip-vm" location = azurerm_resource_group.rg.location resource_group_name = azurerm_resource_group.rg.name allocation_method = "Static" sku = "Standard" } # Create Network Security Group and rule resource "azurerm_network_security_group" "my_terraform_nsg" { name = "nsg-1" location = azurerm_resource_group.rg.location resource_group_name = azurerm_resource_group.rg.name security_rule { name = "SSH" priority = 1001 direction = "Inbound" access = "Allow" protocol = "Tcp" source_port_range = "*" destination_port_range = "22" source_address_prefix = "*" destination_address_prefix = "*" } } # Create network interface resource "azurerm_network_interface" "my_terraform_nic" { name = "nic-1" location = azurerm_resource_group.rg.location resource_group_name = azurerm_resource_group.rg.name ip_configuration { name = "my_nic_configuration" subnet_id = azurerm_subnet.my_terraform_subnet_1.id private_ip_address_allocation = "Dynamic" public_ip_address_id = azurerm_public_ip.my_public_ip_vm.id } } # Connect the security group to the network interface resource "azurerm_network_interface_security_group_association" "example" { network_interface_id = azurerm_network_interface.my_terraform_nic.id network_security_group_id = azurerm_network_security_group.my_terraform_nsg.id } # Generate random text for a unique storage account name resource "random_id" "random_id" { keepers = { # Generate a new ID only when a new resource group is defined resource_group = azurerm_resource_group.rg.name } byte_length = 8 } # Create storage account for boot diagnostics resource "azurerm_storage_account" "my_storage_account" { name = "diag${random_id.random_id.hex}" location = azurerm_resource_group.rg.location resource_group_name = azurerm_resource_group.rg.name account_tier = "Standard" account_replication_type = "LRS" } # Create virtual machine resource "azurerm_linux_virtual_machine" "my_terraform_vm" { name = "vm-1" location = azurerm_resource_group.rg.location resource_group_name = azurerm_resource_group.rg.name network_interface_ids = [azurerm_network_interface.my_terraform_nic.id] size = "Standard_DS1_v2" os_disk { name = "myOsDisk" caching = "ReadWrite" storage_account_type = "Premium_LRS" } source_image_reference { publisher = "Canonical" offer = "0001-com-ubuntu-server-jammy" sku = "22_04-lts-gen2" version = "latest" } computer_name = "hostname" admin_username = var.username admin_ssh_key { username = var.username public_key = azapi_resource_action.ssh_public_key_gen.output.publicKey } boot_diagnostics { storage_account_uri = azurerm_storage_account.my_storage_account.primary_blob_endpoint } } # Create SQL server name resource "random_pet" "azurerm_mssql_server_name" { prefix = "sql" } # Random password for SQL server resource "random_password" "admin_password" { count = var.admin_password == null ? 1 : 0 length = 20 special = true min_numeric = 1 min_upper = 1 min_lower = 1 min_special = 1 } locals { admin_password = try(random_password.admin_password[0].result, var.admin_password) } # Create SQL server resource "azurerm_mssql_server" "server" { name = random_pet.azurerm_mssql_server_name.id resource_group_name = azurerm_resource_group.rg.name location = azurerm_resource_group.rg.location administrator_login = var.admin_username administrator_login_password = local.admin_password version = "12.0" } # Create SQL database resource "azurerm_mssql_database" "db" { name = var.sql_db_name server_id = azurerm_mssql_server.server.id } # Create private endpoint for SQL server resource "azurerm_private_endpoint" "my_terraform_endpoint" { name = "private-endpoint-sql" location = azurerm_resource_group.rg.location resource_group_name = azurerm_resource_group.rg.name subnet_id = azurerm_subnet.my_terraform_subnet_1.id private_service_connection { name = "private-serviceconnection" private_connection_resource_id = azurerm_mssql_server.server.id subresource_names = ["sqlServer"] is_manual_connection = false } private_dns_zone_group { name = "dns-zone-group" private_dns_zone_ids = [azurerm_private_dns_zone.my_terraform_dns_zone.id] } } # Create private DNS zone resource "azurerm_private_dns_zone" "my_terraform_dns_zone" { name = "privatelink.database.windows.net" resource_group_name = azurerm_resource_group.rg.name } # Create virtual network link resource "azurerm_private_dns_zone_virtual_network_link" "my_terraform_vnet_link" { name = "vnet-link" resource_group_name = azurerm_resource_group.rg.name private_dns_zone_name = azurerm_private_dns_zone.my_terraform_dns_zone.name virtual_network_id = azurerm_virtual_network.my_terraform_network.id }outputs.tfという名前のファイルを作成し、次のコードを挿入します。output "resource_group_name" { description = "The name of the created resource group." value = azurerm_resource_group.rg.name } output "virtual_network_name" { description = "The name of the created virtual network." value = azurerm_virtual_network.my_terraform_network.name } output "subnet_name_1" { description = "The name of the created subnet 1." value = azurerm_subnet.my_terraform_subnet_1.name } output "nat_gateway_name" { description = "The name of the created NAT gateway." value = azurerm_nat_gateway.my_nat_gateway.name } output "sql_server_name" { value = azurerm_mssql_server.server.name } output "admin_password" { sensitive = true value = local.admin_password }provider.tfという名前のファイルを作成し、次のコードを挿入します。terraform { required_providers { azapi = { source = "azure/azapi" version = "~>1.5" } azurerm = { source = "hashicorp/azurerm" version = "~>3.0" } random = { source = "hashicorp/random" version = "~>3.0" } } } provider "azurerm" { features { resource_group { prevent_deletion_if_contains_resources = false } } }ssh.tfという名前のファイルを作成し、次のコードを挿入します。resource "random_pet" "ssh_key_name" { prefix = "ssh" separator = "" } resource "azapi_resource_action" "ssh_public_key_gen" { type = "Microsoft.Compute/sshPublicKeys@2022-11-01" resource_id = azapi_resource.ssh_public_key.id action = "generateKeyPair" method = "POST" response_export_values = ["publicKey", "privateKey"] } resource "azapi_resource" "ssh_public_key" { type = "Microsoft.Compute/sshPublicKeys@2022-11-01" name = random_pet.ssh_key_name.id location = azurerm_resource_group.rg.location parent_id = azurerm_resource_group.rg.id } output "key_data" { value = azapi_resource_action.ssh_public_key_gen.output.publicKey }variables.tfという名前のファイルを作成し、次のコードを挿入します。variable "resource_group_location" { type = string default = "eastus" description = "Location of the resource group." } variable "resource_group_name_prefix" { type = string default = "rg" description = "Prefix of the resource group name that's combined with a random ID so name is unique in your Azure subscription." } variable "username" { type = string description = "The username for the local account that will be created on the new VM." default = "azureuser" } variable "sql_db_name" { type = string description = "The name of the SQL Database." default = "SampleDB" } variable "admin_username" { type = string description = "The administrator username of the SQL logical server." default = "azureadmin" } variable "admin_password" { type = string description = "The administrator password of the SQL logical server." sensitive = true default = null }
Terraform を初期化する
terraform init
terraform init -upgrade
重要なポイント:
-
-upgradeパラメーターは、必要なプロバイダー プラグインを、構成のバージョン制約に準拠する最新バージョンにアップグレードします。
Terraform実行計画を作成する
terraform プランを実行して実行プランを作成します。
terraform plan -out main.tfplan
重要なポイント:
-
terraform planコマンドは実行プランを作成しますが、実行はしません。 代わりに、それは設定ファイルで指定された設定を作成するために必要な手順を決定します。 このパターンを使用すると、実際のリソースに変更を加える前に、実行プランが期待と一致するかどうかを確認できます。 - 任意の
-outパラメーターを使用すると、プランの出力ファイルを指定することができます。-outパラメーターを使用すると、レビューしたプランがそのまま適用されることが保証されます。
Terraform 実行プランを適用する
terraform apply を実行して、実行プランをクラウド インフラストラクチャに適用します。
terraform apply main.tfplan
重要なポイント:
-
terraform applyコマンドの例では、以前にterraform plan -out main.tfplanを実行していることを前提としています。 -
-outパラメーターに別のファイル名を指定した場合は、terraform applyへの呼び出しで同じファイル名を使用してください。 -
-outパラメーターを使用しなかった場合は、パラメーターを指定せずにterraform applyを呼び出します。
結果を確認してください。
Azure リソース グループ名を取得します。
resource_group_name=$(terraform output -raw resource_group_name)SQL Server 名を取得します。
sql_server=$(terraform output -raw sql_server)az sql server show を実行して、SQL Server プライベート エンドポイントに関する詳細を表示します。
az sql server show \ --resource-group $resource_group_name \ --name $sql_server --query privateEndpointConnections \ --output tsv
リソースをクリーンアップする
Terraform を使用して作成されたリソースが不要になったら、次の手順を実行します。
terraform プランを実行し、
destroyフラグを指定します。terraform plan -destroy -out main.destroy.tfplan重要なポイント:
-
terraform planコマンドは実行プランを作成しますが、実行はしません。 代わりに、それは設定ファイルで指定された設定を作成するために必要な手順を決定します。 このパターンを使用すると、実際のリソースに変更を加える前に、実行プランが期待と一致するかどうかを確認できます。 - 任意の
-outパラメーターを使用すると、プランの出力ファイルを指定することができます。-outパラメーターを使用すると、レビューしたプランがそのまま適用されることが保証されます。
-
terraform apply を実行して実行プランを適用します。
terraform apply main.destroy.tfplan
Azure での Terraform のトラブルシューティング
Azure で Terraform を使用する場合の一般的な問題のトラブルシューティングを行います。