Microsoft Defender XDR での自動攻撃の中断
適用対象:
- Microsoft Defender XDR
Microsoft Defender XDR は、何百万もの個々のシグナルを関連付け、環境内のアクティブなランサムウェア キャンペーンやその他の高度な攻撃を高い信頼性で特定します。 攻撃の進行中、Defender XDR は、自動攻撃の中断によって攻撃者が使用している侵害された資産を自動的に含めることで、攻撃を中断します。
自動攻撃の中断は、早い段階で横移動を制限し、関連するコストから生産性の低下まで、攻撃の全体的な影響を軽減します。 同時に、セキュリティ運用チームは、資産の調査、修復、およびオンラインへの復帰を完全に制御できます。
この記事では、自動攻撃の中断の概要について説明し、次の手順やその他のリソースへのリンクを示します。
自動攻撃の中断のしくみ
自動攻撃の中断は、進行中の攻撃を含め、組織の資産への影響を制限し、セキュリティ チームが攻撃を完全に修復するための時間を増やすように設計されています。 攻撃の中断では、広範な拡張検出と応答 (XDR) 信号が使用され、攻撃全体を考慮してインシデント レベルで動作します。 この機能は、侵害の 1 つのインジケーターに基づく防止やブロックなどの既知の保護方法とは異なります。
多くの XDR とセキュリティ オーケストレーション、自動化、応答 (SOAR) プラットフォームでは自動応答アクションを作成できますが、自動攻撃の中断は組み込まれており、Microsoft セキュリティ研究者や高度な AI モデルからの分析情報を使用して高度な攻撃の複雑さを打ち消します。 自動攻撃の中断は、侵害された資産を特定するために、さまざまなソースからのシグナルのコンテキスト全体を考慮します。
自動攻撃の中断は、次の 3 つの重要な段階で動作します。
- Defender XDR の機能を使用して、エンドポイント、ID、電子メールとコラボレーション ツール、SaaS アプリからの分析情報を通じて、さまざまなソースからの信号を単一の信頼度の高いインシデントに関連付けます。
- 攻撃者によって制御され、攻撃の拡散に使用される資産を識別します。
- 影響を受ける資産を分離することで、関連する Microsoft Defender 製品間で応答アクションが自動的に実行され、攻撃がリアルタイムで含まれます。
このゲーム変更機能は、脅威アクターの早い段階での進行状況を制限し、関連するコストから生産性の損失まで、攻撃の全体的な影響を劇的に軽減します。
自動アクションを実行する際の高い信頼度の確立
自動アクションを実行すると、組織に与える可能性のある影響を考えると、セキュリティ チームからためらいが生じることがあることを理解しています。 そのため、Defender XDR の自動攻撃中断機能は、忠実度の高い信号に依存するように設計されています。 また、電子メール、ID、アプリケーション、ドキュメント、デバイス、ネットワーク、およびファイル全体で何百万もの Defender 製品シグナルと Defender XDR のインシデント相関関係を使用します。 Microsoft のセキュリティ調査チームによる何千ものインシデントの継続的な調査からの分析情報により、自動攻撃の中断によって高い信号対雑音比 (SNR) が維持されます。
調査は、高品質で正確な保護を確保するために、信号と攻撃の脅威の状況を監視するために不可欠です。
ヒント
この記事では、攻撃の中断のしくみについて説明します。 これらの機能を構成するには、「Microsoft Defender XDR で 攻撃中断機能を構成する 」を参照してください。
自動応答アクション
自動攻撃中断では、Microsoft ベースの XDR 応答アクションが使用されます。 これらのアクションの例を次に示します。
デバイスに含まれる - Microsoft Defender for Endpoint の機能に基づいて、このアクションは、疑わしいデバイスの自動包含であり、そのデバイスとの送受信通信をブロックします。
ユーザーを無効にする - Microsoft Defender for Identity の機能に基づいて、このアクションは、横移動、悪意のあるメールボックスの使用、マルウェアの実行などの追加の損害を防ぐために、侵害されたアカウントの自動中断です。
ユーザーを含める - Microsoft Defender for Endpoint の機能に基づいて、この応答アクションには疑わしい ID が一時的に含まれるので、Defender for Endpoint のオンボード デバイスとの受信通信に関連する横移動とリモート暗号化をブロックするのに役立ちます。
詳細については、「Microsoft Defender XDR での 修復アクション 」を参照してください。
Microsoft Sentinel を使用した SAP の自動応答アクション
統合セキュリティ運用プラットフォームを使用していて、SAP アプリケーション用の Microsoft Sentinel ソリューションをデプロイした場合は、SAP の自動攻撃中断をデプロイすることもできます。
たとえば、財務プロセス操作攻撃の場合に疑わしい SAP ユーザーをロックすることで、侵害された資産を含む SAP の攻撃中断をデプロイします。
リスクを軽減した後、Microsoft Defender 管理者は、攻撃中断応答によって自動的にロックされていたユーザーのロックを手動で解除できます。 ユーザーを手動でロック解除する機能は、Microsoft Defender アクション センターから使用でき、攻撃の中断によってロックされたユーザーに対してのみ使用できます。
SAP に対して攻撃の中断を使用するには、新しいデータ コネクタ エージェントをデプロイするか、エージェントでバージョン 90847355以降が使用されていることを確認してから、必要な Azure ロールと SAP ロールを割り当てて適用します。 詳細については、以下を参照してください:
- SAP データ コネクタ エージェントをホストするコンテナーをデプロイして構成する
- Microsoft Sentinel の SAP データ コネクタ エージェントを更新します。特に 、自動攻撃の中断のためにシステムを更新します。
Azure portal と SAP システムで攻撃の中断を構成する一方で、自動攻撃中断自体は Microsoft Defender ポータルの統合セキュリティ運用プラットフォームにのみ表示されます。
環境内で攻撃の中断が発生したタイミングを特定する
Defender XDR インシデント ページには、攻撃ストーリーを介した自動攻撃中断アクションと、黄色のバーで示される状態が反映されます (図 1)。 インシデントには、専用の中断タグが表示され、インシデント グラフに含まれる資産の状態が強調表示され、アクション センターにアクションが追加されます。
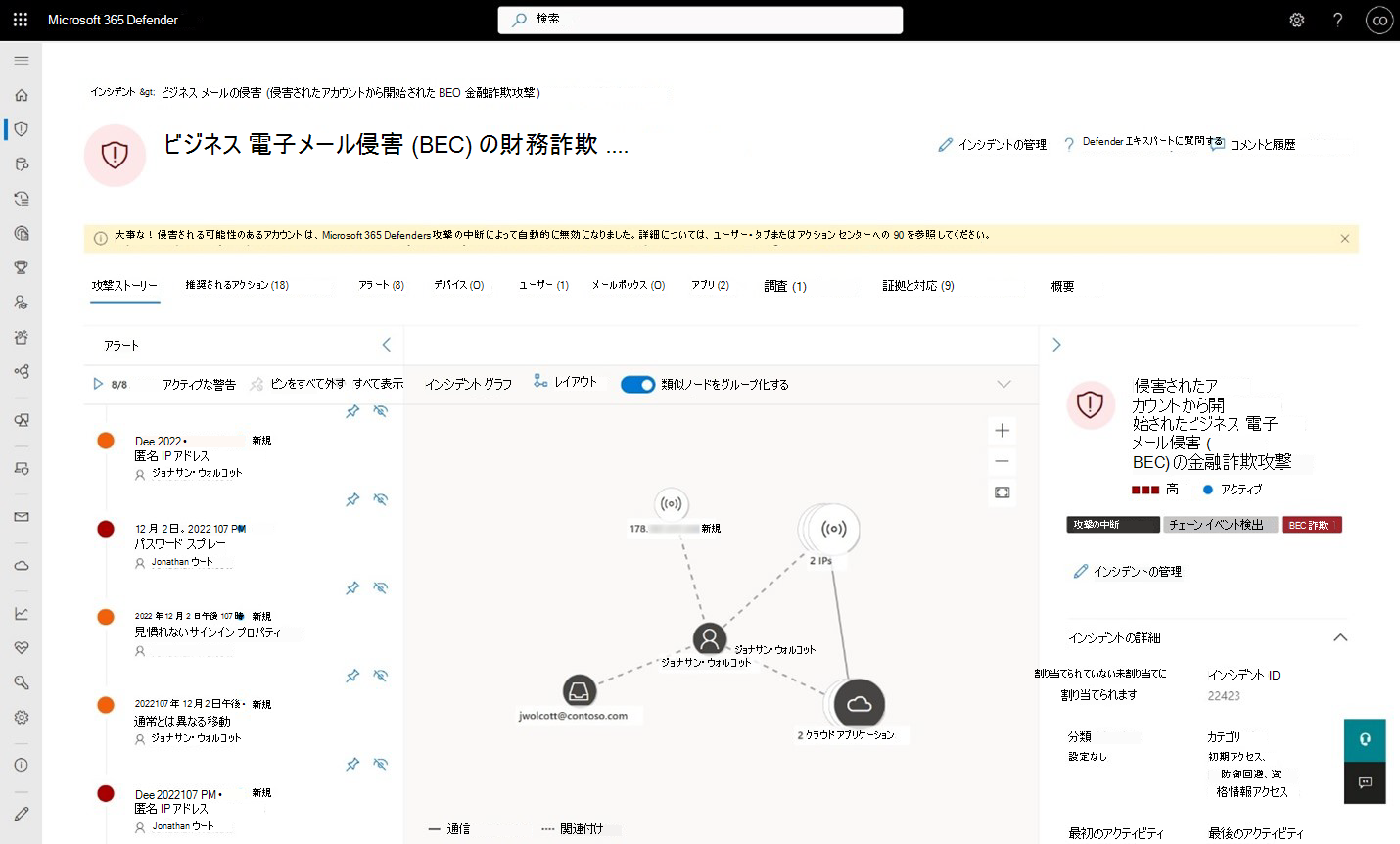 する図 1。自動攻撃の中断がアクションを実行した黄色のバーを示すインシデント ビュー
する図 1。自動攻撃の中断がアクションを実行した黄色のバーを示すインシデント ビュー
Defender XDR ユーザー エクスペリエンスには、これらの自動アクションの可視性を確保するための追加の視覚的な手掛かりが含まれるようになりました。 次のエクスペリエンスで見つけることができます。
インシデント キューで次の手順を実行します。
- [ 攻撃の中断 ] というタイトルのタグが、影響を受けるインシデントの横に表示されます
インシデント ページで、次の手順を実行します。
- 「攻撃の中断」というタイトルのタグ
- ページの上部にある黄色のバナー。自動アクションが強調表示されています
- 現在の資産の状態は、アカウントが無効になっている場合や、含まれているデバイスなど、資産に対してアクションが実行された場合にインシデント グラフに表示されます
API 経由:
(攻撃の中断) 文字列は、自動的に中断される可能性が高い信頼性の高いインシデントのタイトルの末尾に追加されます。 例:
侵害されたアカウントから開始された BEC 金融詐欺攻撃 (攻撃の中断)
詳細については、「 攻撃の中断の詳細と結果を表示する」を参照してください。
次の手順
ヒント
さらに多くの情報を得るには、 Tech Community: Microsoft Defender XDR Tech Community で Microsoft セキュリティ コミュニティに参加します。
フィードバック
以下は間もなく提供いたします。2024 年を通じて、コンテンツのフィードバック メカニズムとして GitHub の issue を段階的に廃止し、新しいフィードバック システムに置き換えます。 詳細については、「https://aka.ms/ContentUserFeedback」を参照してください。
フィードバックの送信と表示