Azure AppFabric Access Control Service (ACS) v 2.0 High Level Architecture – REST Web Service Application Scenario
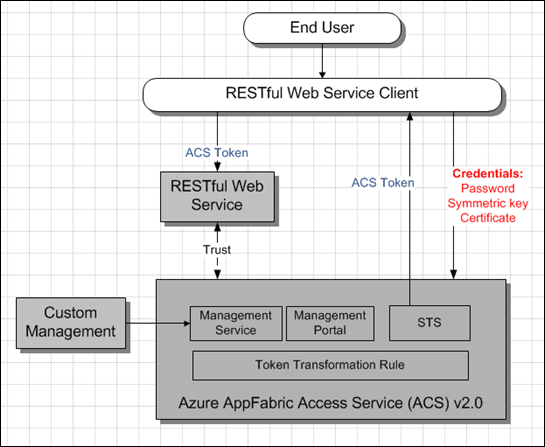
This is a follow up to a previous post Azure AppFabric Access Control Service (ACS) v 2.0 High Level Architecture – Web Application Scenario. This post outlines the high level architecture for a scenario where Azure AppFabric Access Control Service (ACS) V2 involved in authentication and identity flow process between a client and a RESTful Web Service. Good description of the scenario, including visuals and solution summary, can be found here - App Scenario – REST with AppFabric Access Control. The sequence diagram can be found here - Introduction (skip to Web Service Scenario).
In this case there is no involvement of end user, so that User Experience part is irrelevant here.
Important to mention on when to use what for token signing. As per Token Signing:
- Add an X.509 certificate signing credential if you are using the Windows Identity Foundation (WIF) in your relying party application.
- Add a 256-bit symmetric signing key if you are building an application that uses OAuth WRAP.
These keys or certificates are used to protect tokens from tampering while on transit. These certificates and keys are not for authentication. They help maintaining trust between Azure AppFabric Access Control Service (ACS) and the Web Service.
Try out yourself using bootstrap samples available here:
- ASP.NET Simple Service: A very simple ASP.NET web service that uses ACS for authentication and simple authorization
- WCF Username Authentication: A very simple WCF service that authenticates with ACS using a username and password
- WCF Certificate Authentication: A very simple WCF service that authenticates with ACS using a certificate
Related Books
- Programming Windows Identity Foundation (Dev - Pro)
- Developing More-Secure Microsoft ASP.NET 2.0 Applications (Pro Developer)
- Ultra-Fast ASP.NET: Build Ultra-Fast and Ultra-Scalable web sites using ASP.NET and SQL Server
- Advanced .NET Debugging
- Debugging Microsoft .NET 2.0 Applications
More Info
- Azure AppFabric Access Control Service (ACS) v 2.0 High Level Architecture – Web Application
- Windows Identity Foundation (WIF) Explained – Web Browser Sign-In Flow (WS-Federation Passive Requestor Profile)
- Protocols Supported By Windows Identity Foundation (WIF)
- Windows Identity Foundation (WIF) By Example Part I – How To Get Started.
- Windows Identity Foundation (WIF) By Example Part II – How To Migrate Existing ASP.NET Web Application To Claims Aware
- Windows Identity Foundation (WIF) By Example Part III – How To Implement Claims Based Authorization For ASP.NET Application
- Identity Developer Training Kit
- A Guide to Claims-Based Identity and Access Control – Code Samples
- A Guide to Claims-Based Identity and Access Control — Book Download